Yzmcms Background Acquisition Module Ssrf Vulnerability
YzmCMS background acquisition module SSRF vulnerability
Vulnerability Description
YzmCMS Content Management System is a lightweight open source content management system which is developed using the independent research and development framework YZMPHP.
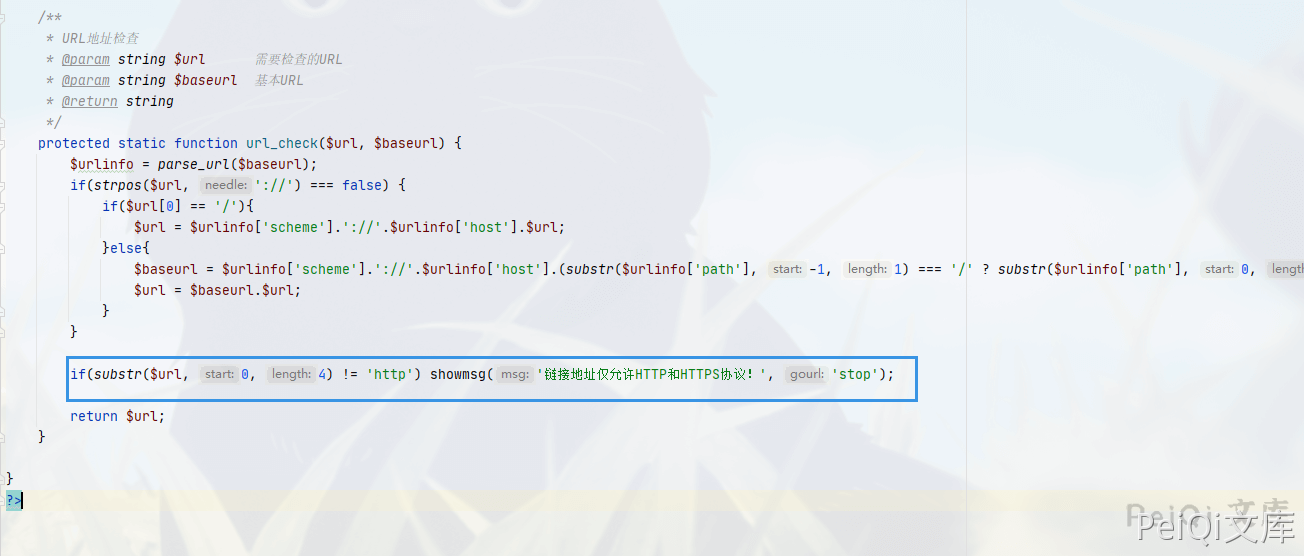
The source code has a defect in protocol identification, resulting in an SSRF vulnerability
