Rconfig Useradmin Inc Php Information Leakage Vulnerability
Rconfig Useradmin Inc Php Information Leakage Vulnerability
rConfig useradmin.inc.php Information leakage vulnerability
Vulnerability Description
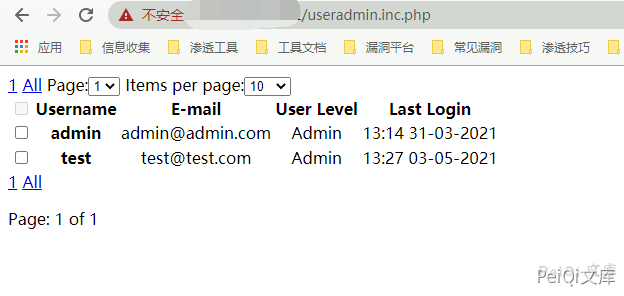
rConfig useradmin.inc.php has an information leakage vulnerability, and you can obtain user email information and login name by accessing files
Vulnerability Impact
rConfig
Network surveying and mapping
app=”rConfig”
Vulnerability reappears
Files with vulnerability
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
<?php
/* Includes */
require_once("../classes/db2.class.php");
include_once('../classes/paginator.class.php');
/* Instantiate DB Class */
$db2 = new db2();
// get timezone for later
$db2->query("SELECT timeZone FROM settings");
$result = $db2->resultsetCols();
$timeZone = $result[0];
date_default_timezone_set($timeZone);
/* Get Row count from users where NOT deleted */
$db2->query('SELECT COUNT(*) AS total FROM users WHERE status = 1');
$row = $db2->resultsetCols();
$result["total"] = $row[0];
/* Instantiate Paginator Class */
$pages = new Paginator;
$pages->items_total = $result['total'];
$pages->mid_range = 7; // Number of pages to display. Must be odd and > 3
$pages->paginate();
echo $pages->display_pages();
echo "<span class=\"\">" . $pages->display_jump_menu() . $pages->display_items_per_page() . "</span>";
/* GET all nodes records from DB */
$db2->query("SELECT id, username, userlevel, email, timestamp FROM users WHERE status = 1 $pages->limit");
$resultSelect = $db2->resultset();
// push rows to $itesm array
$items = array();
foreach ($resultSelect as $row) {
array_push($items, $row);
}
/* Create Multidimensional array for use later */
$result["rows"] = $items;
$i = 0; # row counter to enable alternate row coloring
?>
<table id="userAddTbl" class="tableSimple">
<thead>
<th rowspan="2"><input type="checkbox" disabled="disabled"/></th>
<th rowspan="2">Username</th>
<th rowspan="2">E-mail</th>
<th rowspan="2">User Level</th>
<th rowspan="2">Last Login</th>
</thead>
<tbody>
<?php
foreach ($result['rows'] as $rows):
$id = $rows['id'];
/* This bit just updates the class='row' bit with an alternating 1 OR 0 for alternative row coloring */
echo '<tr class="row' . ($i++ % 2) . '">';
?>
<td align="center"><input type="checkbox" name="tablecheckbox" id="<?php echo $id; ?>"/></td>
<td align="center"><strong><?php echo $rows['username'] ?></strong></td>
<td align="center"><?php echo $rows['email'] ?></td>
<td align="center">
<?php
// quick check if userlevel =9 user is admin else, user is a User
if ($rows['userlevel'] == 9) {
$userlevel = "Admin";
} else {
$userlevel = "User";
}
echo $userlevel;
?></td>
<td align="center">
<?php
// quick convert unix TimeStamp to normal times
$lastLogin = date('H:i d-m-Y', $rows['timestamp']);
echo $lastLogin;
?>
</td>
</tr>
<?php endforeach; ?>
</tbody>
</table>
<?php
echo $pages->display_pages();
echo "<div class=\"spacer\"></div>";
echo "<p class=\"paginate\">Page: $pages->current_page of $pages->num_pages</p>\n";
The file does not have permission to be set, and anyone can access the leaked information
The URL of vulnerability verification is
/useradmin.inc.php
Leaking user information
This post is licensed under CC BY 4.0 by the author.