Vulnerability Impact
YzmCMS version < V5.8 official version
Environment construction
</a-alert>
Vulnerability reappears
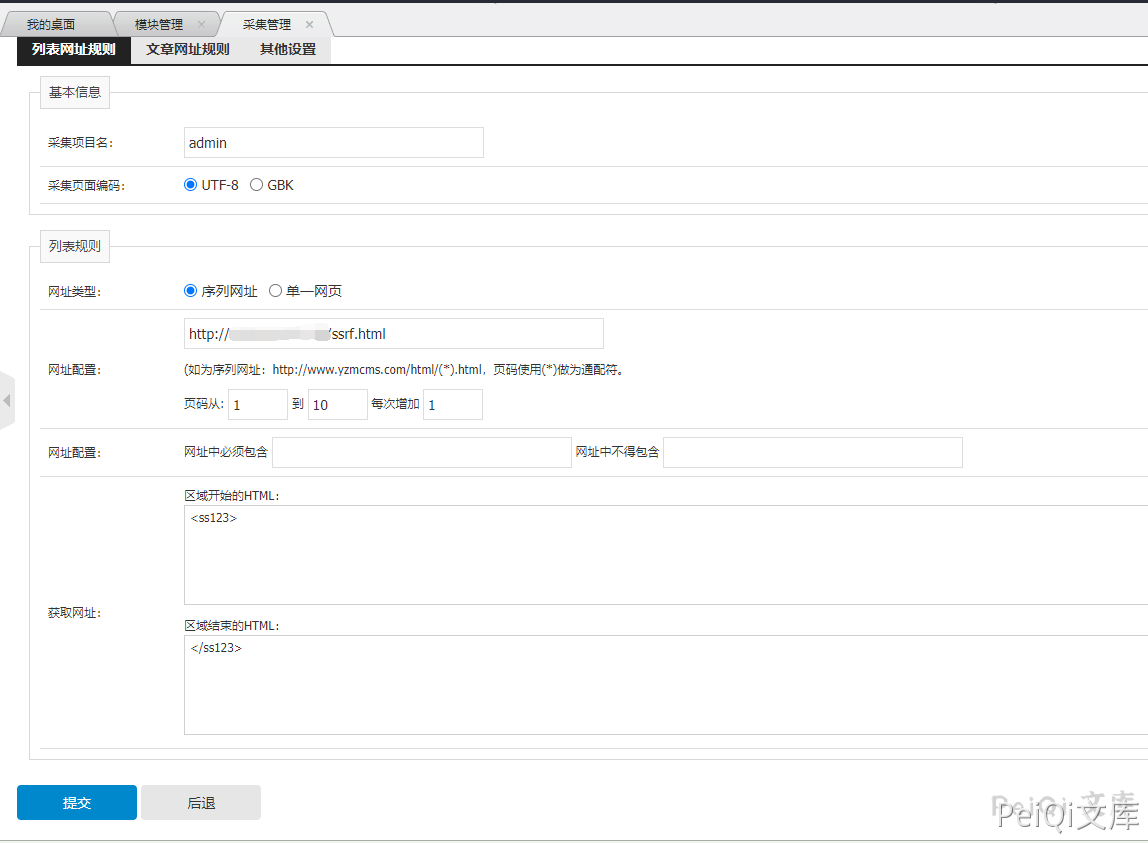
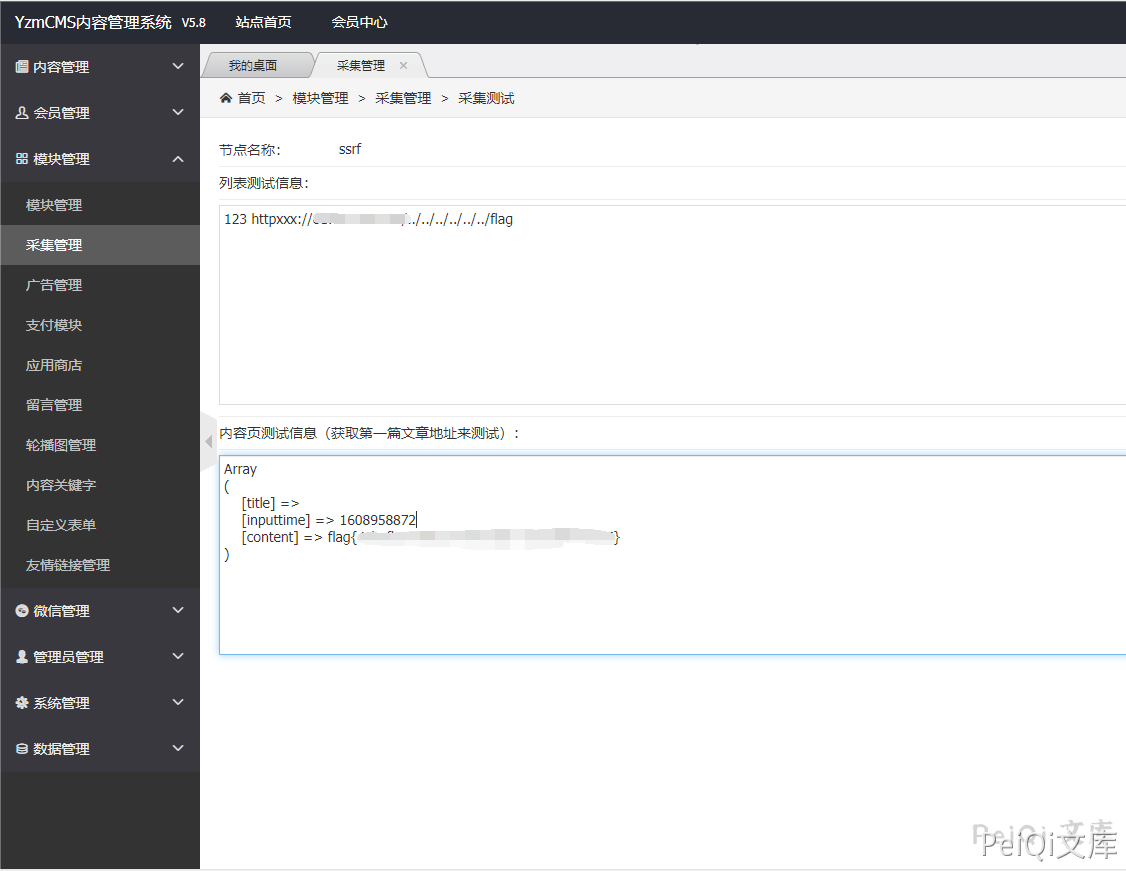
Log in to the background –> Module management –> Collection management
Add collection rules
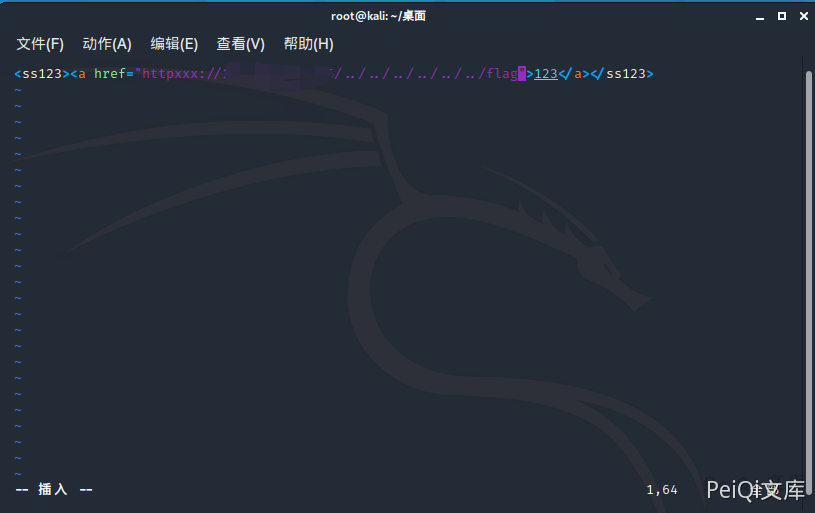
Edit HTML code on your server
The root directory may be different, the payload needs to be changed
Click to collect and read the flag in the root directory
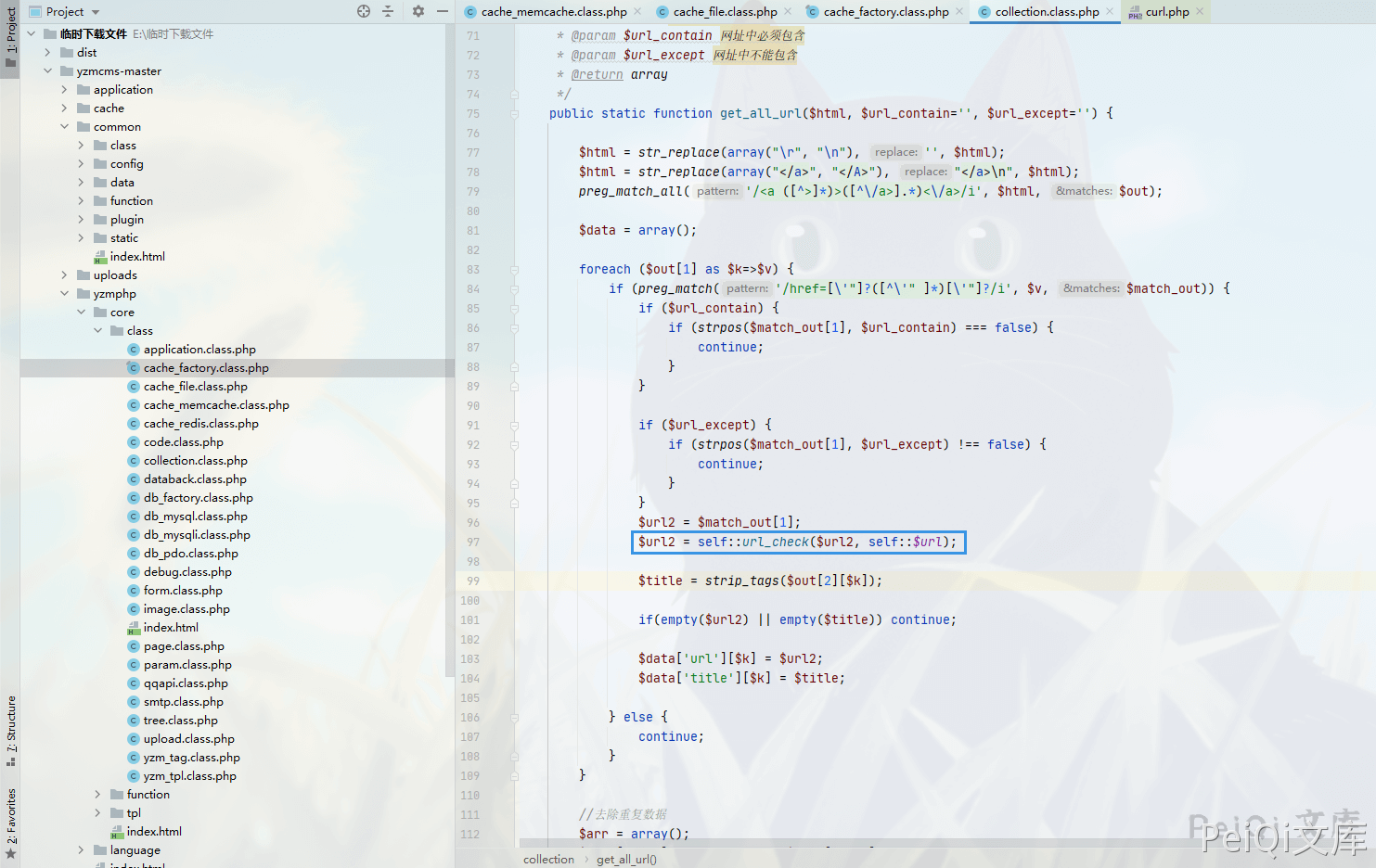
The code location where the vulnerability occurs yzmcms/yzmphp/core/class/cache_factory.class.php
Call the *url_check* function here
You can see that only the first 4 digits are http. You can bypass it by using httpxxx